Password Throttling configuration guide
Use this guide to configure Password Throttling on SecureAuth® Identity Platform to prevent bad actors from accessing a realm via repeated attempts to guess an end user's password.
The Password Throttling feature can be configured to either block the end user from making further password login attempts, or lock the targeted account once reaching the maximum number of invalid attempts within the set timespan.
This feature uses a dynamic, rolling time period for managing the count of password login attempts. Each time the end user starts the realm login page, the attempt count value increases by 1. The attempt is active for the duration of the set time period:
The configured throttling action occurs if the attempt count exceeds the number of incorrect password attempts allowed for the allotted time period.
Once the time period for that attempt has elapsed, the attempt count decreases by 1.
Upon a successful authentication, the attempt count is reset to 0.
Note
Password Throttling is enabled on a per realm basis. However, all realms share the same attempt count value.
Prerequisites
Identity Platform release 19.07 or later
Have a configured application in the Identity Platform
Have a defined user login authentication policy in the Identity Platform
Have an integrated data store in the Identity Platform
Identity Platform configuration
In the Identity Platform, go to the Data Store Summary of the data store connected to the application where you will enable password throttling.
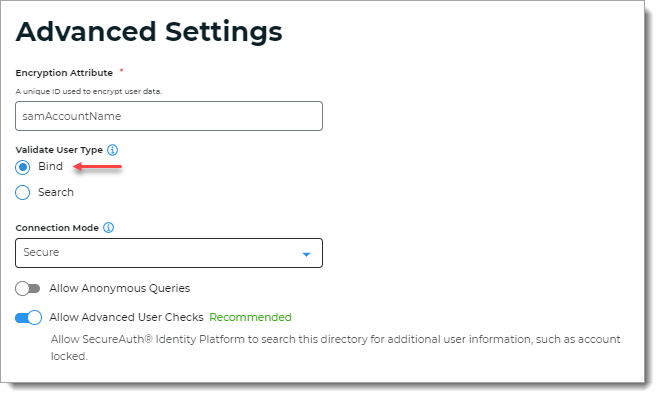
In Advanced Settings, select Bind for Validate User Type.
Click Save.
Go to the Data Store Properties for the data store.
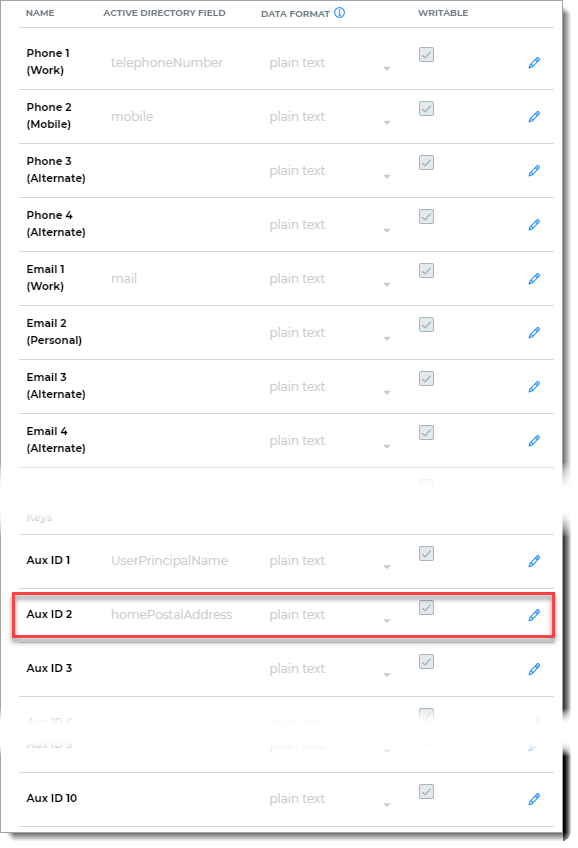
Map the designated Field Attribute to an available Property that matches the attribute's requirement to store the date and time of each invalid password login attempt.
