
Protect API Using Role-Based Access Control (RBAC) with Identity Pools Part 2
Learn how to implement role-based access control for API protection using SecureAuth identity pools in part 2 of this series.

Learn how to implement role-based access control for API protection using SecureAuth identity pools in part 2 of this series.

Throughout the years, creators of SPA applications have used different approaches to securely store OAuth tokens

Securing applications is not easy, we get it. Is it, however, possible to enable the developers to d...

OAuth 2.0 Token Exchange on-behalf-of (delegation) flow enables client applications to act on behalf of a different entity
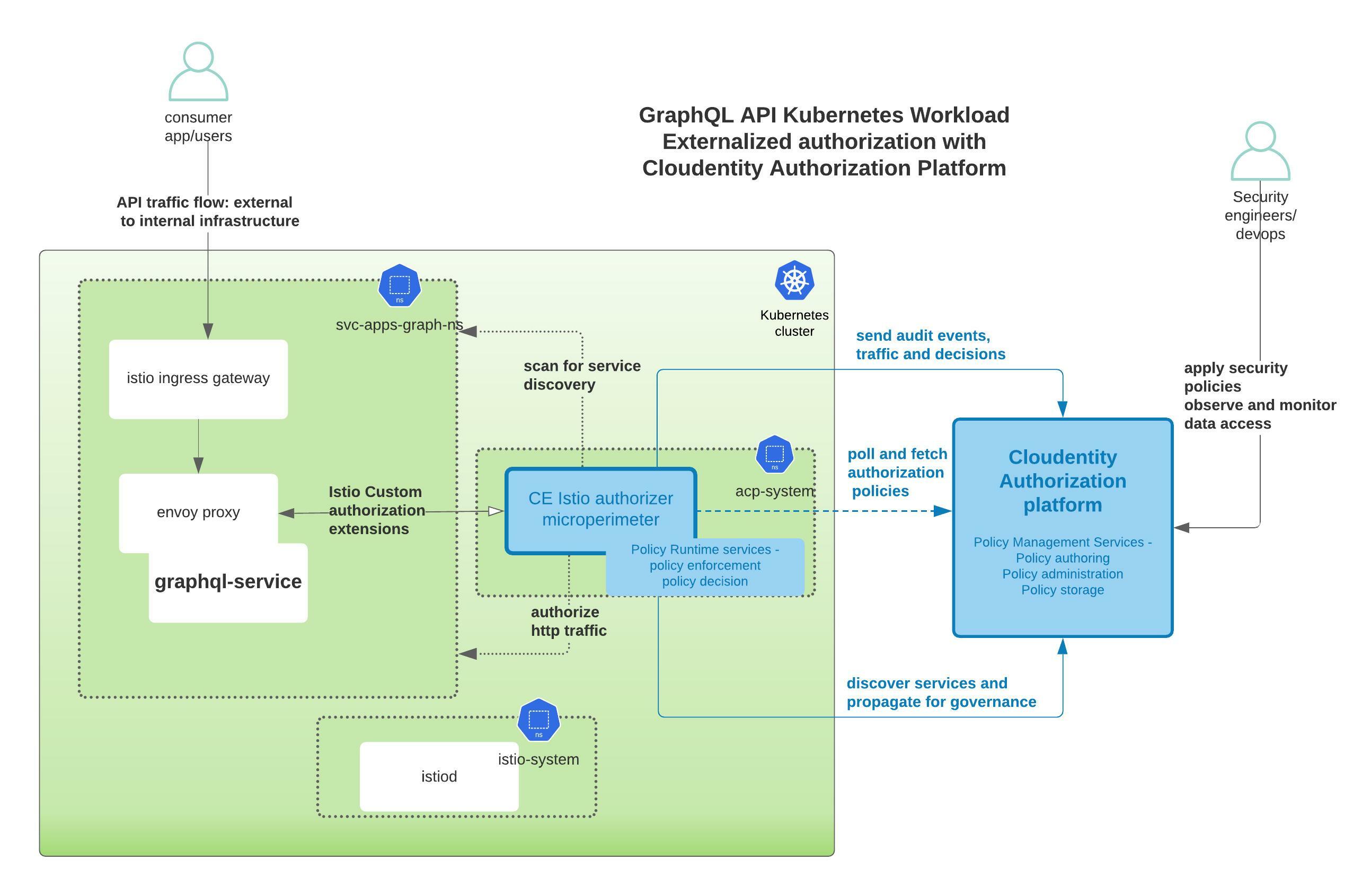
This article is the third part of a series to explore usage of the SecureAuth authorization platform for externalized GraphQL runtime authorization along with policy based access controls.
