RADIUS 2FA VAM Deployment Guide
Updated February 18, 2020
The RADIUS 2FA VAM is one of SecureAuth’s value-added modules, a suite of software components developed by SecureAuth to fit the needs of customers seeking a simple way to adapt their system to the SecureAuth solution.
The RADIUS 2FA VAM provides a migration path for customers leading away from RSA security tokens and toward more advanced two-factor authentication (2FA) methods. Customers can continue to use their existing RSA tokens when authenticating to SecureAuth IdP, allowing a phased retirement of the legacy hard-token technology. This gives SecureAuth IdP the ability to validate RSA soft and hard tokens by using the RSA RADIUS Validation client. Because the integration uses RADIUS, the RADIUS 2FA VAM can be used with RSA and other legacy hard-token modules.
This document details the deployment and configuration of the RADIUS 2FA VAM on a SecureAuth IdP appliance. The addition of the RADIUS 2FA VAM in your environment will enable authentication and authorization of applications on RADIUS 2FA.
Some of the benefits of using the SecureAuth RADIUS 2FA VAM include:
Once migrated from RSA, companies experience a dramatically lower administration cost, improved user uptime, and greater satisfaction
Support for RADIUS validation of RSA soft and hard tokens
Support for any vendor that currently uses a non-SecureAuth token and supports a RADIUS client validation process
What's new in version 3.0
RADIUS 2FA VAM version 3 includes the following new MFA methods available for end users:
Personal Identification Number (PIN) mode: End users can log in with an existing PIN or create a PIN to log in.