The Field Attribute must meet the following requirements:
Directory String
Single Value
Upper range of 4096
Properties that match the field attribute requirements are:
Aux ID 1 - Aux ID 10
Email 1 - Email 4
Phone 1 - Phone 4
For example, map homePostalAddress to Aux ID 2.
Note
The Field Attribute and Property selected will be tied to the Unlock button which can be used on any realm to unlock accounts.
To avoid losing valuable user data, select a Property that is not being used by any other realm, and will only be used for the password unlock function.
Select the Writable checkbox.
Click the blue check mark to save.
Navigate to Advanced Settings (formerly Classic Experience) and set the Workflow Tab for the realm where you will enable password throttling.
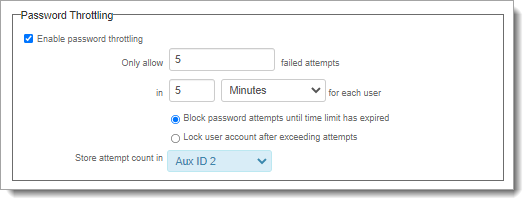
In the Workflow section, set the following for Password Throttling:
Enable password throttling
Select the checkbox to enable password throttling.
Only allow [X] failed attempts
Set to the maximum number of failed login attempts a user can have in the allotted timeframe before throttling takes effect.
in [X timeframe] for each use
Set the timeframe for counting failed attempts and select minutes, hours, or days.
This configuration specifies the rolling time period before throttling takes effect.
Notice
To prevent an Active Directory lockout during a password throttling session, SecureAuth recommends:
The failed attempts value should be less than the Account lockout threshold setting configured for the AD Default Domain Policy
The time value should be greater than the Reset account lockout counter after setting configured for the AD Default Domain Policy
For example:
Default Domain Policy
Password Throttling
Account lockout threshold is set to 10 invalid logon attempts
Only allow 'X' failed attempts should be set to 9
Reset account lockout counter after is set to 20 minutes
in 'X' [timeframe] for each user should be set to 21 Minutes
Block password attempts until time limit has expired
or
Lock user account after exceeding attempts
Select one of the following options to run when the end user exceeds the maximum number of failed login attempts:
Block password attempts until time limit has expired – the end user is prevented from making another login attempt until the attempt count has decreased by at least 1.
Lock user account after exceeding attempts – the end user's account is locked until an administrator unlocks it.
Store attempt count in
Select the Property designated in Step 5 to store the attempt count in.
Click Save.
Warning
Click Save once the configuration is complete and before leaving the Workflow tab to avoid losing changes.
End user experience
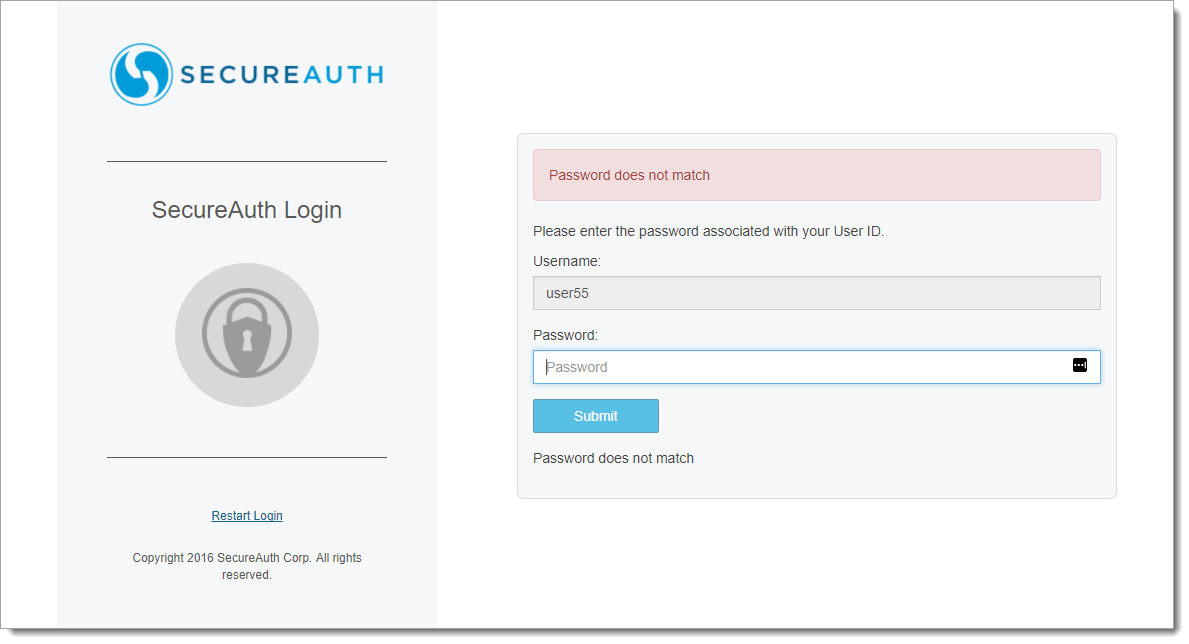
When entering an invalid password, the Password does not match message appears.
