Microsoft Entra ID Configuration
Use this guide to configure Microsoft Entra ID in the Entra ID admin center to allow read and optional write access for SecureAuth Connect integration.
After you complete this configuration, you can integrate it with SecureAuth Connect.
Prerequisites
Before you begin, ensure you have:
- Application Administrator account in Microsoft Entra ID
- Administrative access to the Entra ID admin center
Set up admin privileges in Microsoft Entra ID
To grant access to users in Microsoft Entra ID, you assign Microsoft Entra roles. A role is a collection of permissions.
You will need a Microsoft Entra ID user account with an assigned role of Application administrator on the Directory scope.
To assign this role to a user:
-
Log in to the Microsoft Entra ID admin center as at least a Privileged Role Administrator or Global Administrator.
-
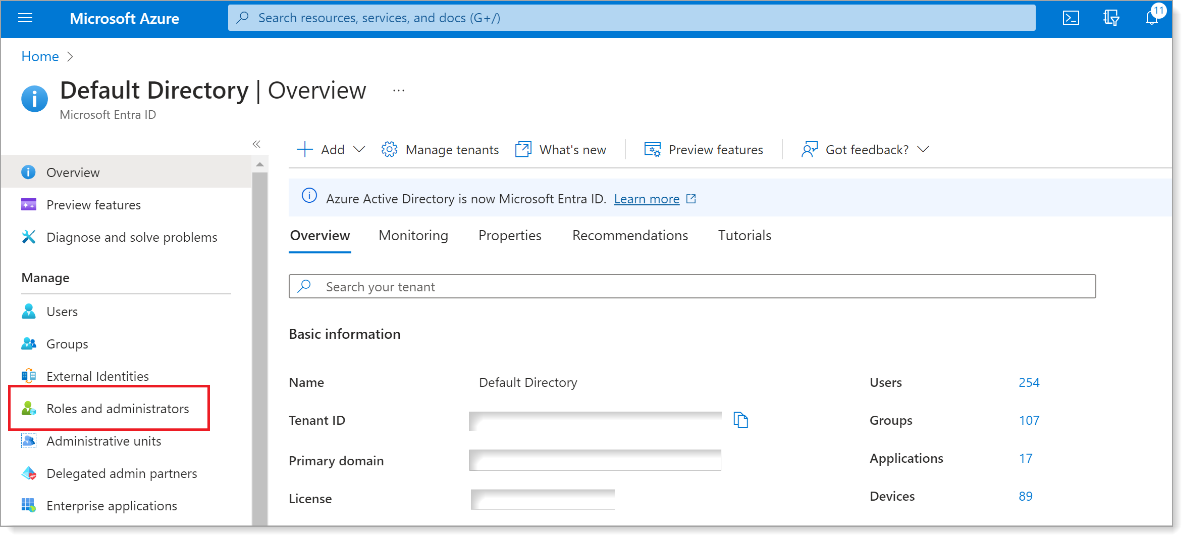
Go to the Microsoft Entra ID directory and from the left navigation, click Roles and administrators.
-
Search for and select the Application Administrator role.
-
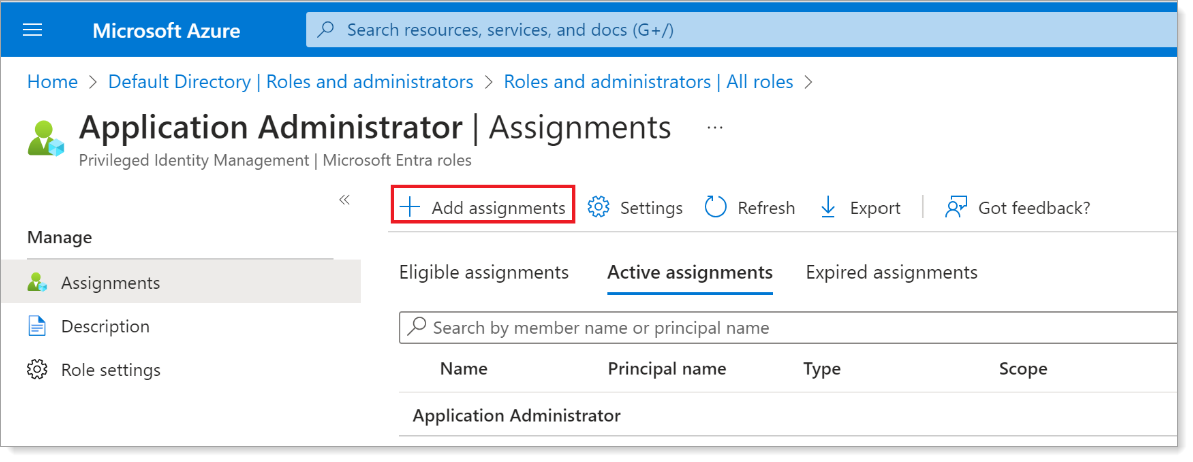
Click Add assignments.
