PingFederate IdP factor MFA integration
Acceptto integrates with PingFederate to enable increased security with Acceptto's intelligent Multi-factor Authentication. This integration uses PingFederate's IdP Adapter Plugin feature to enable Acceptto intelligent MFA.
This allows administrators to configure their PingFederate SSO applications to require Acceptto's Smart MFA before authenticating users.
Acceptto's intelligent MFA uses many different signals to provide a low-friction increase in security.
Prerequisites
An Acceptto account with a configured Identity Provider.
A user with administrative privileges for the PingFederate admin panel.
A user with administrative privileges for the Acceptto services.
The Acceptto SAML Metadata XML file for your account.
The Acceptto PingFederate Idp Adapter
Install the Acceptto PingFederate Idp Adapter plugin
Download the Acceptto PingFederate Idp Adapter plugin JAR file.
Install the JAR file in the deploy directory for your PingFederate instance.
Restart the PingFederate server.
Add a new IdP Adapter instance
The Acceptto SAML Metadata XML File is the SAML metadata for your account, it can be found at https://sso.acceptto.com/my-organization/saml/metadata.xml (where my-organization is the short name assigned by Acceptto to identify your organization).
In the PingFederate admin panel, add a new Idp Adapter instance.
Select Authentication > IdP Adapters > Create New Instance
Fill in the Type form with the following:
Instance Name: Acceptto (or your preferred name)
Instance Id: acceptto (or your preferred id)
Type: Acceptto IdP Adapter
Parent Instance: None
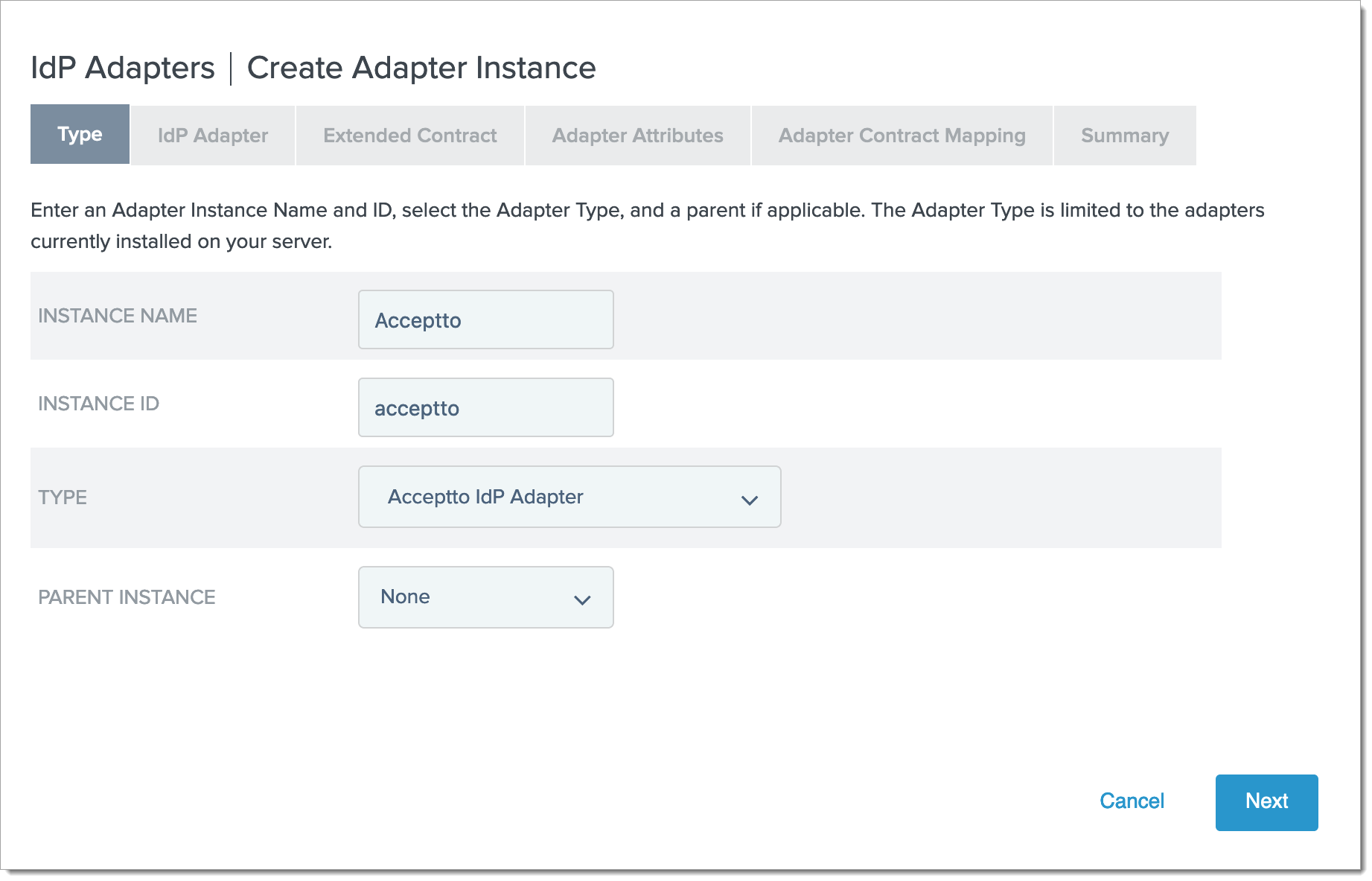
Click Next
Fill in the IdP Adapter form with the following:
