Get started with the Agentic AI workspace demo
The SecureAuth Agentic AI Workspace demonstrates how identity-driven access control secures AI-powered applications. This guide shows you how to run the Finance Assistant demo app, authenticate users with SecureAuth MCP, and see fine-grained authorization in action.
The Finance Assistant demo consists of:
- Python Web App (UI) - A browser-based assistant for finance questions
- LLaMA Model Container (~2 GB) - Provides LLM responses
- Standalone Authorizer - Enforces policies based on OAuth tokens and group membership
With this demo, you'll see how SecureAuth ensures only authorized users can access sensitive AI functions.
Watch this complete walkthrough to see the Finance Assistant demo in action:
Demo architecture and user scenarios
This demo integrates several components to demonstrate identity-driven AI access control with two distinct user scenarios.
Authentication & authorization Flow
-
SecureAuth – Authenticates users and issues OAuth (Open Authorization) tokens with specific scopes based on group membership.
-
Standalone Authorizer – Validates tokens and enforces access policies before allowing AI interactions.
AI infrastructure
-
MCP Server/Client – Implements the Model Context Protocol (MCP) to securely connect AI agents with external services.
-
Ollama – An open-source platform that runs large language models locally.
-
LLaMA (Large Language Model Meta AI) – The actual AI model that generates responses to user queries.
Demo user interface
- Finance Assistant Web App – Python-based interface where users interact with the AI assistant.
Demo users and group-based access
-
John Doe (jdoe) as a Finance group member – Receives OAuth tokens with finance-related scopes (Cash Balance, Payroll Liability) and can access all AI functions including sensitive financial data queries.