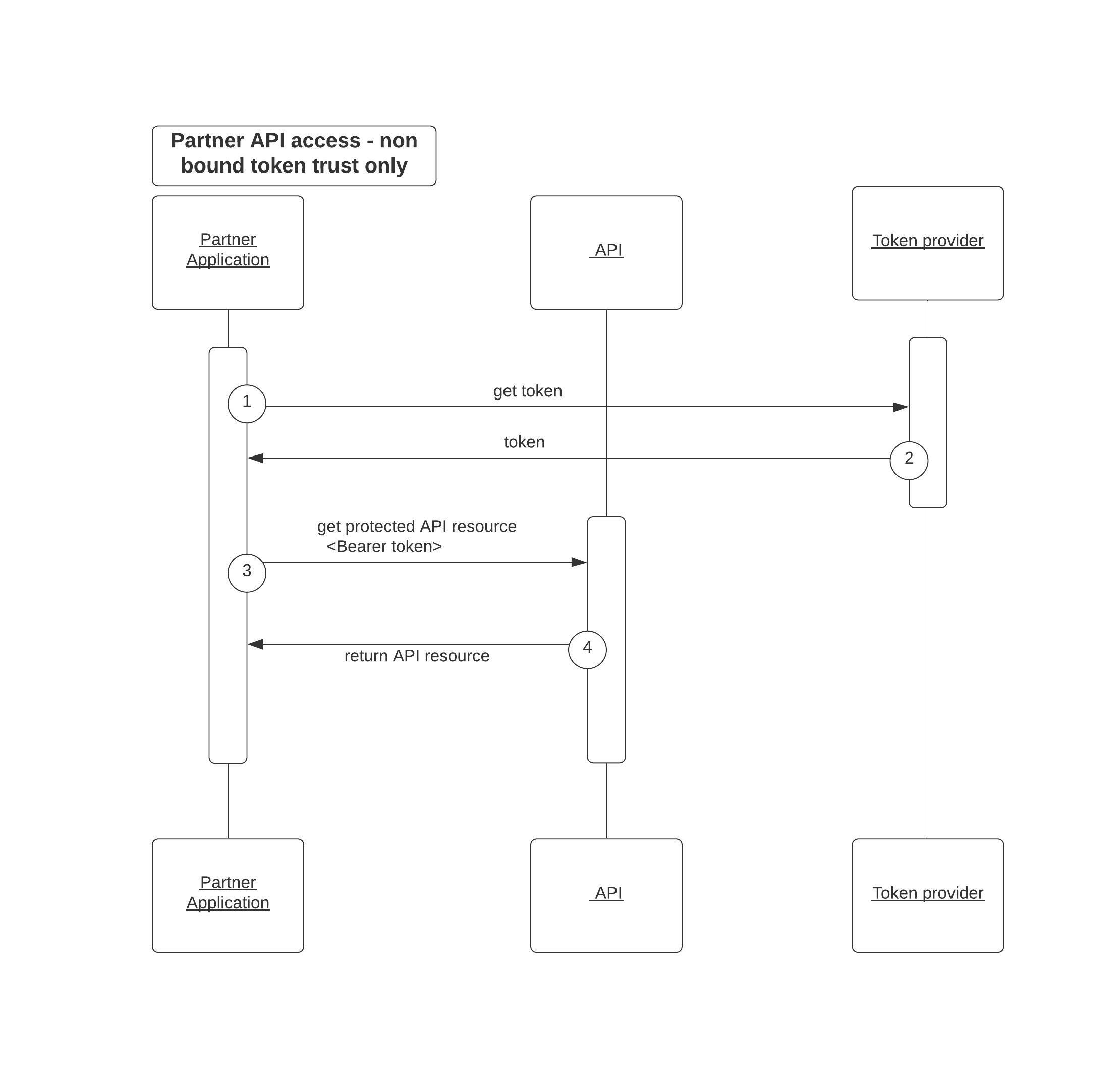
Learn how to secure partner API integrations using OAuth with mutual TLS authentication.