-
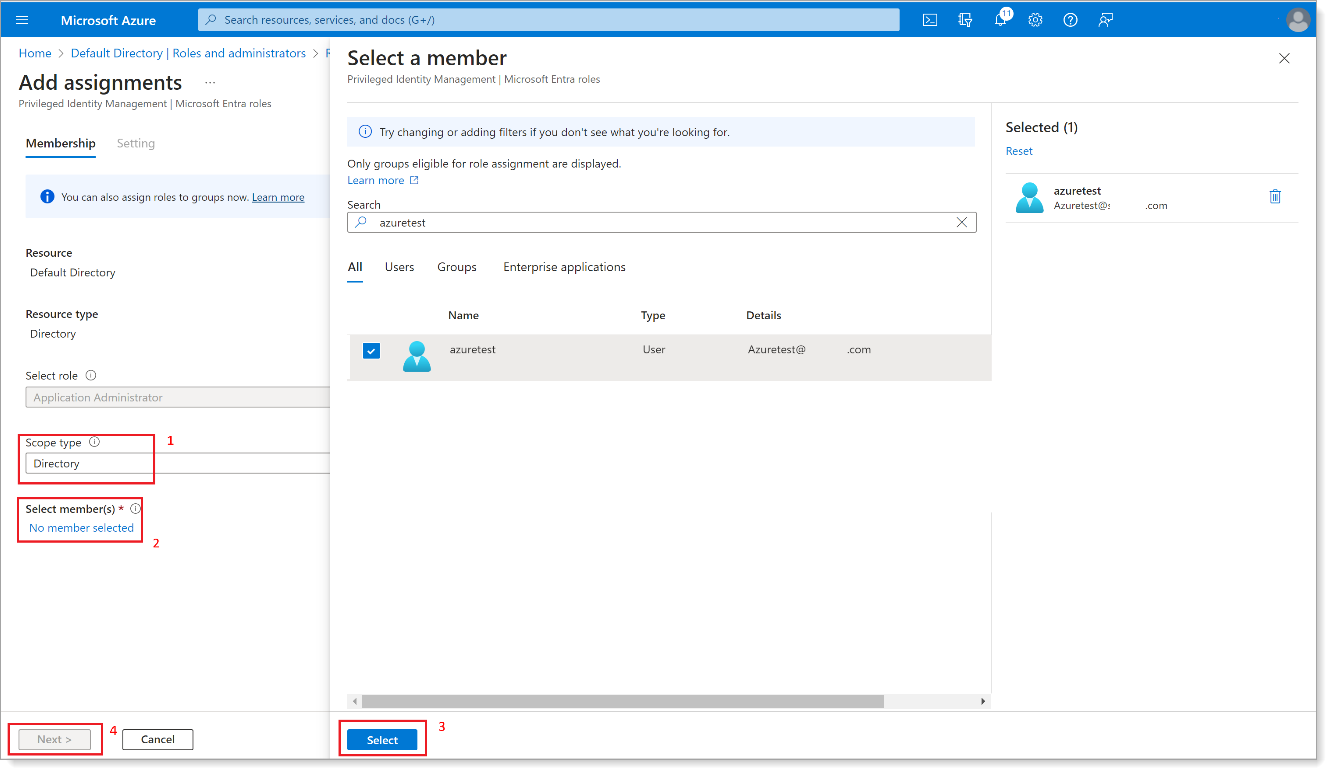
In the left navigation, set the Scope type to Directory. Then, select a user as a member and click Next.
-
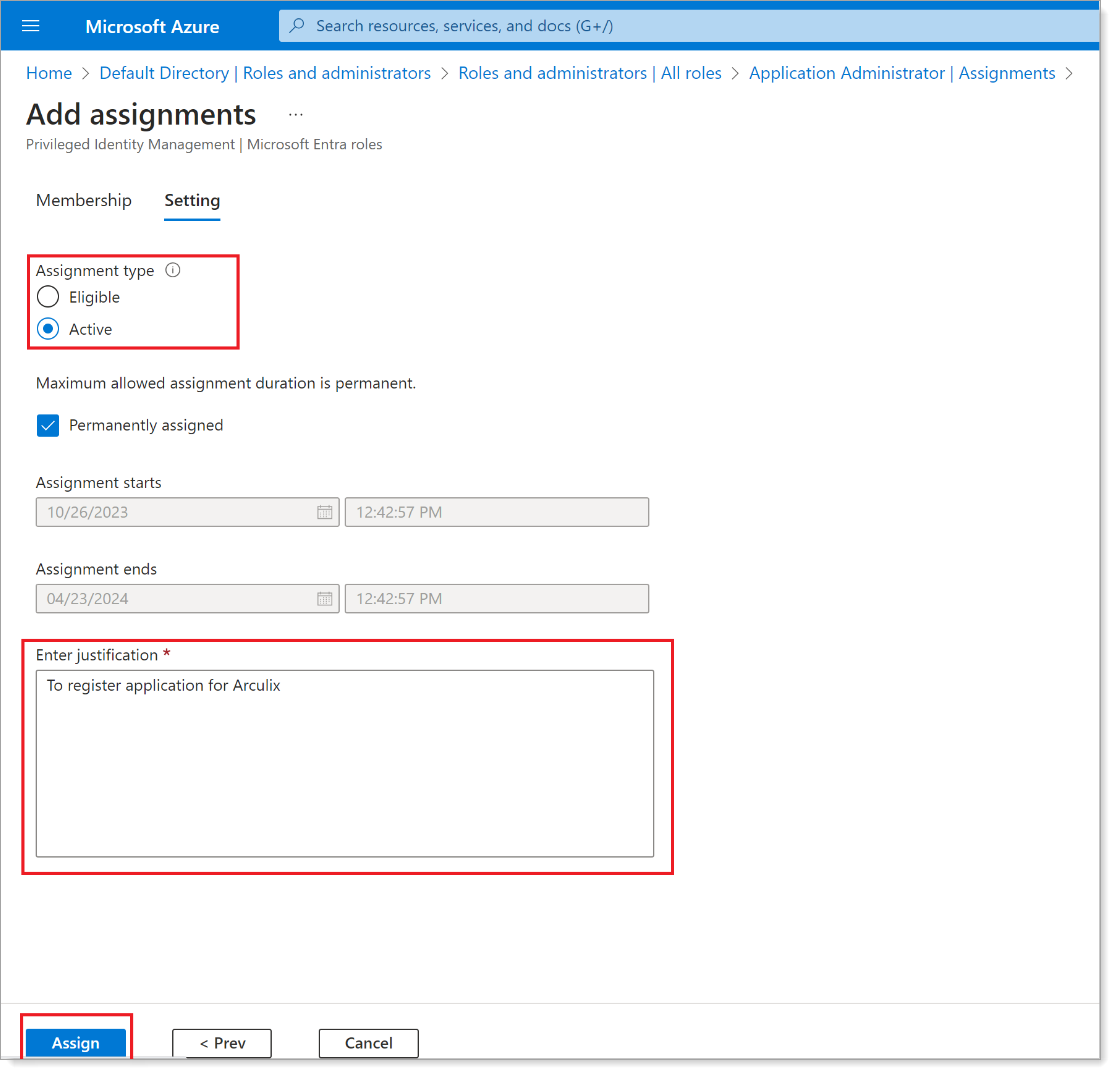
Set the Assignment type to Active, enter the justification, and click Assign.
