How the SecureAuth Risk Engine Prevents Account Takeovers (ATO)
Account takeover (ATO) attacks often use valid credentials obtained through phishing, leaked databases, or credential reuse. Because the credentials themselves are legitimate, authentication alone cannot distinguish between a real user and an attacker.
The SecureAuth Risk Engine (Risk V2) addresses this gap by introducing a contextual and adaptive risk layer on top of authentication. Rule-based analyzers and machine learning (ML) models evaluate every login request and calculate a Level of Assurance (LOA) score based not only on credentials, but also on device, IP, behavioral, and environmental signals.
At the heart of this system is the Risk Process Unit (RPU) - the core component that orchestrates the analysis of each authentication request.
The higher the LOA, the greater the confidence in that session. A low LOA means something feels "off," even if the credentials check out.
The journey of a login request
When an authentication request arrives, it passes through SecureAuth's calculate_score API and the RPU immediately begins collecting context:
- IP address reputation and network type
- Browser fingerprint (DBFP) from 40+ device attributes
- Geolocation and timezone consistency
- Behavioral history and login timing
- Threat intelligence signals, such as leaked credentials or bot detection
Inside the RPU, several independent analyzers evaluate the request. Rule-based analyzers look for known red flags like VPN usage, impossible travel, or new device fingerprints. Adaptive ML models learn what "normal" looks like for each user and tenant, detecting subtle behavioral anomalies that rules cannot capture.
Once all analyzers return their results, the RPU aggregates their scores into a single LOA using a weighted approach. The outcome determines what happens next:
- ALLOW: The system trusts the session and allows it to proceed normally.
- CHALLENGE: The system triggers MFA or an additional verification step.
- DENY: The system blocks the attempt outright.
The system logs every evaluation and streams it to audit systems like Splunk for visibility and compliance.
Risk intelligence signal matrix
The Risk Engine evaluates dozens of signals across four key dimensions. Each signal carries an assigned severity level that influences the final LOA calculation.
IP risk and network intelligence
| Signal | Severity | Description |
|---|---|---|
KNOWN_USER_IP_USED_BY_MANY_USERS | HIGH | IP reused by multiple accounts (possible botnet or credential sharing) |
IP_RISK_SCORE_ABOVE_THRESHOLD | CRITICAL | IP flagged as risky by threat intelligence |
IP_PROXY_TYPE | MEDIUM | Proxy usage detected |
IP_PROXY_LEVEL_ELITE | HIGH | Elite proxy indicating deliberate obfuscation |
IP_ANONYMIZER_ACTIVE_DETECTED | HIGH | Active anonymizer tool detected |
IP_TOR_PROXY_DETECTED | HIGH | Tor network usage |
Geolocation analyzers
| Signal | Severity | Description |
|---|---|---|
LOCATION_CHANGE_IMPOSSIBLE_TRAVEL | CRITICAL | Login pattern impossible given previous location/time |
LOCATION_SUSPICIOUS_COUNTRY | CRITICAL | Login from a high-risk or geo-blocked region |
LOCATION_TIMEZONE_MISMATCH | MEDIUM | Device timezone doesn't align with IP location |
LOCATION_NEW_LOCATION_DISTANCE_THRESHOLD | HIGH | Login from a location far from known trusted locations |
Browser and device fingerprinting (DBFP)
| Signal | Severity | Description |
|---|---|---|
DBFP_NEW_DEVICE_DETECTED | MEDIUM | Unrecognized browser/device fingerprint |
DBFP_TAMPERED_HONEYPOT | CRITICAL | Honeypot field manipulation (fingerprint evasion attempt) |
DBFP_TAMPERED_BROWSER_ATTRIBUTES | HIGH | Suspicious manipulation of browser attributes |
DBFP_HEADLESS_BROWSER | MEDIUM | Headless browser usage that usually indicates automation |
Behavioral and threat intelligence
| Signal | Severity | Description |
|---|---|---|
BEHAVIOR_LEAKED_CREDENTIAL | CRITICAL | Credential pair found in external leak feeds |
BEHAVIOR_LEAKED_USERNAME | HIGH | Username found in compromised datasets |
BEHAVIOR_LEAKED_PASSWORD | HIGH | Password found in leaked password repositories |
BEHAVIOR_BOT_DETECTED | HIGH | Automated login pattern detected |
BEHAVIOR_SIMILAR_CREDENTIAL_COMBO | MEDIUM | Pattern similar to known breached combinations |
The role of machine learning models
While rule-based analyzers flag deterministic issues (e.g., a Tor exit node or leaked credential), adaptive ML models detect subtle anomalies in behavior that rules can't easily describe.