Application Issuer ID: PingFederate Acceptto Plugin (or your preferred name).
Application Metadata File: Upload the Metadata XML file.
SP Certificate: Use an existing certificate, or use the "Manage Signing Certificates" button to create a new one.
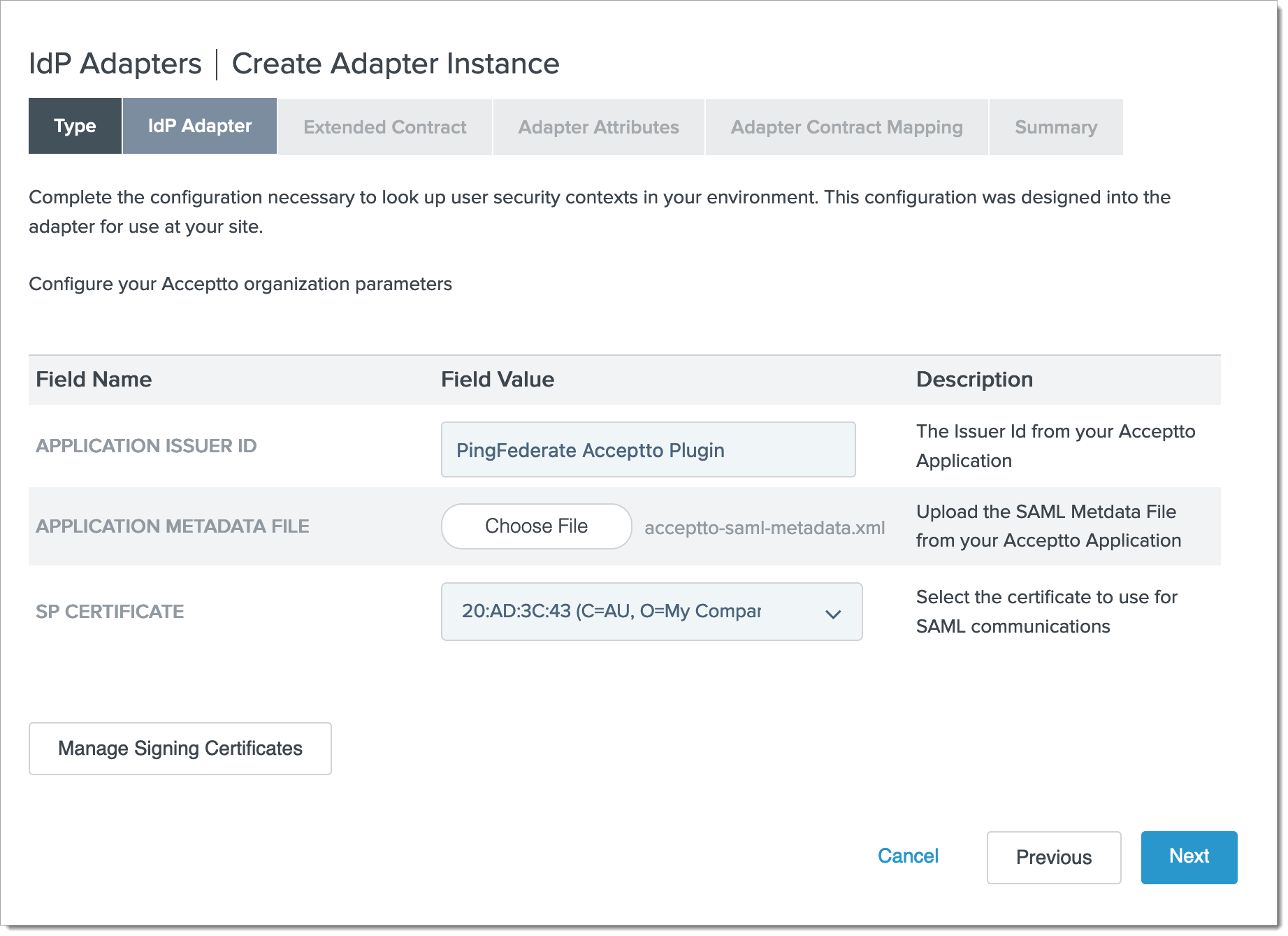
Click Next
Click Next on the Extended Contract form
Fill in the Adapter Attributes form with the following:
Unique User Key Attribute: email
Check the Pseudonym checkbox for email
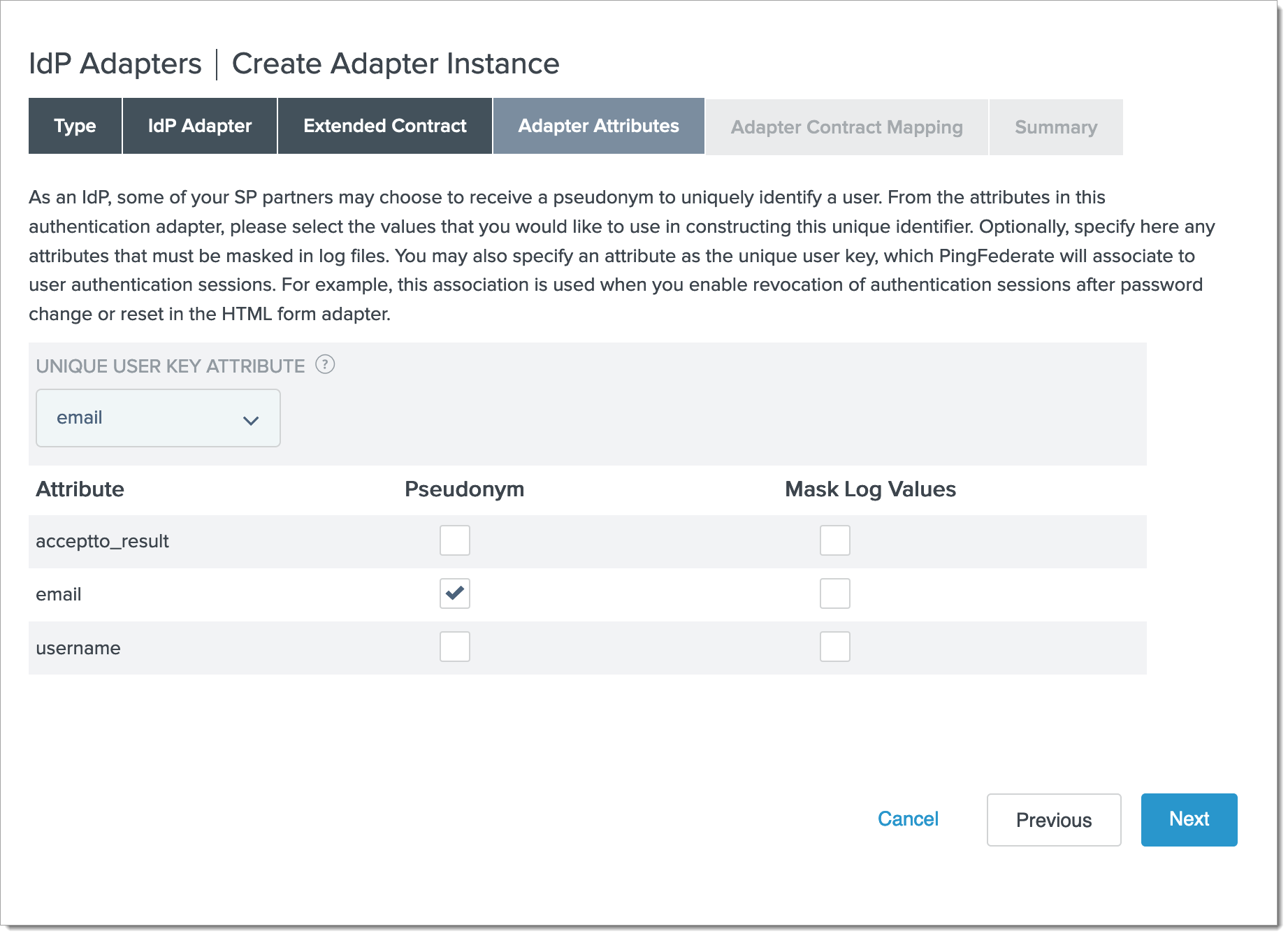
Click Next
Click Configure Adapter Contract