Token mode: End users are requested a second token as an authentication factor, under certain conditions. This feature includes a new token mode (insert a new token) and next token mode (insert a second token after three wrong attempts).
Use cases
The following are use case examples for the RADIUS 2FA after its deployment.
Use case 1 describes how the following occurs:
After the token is validated, the applications protected by SecureAuth IdP through the RADIUS server are now available to the user.
Use case 2 describes how the following occurs:
The VAM supports a use case where the token is sent through SecureAuth RADIUS Server to the SecureAuth IdP for validation; the RSA token will be routed to the IdP and the VAM will be able to validate both SecureAuth OATH soft tokens as well as RSA hard tokens through the same interface.
Use case 1
After you install and configure the VAM, enter a username and password as usual. A screen like the following is displayed.
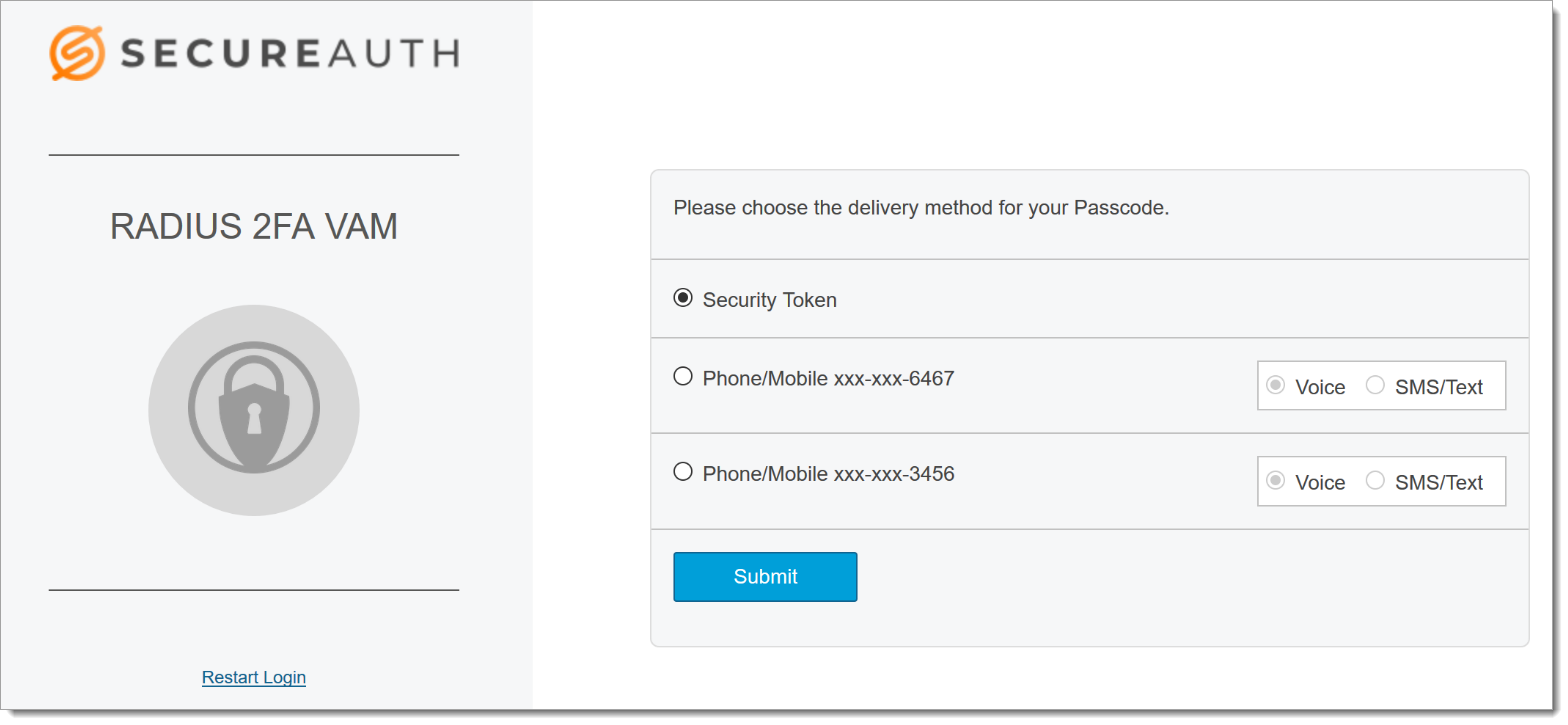 |
After you click Security Token and Submit, a screen like the following is displayed.
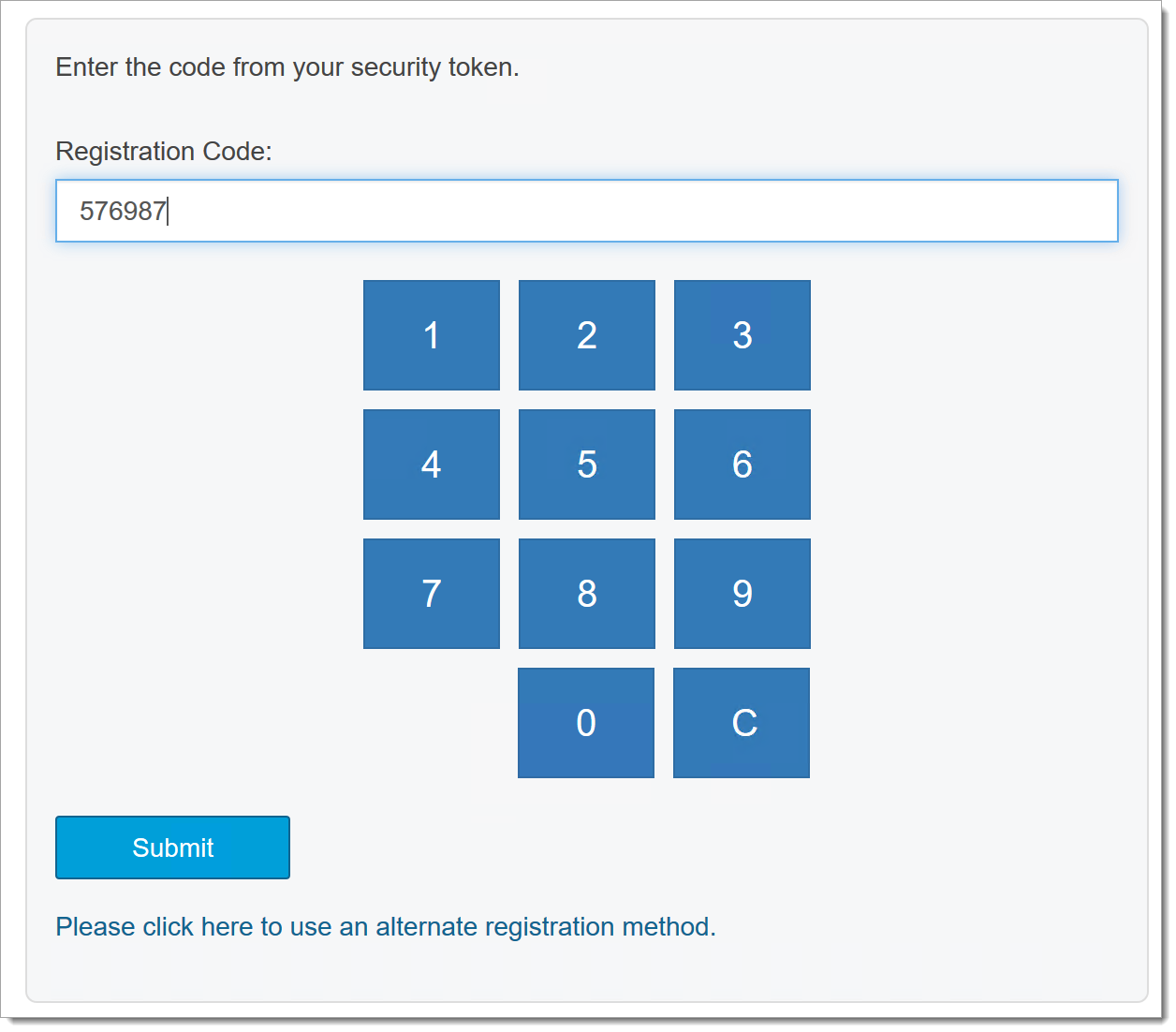 |
Click the buttons to specify the correct security token code and then click Submit.
After the token is validated, the applications protected by SecureAuth IdP through the RADIUS server are now available to the user.
In one example of this workflow, a company possesses both legacy RADIUS servers and Windows servers. Prior to the introduction of this VAM, only the applications connected to the Windows servers would have been available for the advanced authentication techniques offered by SecureAuth IdP; however, with the deployment of the RADIUS 2FA VAM, the RADIUS servers and their allied applications can now use SecureAuth IdP.