SecureAuth's Risk Engine includes four ML models trained per user:
| Model | Focus | Function |
|---|---|---|
| LT (Location Trust) | Geographic patterns | Learns a user's usual login locations and predicts the likelihood of being in a specific place at a given time. Flags anomalies. |
| BT (Browser Trust) | Browser/device patterns | Uses AIML to learn login patterns, time of use, and browser consistency to adapt authentication dynamically. |
| KTU (Kuber-Time-Usage) | Temporal and session behavior | Builds a user-specific temporal profile across applications to detect unusual login times or session frequencies. |
| KTG (Kuber-Time-Group) | Cross-user correlation | Login patterns for users with shared characteristics, such as working in the same organization, timezone, or application environment. |
Comprehensive example: Detecting a sophisticated ATO attempt
Persona: Sarah Patel, Senior HR Manager in New York, USA
Normal behavior:
- Login times: 8 AM to 5 PM EST
- Locations: New York and occasionally Boston
- Devices: MacBook and iPhone
Anomalous event:
- Login time: 2:45 AM EST
- Location: Mumbai, India
- Device: Windows laptop
- Browser: New Chrome version not seen before
Analyzer outcomes
| Analyzer | Detection | Result |
|---|---|---|
| DBFP | 9 of 42 fingerprint attributes differ (screen size, OS, browser version) | Moderate device anomaly |
| BT | New browser version and off-hour usage | Browser trust reduced |
| LT (Trusted Location) | Mumbai location is abnormal | Location trust drops to 0.15 |
| KTU | Login time far outside typical window | Low score 0.22 |
| KTG | HR group typically logs in 8 AM to 6 PM EST | Low group trust 0.18 |
| Geo-IP | IP shared with 14 unknown accounts + VPN detected | Geo-IP score 0.10 |
Final LOA score: 0.24
Below threshold (0.5) → MFA challenge or session block initiated.
Result:
The Risk Engine prevents a potential account takeover by correlating anomalies across device, location, and behavioral dimensions while maintaining a seamless experience for legitimate users.
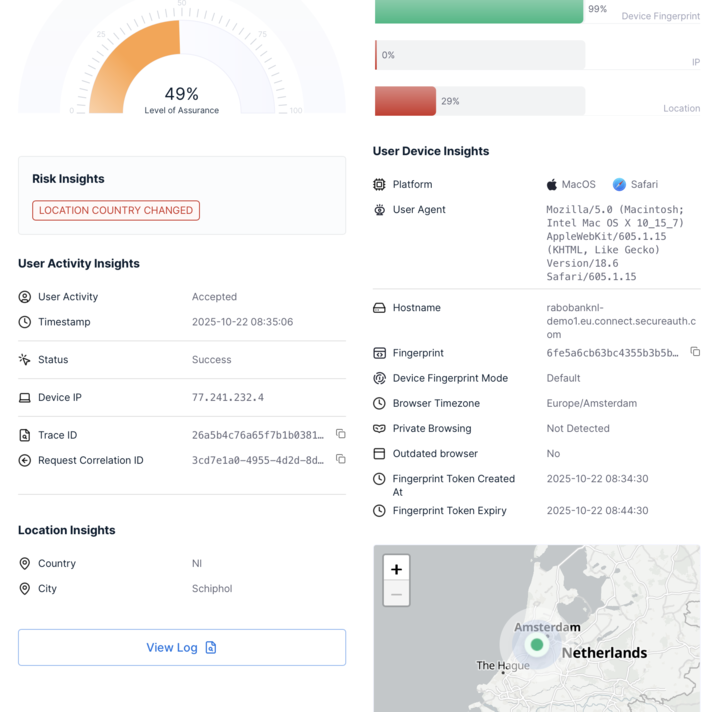
ATO detection metrics and insights
The SecureAuth Risk Engine continuously analyzes authentication events across multiple behavioral and contextual dimensions. The Risk Analytics Dashboard surfaces key insights and metrics to help security teams detect Account Takeover (ATO) attempts and identify abnormal usage patterns.