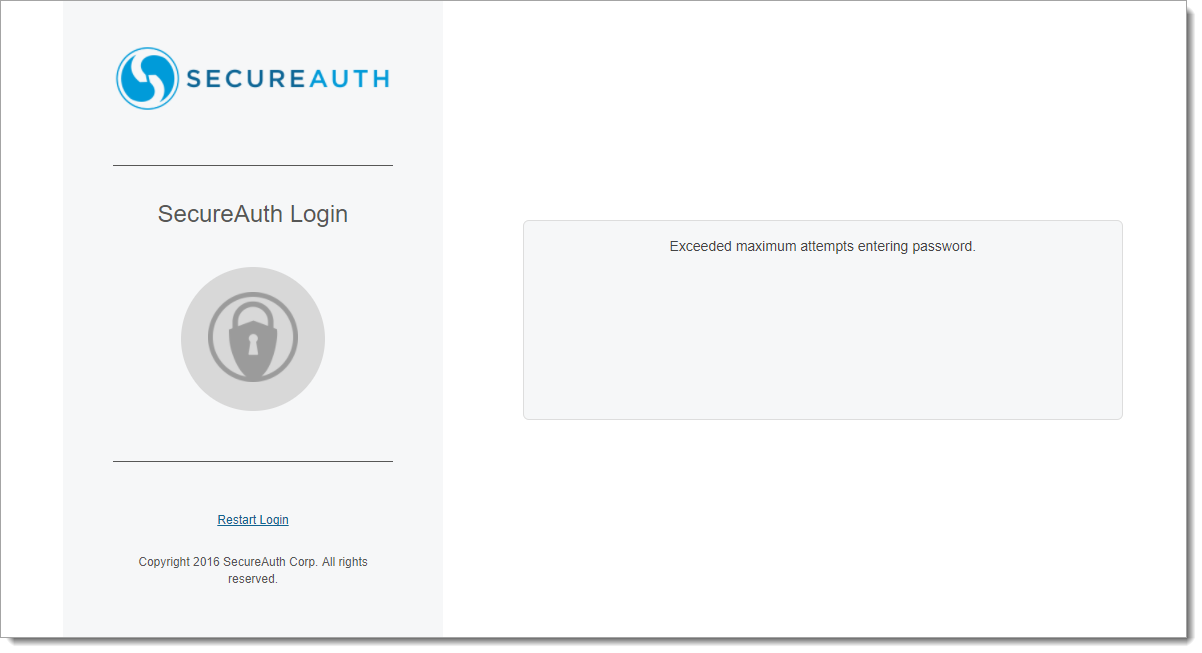
After entering an invalid password for the configured maximum number of failed attempts within a given timeframe, the Exceeded maximum attempts entering password message appears.
If the Block password attempts until time limit has expired feature is enabled, the end user can enter a password again when the time limit has expired.