Process
To configure Microsoft Entra ID for SecureAuth Connect in the Entra ID admin center, complete these tasks:
- Task A: Register an application for SecureAuth Connect
- Task B: Add API permissions for SecureAuth Connect
- Task C: Create the client secret
- Task D: Get registered application information
Task A: Register an application for SecureAuth Connect
To integrate Microsoft Entra ID with SecureAuth Connect, you need to register an application in the Entra ID admin center.
-
Log in to your Entra ID Account through the Entra ID admin center.
-
Select Microsoft Entra ID.
-
Select App registrations and click New registration.
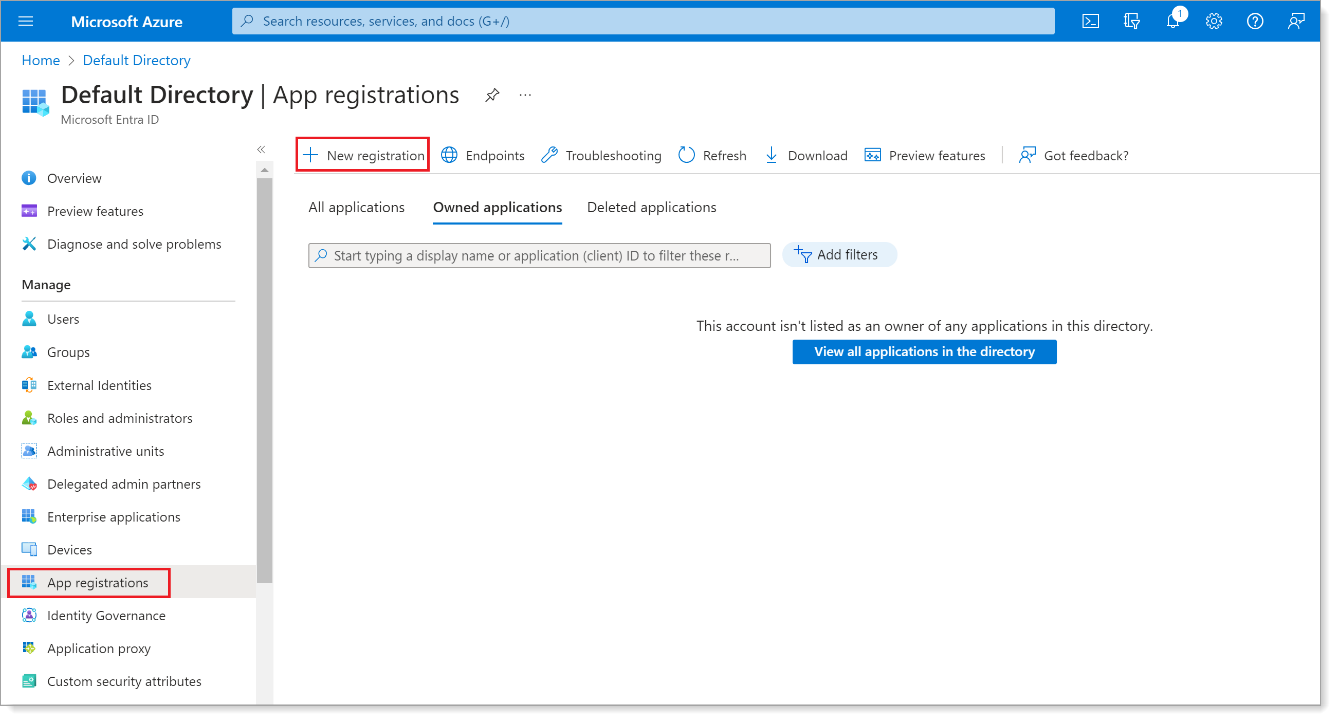
-
Set a Name and keep the default Supported account types setting, wihch is a single tenant.
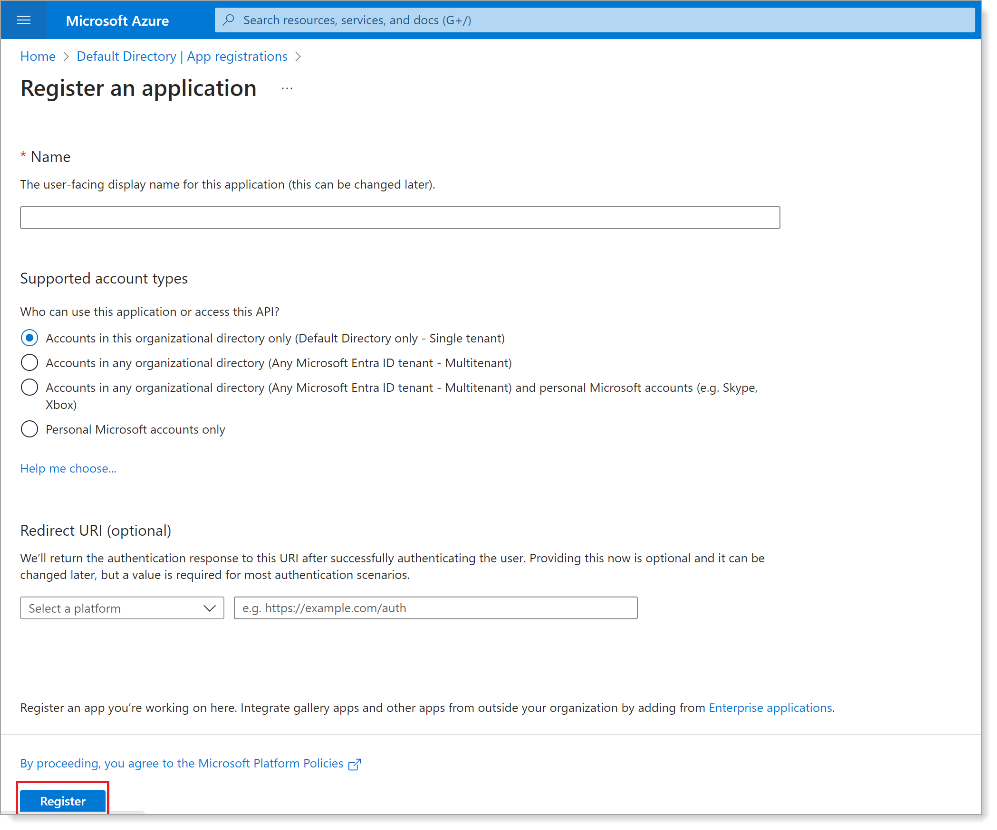
-
Click Register.
