Single Logout (SLO) VAM Deployment Guide
Note
This guide applies only to Identity Platform release 23.07 and earlier.
To enable this feature for Identity Platform release 24.04 or later, see How to configure Single Logout (SLO).
The Single Logout (SLO) Value-Added Module (VAM) provides the SecureAuth® Identity Platform (formerly SecureAuth IdP) with the ability to log out of several service providers using a single logout request, by using the same multisession token. Once you log out of one service provider, it sends a logout request to the Managed Logout page for that realm.
This VAM is added to the SecureAuth Identity Platform appliance using an installer that supplements the appliance with all necessary files and modifies the configurations accordingly.
Architecture
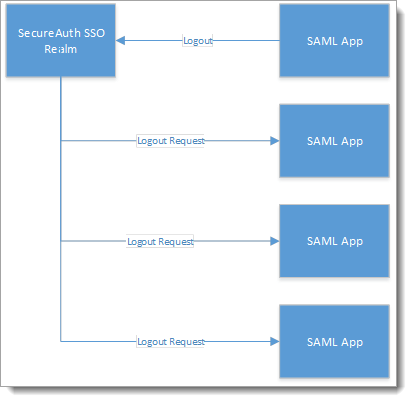
The Managed Logout page constructs a stack of frames for each of the service providers currently logged in with the same multisession token. It then creates an iframe for each of the service providers in the stack. Each of these iframes has a Restart page as the source URL. Each iframe clears out sessions, logs the user out of the SecureAuth realm, and sends a logout request to the corresponding service provider, as shown in the following image.
 |
Installation guidelines
Download the installer for the Single Logout VAM.
Create the Identity Platform realms or know which realms are set up for single logout (SLO) functionality.
System prerequisites
SecureAuth Identity Platform version 9.0 or later.
Using the SecureAuth Identity Platform Web Admin, either create new realms for this process or identify those existing realms designated for single logout (SLO).
Installation
The following is a list of files provided by SecureAuth in the ShareFile link. Copy these files to the SecureAuth realm folder (D:\Secureauth\SecureAuthXX):
../SecureAuthXX/AssertionConsumerService.aspx
../SecureAuthXX/AssertionConsumerService.aspx.vb
../SecureAuthXX/ManagedLogout.aspx
../SecureAuthXX/ManagedLogout.aspx.vb
../SecureAuthXX/Restart.aspx
../SecureAuthXX/Restart.aspx.vb
../SecureAuthXX/Authorized/SAML20IdPInit.aspx
../SecureAuthXX/Authorized/SAML20IdPInit.aspx.vb
../SecureAuthXX/Authorized/SAML20SPInit.aspx
../SecureAuthXX/Authorized/SAML20SPInit.aspx.vb
../SecureAuthXX/Authorized/WSFedProvider.aspx
../SecureAuthXX/Authorized/WSFedProvider.aspx.vb
../SecureAuthXX/Authorized/SAML20IdPInitACS.aspx
../SecureAuthXX/Authorized/SAML20IdPInitACS.aspx.vb
../SecureAuthXX/Authorized/SAML20LogoutService.aspx
../SecureAuthXX/Authorized/SAML20LogoutService.aspx.vb
../SecureAuthXX/Bin/SecureAuth.SingleLogout.dll.
../SecureAuthXX/Bin/MFC.SAML20.dll
Configuration steps
In the web.config, add the following keys in the <appSetting> section for each SecureAuthXX realm.
<add key="SingleLogout" value="True" /> <add key="MultiSessionEnabled" value="True" /> <add key="SingleSessionEnabled" value="False" /> <add key="SSTokenName" value="SSToken" /> <add key="MSTokenName" value="MSToken" /> <add key="LogoutMethod" value="2" /> <add key="CaptureLogoutURL" value="True" /> <add key="LogoutUrl" value="https://URL" /> <add key="LogoutTokenExpiration" value="True" /> <add key="LogoutTokenExpirationTime" value="5" /> <add key="SignLogoutMessage" value="False" />
For more information about the keys, see the following table.
Key | Description |
MultiSessionEnabled | Used if there are multiple service providers, otherwise considered SLO. |
SingleSessionEnabled | Used if there is only one service provider application. |
SSTokenName | This is an arbitrary value used for the name of the single-session cookie. If multiple realms share the same SSTokenName, the last realm from which the user authenticates will be the only session from which the user logs out. |
MSTokenName | This is an arbitrary value used for multisession cookie(s). Multiple realms can use the same MSTokenName to chain together SLO. More than one MSTokenName can exist per appliance. |
LogoutMethod | Directs the logout system to use a specific logout method (for example, SAML or WS-Federation) and how to use it (for example, HTTP-Redirect or POST). The service provider (SP) dictates what is used. Options are:
|
CaptureLogoutURL | Used for WS-Federation or SAML to capture the reply or ACS/Logout URL value dynamically for the logout URL. The SP must provide these values in the initial login request for this feature to work. |
LogoutUrl | Used for a static URL if none is supplied by WS-Fed, or, for example, for SAML 2.0 systems. This is provided by the service provider. |
LogoutTokenExpiration | Use one of the following settings:
|
LogoutTokenExpirationTime | The time (in minutes) after creation the logout token expires when LogoutTokenExpiration is set to True. |
SignLogoutMessage | Directs the system to add a signature to the logout message. |
Note
The Single Logout Configuration page only opens for realms to which the Single Logout module is installed.
Multi-session SLO works only with realms that do not have the HTTP Redirect option in the Logout Method field on the configuration page.
Upgrade information
Before upgrading SecureAuth software, open a Support ticket. The process of upgrading to a newer SecureAuth software version might cause the SecureAuth VAM to become invalid and stop working. When your site is ready to upgrade SecureAuth software, get started by creating a support ticket selecting I have a question or issue regarding SecureAuth Value-Added Modules (VAMs) from the "Submit a request" list. A SecureAuth Tailoring engineer will contact you to evaluate and ensure that the VAM will work with updated SecureAuth software.