VMware Horizon RADIUS integration
Multi-Factor Authentication (MFA) is an extra layer of security used when logging into websites or apps. Individuals are authenticated through more than one required security and validation procedure that only they know or have access to.
RADIUS is a protocol commonly used to authenticate, authorize, and account for user access and actions. Acceptto offers a simple solution for adding MFA to VMware Horizon via its Radius solution. This document is a step-by-step guide to connect your VMware Horizon structure to the Acceptto Radius agent.
Prerequisites
Acceptto RADIUS Agent that is configured and connected to your user directory. For example, Microsoft Active Directory (AD).
For more information, see the Acceptto RADIUS deployment guide.
A user with administrative privileges for the VMware Horizon Connection Server.
Configure the Acceptto RADIUS Agent
To integrate Acceptto with your VMware Horizon structure, you will need to install an Acceptto RADIUS Agent on a machine within your network. This server will receive RADIUS requests from your Horizon server, check with LDAP server to perform primary authentication, and then contact Acceptto cloud service for secondary authentication.
Log into the Acceptto RADIUS Agent with an administrative user and open the radius-agent-config.env file with an editor. It is located in the installed directory of RADIUS Agent. RADIUS clients are configured in this setting.
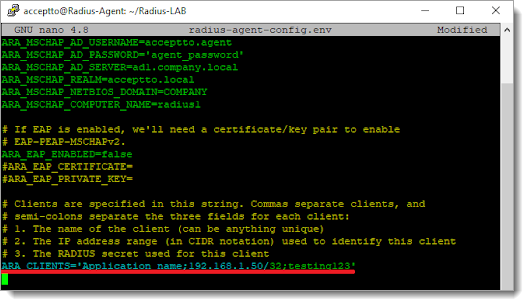
Go to the bottom of radius-agent-config.env file and change the ARA_CLIENTS attribute as follows. The values should be separated by semicolons (;).
ARA_CLIENTS = An optional name for your Horizon; IP address of your Horizon server; a shared secret
An example configuration might look like this:
ARA_CLIENTS = Horizon;192.168.10.10/32;testing12345
Save the file and run the following command to set changes:
docker-compose down && docker-compose up -d
Configure VMware Horizon Connection Server
Sign in to the Horizon Administrator Console.
Navigate to “Servers” and then “Connection Servers”.
Click Edit.
In the dialog window, select the Authentication tab. Scroll down to the "Advanced Authentication” section.
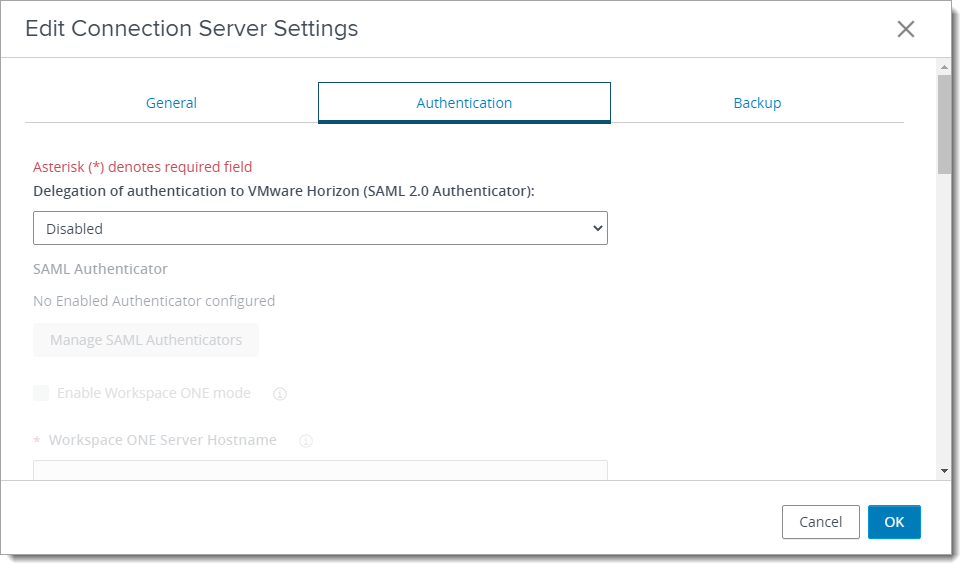
Select RADIUS in the "2-factor authentication" drop-down list. Enable both “Enforce 2-factor and Windows user name matching” and “Use the same username and password for RADIUS and Windows authentication”.
