Connect Active Directory
Connect your existing Active Directory to SecureAuth Connect to enable secure authentication for your workforce. This integration uses the SecureAuth LDAP Agent to create a secure connection between SecureAuth and your on-premises Active Directory.
Prerequisites
Before connecting Active Directory, ensure you have:
- Active Directory administrative credentials
- Service account with read access to Active Directory
- Virtual server or machine to host the LDAP Agent (can be configured after AD connection)
- Network connectivity between the planned LDAP Agent location and your domain controllers
Connect Active Directory
Step 1: Create new directory
- In your Workforce workspace, go to Authentication > User Stores.
- Click Create New Directory. Result: The New User Directory page opens.
- Select Microsoft Active Directory.
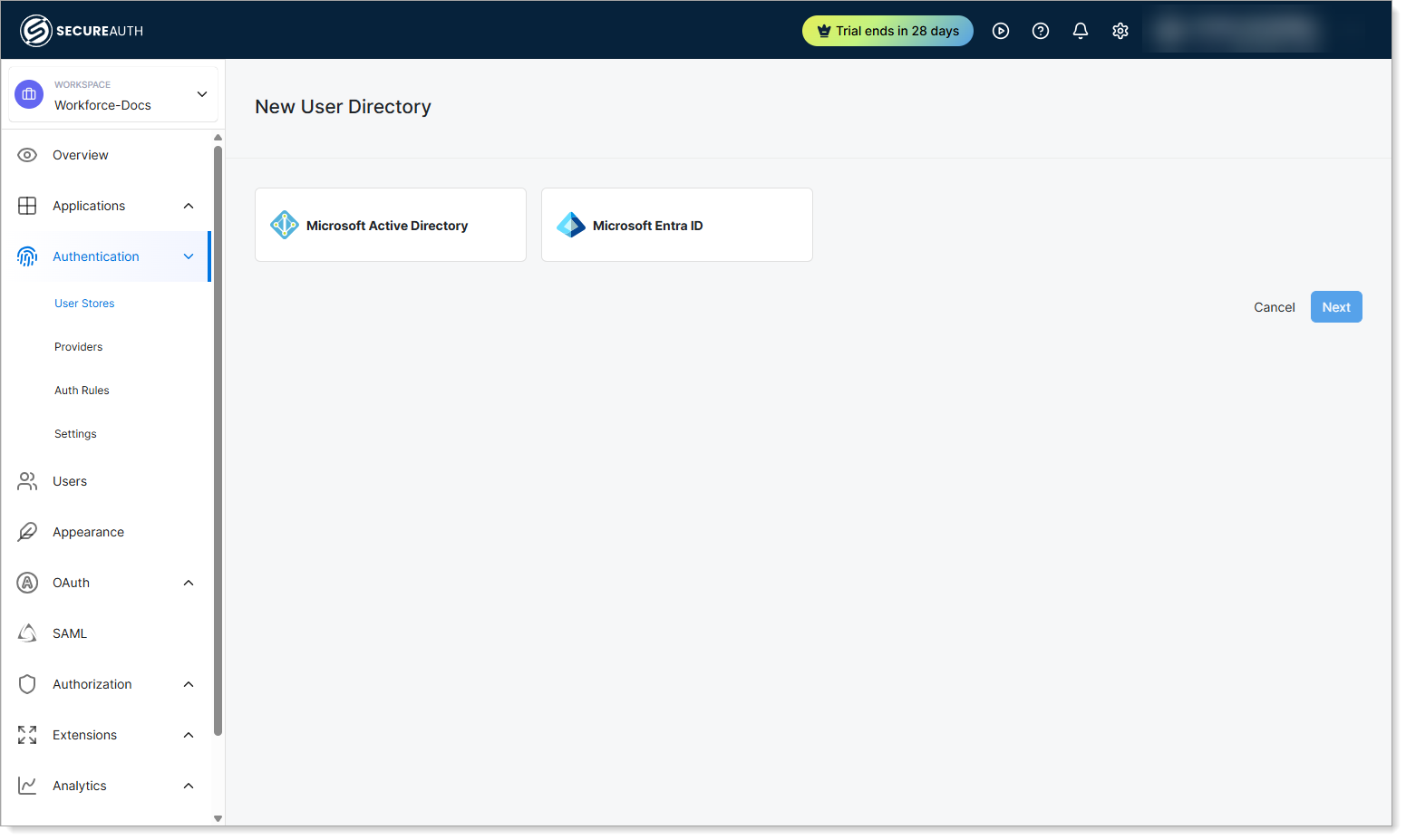
- Click Next.