Task B: Add API permissions for SecureAuth Connect
Grant read and write permissions for the SecureAuth Connect API calls to Microsoft Entra ID..
-
From the App registrations list, click name of the registered app that you just created.
-
In the left pane, click API Permissions. Then, click Add a permission.
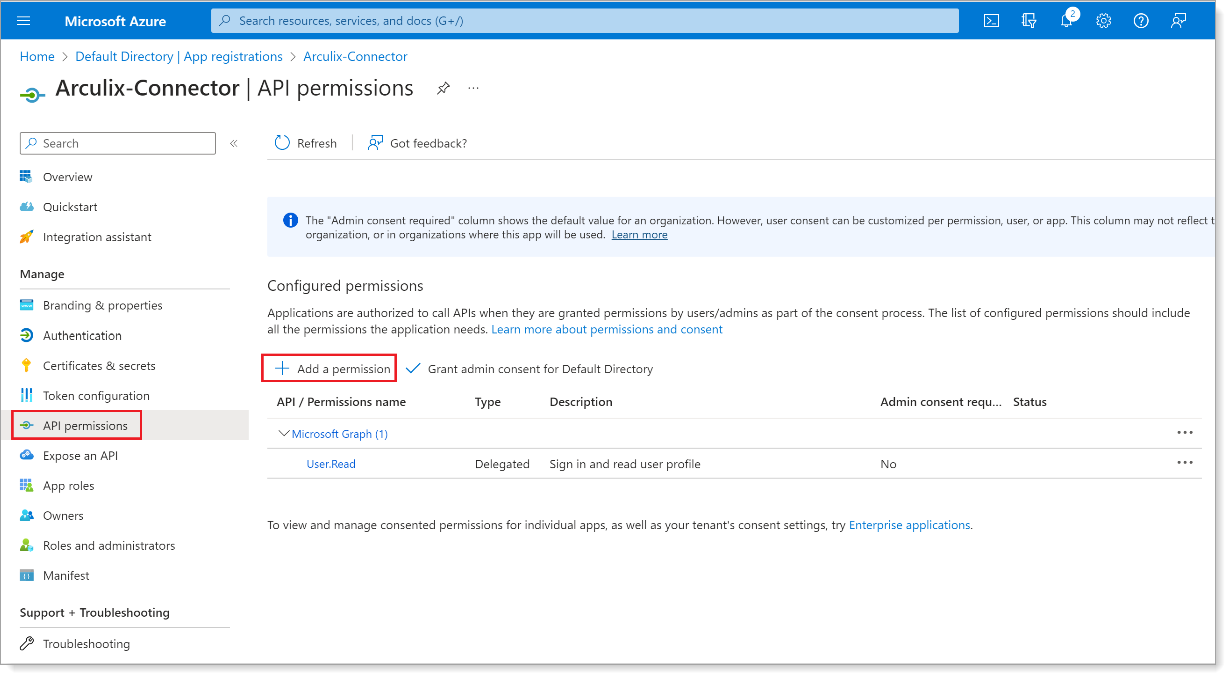
-
Select Microsoft Graph.
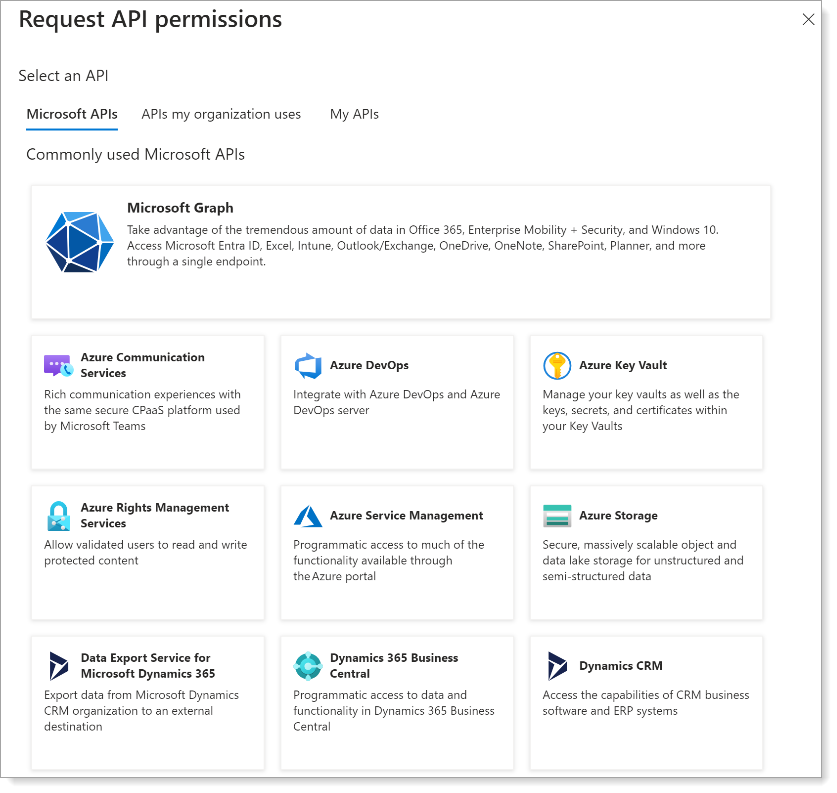
-
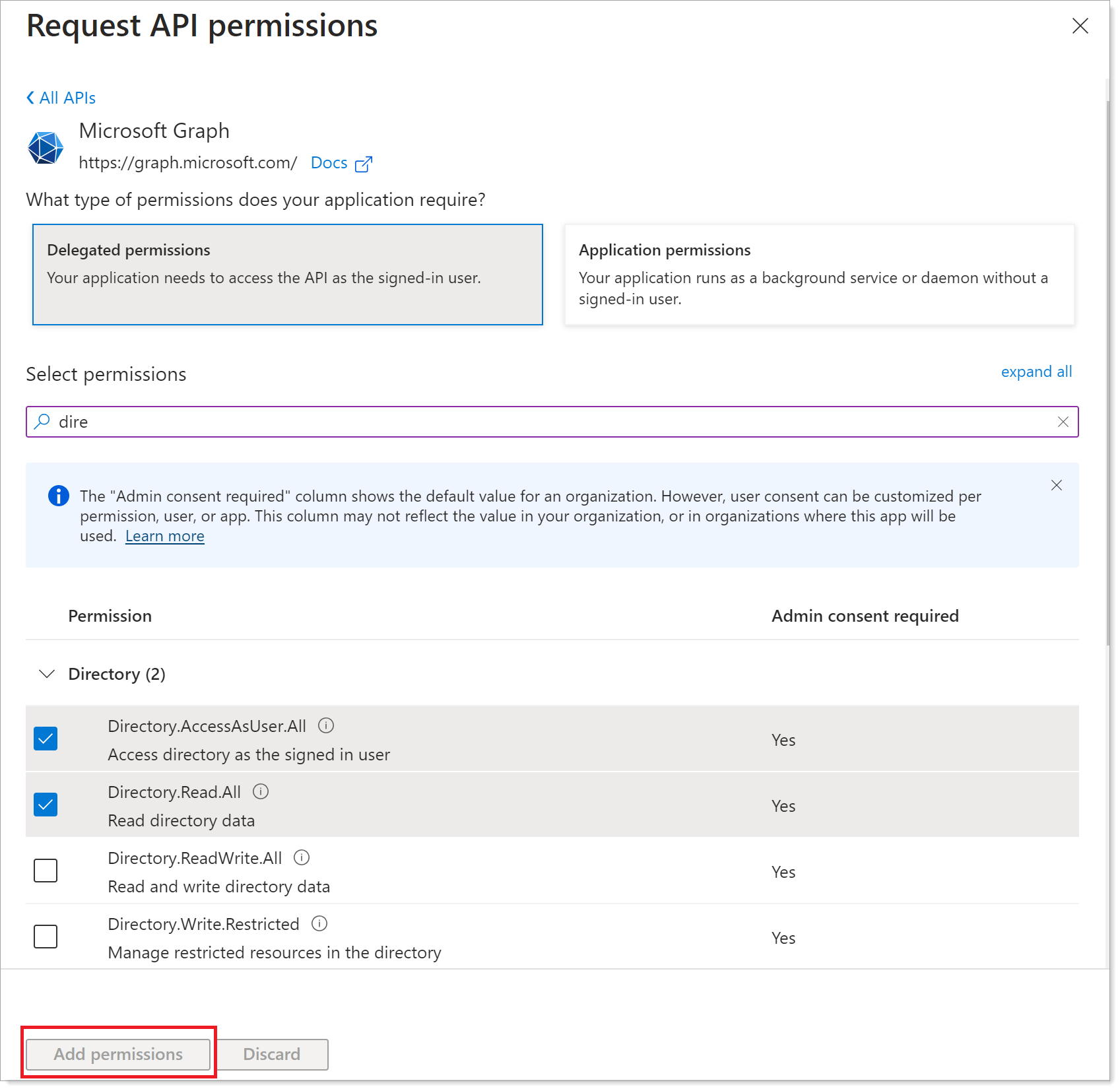
Click Delegated permissions. Scroll down to find and select the following check boxes:
- Directory.AccessAsUser.All
- Directory.Read.All
- Group.Read.All
- User.Read
- User.Read.All
-
After selecting delegated permissions, scroll to the bottom of the page and click Add permissions.
-
Click Add a permission again and select Microsoft Graph.
-
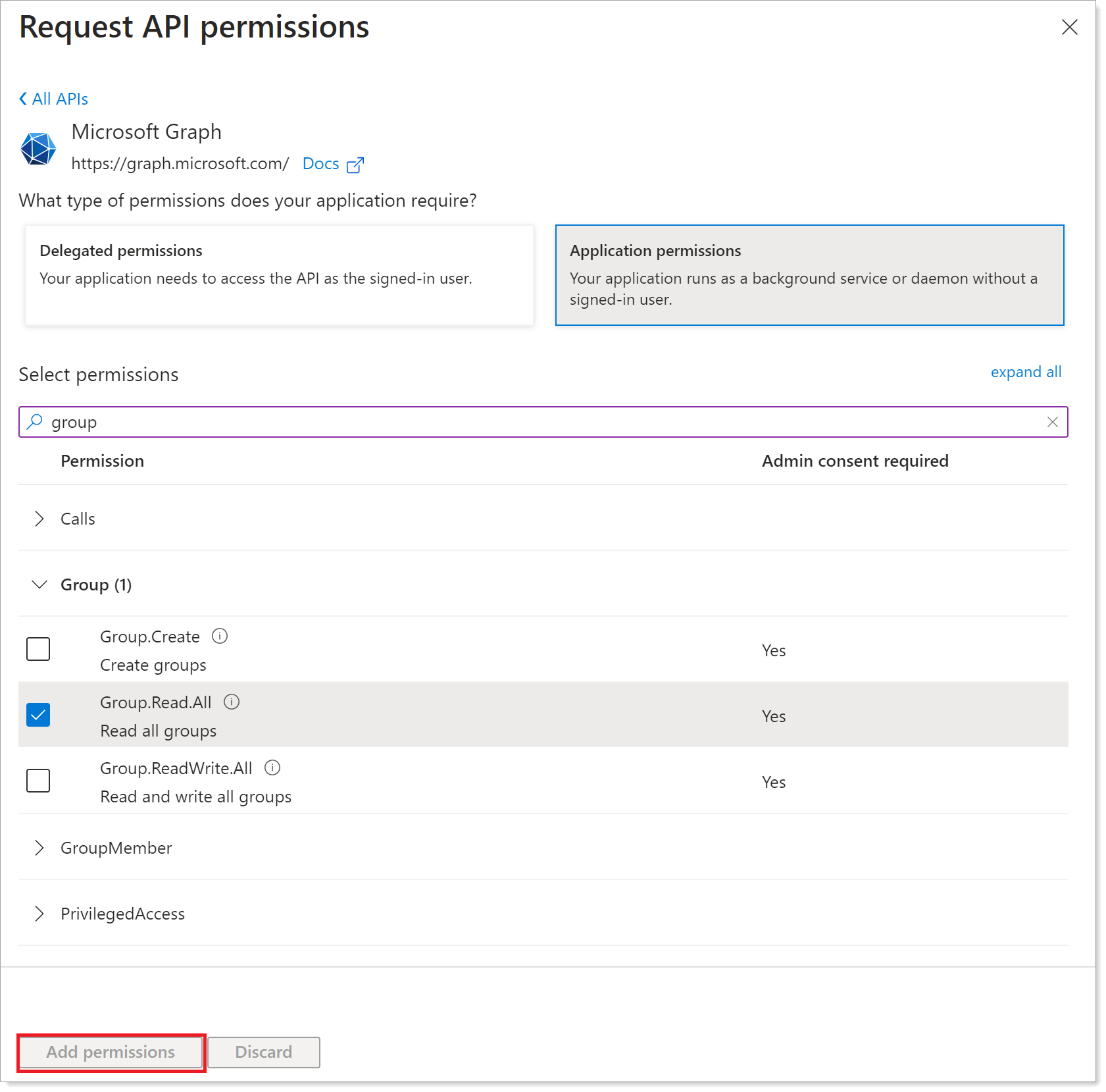
Click Application permissions. Scroll down to find and select the following check boxes:
- Directory.Read.All
- Group.Read.All
- User.Read.All
-
After selecting delegated permissions, scroll to the bottom of the page and click Add permissions.