Use case 2
In addition to validating the RSA token through the SecureAuth Web UI, the VAM supports a use case where the token is sent through SecureAuth RADIUS Server to SecureAuth IdP for validation.
In this use case, configure the RADIUS client, such as Citrix VPN, to use SecureAuth RADIUS server instead with token validation only. The RSA token will be routed to the IdP and the VAM will validate both SecureAuth OATH soft tokens as well as RSA hard tokens through the same interface.
You can test this use case with NTRadPing, where the RADIUS Server is the IP address of the SecureAuth RADIUS server, and the Password is the RSA Hard Token. You can validate SecureAuth OATH tokens as well.
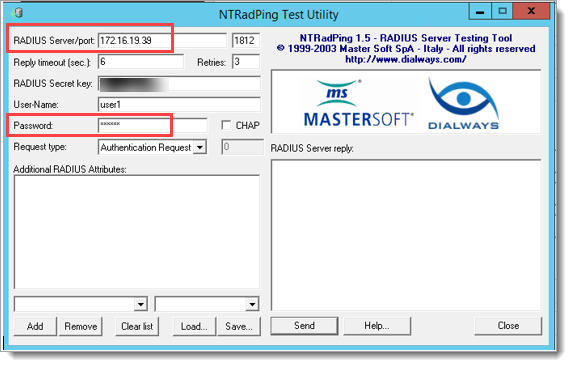 |
To enable this use case, add the following app settings in the web.config:
RADIUSOathTokenField
RADIUSTokenField
The app settings are used to map the authenticated user to other profile properties, if needed. For example, if the RSA Token is sending the sAMAccountName to validate the token but the Authenticated UserID in the realm is mapped to be the UPN, you must map AuxID5 to sAMAccountName to properly send the username that RSA expects for token validation. The following are the mappings:
<add key="RADIUSOathTokenValidationEnabled" value="True" /> <add key="RADIUSOathTokenField" value="AuxID5" /> <add key="RADIUSTokenField" value="AuxID5" />
Workflows
The following are example workflows for RADIUS 2FA basic, and for the new PIN and token methods.
Basic authentication workflow
The following shows an authentication workflow for an end user attempting to open an application through RSA.
An end user attempts to open an application.
The application redirects to SecureAuth IdP.
