Add native or mobile application
Add a native or mobile application to enable secure user authentication on iOS, Android, or desktop devices.
Native and mobile applications use PKCE (Proof Key for Code Exchange) to secure the authentication flow without requiring a client secret.
Before you begin
You'll need:
- Access to your workspace in SecureAuth
- The redirect URI for your application (often a custom URL scheme like
myapp://callback) - Access to your mobile or desktop application code
Add the application
-
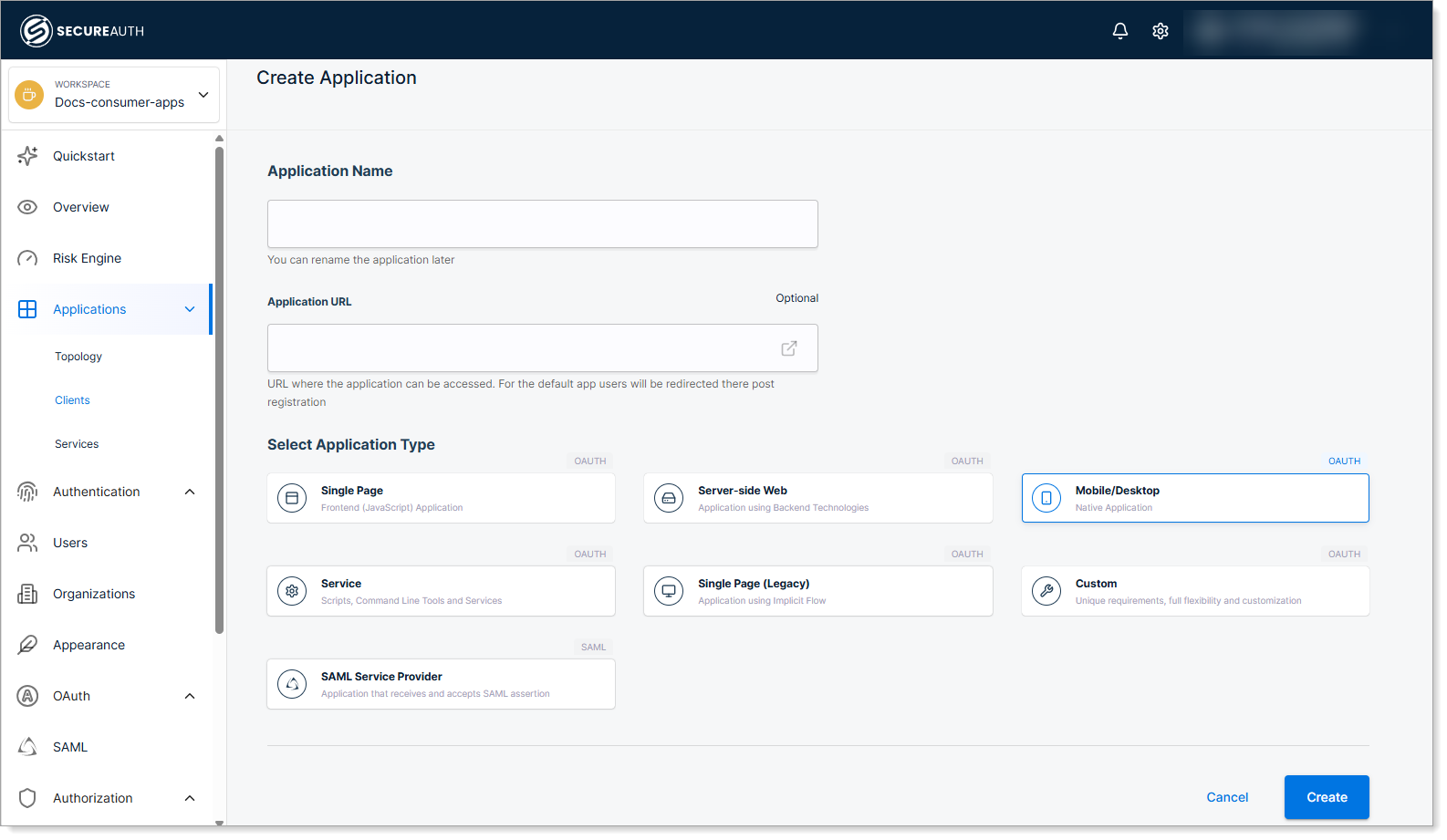
In your workspace, select Applications > Clients > Create client.
