Configure the Level of Assurance (LOA) threshold
The Level of Assurance (LOA) threshold determines the confidence level required for authentication. If your users' real-time LOA falls below the threshold you set, they must verify their identity with a second factor.
-
Go to Sign-in and Sign-up settings.
-
Tenant level: Go to Tenant Settings (gear icon) > Identity Pools > [Selected Identity Pool] > Sign-in and Sign-up.
-
Workspace level: In your workspace, go to Users > Sign-in and Sign up.
-
-
Expand the Sign-in section and locate the Level of assurance threshold setting.
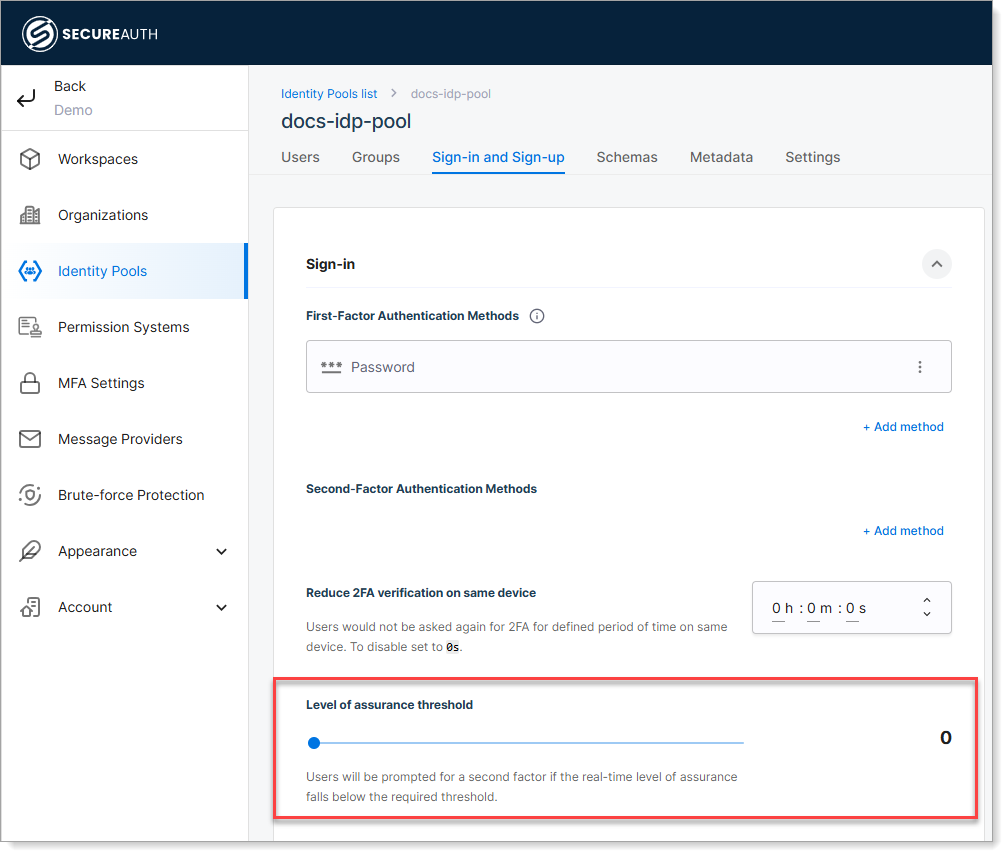
-
Adjust the slider to set the required confidence level.
For guidance on choosing a threshold level, see Understanding LOA threshold levels below.
To learn more about how the risk engine calculates LOA, see Risk Engine: Smarter security in action and Risk analyzers.
-
Save your changes.
Understanding LOA threshold levels
The LOA threshold you set determines how often users are prompted for additional authentication. Choose a level that balances your security requirements with user convenience.
| Level | When to use | User experience | Security considerations | Best for |
|---|---|---|---|---|
| Low (30%) - Minimal Security | You prioritize user convenience over strict security. | Rare MFA prompts, even from new devices. | Users may be new or logging in from unknown devices with minimal additional verification. | Public-facing apps, convenience-focused applications |
| Medium (60%) - Balanced Security | You need moderate security for standard business use. | MFA required for suspicious activity, but trusted devices build confidence over time. | Moderate confidence level. Repeated logins from the same device increase LOA over time. | Standard business applications |
| High (80%) - Maximum Security | You require strong security for sensitive data or compliance. | Frequent MFA prompts until strong device trust is established. | Strong assurance in user identity based on comprehensive device characteristics and behavior patterns. | Sensitive data access, compliance environments |
How LOA works
The risk engine continuously evaluates user behavior and device characteristics:
- New users/devices: Start with lower LOA scores
- Trusted patterns: LOA increases with consistent, safe behavior
- Suspicious activity: LOA decreases, triggering MFA requirements
- Device recognition: Familiar devices gradually build higher confidence
Best practices
Security recommendations
- Start conservative: Begin with medium (60%) and adjust based on user feedback
- Monitor patterns: Review authentication logs to optimize threshold settings
- Consider user types: Different user groups may need different LOA requirements
User experience considerations
- Communicate changes: Inform users about new security measures
- Provide alternatives: Ensure multiple MFA options are available
- Monitor support requests: Watch for increased authentication-related help desk tickets
Troubleshooting
Common issues
| Issue | Symptom | Solution |
|---|---|---|
| Too many MFA prompts | Users complain about constant authentication | Lower the LOA threshold or check risk analyzer sensitivity |
| Insufficient security | Unauthorized access from suspicious sources | Raise the LOA threshold and review risk engine settings |
| Inconsistent behavior | MFA requirements seem random | Review risk analyzer configuration and device trust policies |
Monitoring and adjustment
- Review authentication logs weekly for the first month after changes
- Survey users about authentication experience
- Adjust thresholds based on security incidents and user feedback
- Monitor LOA scores to understand typical user patterns