Multi-device usage
Tracks how many distinct devices a user employs over a given time window.
Abnormal spikes can indicate credential sharing or session hijacking.
- Example insight: User logged in from 4 unique devices within 1 hour.
- Detection sources: DBFP Analyzer, Behavior Analyzer
Multi-IP and geolocation anomalies
Identifies multiple logins from diverse IPs or distant locations within short timeframes.
Helps flag impossible travel or VPN-based obfuscation.
- Example insight: Consecutive logins from Frankfurt and New Jersey within 8 minutes.
- Detection sources: IP Reputation Analyzer, Geolocation Analyzer
Device usage pattern change
Highlights shifts in device type, platform, or browser signature compared to user baseline.
- Example insight: Browser changed from Chrome/macOS to Edge/Windows within 30 minutes.
- Detection sources: DBFP Analyzer, BrowserTrust Model
Time-based anomalies
Evaluates login timestamps relative to historical behavior.
- Example insight: Login occurred at 3:12 AM local time, outside the user's 7 AM to 6 PM pattern.
- Detection sources: KTU / KTG Time Models, Behavior Analyzer
Multi-region or country switching
Detects user activity originating from multiple regions within a short period.
Often linked to VPN use or shared accounts across geographies.
- Example insight: User accessed account from US-East and EU-West within 12 hours.
Shared account or subscription detection
Correlates overlapping device fingerprints, IPs, and session timings across different user IDs.
Flags potential account sharing or reseller abuse.
- Example insight: Three user IDs share the same device fingerprint and residential IP.
- Detection sources: DBFP Analyzer, IP Reputation Analyzer, Behavior Analyzer
Session velocity and frequency
Measures login bursts, concurrent sessions, or abnormally high activity.