Step 2: Configure connection details
Complete the basic connection settings.
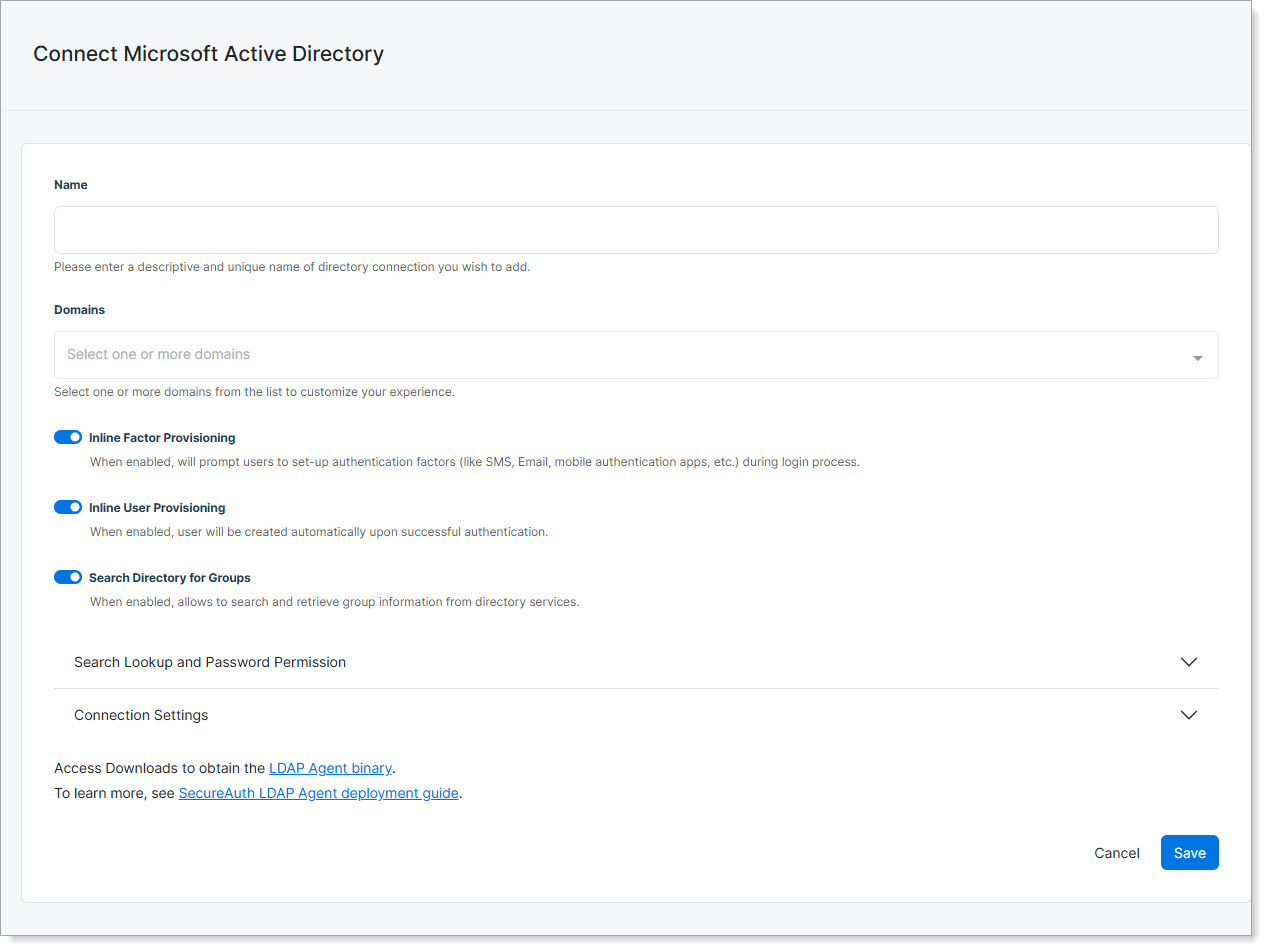
Name
Enter a descriptive and unique name for your Active Directory connection.