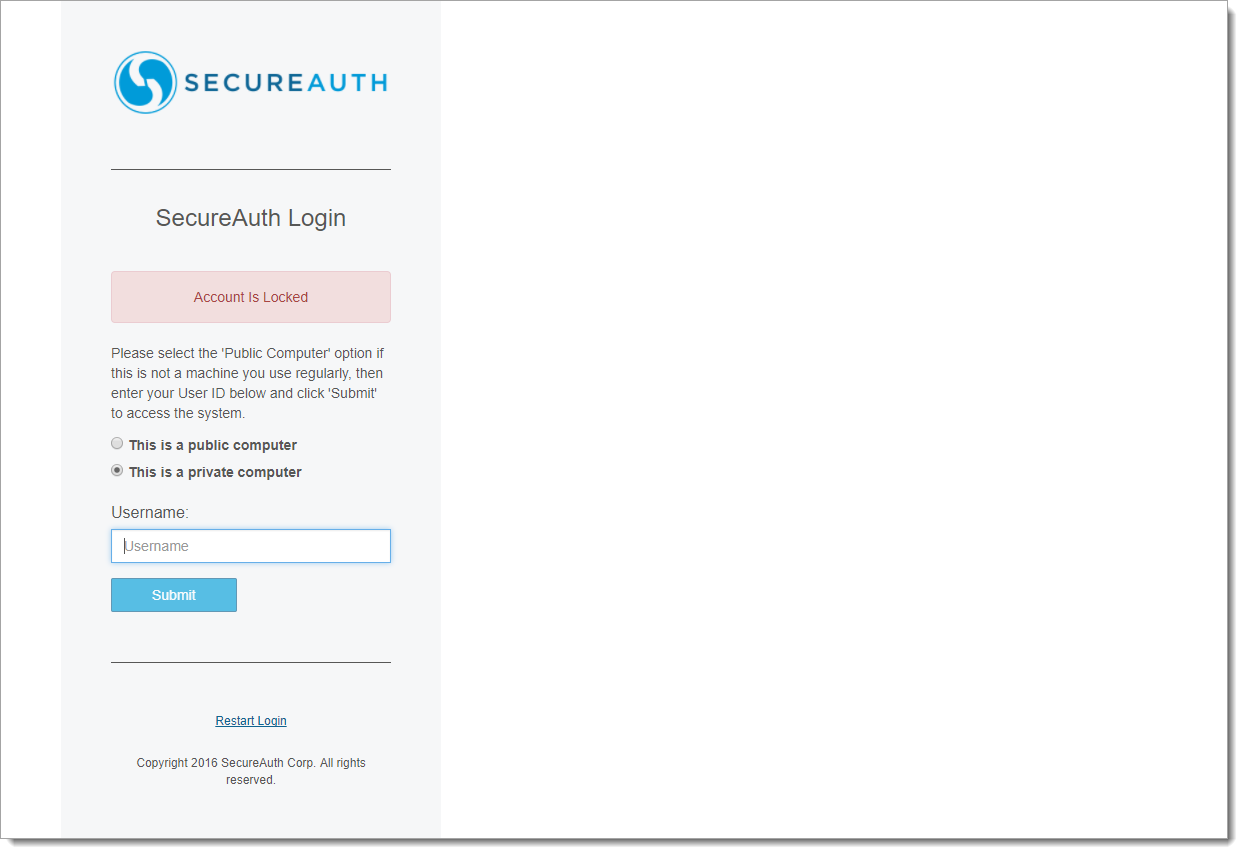
If the Lock user account after exceeding attempts feature is enabled, when the maximum number of failed attempts within the time limit is reached and a new session is started, the end user is presented with the Account is Locked screen. Only an administrator can unlock the user's account.