If the end user is not logged in, SecureAuth IdP prompts the user for userid and password.
The end user enters the credentials and clicks Submit.
The end user is prompted to enter a form of MFA.
The end user chooses the RSA method and enters the code or pin.
SecureAuth IdP validates the code or pin to RSA.
If validation is successful, the end user is redirected to the application.
PIN mode (new PIN)
The following shows an authentication workflow for an end user attempting to open an application by using a new PIN through RSA.
An end user attempts to open an application.
The application redirects to SecureAuth IdP.
If the end user is not logged in, SecureAuth IdP prompts the user for userid and password.
The end user enters the credentials and clicks Submit.
The end user is prompted to enter a form of MFA.
The end user chooses the RSA method.
The end user enters the code.
SecureAuth IdP requests a new PIN.
The end user enters the new PIN.
SecureAuth IdP requests that the end user re-enter PIN.
The end user enters PIN again.
SecureAuth IdP requests that the end user enter a token code + PIN
The end user enters the token code + PIN.
SecureAuth IdP validates the token code + PIN to RSA.
If validation is successful, the end user is redirected to the application.
Token mode (new token)
The following shows an authentication workflow for an end user attempting to open an application by using a new token through RSA.
The end user attempts to open an application.
The application redirects to SecureAuth IdP.
If the end user is not logged in, SecureAuth IdP prompts the end user for userid and password.
The end user enters the credentials and clicks Submit.
The end user is prompted to enter a form of MFA.
The end user chooses RSA method and enters the code.
SecureAuth IdP requests that the end user re-enter new token code.
The end user enters the token code again.
SecureAuth IdP validates the token code to RSA.
If validation is successful, the end user is redirected to the application.
Solution architecture
The essential architecture of the RADIUS 2FA VAM solution is described in the following topology image and description.
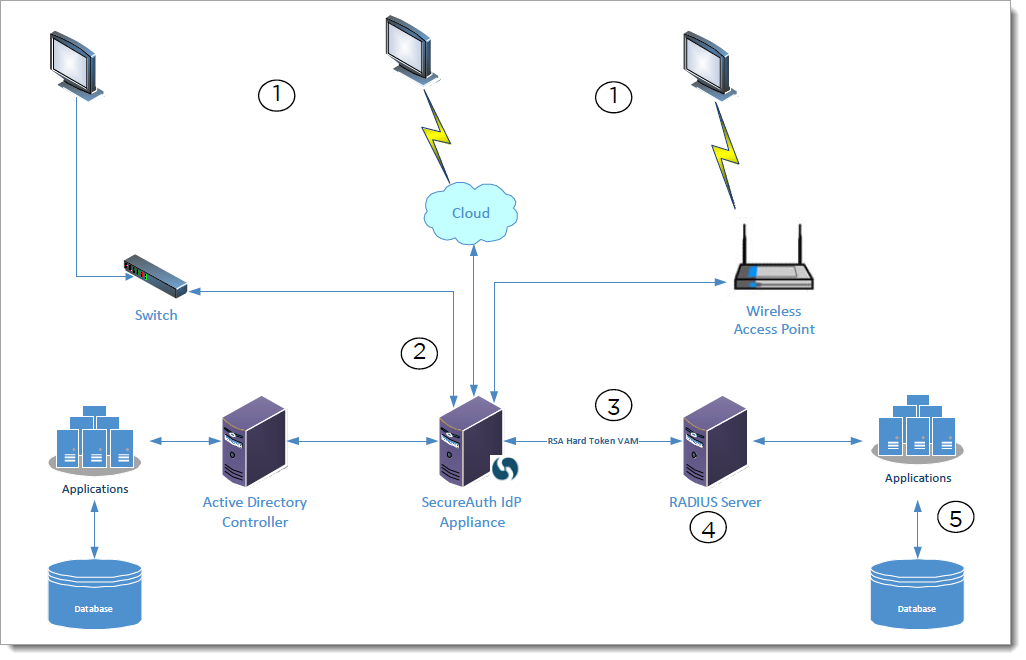 |
The following steps describe the process flow; the step numbers correspond to the circled numbers in the previous image:
An external user enters a well-known application address in a web browser for a federation- or non-federation-aware application using SecureAuth for its main authentication. The application address entered reaches the SecureAuth IdP appliance.