-
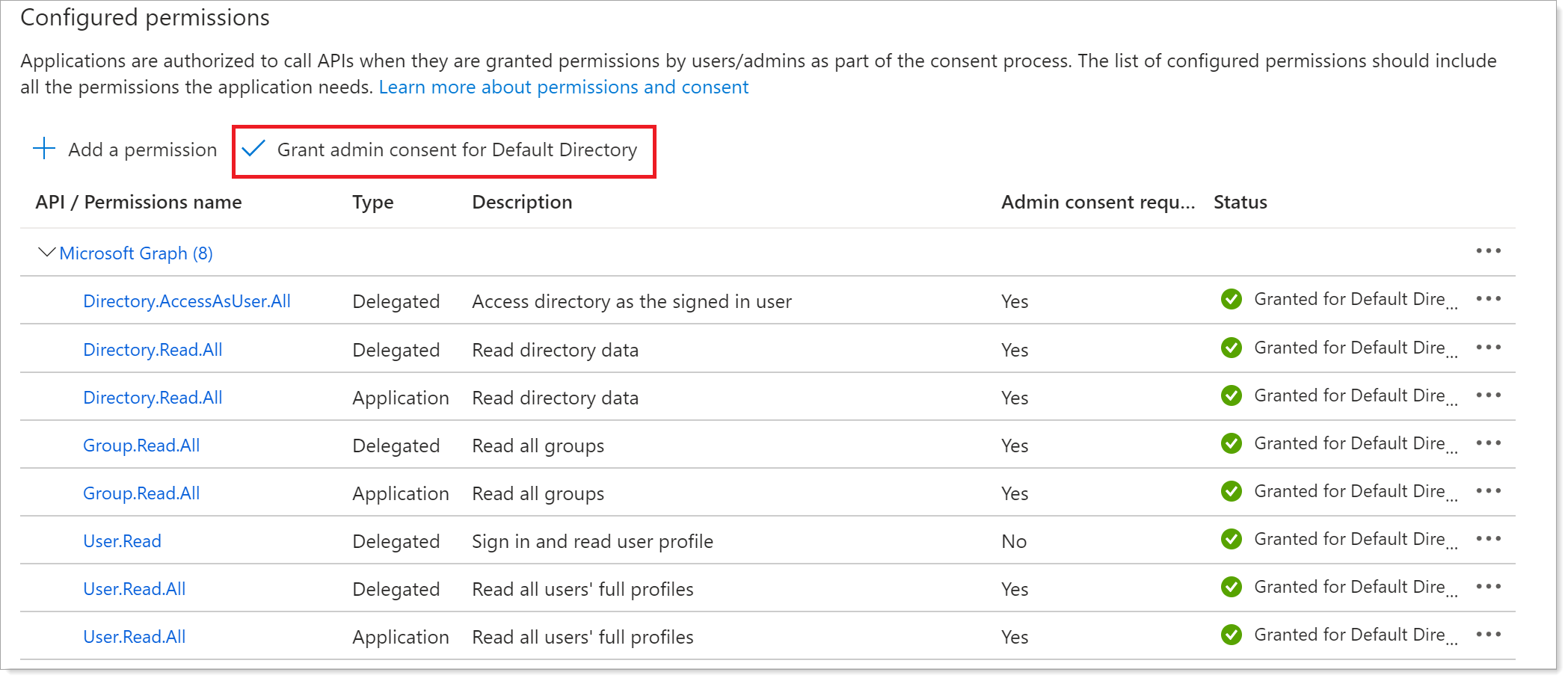
Verify the permissions you added and click Grant admin consent.
Task C: Create the client secret
Create an application secret key for the SecureAuth Connect connection to Microsoft Entra ID. You will need to provide this client secret when configuring the connection in SecureAuth Connect.