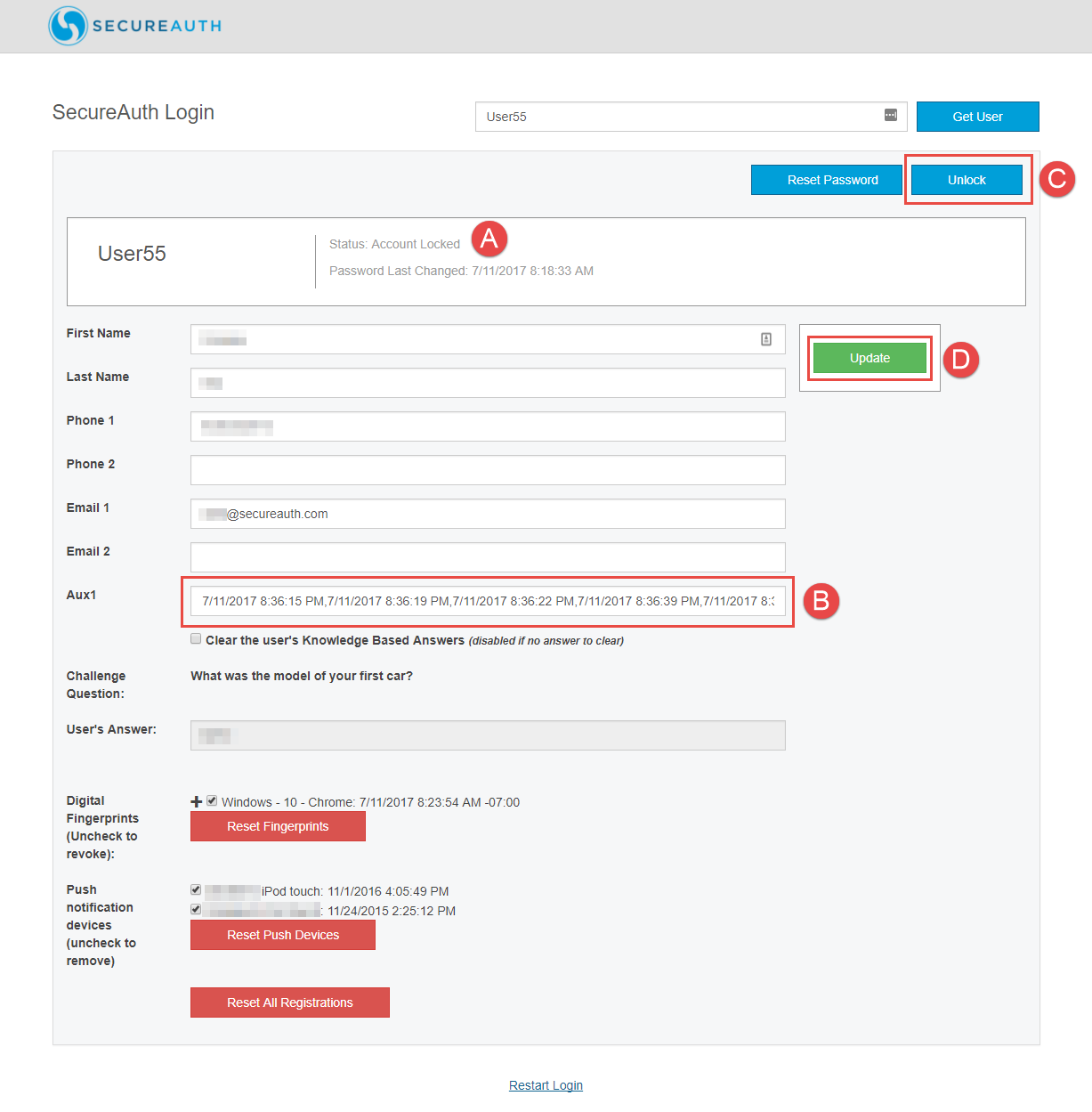
Unlock an end user account
Log into the designated realm and retrieve the end user's locked account.
Confirm the account status shows Status: Account Locked (Image Item A).
Review the history of invalid password entries in the Aux1 field (Image Item B).
This information includes the date and time of each failed attempt (using the MM/DD/YYYY HH:MM:SS AM/PM format), separated by a comma.
Click Unlock (Image Item C). This action clears the history of invalid password entries on the Aux1 field and unlocks the account on the directory.
Warning
If any other realm is used to unlock user accounts – for example, an unlock account realm – when the administrator clicks Unlock for a specified user on that realm, content in the Aux1 field on this screen will be cleared, regardless of the field to which this property is mapped, and the user account will also be unlocked on all other realms.
Click Update (Image Item D).