Microsoft Active Directory Federation Services ADFS plugin integration
Multi-factor authentication (MFA) is an extra layer of security used when logging into websites or apps in which individuals are authenticated through more than one required security and validation procedure that only you know or have access to.
Acceptto offers a simple solution for adding MFA for Active Directory Federation Services (AD FS) v3.0 on Windows Server 2012 R2 and v4.0 on Windows Server 2016. With this feature, customers can use ADFS as their Identity Provider (IdP) to login to their applications and empower it with Acceptto MFA to provide a strong method of authentication.
Prerequisites
An Acceptto user account with Administrator privileges for your organization.
An Active Directory user with enough privileges to administer the Active Directory Federation Services server.
All the users that are going to use the Acceptto MFA service must be enrolled using the It’sME application.
Initial steps
Sign up for Acceptto account, download It’sMe™ mobile app and sign in with your account.
Log in to the Acceptto Admin Panel and navigate to Applications.
Click the New Application button to make an application for protecting the ADFS and get your UID and Secret codes.
Treat your UID and Secret code like any sensitive credential. Don't share it with unauthorized individuals or email it to anyone under any circumstances!
If you do not plan to use ADFS in an external facing environment, such as a proxy, configure the URL callback to point to https://mfa.acceptto.com. Also, note that you can create multiple applications to cover different relying parties.
Once the application is created, add usernames to the application by selecting the control “Usernames”. Add the usernames and emails of the users that are going to be logging in using AD FS.
Install “Remote Server Administration Tools” feature on the AD FS server.
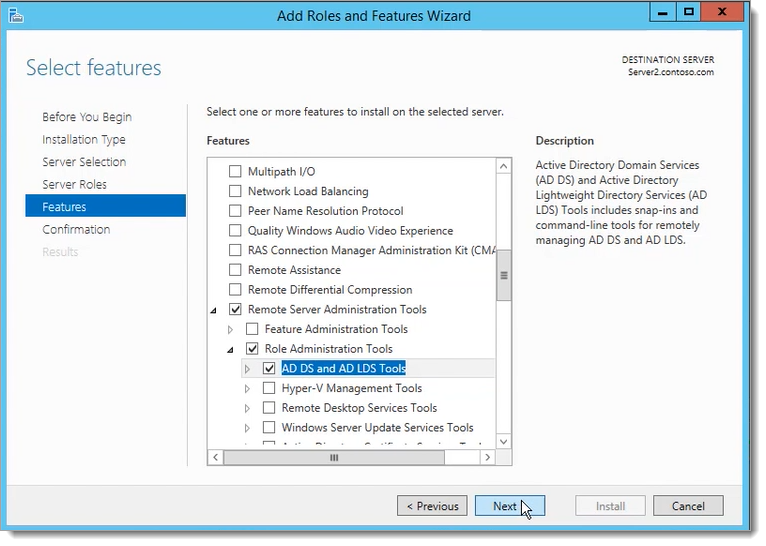
Install Acceptto AD FS MFA Authentication Provider
Run the Acceptto AD FS MFA authentication provider as a user with administrator privileges on each of your AD FS servers.
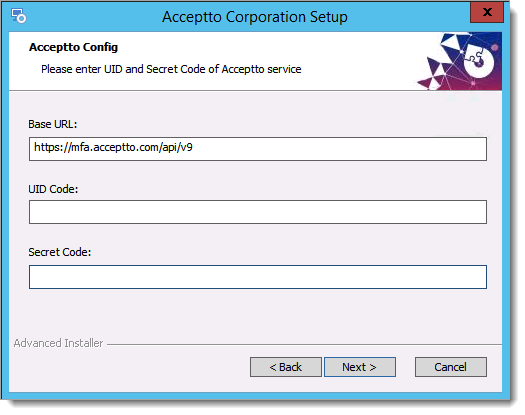
Enter your UID and Secret code that you obtained in the Initial Steps when you created the application and finish the installation. Then, restart the server.
Configure AD FS v3.0 Multi-factor Authentication
Launch the AD FS Management console on your server. Expand AD FS, click Authentication Policies and then click the Edit Global Multi-factor Authentication.