-
Enter a name for your application, select the Mobile/Desktop (native) type, and click Create.
-
Configure the Redirect URI for your application.
The redirect URI is where SecureAuth sends users after they log in. For mobile apps, this is typically a custom URL scheme (like
myapp://callback).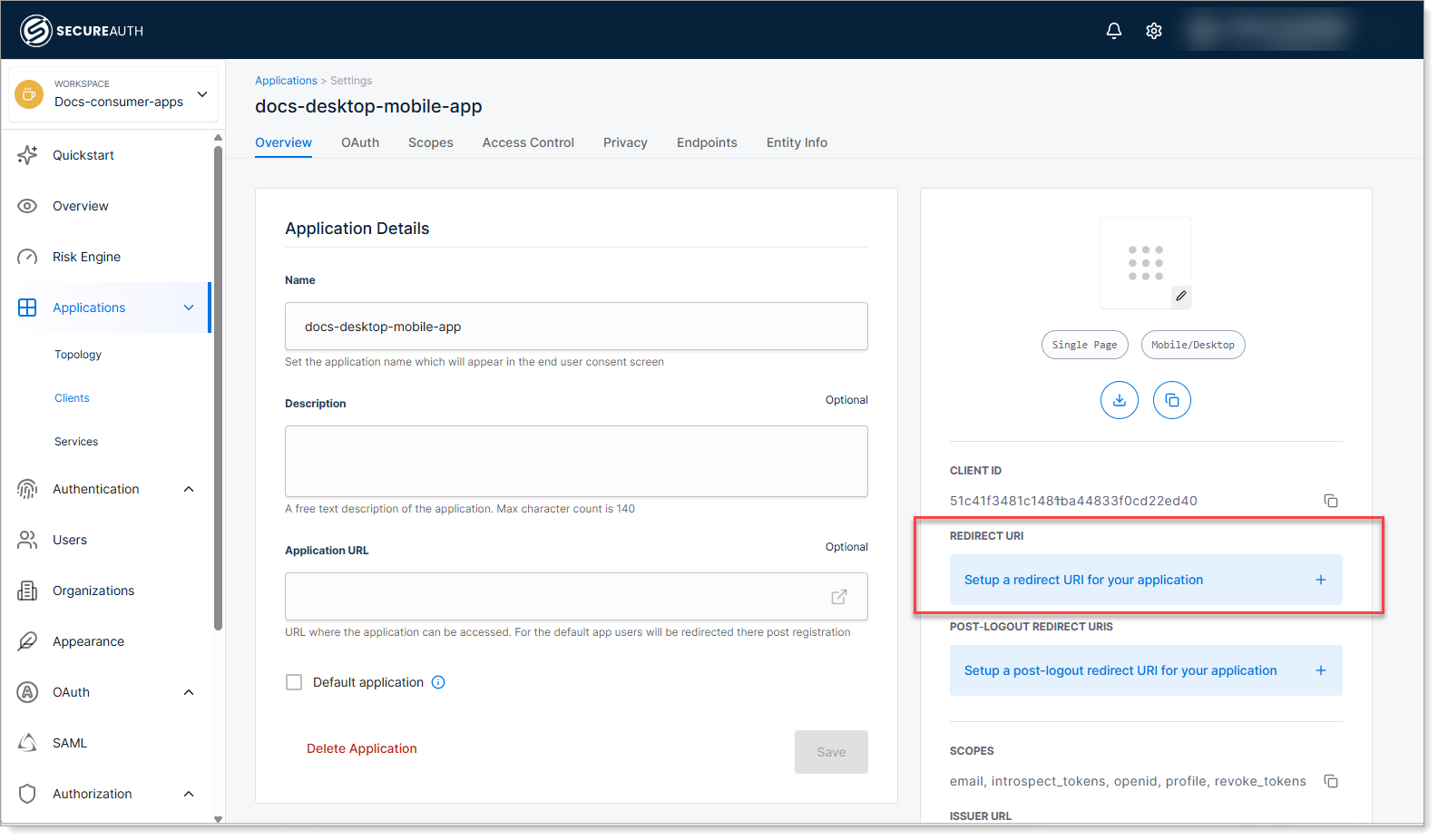
-
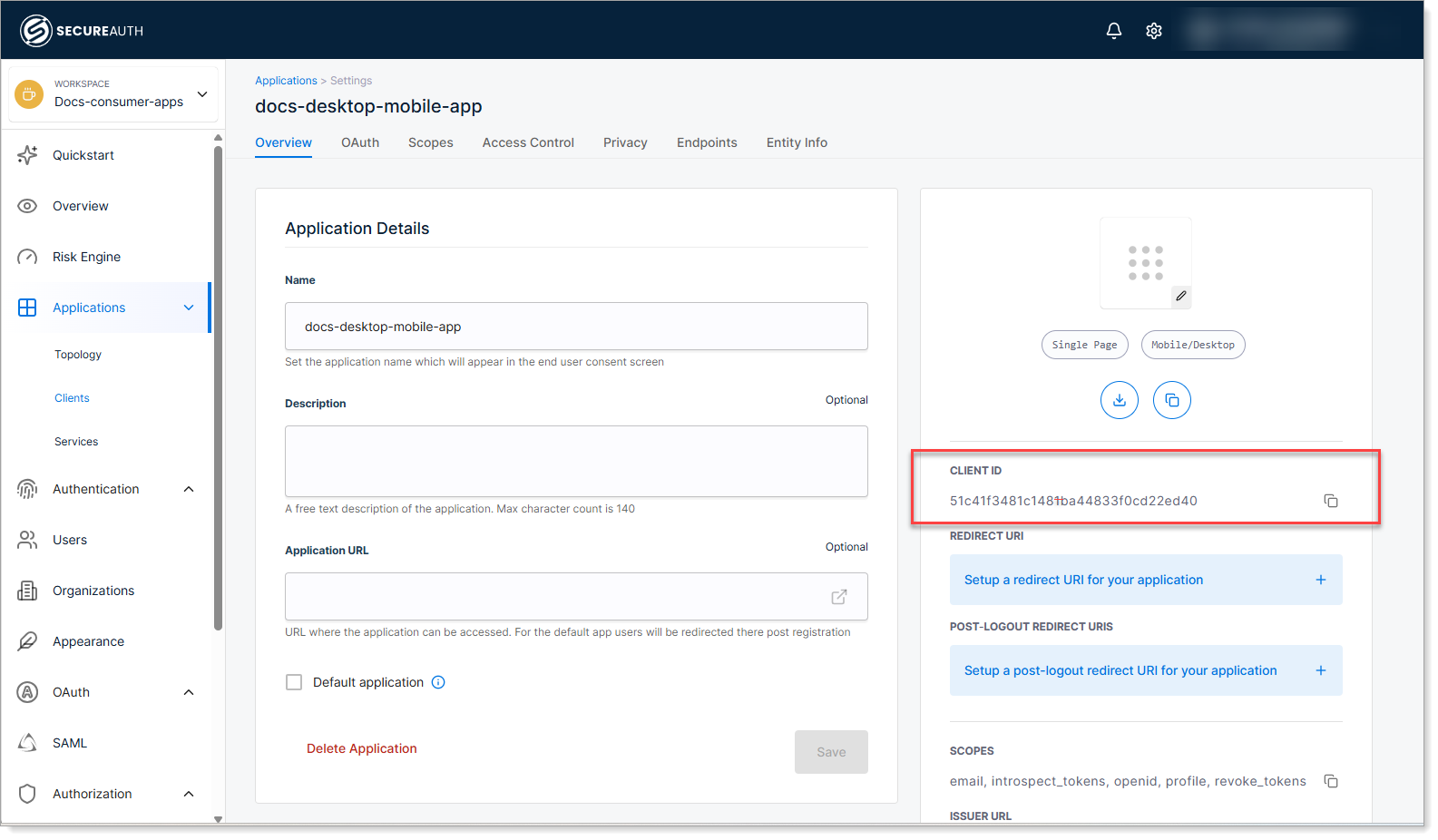
Copy the Client ID and save the configuration.