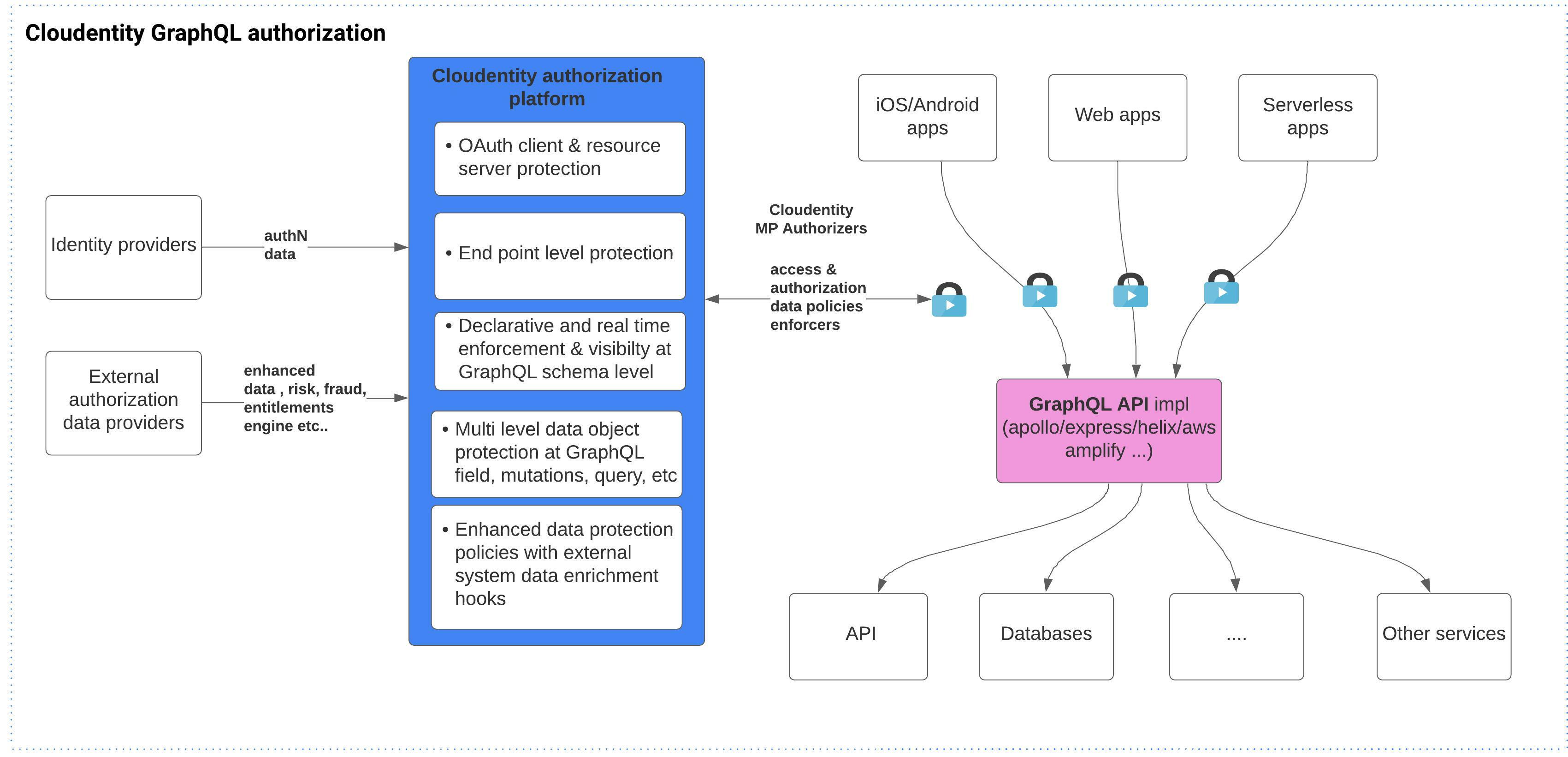
This article is the first part of a series to explore usage of the SecureAuth authorization platform for externalized GraphQL runtime authorization along with policy based access controls.