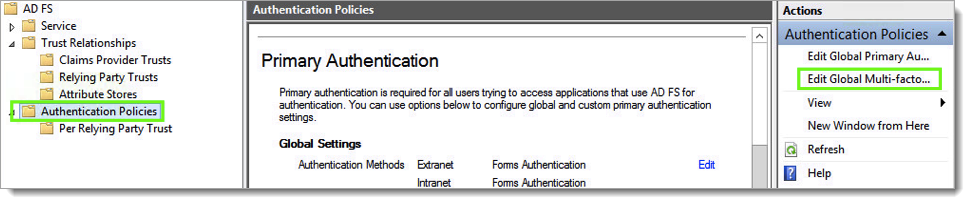
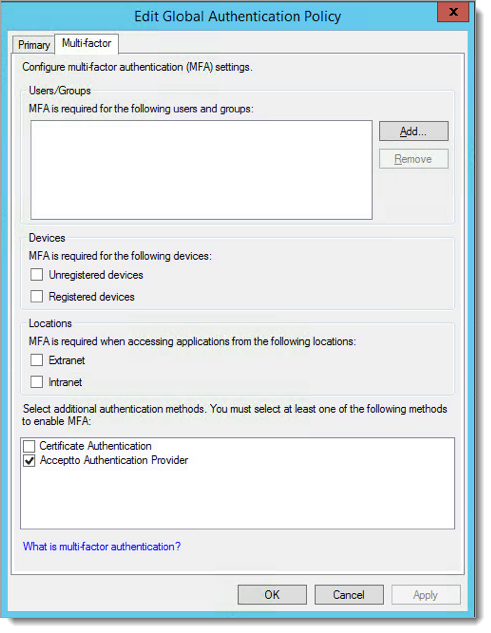
On multi-factor tab, check the box next to the Acceptto Authentication Provider and click OK.
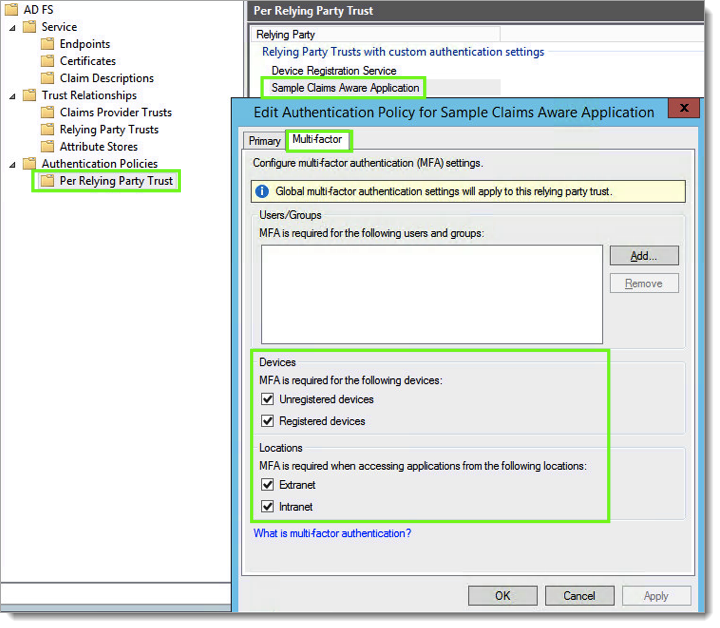
Expand Authentication Policies. Click Per relying Party Trust and Right-click the relying party where you want to apply Acceptto MFA. Choose Edit custom multi-factor Authentication. On the multi-factor tab, select the ‘Devices’ and ‘locations’ you need and click OK.
Configure AD FS v4.0 Multi-factor Authentication
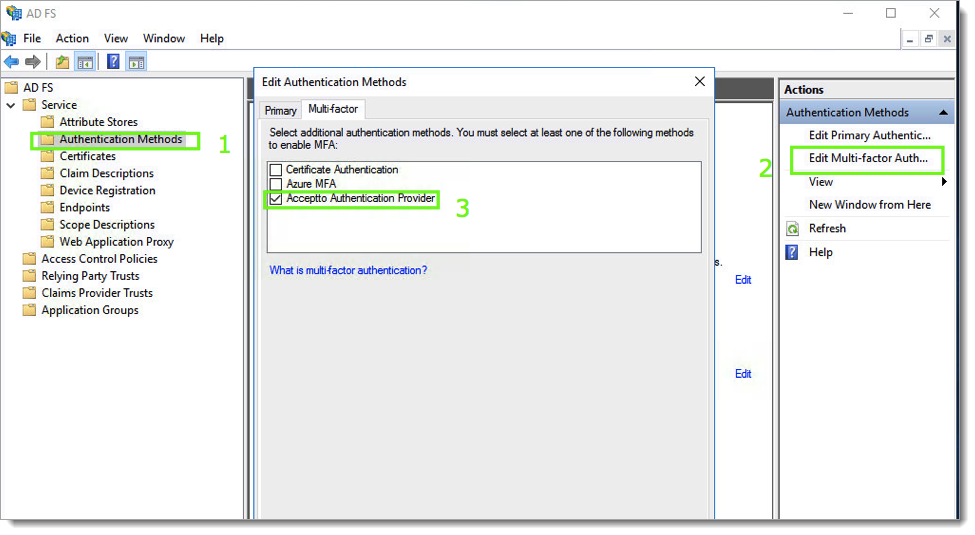
Launch the AD FS Management console on your server. Expand Services, click Authentication Methods and then click the Edit Multi-factor Authentication. Check the box next to the Acceptto Authentication Provider and click ok.