Click Next on Attribute sources & User Lookup
Fill in the Adapter Contract Fulfillment form with the following sources:
acceptto_result: Adapter
email: Adapter
username: Adapter
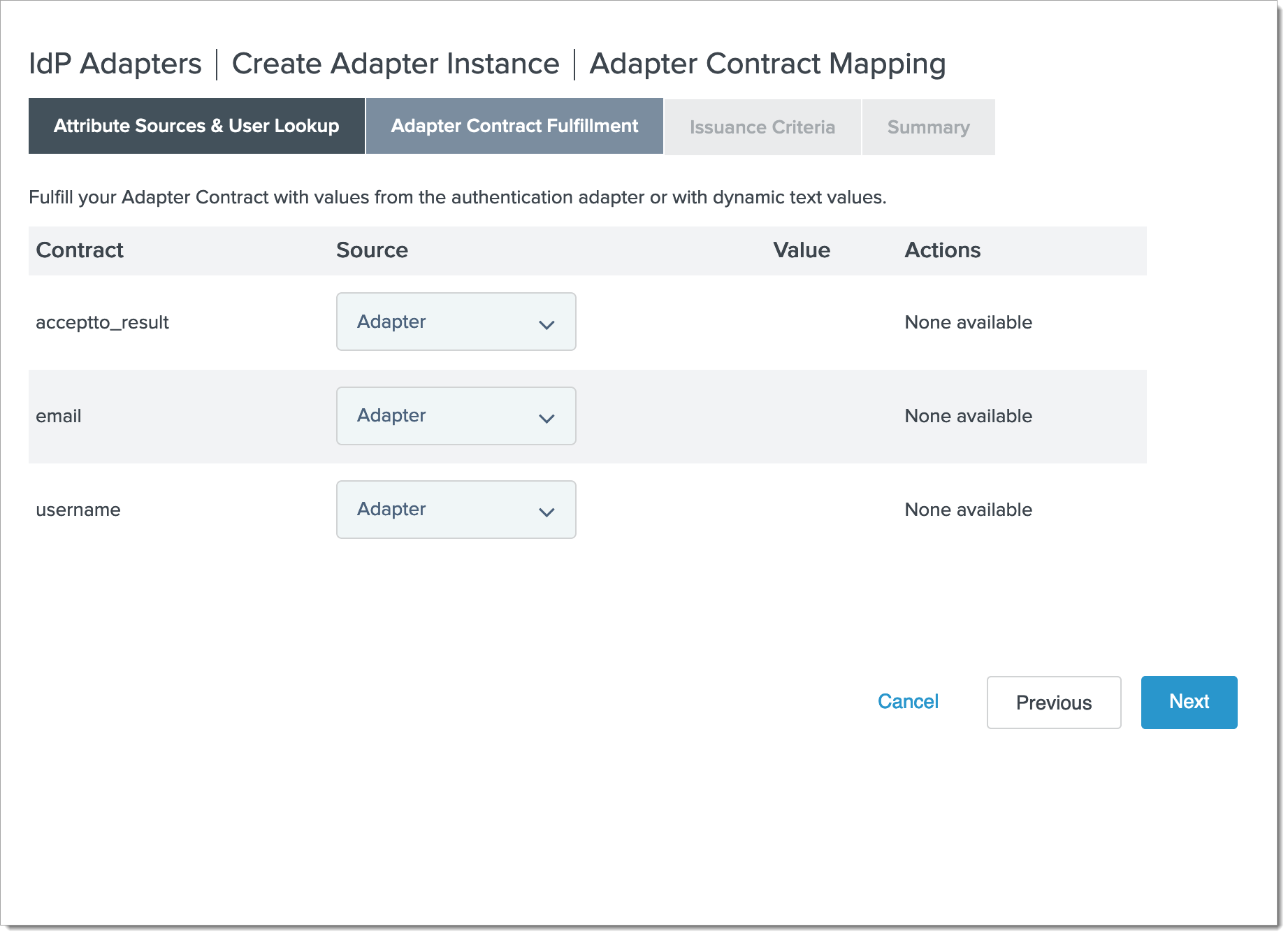
Click Next
Click Next on Issuance Criteria
Click Done
Click Next
Click Save
Add Chained Adapter
In order to enable Acceptto's MFA after initial authentication, we use a chained adapter.
Select Authentication > IdP Adapters > Create New Instance
Fill in the Type form with the following:
Instance Name: Chained Acceptto (or your preferred name)