- Example insight: User initiated 25 login attempts within 10 minutes.
- Detection sources: Behavior Analyzer
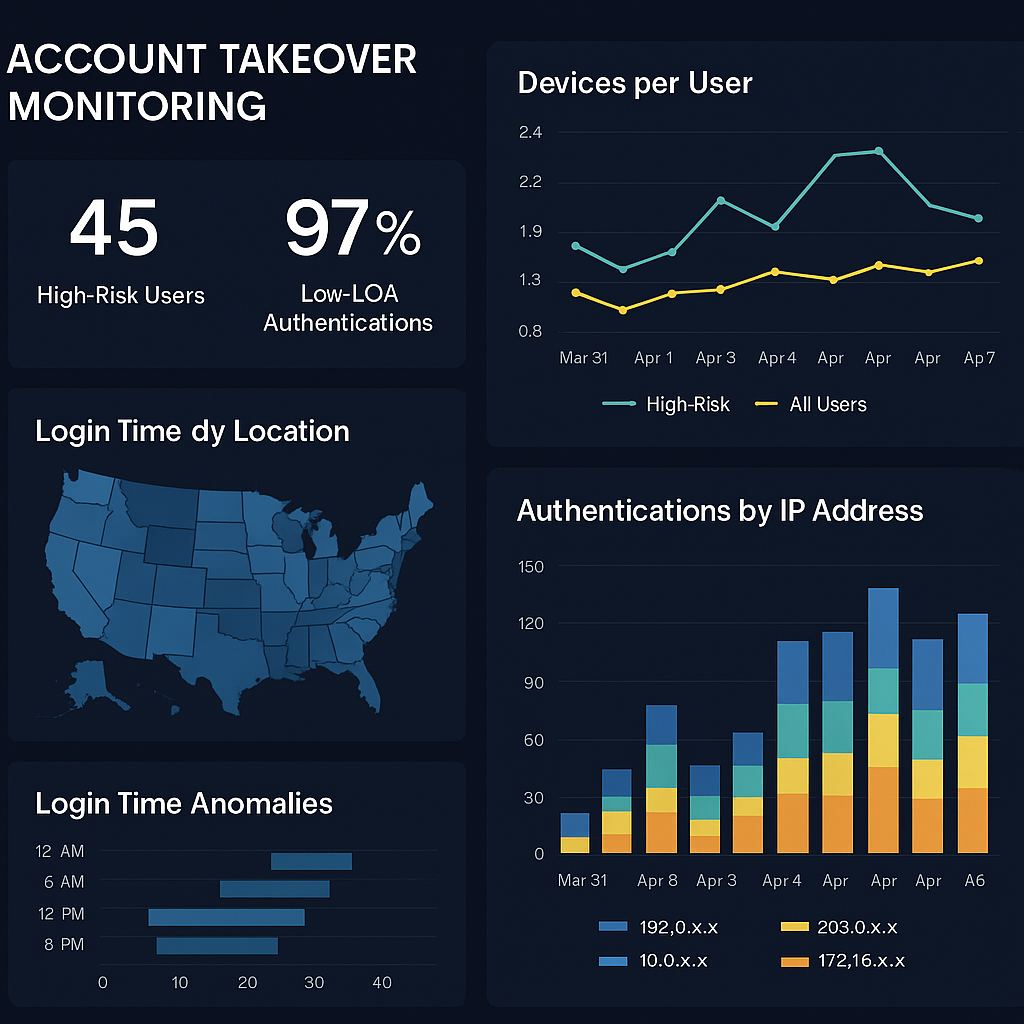
High-risk user indicators
The Risk Dashboard aggregates these dimensions into user-level risk profiles, enabling proactive defense and forensic visibility.
| High-Risk Insight | Description | Example Trigger |
|---|---|---|
| ATO-Prone User | Multiple low-LOA logins or failed MFA attempts | ≥3 CHALLENGE/FAIL in 24h |
| Device Farmer | High diversity of devices in short period | >10 unique DBFPs in 7 days |
| VPN-Only User | All logins originate from VPNs or proxies | 100% VPN connections |
| Shared Credentials | Multiple accounts use same IP or fingerprint | ≥5 user_ids per IP |
Common dashboard visualizations include:
- User Risk Timeline: LOA trend per user over time
- Device vs. IP Heatmap: Correlation between device count and IP diversity
- Geo Risk Map: Real-time view of high-risk login origins
- High-Risk User Table: Ranked list of users with most frequent low LOA scores
- Time-of-Day Analysis: Highlight of login time anomalies and off-hour access patterns
Compliance and reporting
The system logs every analyzer output, LOA score, and decision and streams them to monitoring tools like Splunk. This provides:
- Real-time monitoring of risky logins
- Audit trails for compliance frameworks such as SOC2, PCI-DSS, ISO 27001
- Evidence supporting a Zero Trust authentication model
Summary
Even when credentials are valid, the SecureAuth Risk Engine evaluates login attempts across multiple dimensions: IP risk, device fingerprint, geolocation, time, and behavioral signals.
By combining rule-based checks, ML models, and threat intelligence, the engine provides an adaptive, explainable defense against account takeover attacks while keeping legitimate users' experience seamless.