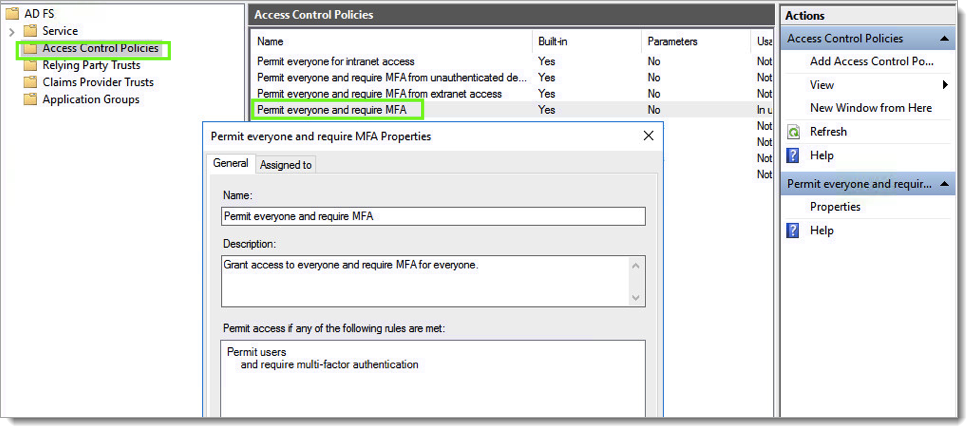
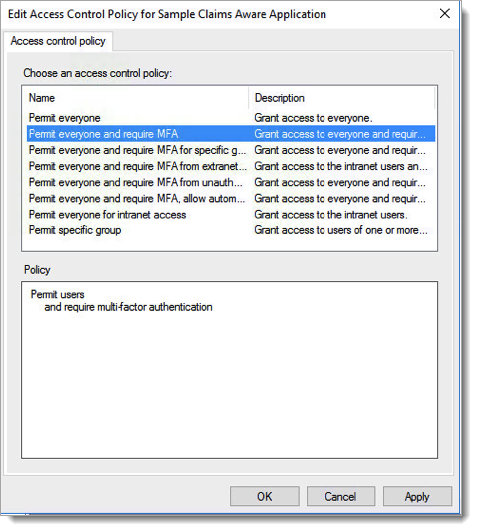
Go to Access Control Policies and either edit one of the existing MFA policies to apply it to users or groups or create a new MFA policy if no pre-defined one is sufficient for your organization's MFA requirements.
Go to Relying Party Trusts, right-click the relying party trust where you want to add Acceptto MFA, then select Edit Access Control Policy.
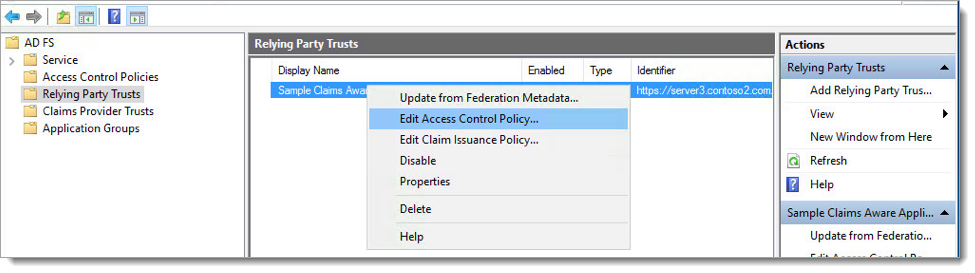
Select the preferred access control policy, then click OK.
Acceptto AD FS MFA Protection Installation is complete. You can now extend the Access Policy to other Relying Parties and increase their security by adding Acceptto Multi-Factor Authentication.