Example: Corporate Active Directory
Domains
Select one or more domains from the list to customize your experience.
Example: company.com, hr.company.com
Enable the following based on your requirements:
Inline Factor Provisioning
Prompts users to set up authentication factors (like SMS, email, mobile authentication apps) during the login process.
Inline User Provisioning
Creates users automatically upon successful authentication.
Search Directory for Groups
Looks up user group membership directly from the directory during authentication for policy enforcement.
Step 3: Configure search and password settings
Expand Search Lookup and Password Permission to configure user and group attributes.
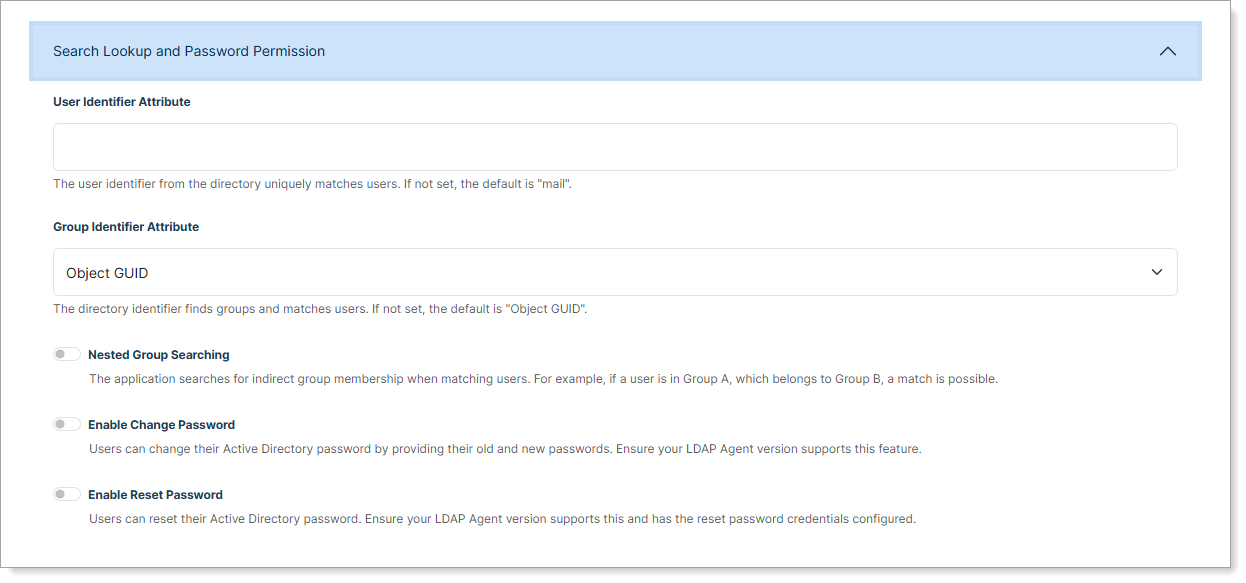
User Identifier Attribute
The attribute from the directory that uniquely matches users.
Default: mail | Alternatives: sAMAccountName, userPrincipalName
Group Identifier Attribute
The attribute that identifies groups in your directory.
Default: Object GUID | Alternative: distinguishedName
Enable the following based on your requirements:
Nested Group Searching
Matches users to groups through nested (indirect) group membership.
For example, if a user is in Group A and Group A is a member of Group B, the user will match to Group B.