You'll need the Client ID to connect your application code to SecureAuth. Native and mobile apps do NOT use a client secret for security reasons.
Integrate with your application
After creating the client in SecureAuth, integrate it with your native or mobile application code using an OAuth/OIDC library that supports PKCE.
Example: iOS with AppAuth
// Install AppAuth: pod 'AppAuth'
import AppAuth
let configuration = OIDServiceConfiguration(
authorizationEndpoint: URL(string: "https://YOUR_TENANT.YOUR_REGION.connect.secureauth.com/YOUR_TENANT/YOUR_WORKSPACE/oauth2/authorize")!,
tokenEndpoint: URL(string: "https://YOUR_TENANT.YOUR_REGION.connect.secureauth.com/YOUR_TENANT/YOUR_WORKSPACE/oauth2/token")!
)
let request = OIDAuthorizationRequest(
configuration: configuration,
clientId: "YOUR_CLIENT_ID",
scopes: ["openid", "profile", "email"],
redirectURL: URL(string: "myapp://callback")!,
responseType: OIDResponseTypeCode,
additionalParameters: nil
)
let appDelegate = UIApplication.shared.delegate as! AppDelegate
appDelegate.currentAuthorizationFlow = OIDAuthState.authState(
byPresenting: request,
presenting: self
) { authState, error in
if let authState = authState {
print("Got authorization tokens. Access token: \(authState.lastTokenResponse?.accessToken ?? "none")")
} else {
print("Authorization error: \(error?.localizedDescription ?? "unknown error")")
}
}
Example: Android with AppAuth
// Add to build.gradle: implementation 'net.openid:appauth:0.11.1'
import net.openid.appauth.*
val serviceConfig = AuthorizationServiceConfiguration(
Uri.parse("https://YOUR_TENANT.YOUR_REGION.connect.secureauth.com/YOUR_TENANT/YOUR_WORKSPACE/oauth2/authorize"),
Uri.parse("https://YOUR_TENANT.YOUR_REGION.connect.secureauth.com/YOUR_TENANT/YOUR_WORKSPACE/oauth2/token")
)
val authRequest = AuthorizationRequest.Builder(
serviceConfig,
"YOUR_CLIENT_ID",
ResponseTypeValues.CODE,
Uri.parse("myapp://callback")
).setScopes("openid", "profile", "email")
.build()
val authService = AuthorizationService(this)
val authIntent = authService.getAuthorizationRequestIntent(authRequest)
startActivityForResult(authIntent, AUTH_REQUEST_CODE)
Example: React Native with react-native-app-auth
// Install: npm install react-native-app-auth
import { authorize } from 'react-native-app-auth';
const config = {
issuer: 'https://YOUR_TENANT.YOUR_REGION.connect.secureauth.com/YOUR_TENANT/YOUR_WORKSPACE',
clientId: 'YOUR_CLIENT_ID',
redirectUrl: 'myapp://callback',
scopes: ['openid', 'profile', 'email'],
};
const authResult = await authorize(config);
console.log('Access Token:', authResult.accessToken);
You can use any OAuth library that supports the Authorization Code flow with PKCE.
Test the integration
- Launch your application on a device or emulator.
- Trigger the login flow.
- Verify that users are redirected to SecureAuth for authentication.
- After logging in, confirm users are redirected back to your application.
Next steps
- Restrict access with user policies to control who can use the application
- Set up single sign-on (SSO) by connecting external identity providers
- Skip the consent screen for your own applications
- Enable passwordless authentication for a better user experience