Authentication apps global MFA settings
At the global level, configure the authentication methods sent by SecureAuth Authenticate app. You can also configure third-party apps like Google Authenticator and Microsoft Authenticator. To authenticate into a resource, users receive passcodes, push notifications, or verify their biometric identity.
You can limit the use of this MFA method in a policy.
On the left side of the Identity Platform page, click Multi-Factor Methods.
Click the pencil icon for Authentication Apps.
The configuration page for Authentication Apps appears.
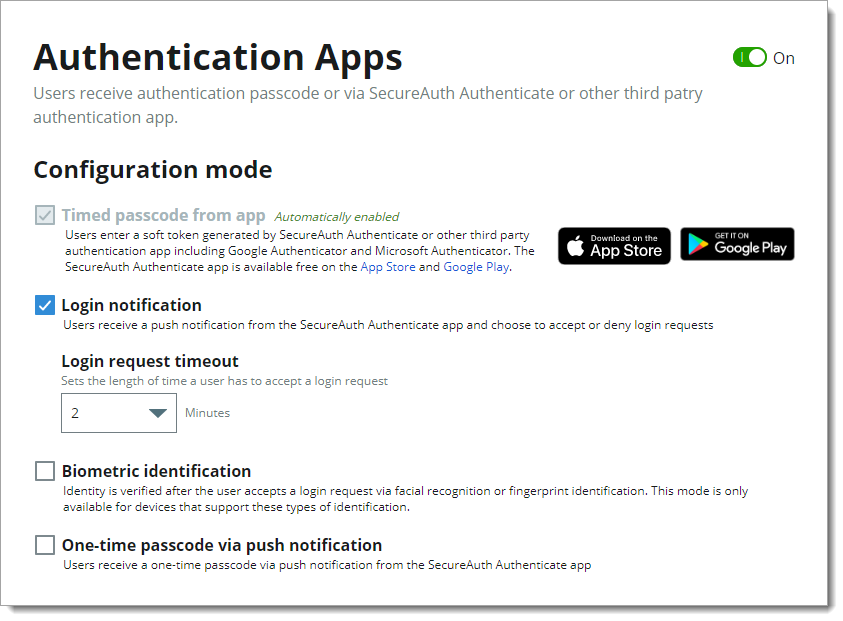
To enable or disable the global Authentication Apps multi-factor method, slide the toggle On or Off.
In the Configuration mode section, set any of the following configurations.
Timed passcode from app
When Authentication Apps toggle is On, it automatically enables the ability for users to receive a soft token generated by SecureAuth Authenticate app or another third-party authentication app.
Login notification
Indicate whether users can receive a push notification from the SecureAuth Authenticate app and allow them to choose or deny login requests.
Login request timeout
For the login notification, set the length of time a user has to accept a login request at one, two, three, four, or five minutes.
Biometric identification
Enable whether users can use biometric identification like facial recognition and fingerprint by means of the SecureAuth Authenticate app.
One-time passcode via push notification
Indicate whether users can receive a one-time passcode by means of a push notification from the SecureAuth Authenticate app.
In the Push Notification Settings section, set the following configuration.
Company name
Name of company to display on the push notification when it is delivered to the user's device.
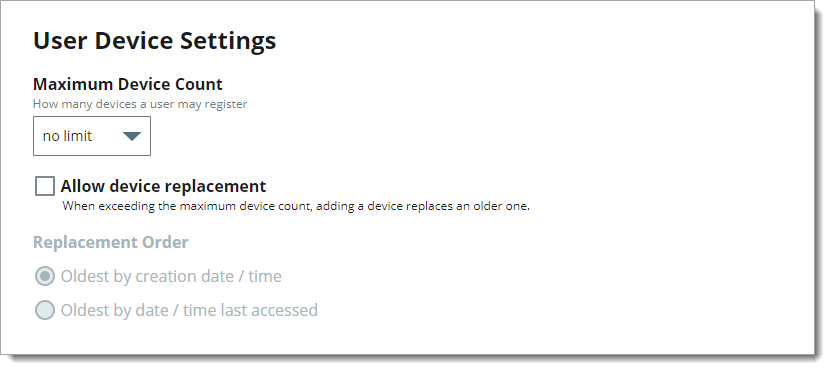
In the User Device Settings section, set the following configurations.
Maximum Device Count
Set the number of devices a user can register to receive authentication tokens. Values range from no limit or up to ten devices.
Allow device replacement
Indicate whether to allow device replacement when a user has reached the maximum number of devices.
Replacement order
Choose one of the following options for replacing an authentication token:
Oldest by creation date / time - replace the oldest authentication token with the newest one
Oldest by date / time last accessed - replace the least used and last accessed authentication token with the newest one
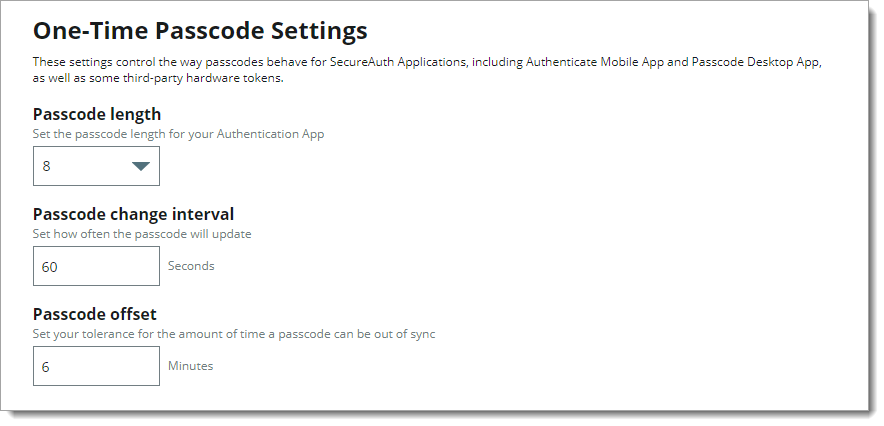
In the One-Time Passcode Settings section, set any of the following configurations that apply to the SecureAuth Authenticate Mobile App and the Passcode Desktop App.
Passcode length
Set the length of the passcode in the Authentication App at six, eight, or nine digits.
Passcode change interval
Set how often in seconds, the passcode updates in the Authentication App.
Passcode offset
To make up for time differences between devices and to enable prolonged validity after the code is no longer displayed, set the tolerance in minutes for the amount of time a passcode can be out of sync.
Click Save.
Next steps
Configure a policy on the Multi-Factor Methods tab to use the SecureAuth Authenticate app as an authenticator in the login workflow.
Encourage your end users to download and install the SecureAuth Authenticate app from the App Store or Google Play.