SAML application integration
This topic covers how to integrate a generic SAML application in the SecureAuth® Identity Platform to securely allow the right user access to a third-party application in your organization.
On the left side of the Identity Platform page, click Application Manager.
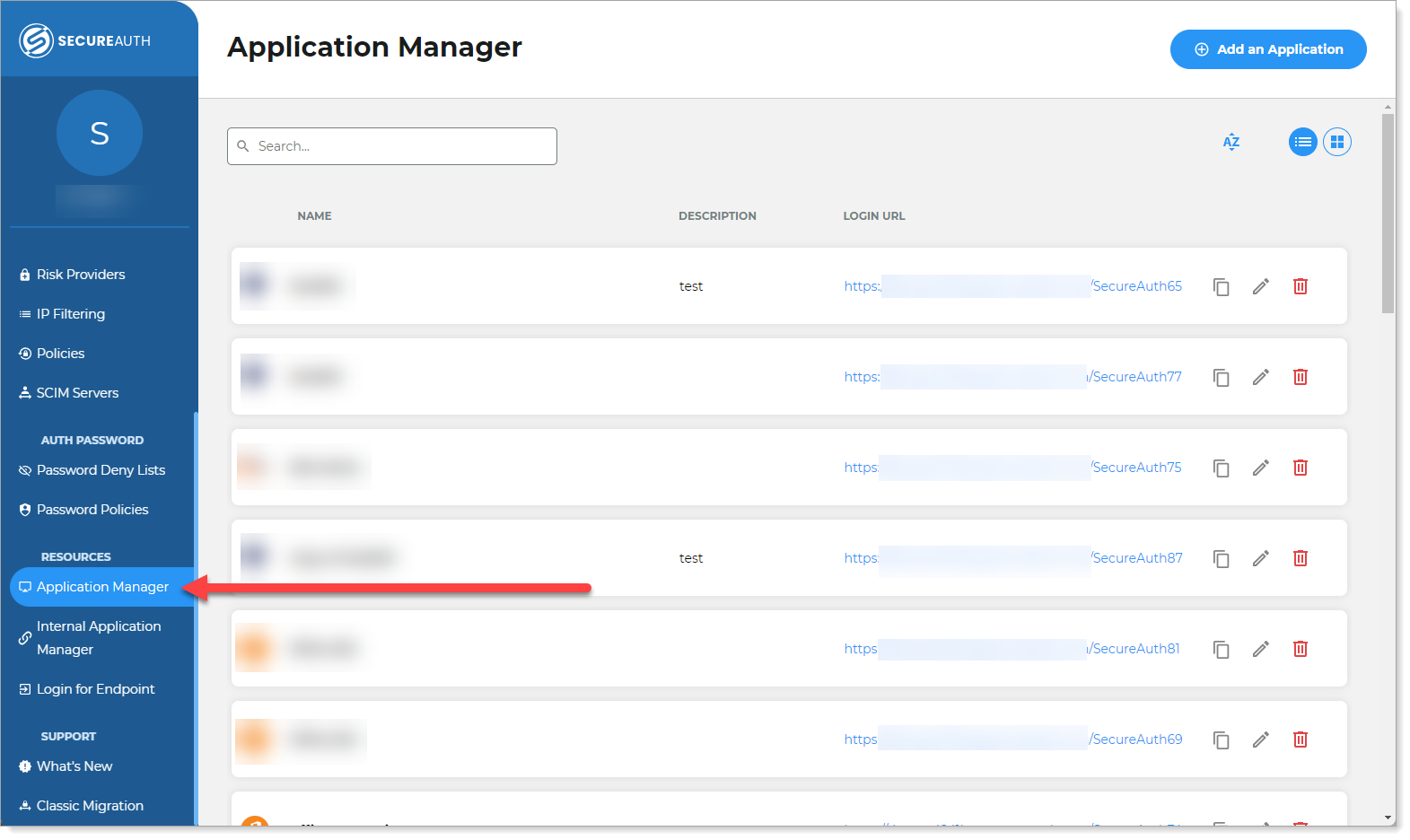
Do one of the following:
To clone an application, click the copy icon for an application and continue to the next step.
To add an application, click Add an Application.
The application template library appears. From the list, select SAML Application.