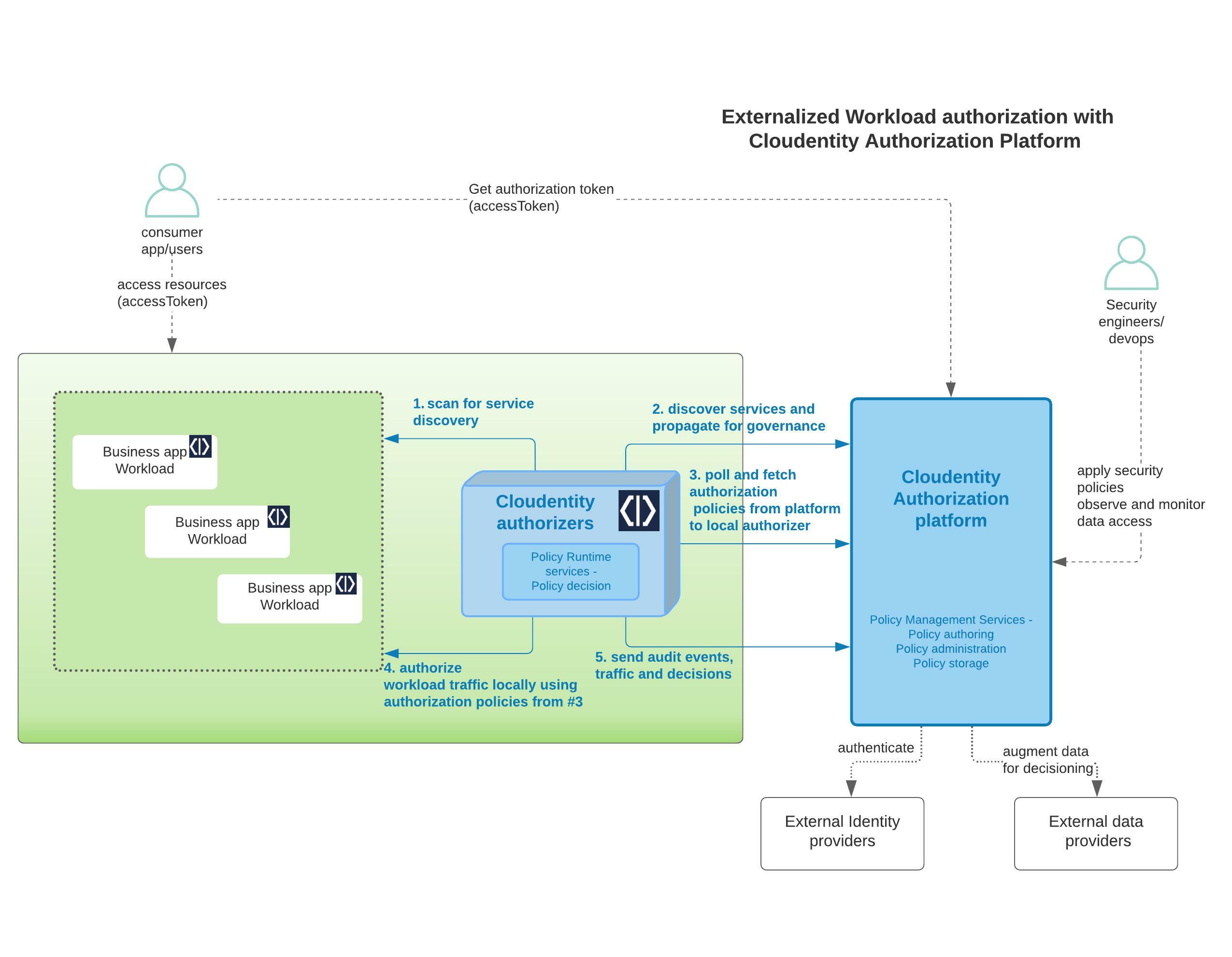
This article is the second part of a series to explore usage of the SecureAuth authorization platform for externalized GraphQL runtime authorization along with policy based access controls.

This article describes how the OpenID foundation certification process is done in SecureAuth with th...
Solid backup process is a necessity for any SaaS platform and SecureAuth is no exception. We underst...