The request is mediated by SecureAuth IdP. The username and password, along with multi-factor authentication, is performed depending on the SecureAuth realm configuration.
During multi-factor authentication, the SecureAuth application validates using a user’s hard token (in the form of a key fob, chip, password + token, password, passcode, or other accepted method).
The validation of the hard token through SecureAuth is a RADIUS request back to the RSA or other token validation system through RADIUS.
The applications and data overseen by the RADIUS server are then made available to the authenticated requester.
While the RADIUS 2FA VAM was designed for use with the RADIUS 2FA, you can use other RADIUS server providers with this VAM, such as Vasco, Defender, and SafeNet.
Prerequisites
The requirements to deploy this VAM include the following:
SecureAuth IdP version 9.2 and later; SecureAuth Identity Platform version 19.07 and later
RADIUS server able to validate the token as specified for the hard token deployment; RADIUS servers such as RSA, Vasco, Defender, or SafeNet
RSA SecurID Token for Windows versions 8.1 and 8.3
Connectivity between SecureAuth IdP appliance and RADIUS server
Download the appropriate version of RADIUS 2FA package. (A version of this package exists for each supported version of SecureAuth IdP.)
Deployment
While there are several ways to deploy the RADIUS 2FA VAM, the procedure in the following sections is the recommended approach.
Best practices
When planning for deployment, keep in mind the following best practices:
Use the RADIUS Test Client to streamline the integration.
Test both the RADIUS server connectivity and token validation using the Test Client before any integration.
For more on the Test Client, see “Testing the RADIUS 2FA VAM Deployment” on page 13.
Specific errors occur with RADIUS server policies in Vasco RADIUS servers. Alleviate problems by using the Test Tool and examining the server logs.
Be sure to download the RADIUS 2FA deployment package from the SecureAuth website that matches your version of SecureAuth IdP.
This VAM currently supports three versions of SecureAuth IdP, but each IdP version has its own “flavor” of the RADIUS 2FA VAM. Check your current SecureAuth IdP version to download the correct VAM version.
Installing the VAM
To configure the SecureAuth IdP RADIUS installation for RADIUS 2FA, perform the following steps.
Download the RADIUS 2FA VAM Deployment Package from the SecureAuth website to an appropriate directory on the hard drive where the SecureAuth IdP client program has been installed.
For the location of this deployment package, contact your Custom Development Sales Engineer.
Uncompress the RADIUS Client Deployment Package. You will see the following subfolders:
Unpack the SecureAuthxx folder.
Copy these files to the targeted realm’s bin folder, such as
SecureAuth1/binorSecureAuth2/bin.Repeat this step for each SecureAuth folder that currently exists, except for the
SecureAuth0folder.
Configuring the VAM
Open the SecureAuth IdP Admin Console by entering the URL on the local machine’s browser: http://localhost:8088/configuration
The admin console user interface can only be viewed on the local machine access.
On the admin console, click the Tools tab and select the Update Web Config option.
In the following screen, click both the Update and Update Resource buttons.
The web config files are updated using the new DLLs you copied to the appropriate folders. After the update is completed, the admin UI is displayed.
In the SecureAuthXX folder, open web.config as administrator, and add the following configuration
In <SectionGroup name=”system.web”>
<section name="oneTimePasswordRadiusService" type="SecureAuth.OTP.Radius.OneTimePasswordConfiguration, SecureAuth.OTP.Radius" allowDefinition="MachineToApplication" />
In key RegMethodOrder add “radius”
<add key="RegMethodOrder" value="Email,..,PushAccept,radius" />
Add the following keys
<add key="RadiusOathTokenValidationEnabled" value="True" /> <add key="RadiusOathTokenField" value="AuxID5" /> <add key="RadiusTokenField" value="AuxID5" /> <add key="msgRADIUSMethod" value="RADIUS Registration Method Selected" /> <add key="RegistrationRadius" value="True" /> <add key="RSATimeout" value="2" />Update the following key with RADIUS option
<add key="RegMethodOrder" value="Email,Help,...,RADIUS" />
Add the RADIUS provider inside <!-- otp--> section
<oneTimePasswordRadiusService> <providers> <clear /> <add description="Radius Server Provider" Authentication_Port="1812" Authentication_Account="1813" Retries="3" Socket_Timout="6000" Hostname="" Shared_Secret="" RadiusClientNAS_IP_Address="" name="OTPRadiusProvider" type="SecureAuth.OTP.Radius" /> </providers> </oneTimePasswordRadiusService>The default settings for the attached RADIUS server are displayed.