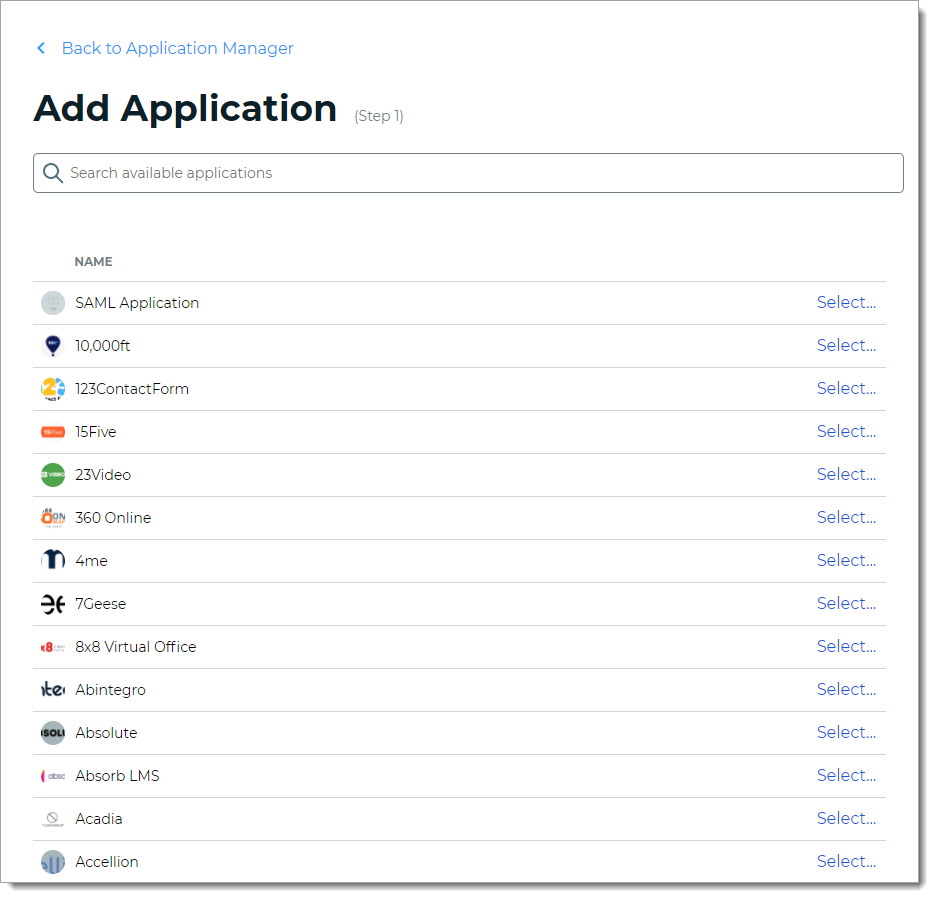
On the Applications Details page, set the following configurations.
Application Name
Name is prefilled by default. You can optionally change the application name.
This displays in the Application Manger list and on the Application Settings page.
Application Description
This is an internal description not shown to end users at login.
Upload logo
Click Upload to add a logo for the SAML application.
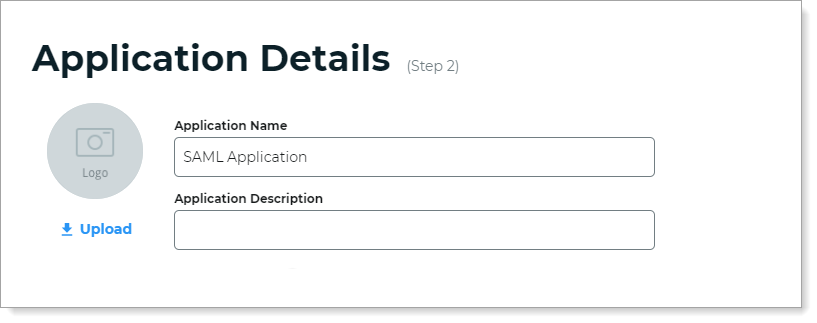
In the Authentication and Access section, set the following configurations.
Authentication Policy
Select the login authentication policy for this application.
Data Stores
Enter the data stores to to authenticate and allow user access for this application.
Start typing to bring up a list of data store names. You can enter more than one data store.
Groups
Use one of the following options:
Slider in the On position (enabled): Allow users from every group in your selected data stores access to this application.
Slider in the Off position (disabled): Enter the specific groups who are allowed access to this application.
Tip
Admins typically set it to Allow every group in your selected data stores access to this application.
Otherwise, you could add specific user groups for user testing until making the switch over to more or all groups.
Realm Number
Select the Realm Number to use for this application.
SCIM Server
To learn more about using a SCIM server, see SCIM provisioning overview.
Click Continue.
The Connection Settings page appears.
In the Configure Connection section, set the following configuration.
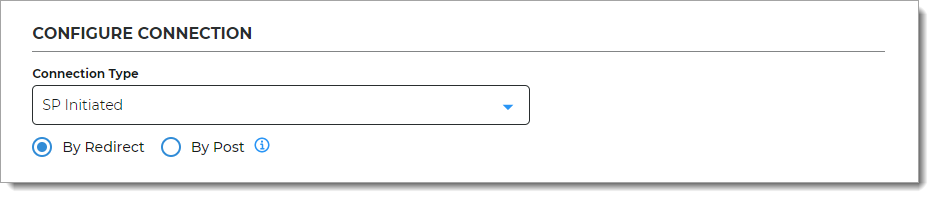
Connection Type
Select one of the following:
SP Initiated – Starts the login process at the service provider / application, then redirects the user to the Identity Platform for authentication, and upon successful authentication, it finally asserts the user back to the application. The SAML specification allows for service providers to send authentication requests (AuthnRequest) to the Identity Platform either by HTTP Redirect or HTTP Post. The service provider configuration or metadata tells you what is used for the authentication request.
By Redirect – Use HTTP Redirect binding to send the AuthnRequest with the signature related to the request.
By Post – Use HTTP Post binding to send the AuthnRequest with the embedded signature.
IdP Initiated – Starts the login process at the Identity Platform, and upon successful authentication, asserts the user to the application.
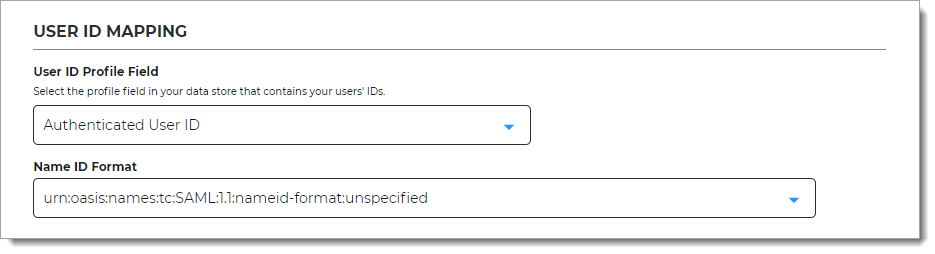
In the User ID Mapping section, set the following configuration.
User ID Profile Field
Select the profile field in your data store that contains the user IDs.
Name ID Format
Select the name ID format to use for sending the SAML response.
The default unspecified format is accepted by most applications.
In the SAML Assertion section, set the following configurations.
Upload Metadata
If you have a preconfigured XML file with your SAML settings, select the Upload Metadata link at the bottom right of the page.
Note
To use the metadata upload feature, you must provide an issuer, map user ID values, and select a certificate to properly configure the connection.
After the file is uploaded, review the prepopulated fields and make the necessary edits.
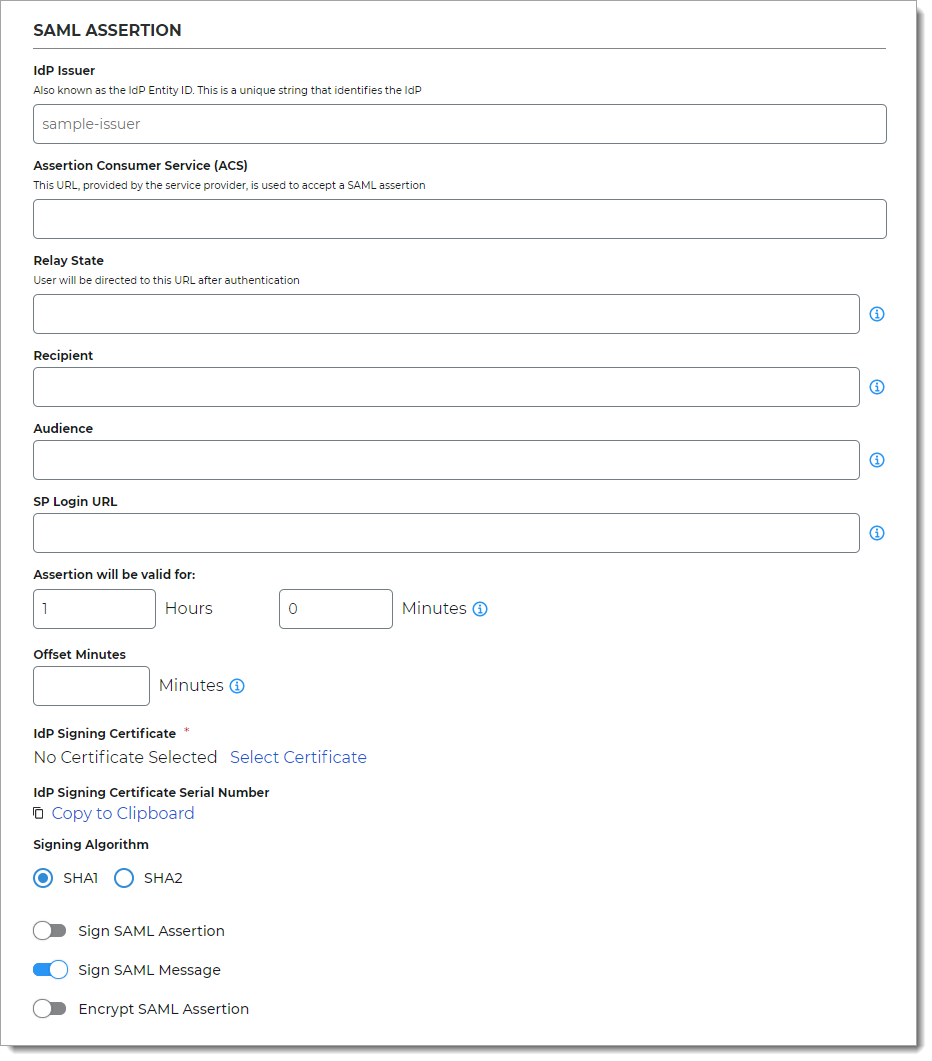
IdP Issuer
A unique name that must match exactly on the Identity Platform side and the application side. This helps the SAML application identify the Identity Platform as the SAML issuer.
Assertion Consumer Service (ACS)
Enter the URL from the service provider to let the application accept a SAML assertion from the Identity Platform.
Relay State
Optional. User is directed to this URL after authentication.
Recipient
Optional. This field is usually the same as the consumer (ACS) URL.
Audience
Optional. A unique string that identifies the service provider (SP). Usually, this is the entity ID of the service provider.
SP Login URL
This is the login URL of the Service Provider (SP). Usually, this is the same address the Relay State or Assertion Consumer Service (ACS) URL.
Assertion will be valid for
Indicate in hours and minutes, how long the SAML assertion is valid. It is referred to as SAML NotOnOrAfter in the SAML Specifications.
The default setting is one hour, but for more sensitive application resources, the recommended value is between one to five minutes.
Offset Minutes
Indicate in minutes to account for the time differences among devices. This is referred to as SAML NotBefore in the SAML Specifications.
Recommended value is five minutes.
IdP Signing Certificate
Click Select Certificate, choose the IdP signing certificate to use, and then click Select to close the box.
IdP Signing Certificate Serial Number
When you select an IdP signing certificate, the serial number populates this field.
Signing Algorithm
The signing algorithm digitally signs the SAML assertion and response.
Choose the signing algorithm – SHA1 or SHA2 (slightly stronger encryption hash and is not subject to the same vulnerabilities as SHA1).
Sign SAML Assertion
Enable signing of the SAML assertion to ensure assertion integrity when the assertion is delivered to the service provider (SP).
Sign SAML Message
Enable signing of the SAML message to ensure message integrity when the message is delivered to the service provider (SP).
Encrypt SAML Assertion
Enable encryption of the SAML assertion if only the service provider and the Identity Platform should understand the assertion. Next, select the data and key encryption methods:
Data Encryption Method – Select the algorithm of the data encryption method
Key Encryption Method – Select the type of key encryption method (symmetric or asymmetric)
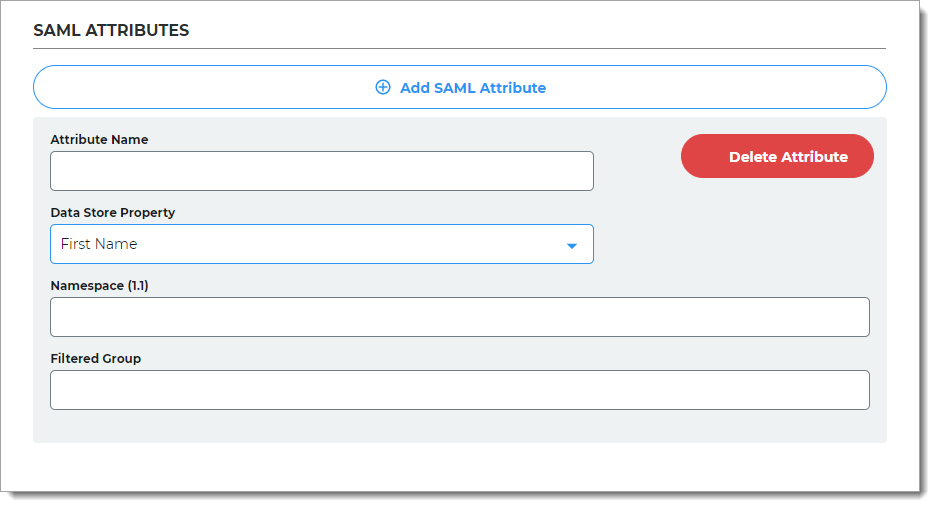
If more information from the directory needs to be sent in the assertion, in the SAML Attributes section, click Add SAML Attribute and set the following configurations.
Attribute Name
Provide the attribute name from the directory to which identifies the user to the application.
For example, givenname
Data Store Property
Select the data store property which maps to this directory attribute.
For example, First Name
Namespace (1.1)
Set the authorization URL to tell the application which attribute is being asserted.
Filtered Group
Provide the group names from the directory to ensure users have appropriate view permissions based on their group membership. You can use a full regular expression or full group domain name list.
When the Data Store Property is set to Groups, use the regular expression like this:
.*(Group1|Group2|Group3)When the Data Store Property is set to Full Group DN List, use the full group domain name list like this:
.*(cn=admin,dc=acme,dc=com|cn=devops, dc=acme,dc=com)This field applies to Identity Platform version 20.06 or later.
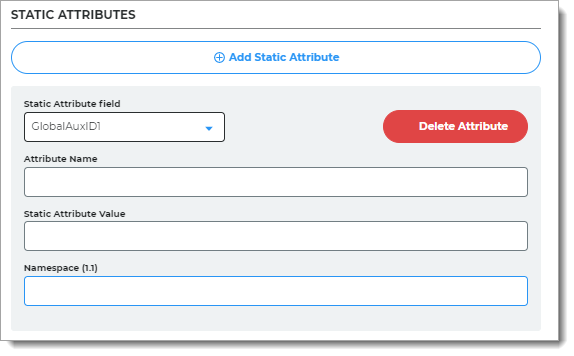
To add attributes with fixed values that apply to all users, in the Static Attributes section, click Add Static Attribute and set the following configurations.
Static Attribute field
Select the Global Aux ID to map the static attribute to. The options are Global Aux ID 1 to Global Aux ID 5.
For example, select Global Aux ID 1.
Attribute Name
Set to the attribute name required by the Service Provider.
For example, companyName.
Static Attribute Value
Set the value of the attribute. This value is fixed and applies to all users.
For example, SecureAuth.
Namespace (1.1)
Set to the value required by the Service Provider.
Click Add Application.
After it saves the application, the Information for Service Providers page appears. You will need this information to complete the configurations on the service provider side.
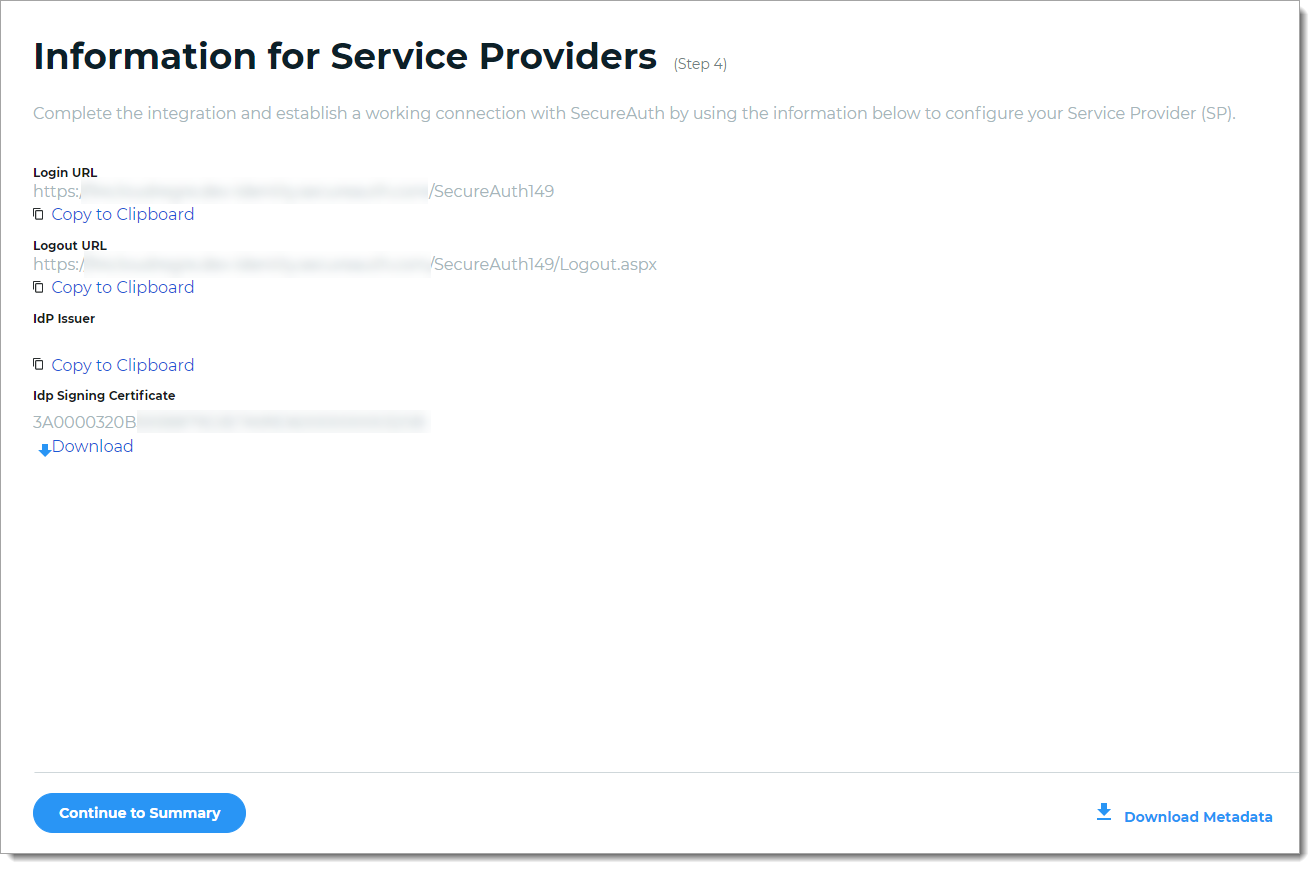
To complete the integration and establish a working connection with SecureAuth, provide the following information as required to the service provider.
Login URL, Logout URL, IdP Issuer
Click Copy to Clipboard to copy the Identity Platform realm information and paste it in the corresponding field on the service provider user interface, as required.
IdP Signing Certificate
Download the IdP Signing Certificate.
Download Metadata
To download the metadata file:
Click Download Metadata.
Enter the Domain name to the Identity Platform appliance URL or IP address.
For example, https://secureauth.company.com or https://111.222.33.44
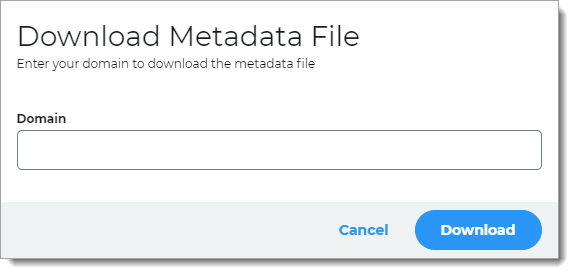
Click Download to get the configuration file.
