Risk Engine: Smarter security in action
The Risk Engine is your key to stronger, smarter security. It works behind the scenes to check for risks whenever someone logs in or accesses sensitive information. Using advanced tools like rules, machine learning (ML), and AI, it quickly spots potential threats and keeps your system safe.
Here’s how it works:
It’s organized into domains, each focused on different risk factors. For example, the Device domain uses tools like the Browser Fingerprint Analyzer to check if a device is safe.
It uses a Level of Assurance (LOA) to decide how much access to allow based on risk.
A dynamic scoring model adjusts risk levels in real time, so the system stays ahead of threats.
The Risk Engine is easy to set up and works seamlessly with your existing systems. From day one, it provides strong security using machine learning (ML) to help your organization stay secure.
How the Risk Engine powers risk-based authentication
Risk-Based Authentication (RBA) adds an extra layer of security by adapting to the situation whenever someone tries to log in. It looks at factors like user behavior, device, and network to decide how much verification is needed. This approach keeps things simple for trusted users while adding stronger checks when something seems risky.
RBA works perfectly with a Zero Trust security model. Zero Trust assumes that threats can come from anywhere, inside or outside your network. That’s why it constantly verifies users and devices, making sure only the right people can access important systems and data.
The Risk Engine powers RBA by analyzing risks in real time, helping your organization stay secure without slowing down users.
The Risk Engine: Your security core
The Risk Engine is the heart of any Risk-Based Authentication (RBA) system. It works in real time to assess how risky a login attempt might be, using data from multiple sources to make smart decisions.
Here’s what the Risk Engine checks:
User Behavior: Does this login match the user’s normal habits, like time of day, location, or device? If something seems unusual, it may flag the attempt as high risk.
Device Information: Is the device trusted? Using device and browser fingerprinting, the engine identifies potential risks and calculates a confidence score based on changes or mismatches.
Network & IP Address: Is the request coming from a trusted network or IP address? Attempts from suspicious IPs or restricted countries lower confidence levels.
Geolocation: Is the user in a typical location? Logins from unusual places or sudden location changes (like impossible travel) may trigger extra checks.
User History: Has the user shown risky behavior before? Things like failed logins, unusual account activity, or rejected MFA requests can reduce confidence in the attempt.
The Risk Engine brings all this data together to decide how much verification is needed. It keeps systems secure while letting trusted users log in easily.
What is Level of Assurance (LOA)?
The Level of Assurance (LOA) is a key measure of how much trust an organization places in a user's identity during authentication. It shows how confident the system is that the person logging in is who they claim to be.
Here’s how it works:
Higher LOA Scores: These mean stronger, more secure authentication methods were used, giving more confidence in the user’s identity.
Behavior Monitoring: The system checks login patterns, device use, and location. If everything matches the user’s usual behavior, confidence goes up. If something seems unusual, the system might require extra verification.
The LOA score ensures a balance between security and ease of use. Higher scores mean more reliable authentication, helping organizations keep their systems secure while maintaining trust in user identities.
Inside the LOA scoring system
The Level of Assurance (LOA) score evaluates the trustworthiness of a user’s identity during authentication. It’s calculated using a weighted scoring model that combines results from multiple risk factors, like device, user behavior, and location.
Here’s how it works:
Confidence Analyzer Scores: Each analyzer generates a score (0–100) based on confidence.
Weighted Scores: Each score is multiplied by its weight to reflect its importance.
Domain-Level Scores: Weighted scores for all analyzers are combined within each domain.
Final LOA Score: The total weighted score is divided by the sum of all weights, resulting in an LOA score.
Example table
Confidence Analyzer | Score (0–100) | Weight | Weighted Score (Score × Weight) |
|---|---|---|---|
Browser Fingerprinting | 80 | 1 | 80 |
IP | 90 | 1 | 90 |
Location Trust | 70 | 0.5 | 35 |
ML Time Anomaly (User) | 50 | 0.5 | 25 |
ML Time Anomaly (Group) | 60 | 0.25 | 15 |
Step-by-step calculation:
Total Weighted Score: 80 + 90 + 35 + 25 + 15 = 245
Total Weights: 1 + 1 + 0.5 + 0.5 + 0.25 = 3.25
Final LOA Score: 245 ÷ 3.25 = 75.4
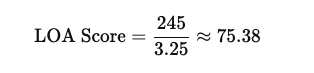 |
This method ensures the most critical factors have the greatest influence, providing an accurate and actionable score to assess risk and guide authentication decisions.