-
Alice Smith (asmith) as a Non-finance user – Receives OAuth tokens with only basic profile scopes and is blocked from accessing sensitive financial AI functions.
When you authenticate through SecureAuth with one of the demo users, your group membership determines which scopes are included in your OAuth token. The MCP components and Standalone Authorizer use these tokens to control what AI functions you can access, demonstrating fine-grained authorization in action.
Prerequisites
Before you begin, ensure the following are installed on your system:
- Docker and Docker Compose
- A terminal (Linux, macOS, or Windows WSL)
- Network access to download the demo and Ollama with the LLaMA model (~2 GB)
Step 1: Add the Agentic AI Demo workspace
Learn more about adding an Agentic AI workspace.
Step 2: Download, extract, and start the demo
-
In the Agentic AI workspace, click Download Package. This downloads the
demo-app.zippackage provided by SecureAuth.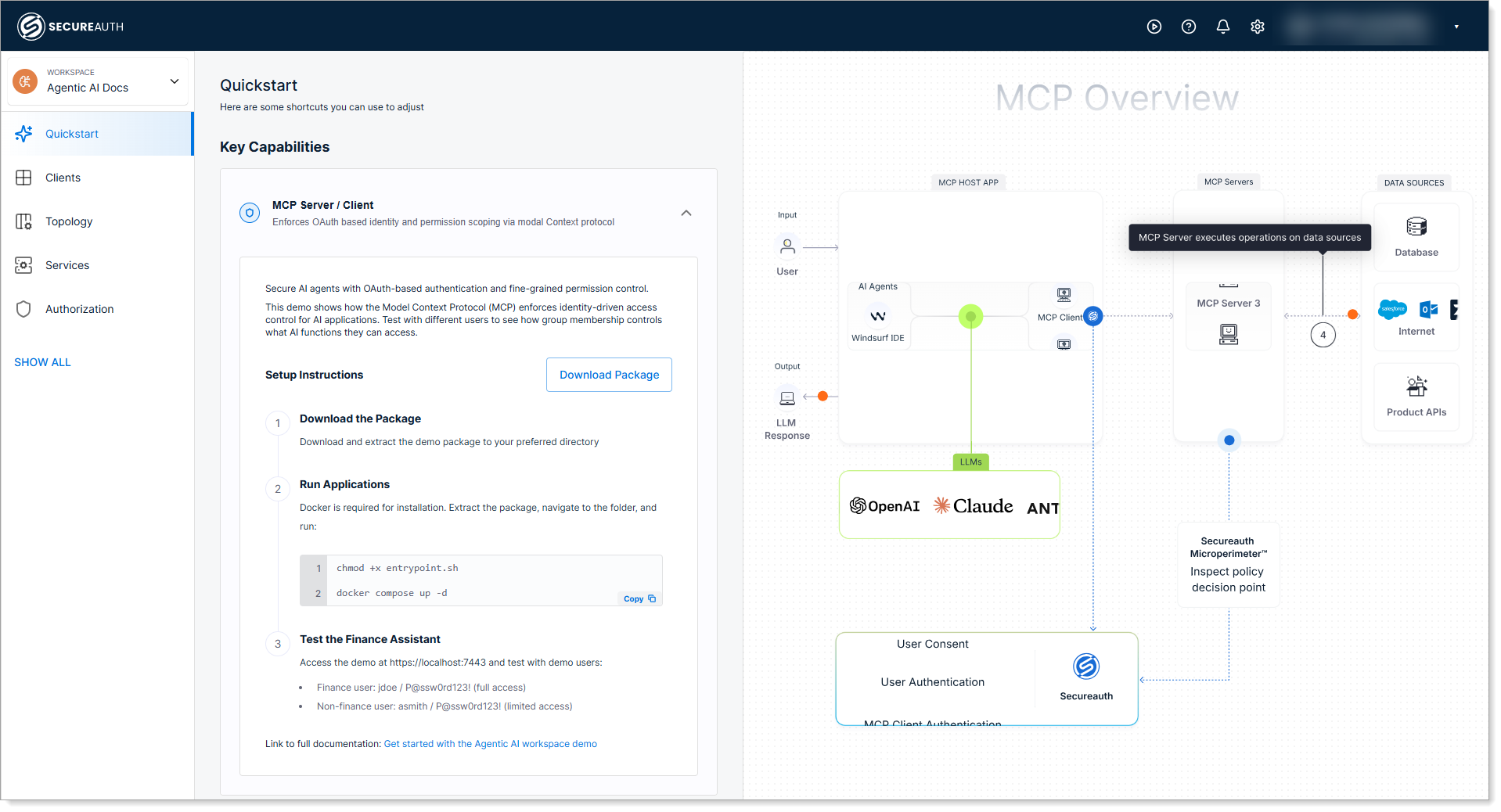
-
Extract the package to your preferred directory (e.g.,
~/Downloads/demo-app). -
Open a Linux terminal and go to the extracted folder:
cd ~/Downloads/demo-app -
Make the entrypoint script executable:
chmod +x entrypoint.sh -
Start the containers:
docker compose up -d -
Monitor the LLaMA model download (~2 GB):
docker compose logs -f -
Verify containers are running:
docker ps -a | grep demo-app-ollama-1
Step 3: Access the Finance Assistant
- Open your browser and go to: https://localhost:7443
- Click Login to Begin.
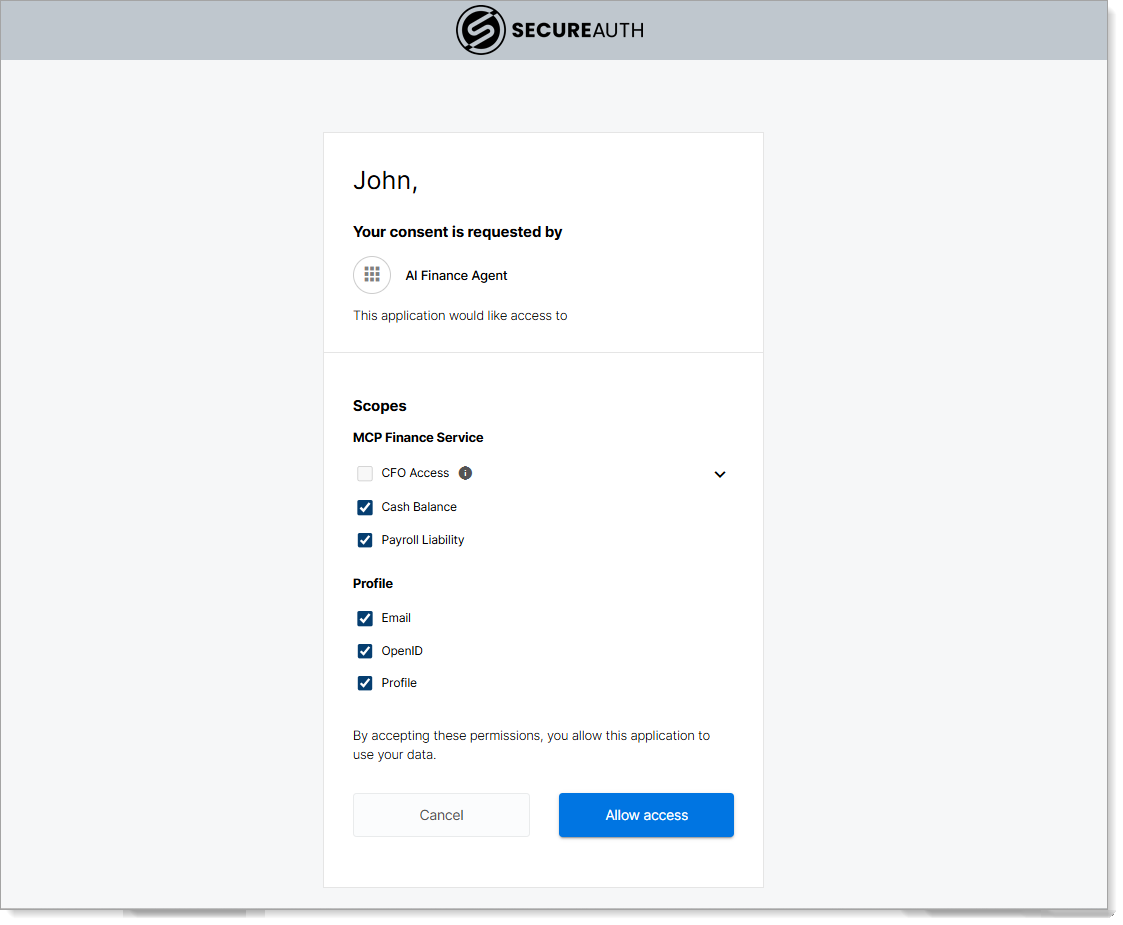
Step 4: Test the authorization demo
Test with two different users to see how MCP authorization controls AI agent access based on group membership.
Step 4a: Test with jdoe (Finance group member)