-
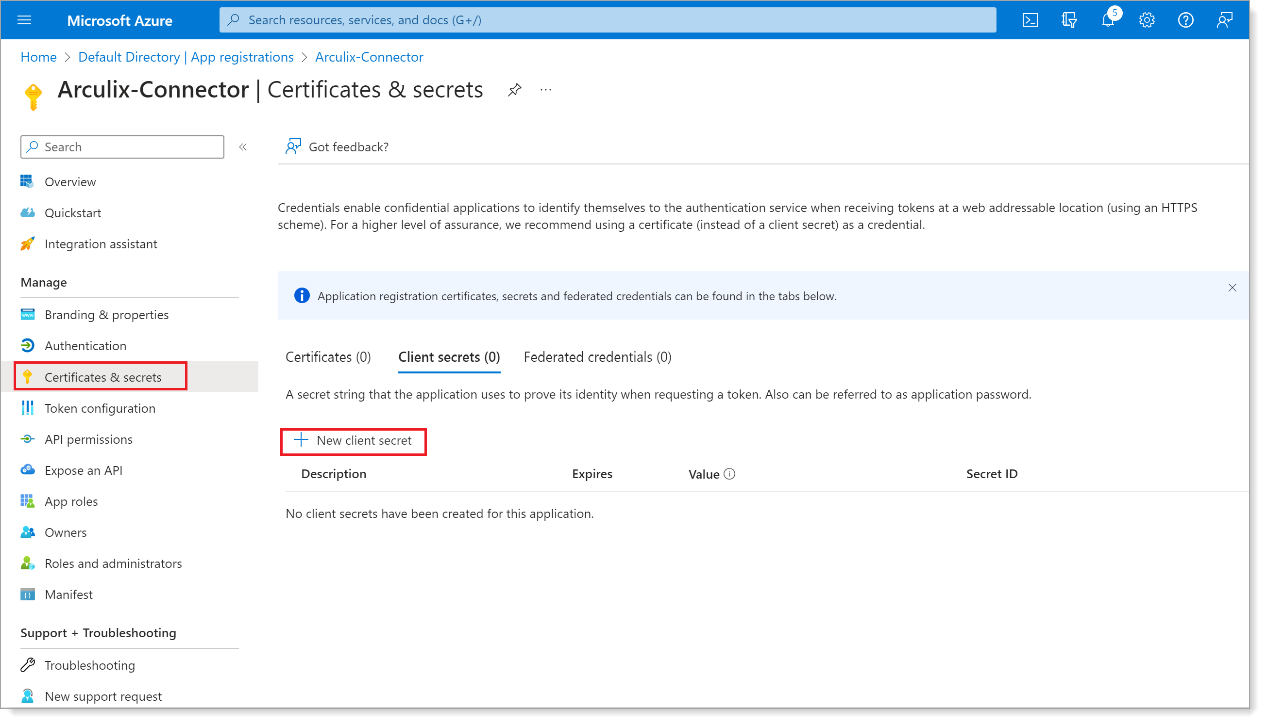
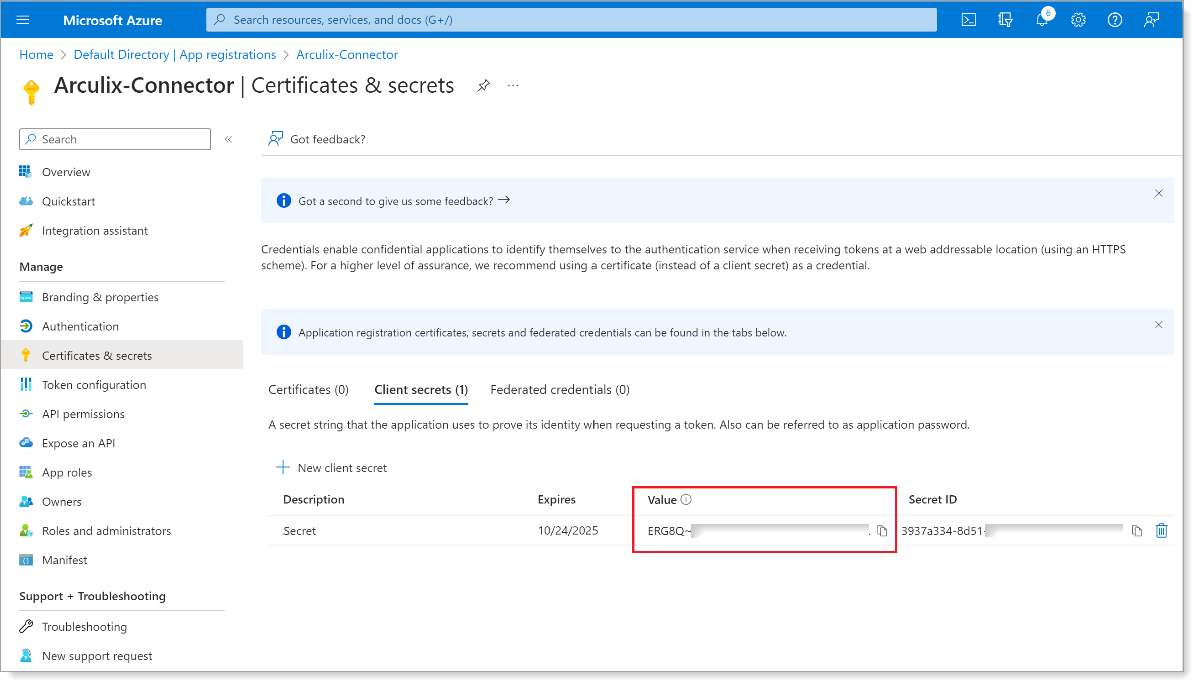
From the left pane, click Certificates & secrets. Then, click New client secret.
-
Enter a description and set expiration to 24 months. Then, click Add.
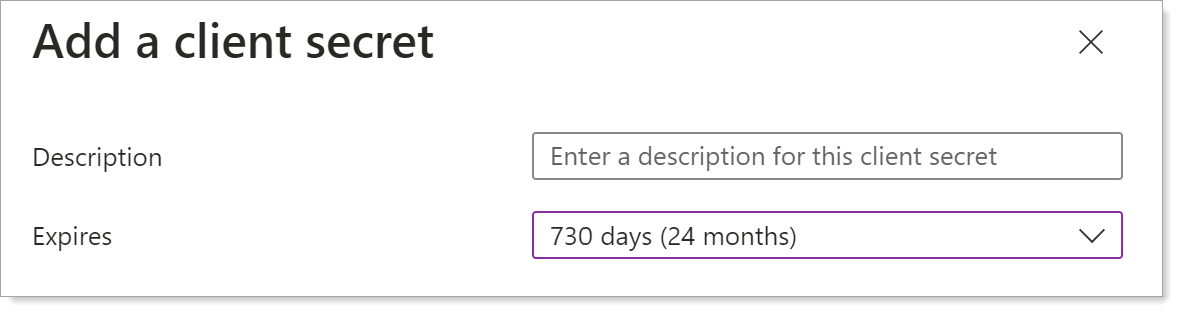
-
Copy the client secret Value before the system masks it when you leave the page.