Enable Change Password
Allow users to change their own AD password by entering their current password and a new one.
Note: Requires LDAP Agent version with password change support
Enable Reset Password
Allow users to reset their AD password through a password reset flow.
Note: Requires LDAP Agent version with password reset support and proper bind credentials configured.
Step 4: Configure connection settings
Expand Connection Settings to configure agent communication.
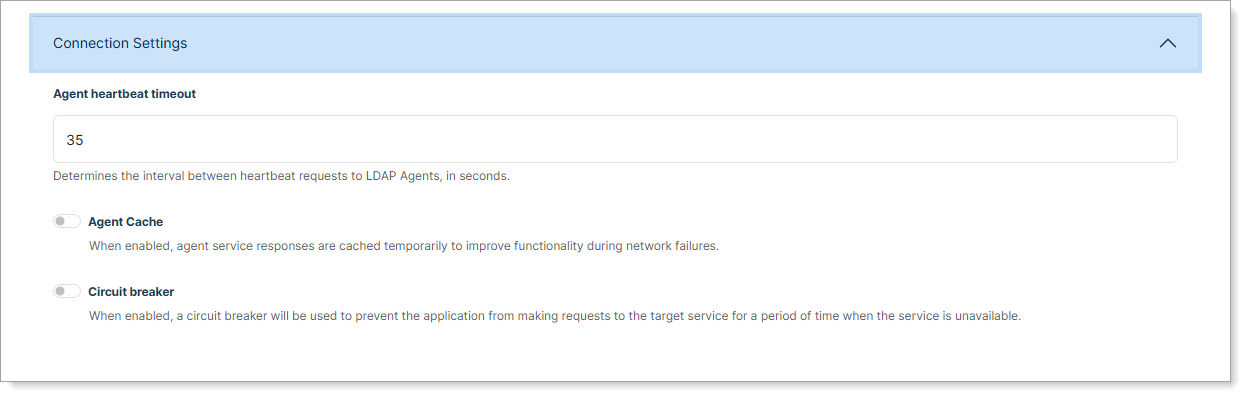
Agent heartbeat timeout
Determines the interval between heartbeat requests to LDAP Agents, in seconds.
Default: 35 seconds
Enable optional performance features:
Agent Cache
Temporarily cache agent service responses. Helps maintain functionality during brief network interruptions.
- Agent Cache Duration – Set how long cached responses remain valid. Enter values in hours and minutes. Default:
25hours
Circuit breaker
Temporarily stop requests to a target service when repeated errors are detected. Prevents excessive retry attempts when the service is down.
- Volume Threshold – Minimum number of requests in a time window before the error rate is calculated. Default:
10 - Error Threshold – Percentage of failed requests (out of the total volume threshold) that triggers the circuit to open. Default:
50 - Time Window – Length of the time window (in seconds) used to evaluate error rates. Default:
30 - Sleep Window – Duration (in seconds) the system waits before retrying requests after the circuit opens. Default:
300
Step 5: Complete setup
- Save your changes.
- Scroll down the page and download the LDAP Agent binary from the provided link.
- Follow the SecureAuth LDAP Agent deployment guide to complete the installation.
Verify Active Directory connection
After configuration, confirm the Directory Information panel shows the directory as online and check the Directory Details.