Use the following table to change the values in the RADIUS Server Settings section in the image after the table, if needed.
Host Name
Enter the IP address or the server name of the attached RADIUS server
RADIUS Server
Select whether a RADIUS server is enabled for this SecureAuth appliance.
Authentication Port
Enter the port number this appliance will use to authenticate applications overseen by the external RADIUS server gateway.
Authentication Account
Enter the account number needed to verify the RADIUS server authentication.
Retries
Enter the number of timeout errors allowed to access this RADIUS server before the server is locked for a specific amount of time.
Socket Timeout
Enter the number of milliseconds this RADIUS port is allowed to time out before another try is possible.
Shared Secret
Enter the shared secret that enables this appliance to access the RADIUS server.
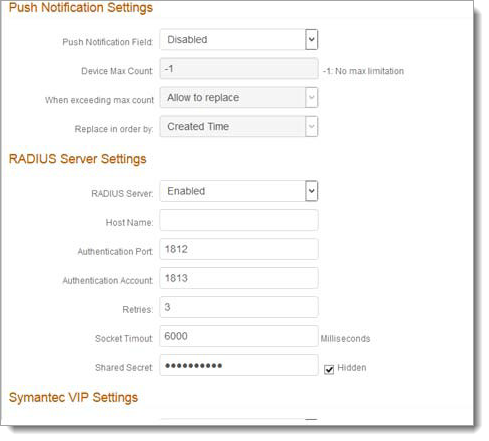
If you updated fields in the previous step, update the configuration accordingly.
SecureAuth IdP is now configured to use a RADIUS-generated hard token as a second-factor authentication.
Resting the RADIUS 2fa VAM deployment
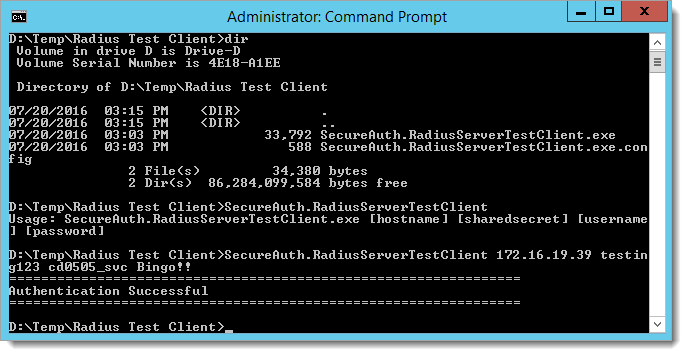
A third component included in the RADIUS 2FA VAM deployment package is the RADIUS Test Client. This command line tool enables you to test the deployment and ascertain whether the VAM configuration is working properly prior to integration.
Place the RADIUS test tool in a directory and extract the files. One of the files is an executable.
Open the command line prompt by typing
cmd. The command prompt dialog box is displayed.Change directory to the directory where you placed the executable, then enter:
SecureAuth.RADIUSServerTestClient [hostname] [sharedsecret] [username] [password]where:
[hostname]Enter the name of the host where the RADIUS server resides
[sharedsecret]Enter the shared secret that enables the RADIUS server to communicate with the client
[username]Enter the name of the user
[password]Enter the password associated with this user
If you enter the executable name only, a list of all parameters supported by this executable is displayed.
The test client runs and shows whether the deployment was successful, as shown in the following example.
Reference
For information about RSA, see Customer Guide to RSA Technical Support:
Upgrade information
Before upgrading SecureAuth software, open a Support ticket. The process of upgrading to a newer SecureAuth software version might cause the SecureAuth VAM to become invalid and stop working. When your site is ready to upgrade SecureAuth software, get started by creating a support ticket selecting I have a question or issue regarding SecureAuth Value-Added Modules (VAMs) from the "Submit a request" list. A SecureAuth Tailoring engineer will contact you to evaluate and ensure that the VAM will work with updated SecureAuth software.