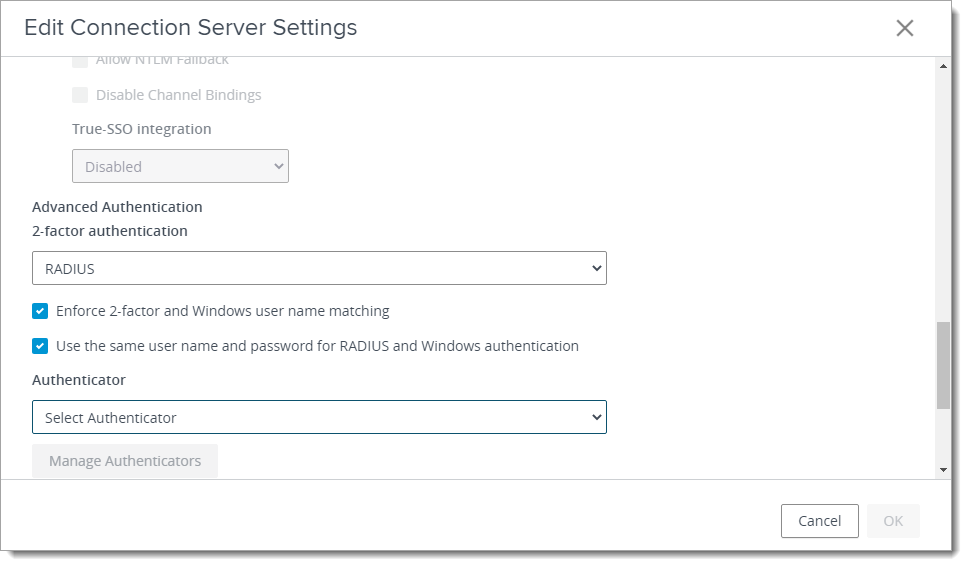
In the Authenticators section, select “Create New Authenticator” and fill the form based on the following table. Type a name of your choice for Authenticator Name.
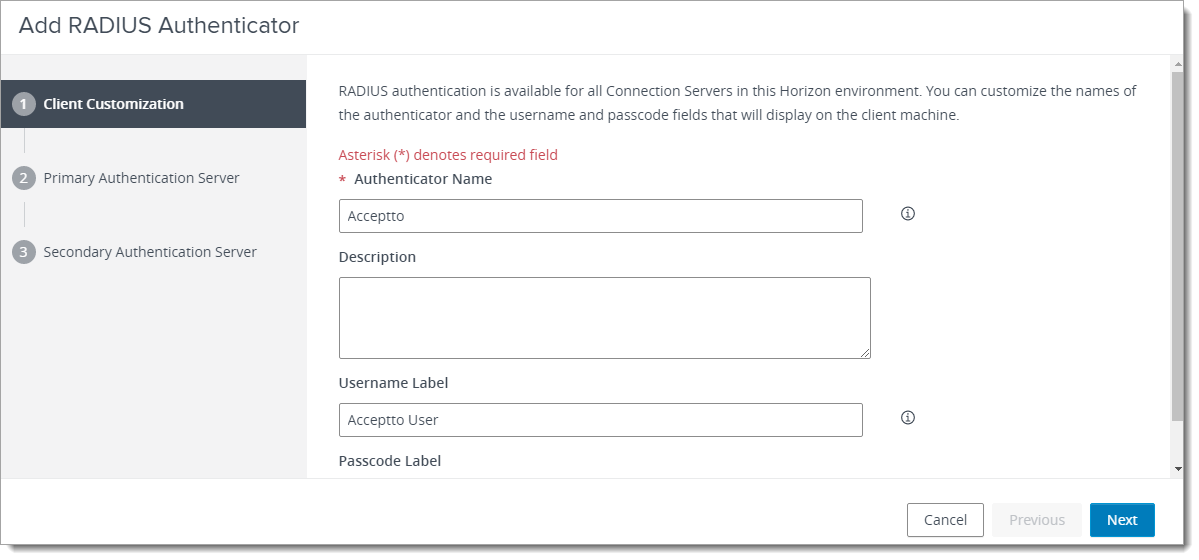
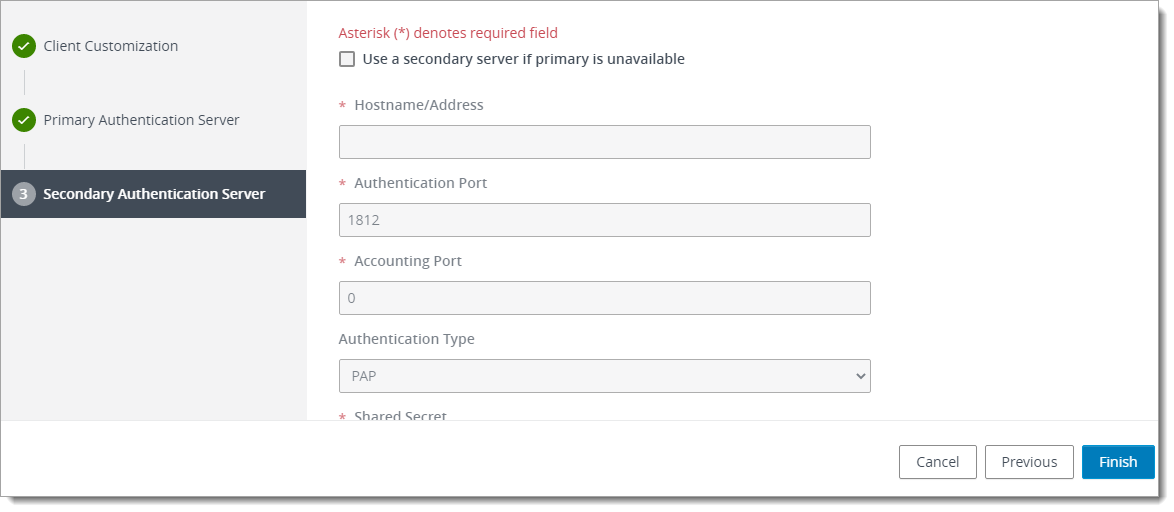
Click Next and fill the rest of fields regards to the below table:
Hostname/Address: IP/Name of Acceptto RADIUS Agent configured in the previous section
Authentication port: The RADIUS port (default is 1812)
Accounting port: 0
Authentication type: PAP
Shared secret: The RADIUS secret you configured in the previous section
Server Timeout: 60
Test your application integration
Launch the VMware Horizon Client. Initiate a connection to the Server and enter your primary credentials.
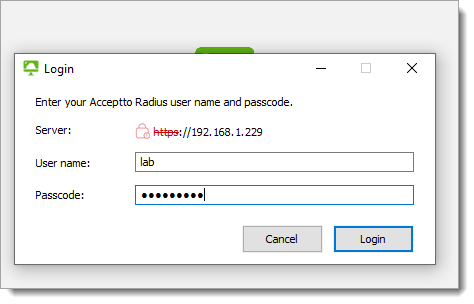
Your It’sMe app will show a notification. After verification, access will be provided to your virtual desktop environment.