Rule-based vs. AI: Smarter risk assessment
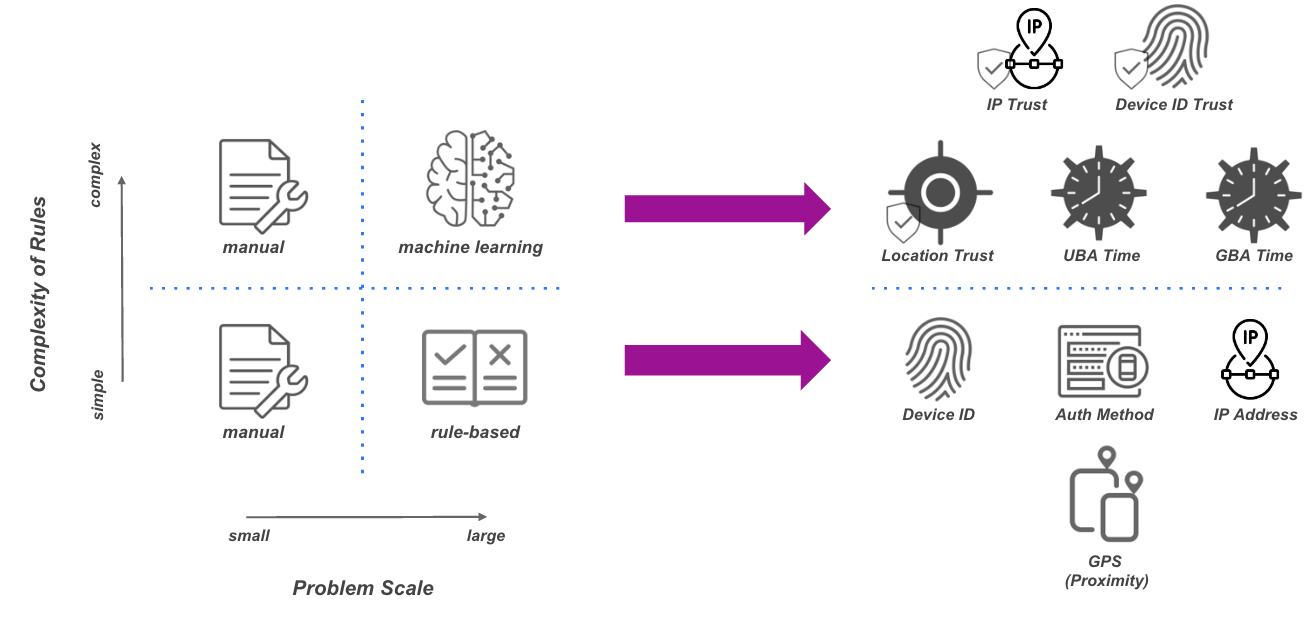
Modern security systems use two key approaches to identify risks: rule-based systems and machine learning (ML). Each has a unique role in keeping systems secure.
Rule-based systems. These rely on rules set by administrators to spot risky actions. For example, they check for things like trusted devices, known IP addresses, or unusual location changes (like "impossible travel"). While great for simple risks, rule-based systems may miss more advanced or evolving threats.
Machine learning models. ML uses data and patterns to assess risks in real time. By learning from past behavior, these models can detect subtle and complex threats that rules might overlook. They adapt as risks evolve, offering a more flexible and robust solution.
Combining these two approaches creates a powerful defense. Rules handle known risks, while ML uncovers the unexpected, ensuring your systems stay ahead of threats.
 |
DBFP and BT: Smarter device authentication
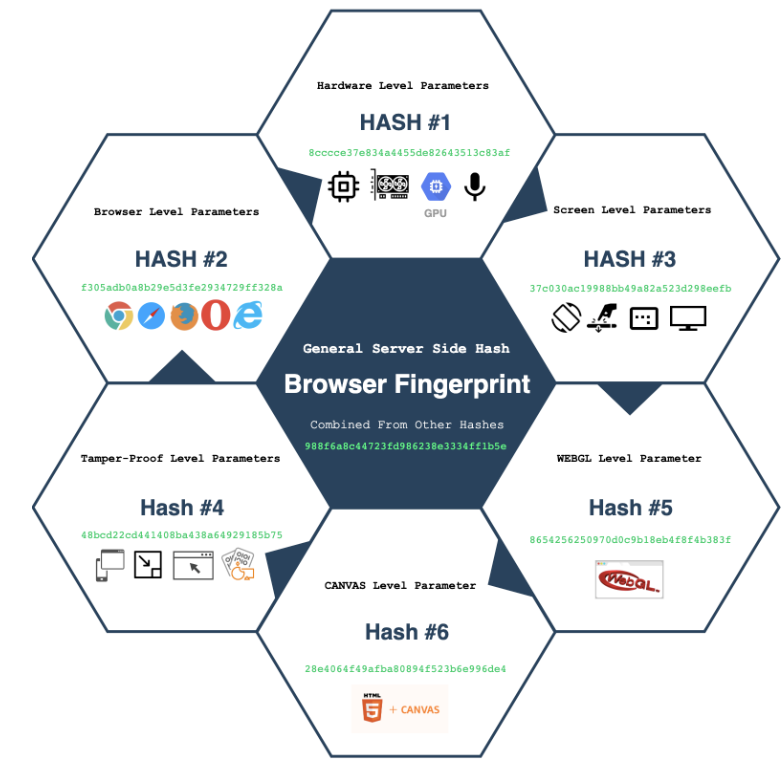
Device Browser Fingerprint (DBFP) is a key tool for improving security. It collects over 30 unique details from a user’s device—like browser type, operating system, screen size, and plugins. These details create a unique "fingerprint" for each device.
The system uses these fingerprints to track how users typically log in. By spotting changes or unusual activity, DBFP can detect potential fraud, helping secure your accounts while keeping trusted users’ access seamless.
 |
Browser Trust (BT) uses AI and machine learning (AIML) to make authentication smarter and more adaptive. Instead of relying on rigid rules, BT dynamically analyzes user behavior, creating a personalized confidence score for each login attempt.
Here’s what BT evaluates:
Login Patterns: Times of day and days of the week.
Device and Browser Usage: Is the device and browser consistent with past logins?
Authentication Method Consistency: Are the user’s methods predictable or unusual?
By learning a user’s typical behavior, BT gets more accurate over time, adjusting security levels based on real-time data.
 |
John Doe’s device pattern example
John Doe uses multiple devices each day:
Morning: Phone
Afternoon: Work laptop
Evening: Personal laptop
The Risk Engine assigns each device a unique fingerprint. If John suddenly logs in from his work laptop in the middle of the night, the system flags it as unusual and may require extra verification.
This approach balances security and convenience, protecting against threats while minimizing user friction.