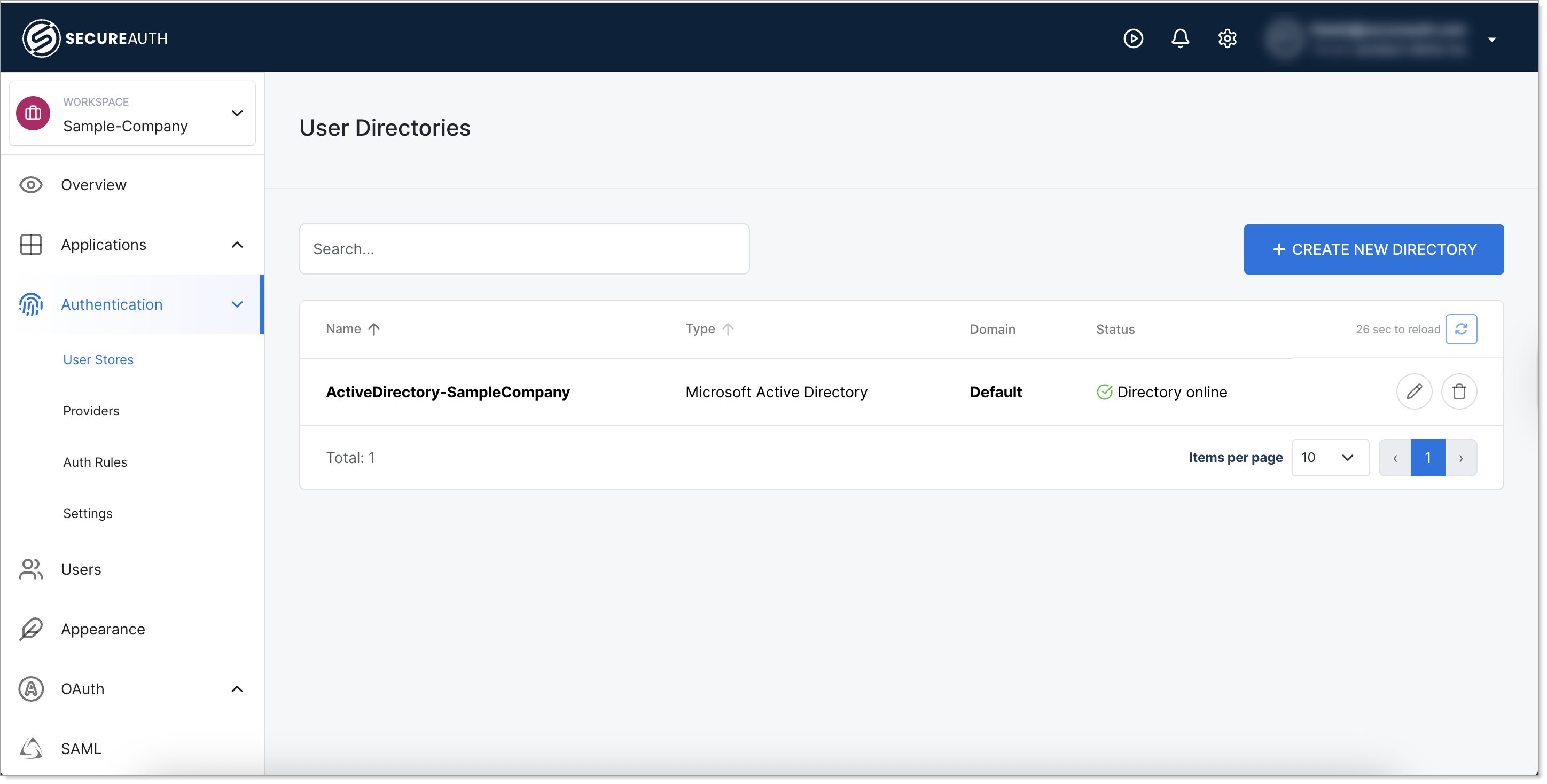 Check Active Directory status in list
Check Active Directory status in list
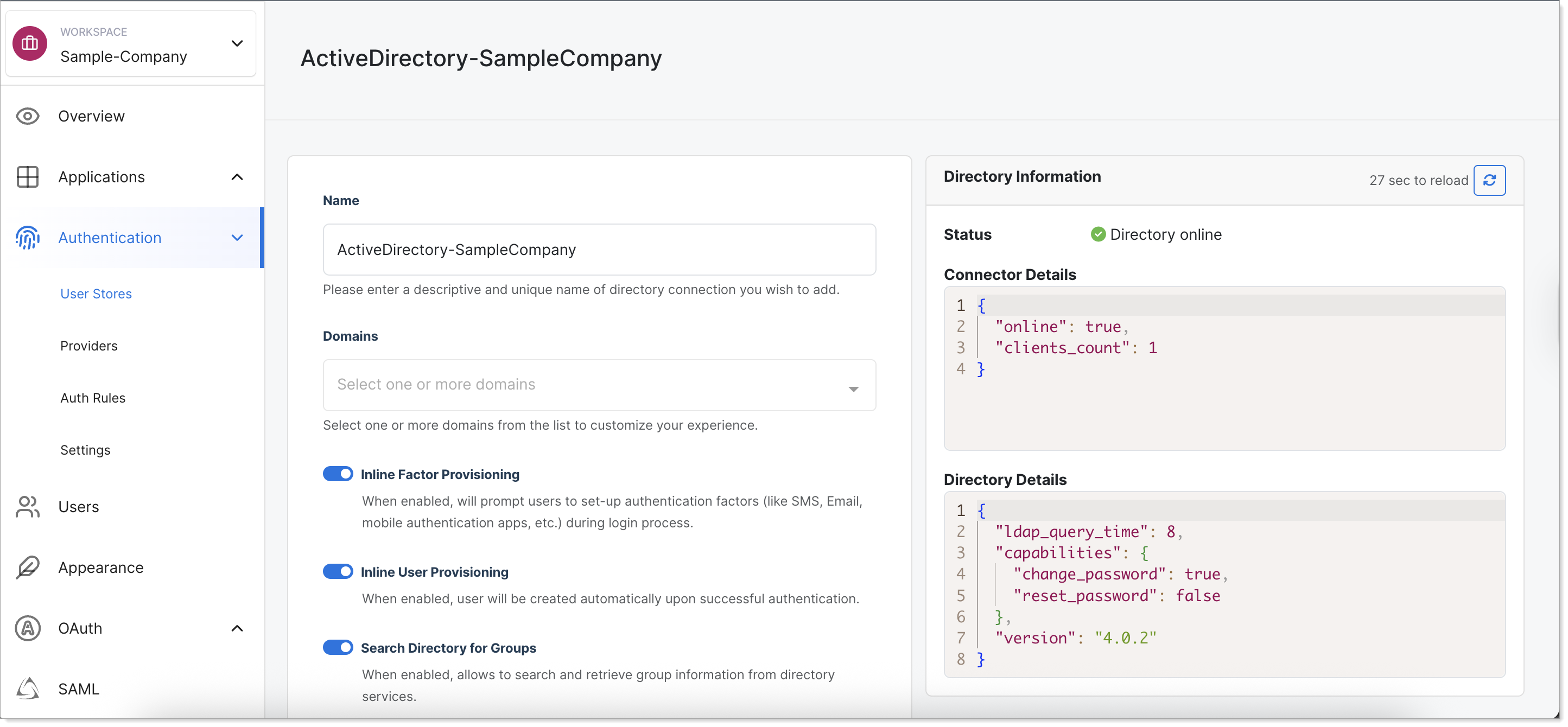 Check Active Directory status in edit mode
Check Active Directory status in edit mode
Log locations
- Windows:
C:\Program Files\SecureAuth\LDAP Agent\logs - Linux:
/var/log/secureauth-ldap-agent
Default directory behavior
When you have multiple user directories (Active Directory, Microsoft Entra ID, Identity Pools, etc.), SecureAuth uses domain matching to determine which directory to authenticate users against:
-
Domain matching – When a user logs in (for example,
jsmith@acme.com), SecureAuth looks for a directory that matches the domain part after@(likeacme.com). -
Default fallback – If no matching domain is found, SecureAuth uses the directory marked as default.