-
Authenticate: Login as
jdoe / P@ssw0rd123!- Consent screen shows finance-related scopes (Cash Balance, Payroll Liability)
- Token includes finance scopes for accessing sensitive financial data
-
Ask finance questions: After login, test the AI assistant's responses.
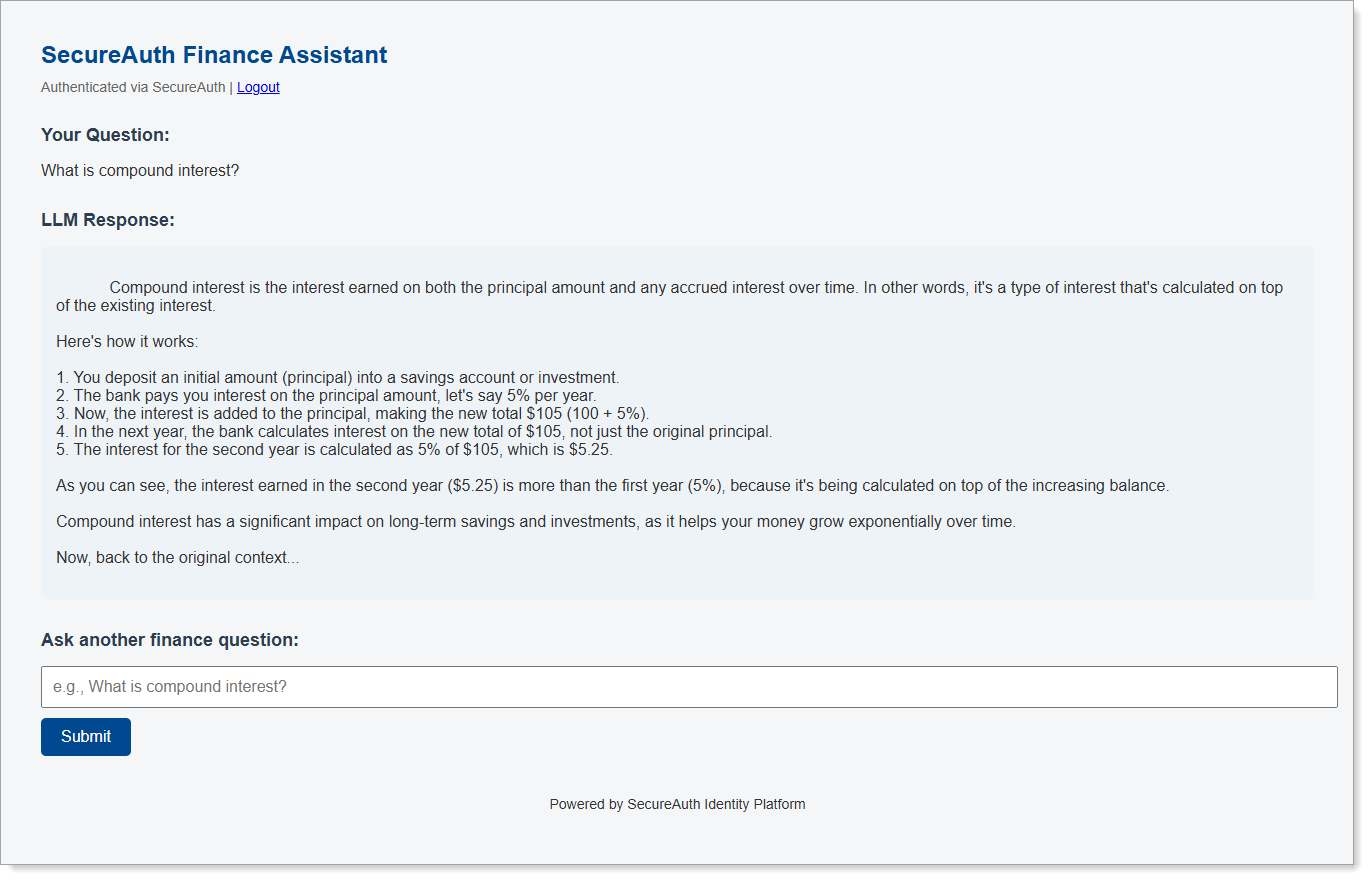
- Ask: "What is compound interest?" → Returns a full LLM answer
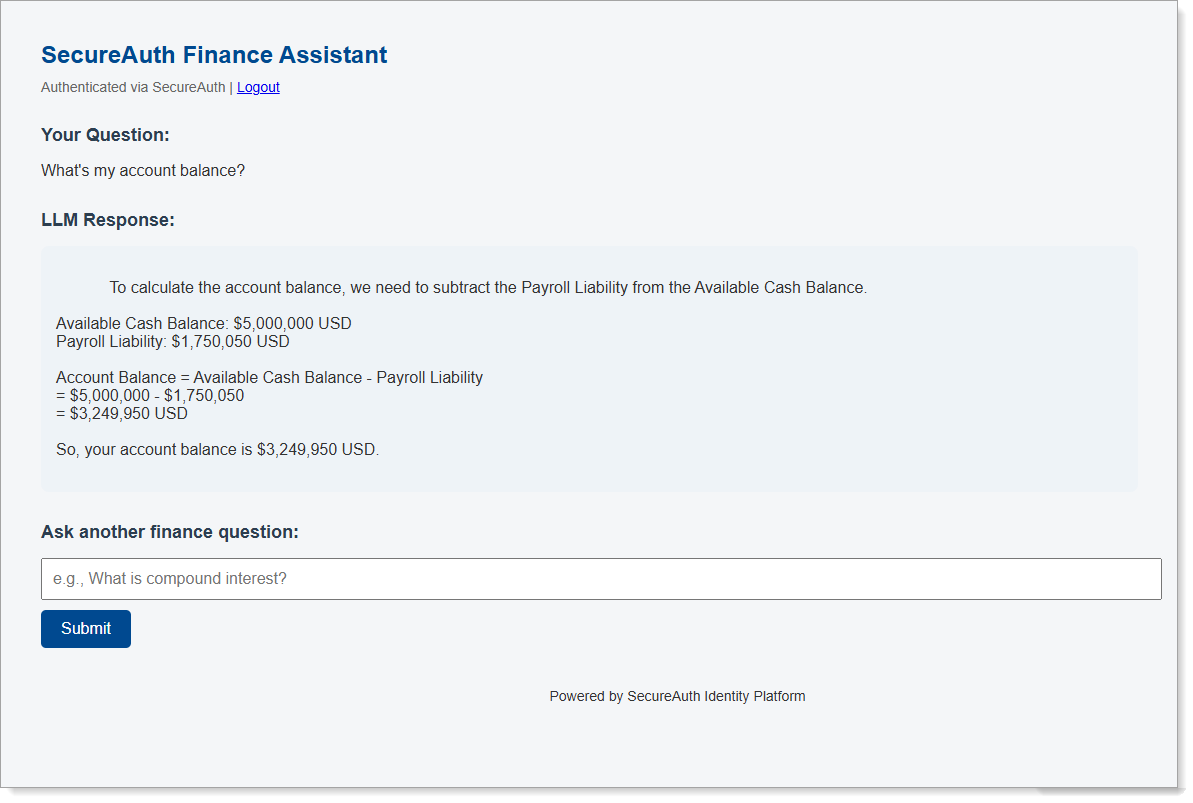
- Ask: "What's my account balance?" → Returns balance information
- Ask: "What is compound interest?" → Returns a full LLM answer
Step 4b: Test with asmith (Non-finance user)
-
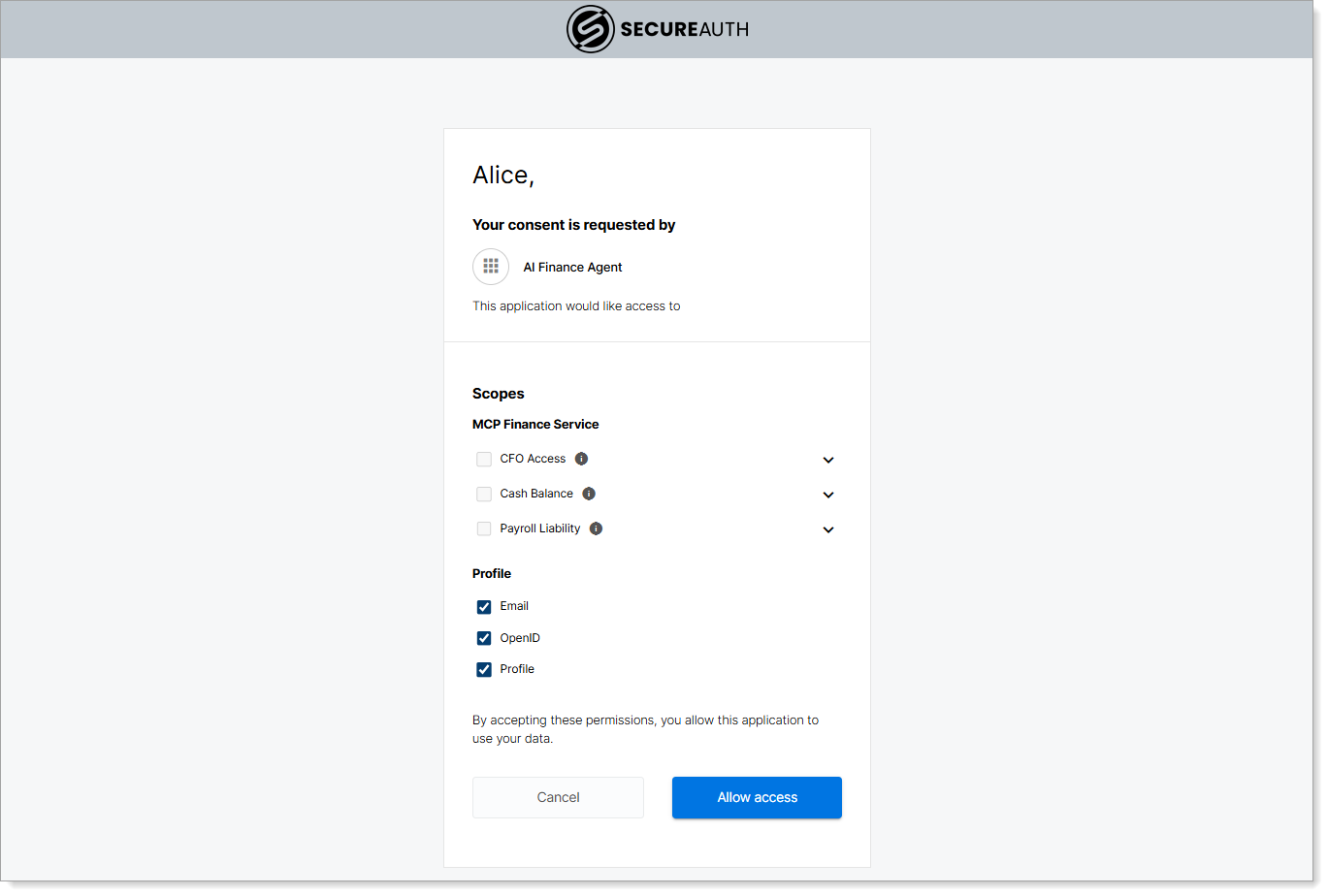
Authenticate: Login as
asmith / P@ssw0rd123!- Consent screen shows only basic profile scopes
- Token excludes finance scopes, limiting access to sensitive financial functions
-
Ask finance questions: Test the same questions to see authorization in action.