Note: You will need this client secret value when configuring the connection in SecureAuth Connect.
-
From the left pane for this app registration, click Authentication.
-
In the Advanced settings section, select Yes.
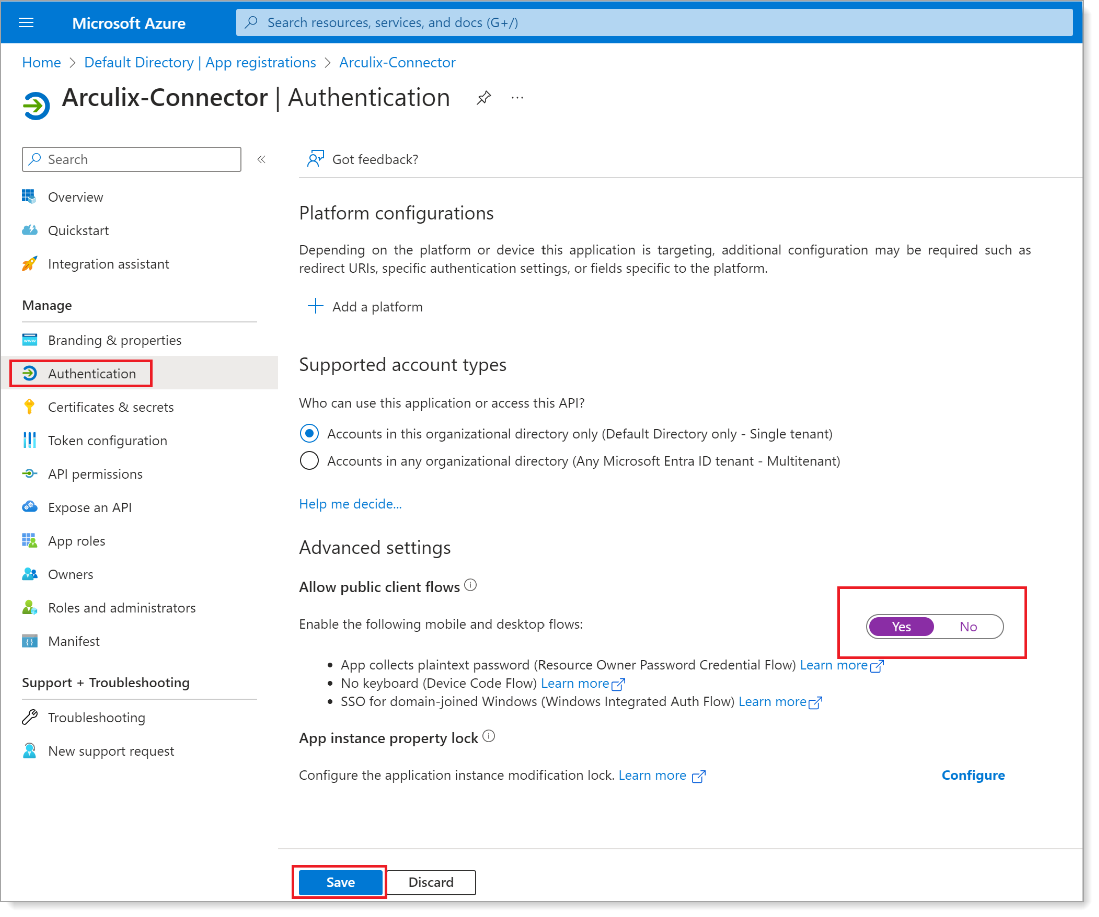
-
Save your changes.
Task D: Get registered application information
For the SecureAuth Connect side of the configuration, copy and note these two values: Application (client) ID and Directory (tenant) ID.
-
Select Microsoft Entra ID.
-
Select App registrations.
-
From the list, click the application name link.
-
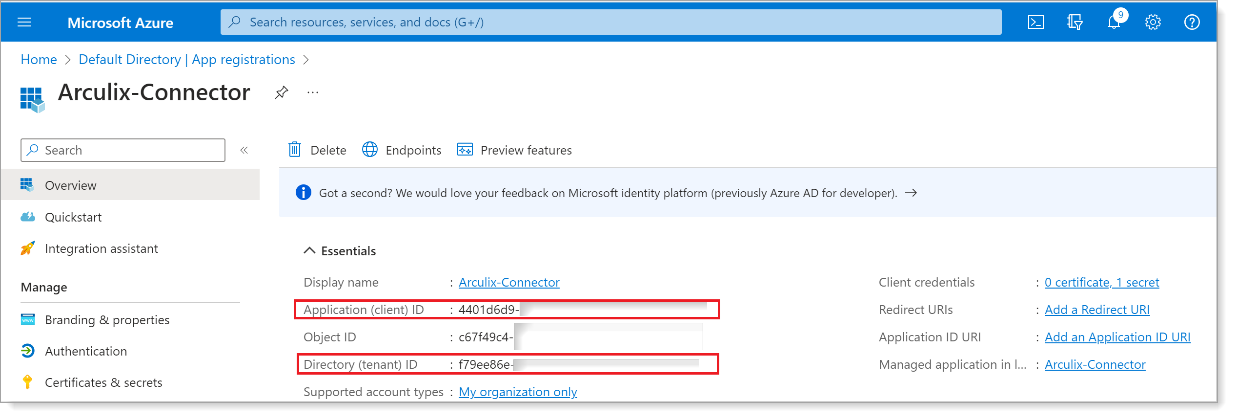
In the Overview section, copy these values:
Note: You will need these values for the SecureAuth Connect configuration.
- Application (client) ID
- Directory (tenant) ID
Next steps
After completing the configuration steps in your Microsoft Entra ID admin center, proceed to Connect Microsoft Entra ID in SecureAuth Connect.
To complete this step in the SecureAuth Connect admin console, gather these values:
- Directory Tenant ID - Your Microsoft Entra tenant ID
- Client ID - The application (client) ID from your Microsoft Entra ID app registration
- Client Secret - The client secret associated with your Microsoft Entra ID application
- Entra ID Tenant Domain - Your verified domain, such as
company.onmicrosoft.com