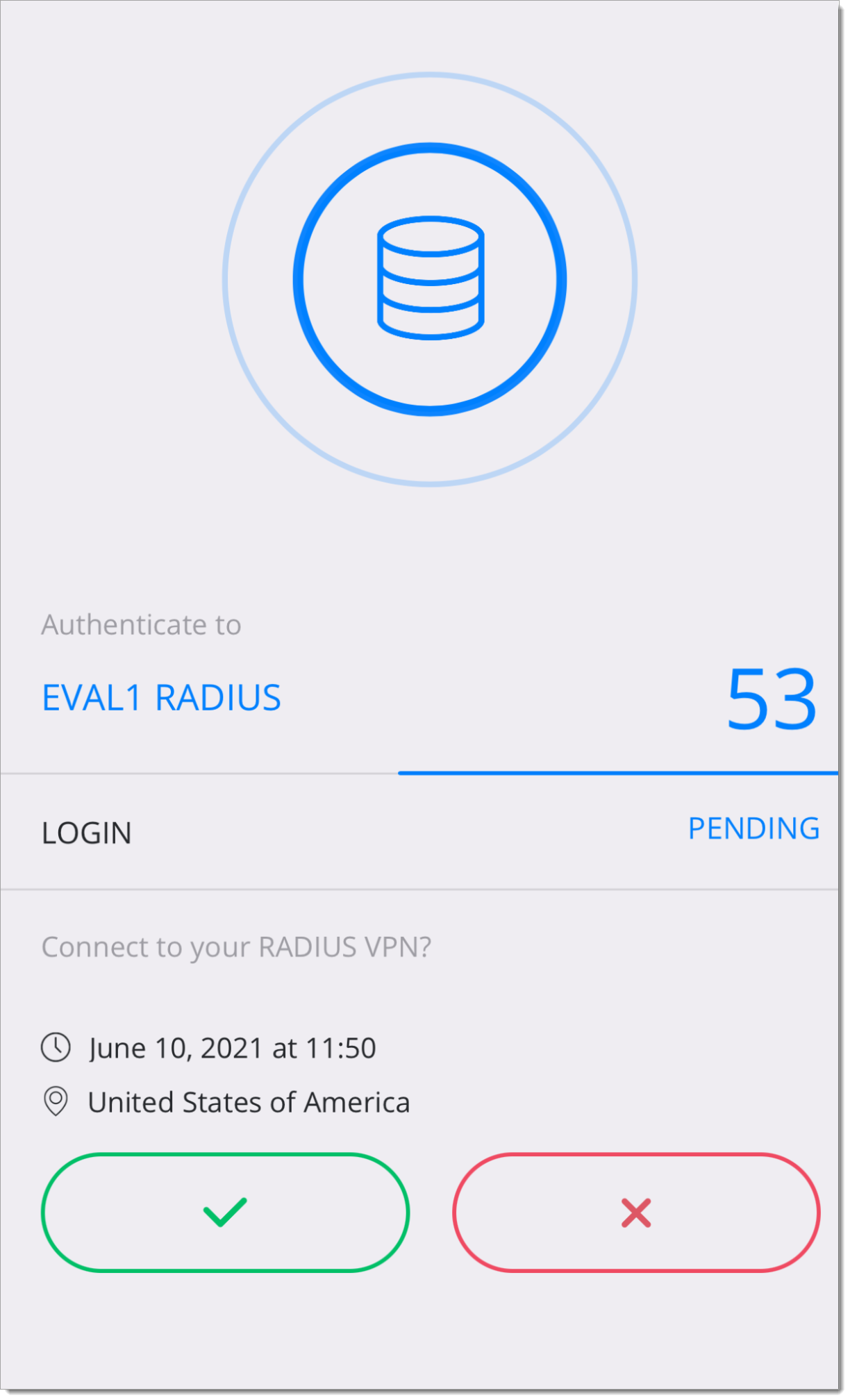
Support
If you have questions or need assistance, contact SecureAuth Support.
Sales
Want to learn more about our MFA solutions? Contact our Professional Services for a demo today.
Disclaimer
All product names, trademarks, and registered trademarks are the property of their respective owners.
All company, product, and service names used in this document are for identification purposes only. The use of these names, trademarks, and brands do not constitute an endorsement by the SecureAuth Corporation.