Upload the file to the service provider.
Click Continue to Summary to review the application settings.
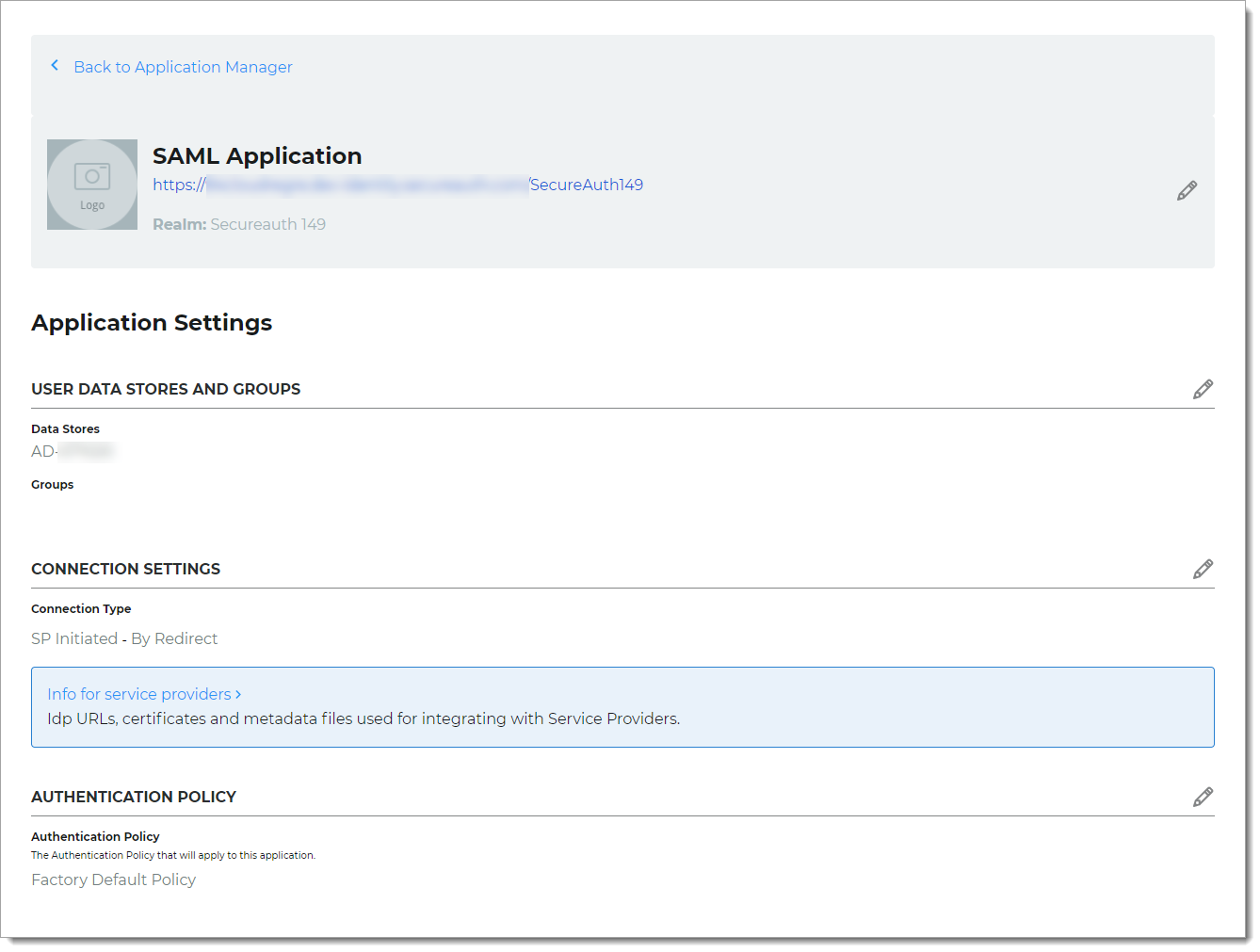
Click Back to Application Manager at the top of the page to find the application added to the list.