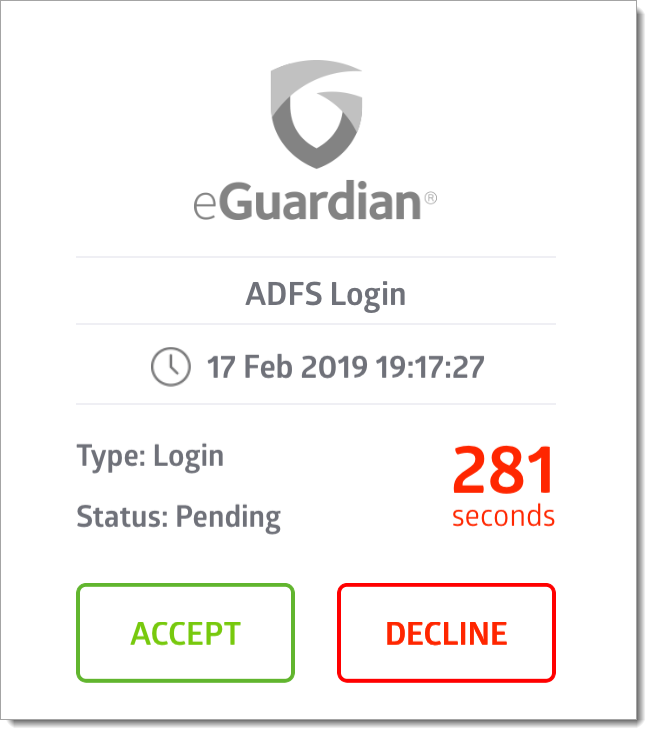
Test Your Setup
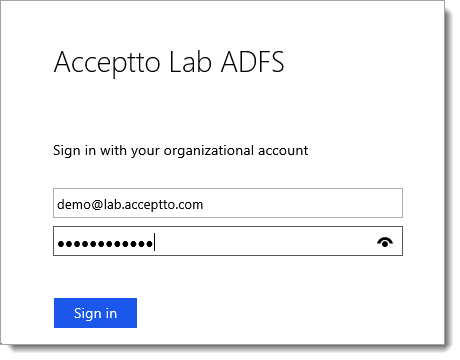
Open your browser and go to a relying party for your AD FS 3 or 4 deployment.
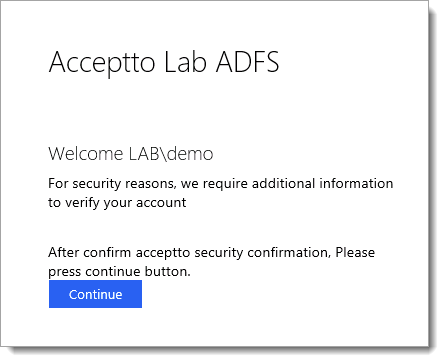
Log in with your user credentials and note that the user is now requested to perform Multi-Factor Authentication using the Acceptto It’sMe mobile application before access is allowed.
 |
 |
 |
Configure CSP policies
In Windows Server 2019, Microsoft introduced a new security feature to allow for custom HTTP headers to be sent by AD FS. As a result there are more restrictive policies around using an ADFS plugin.
You can inspect your current CSP policies by running the following command:
Get-AdfsResponseHeaders | Select -ExpandProperty ResponseHeaders
If your CSP policies are populated, then you need to make sure you also add the following rules so the ADFS plugin can work as expected:
script-src 'self' 'unsafe-inline' 'unsafe-eval' 'script-src-elem' https://*.jquery.com https://*.acceptto.com; connect-src wss://*.acceptto.com https://*.acceptto.com;"
This is an example of adding the above rules to the default CSP settings of a 2019 ADFS server:
Set-AdfsResponseHeaders -SetHeaderName "Content-Security-Policy" -SetHeaderValue "default-src 'self' 'unsafe-inline'; img-src 'self' data:; script-src 'self' 'unsafe-inline' 'unsafe-eval'; script-src-elem 'unsafe-inline' https://*.jquery.com https://*.acceptto.com; connect-src wss://*.acceptto.com https://*.acceptto.com;"
If you are running in an on-premises environment please contact our technical support for a list of updated endpoint addresses for your deployment.
Support
If you have questions or need assistance, contact SecureAuth Support.
Sales
Want to learn more about our MFA solutions? Contact our Professional Services for a demo today.
Disclaimer
All product names, trademarks, and registered trademarks are the property of their respective owners.
All company, product, and service names used in this document are for identification purposes only. The use of these names, trademarks, and brands do not constitute an endorsement by the SecureAuth Corporation.
Microsoft, Windows and AD FS are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries.