HID hard token support
This document describes the process of how to provide HID hard OATH token provisioning and management functions within the SecureAuth Identity Management (IdM) suite.
Identity Platform configuration
To support HID hard tokens in the SecureAuth® Identity Platform, make the following configurations described in this section.
Map the OATH Seed to a data source
Go to the Data tab.
In the Profile Fields section, set the OATH Seed field.
Make sure it is correctly mapped to a directory attribute (if using LDAP). If using SQL, make sure the stored procedure returns a value for OATH Seed.
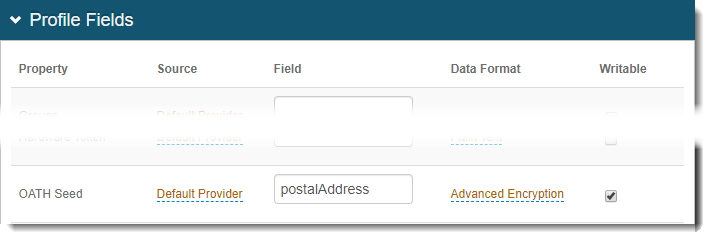
Save your changes.
Map the OATH Seed to an editable field on the user self-service page (aka account update)
In the Profile Fields section, locate any auxiliary field. For example, Aux ID 1.
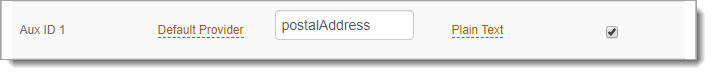
Map this field to the same value used in the OATH Seed field, and select the Writable check box.
Save your changes.
Go to the Post Authentication tab.
In the Post Authentication section, set the following:
Authenticated User Redirect
Set to User Self Service Account Update.
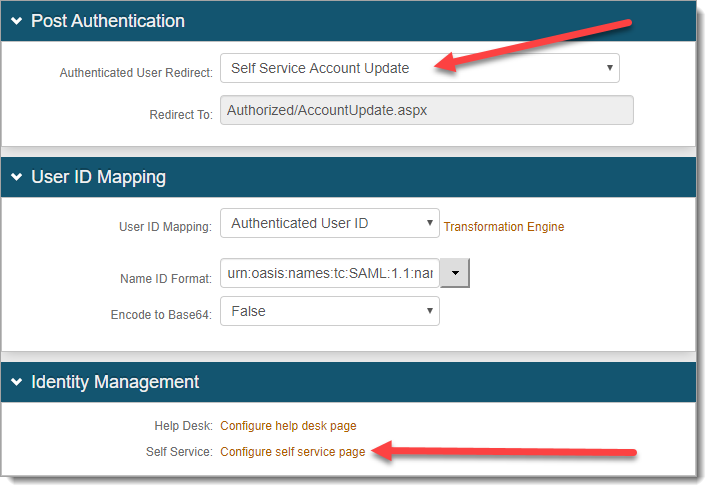
In the Identity Management section, click the Configure self-service page link.
On the Self Service page, set the auxiliary field (for example, Aux ID 1) to Show Enabled.
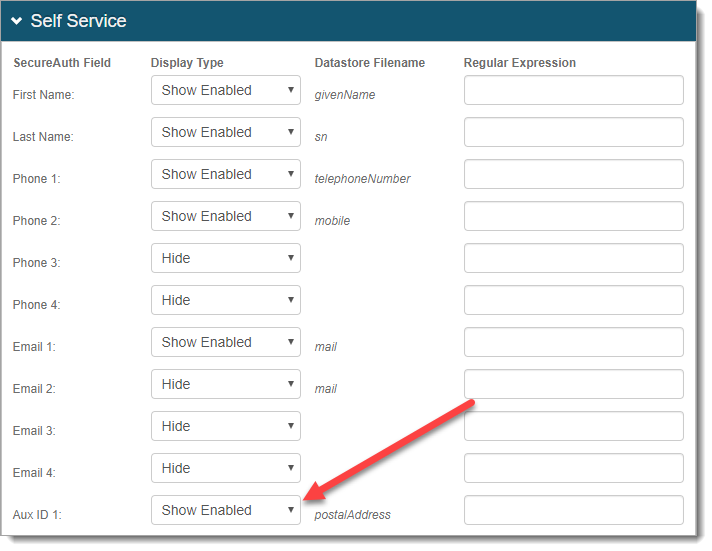
Save your changes.
Configure the OATH Settings to match the HID hard token in use
Go to the Multi-Factors Methods tab.
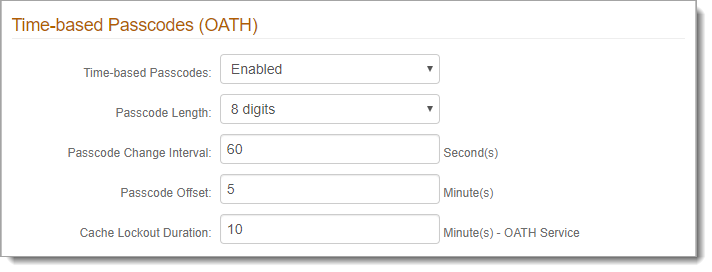
In the Multi-Factor Configuration section, scroll down to the Time-based Passcodes (OATH) subsection and set the following to match the HID hard token in use:
Time-based Passcodes
Set to Enabled.
Passcode Length
Set the length of the passcode.
Note
This value must match the same setting on the Post Authentication tab in the Multi-Factor App Enrollment section. See Multi-factor app enrollment URL configuration.
Passcode Change Interval
Set the number of seconds the passcode is available.
Note
This value must match the same setting on the Post Authentication tab in the Multi-Factor App Enrollment section. See Multi-factor app enrollment URL configuration.
Passcode Offset
Set the number of minutes the passcode is to remain valid between devices.
Cache Lockout Duration
Set the number of minutes an account remains locked after using passcodes for too many failed login attempts.
Save your changes.
Next steps
Once you have the Identity Platform configured to use HID hard tokens, the next step is to install and run the SecureAuth Hard Token Decrypt Tool to decrypt HID hard tokens. Follow instructions in that topic to enter and save the HID token OATH Seed to the user profile.