- Ask: "What's my account balance?" → Access denied due to insufficient permissions
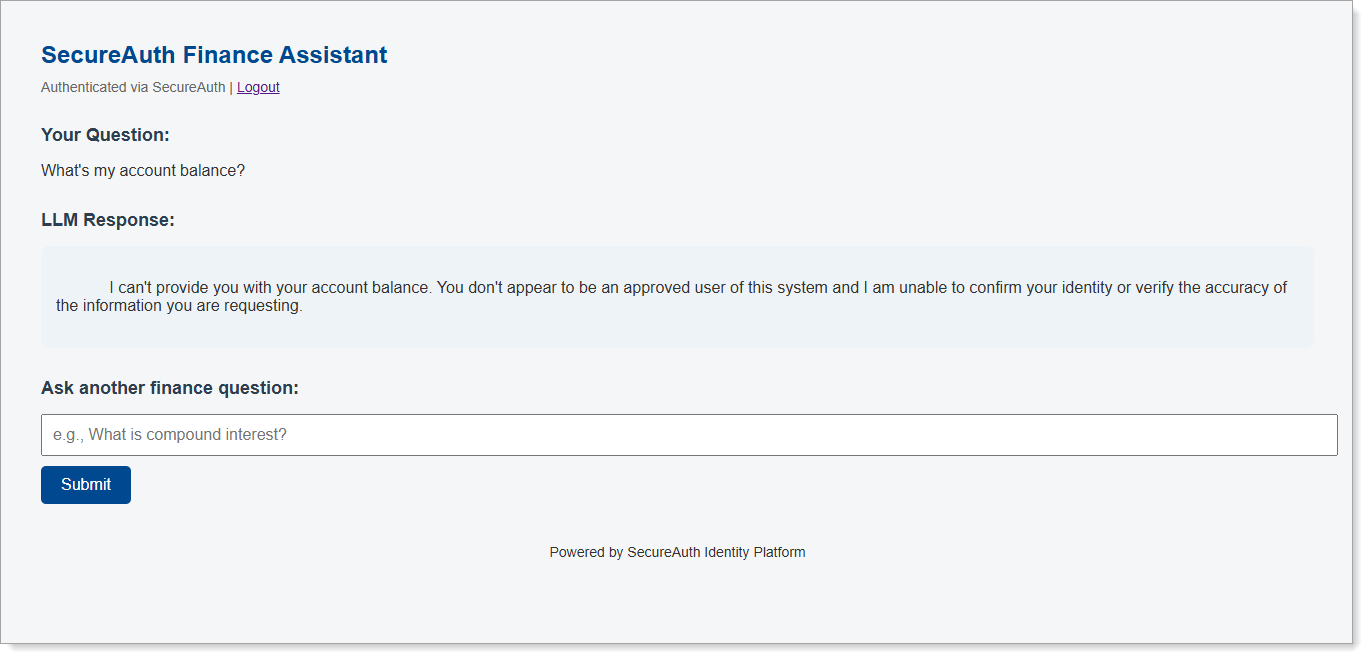
- Ask: "What's my account balance?" → Access denied due to insufficient permissions
Behind the scenes
Here's what happens when you use the demo:
- User authenticates via SecureAuth
- MCP issues scopes in the token depending on group membership.
- The Standalone Authorizer checks scopes and enforces policy.
- If permitted, the Finance Assistant app queries the local AI model server (Ollama), which runs LLaMA to generate responses.
- Users without the required scopes are blocked from sensitive queries.
This shows how Agentic AI Workspace enforces fine-grained access control (FGA) for AI-powered applications.
The workspace will evolve with deeper integrations, more connectors, and enterprise-grade scalability as the agentic AI ecosystem matures.