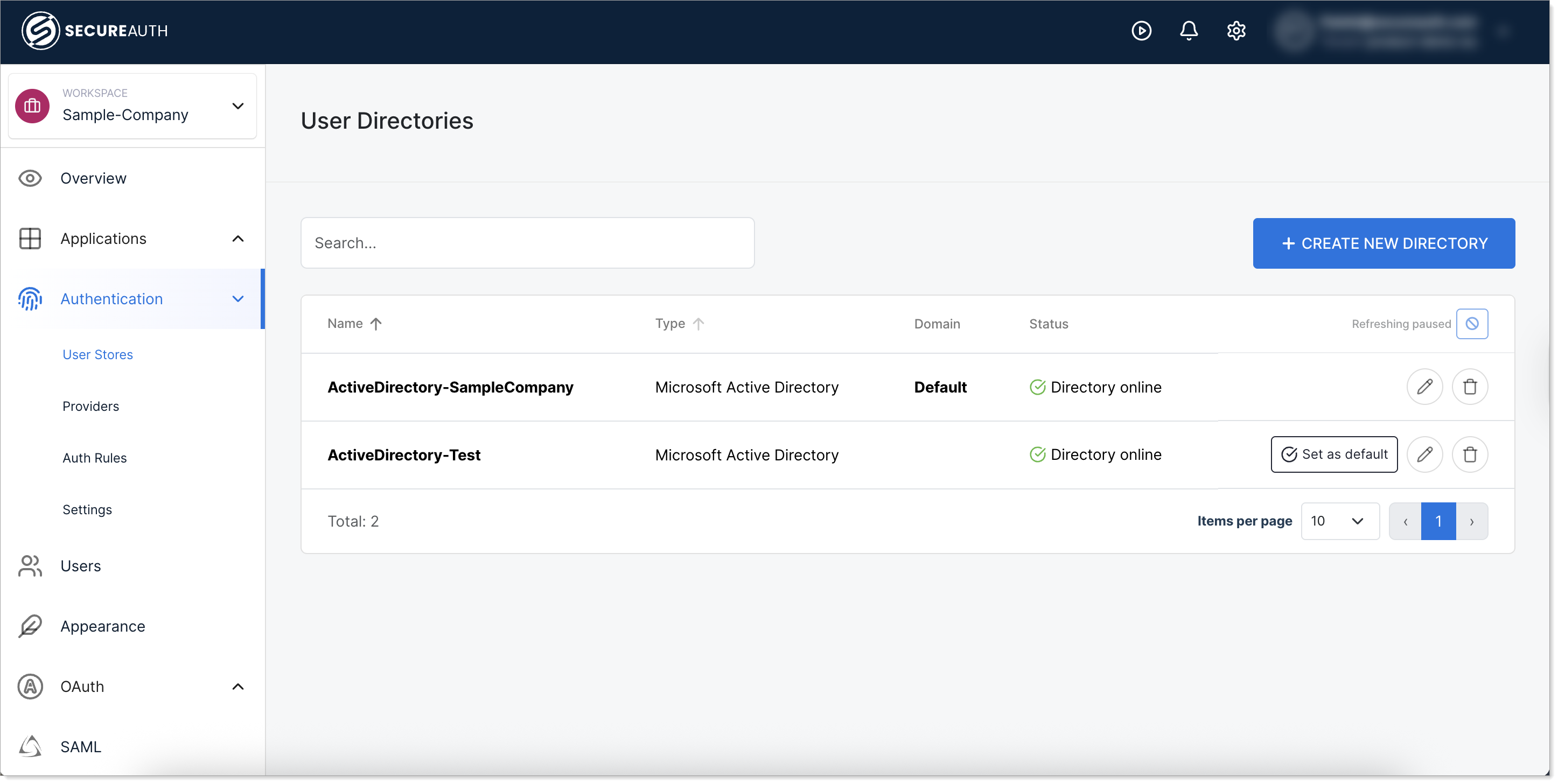
Set a directory as default
To change which directory serves as the default:
- In your Workforce workspace, go to Authentication > User Stores.
- Find the directory you want to set as default.
- Click Set as default.
Important considerations:
- Only one directory can be marked as default at a time.
- Users created directly in the workspace with the same domain name as your Active Directory will not be found if domain matching takes precedence.
- The default directory is used when no domain match is found during authentication.
Next steps
After connecting Active Directory:
- Configure authentication policies for your workforce
- Set up additional applications for SSO