Instance Id: chained (or your preferred name)
Type: Composite Adapter
Parent Instance: None
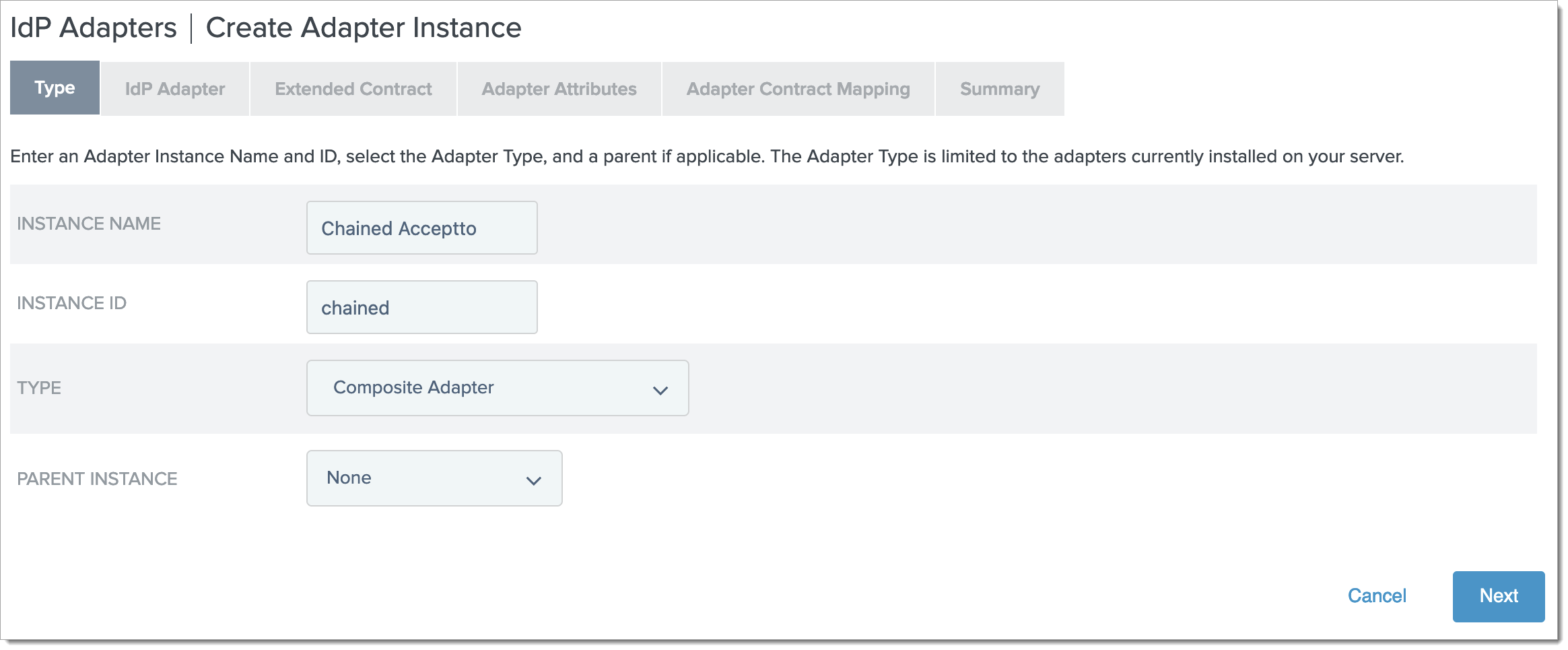
Click Next
Fill in the sections on the IdP Adapter form as follows:
Adapters
Click "Add a new row to 'Adapters'"
Set the Adapter Instance to HTMLFormPD (or your primary authentication adapter)
Click Update
Click "Add a new row to 'Adapters'"
Set the Adapter Instance to Acceptto (or the name you chose for the adapter instance)
Click Update
Input User ID Mapping
Click "Add a new row to 'Input User ID Mapping'"
Select HTMLFormPD (or your primary authentication adapter)
Select username
Click Update
Click "Add a new row to 'Input User ID Mapping'"
Select Acceptto (or the name you chose for the adapter instance)
Select email
Click Update
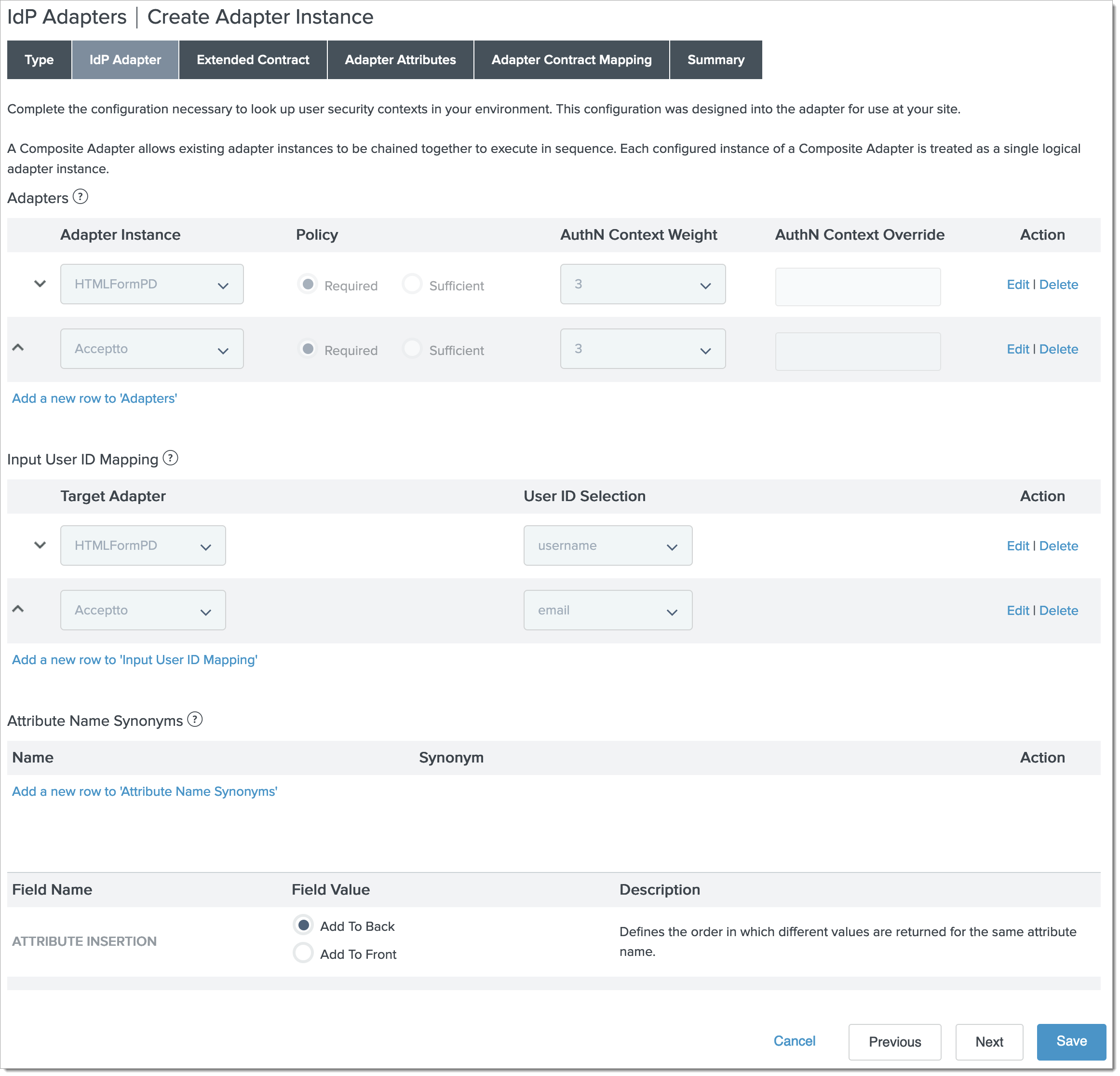
Click Next
Fill in the Extended Contract form as follows:
Under Extend the Contract enter username
Click Add
Under Extend the Contract enter email
Click Add
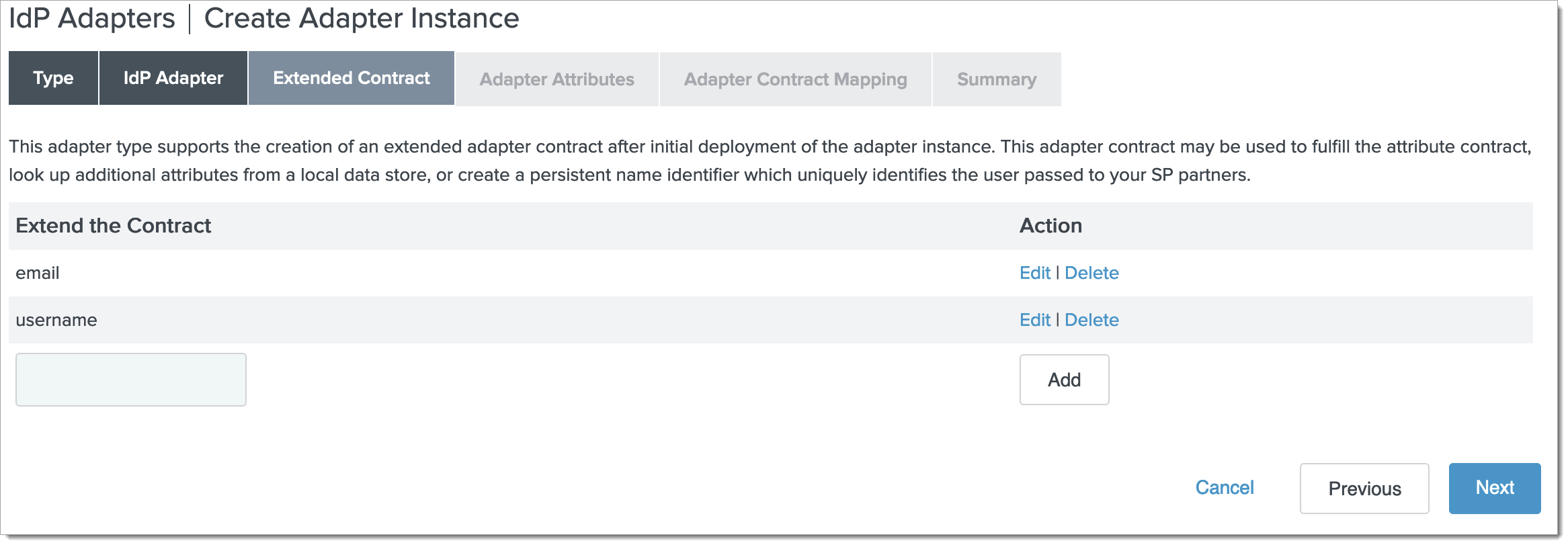
Click Next
Fill in the Adapter Attributes form as follows:
Unique User Key Attribute: email
Check the Pseudonym checkbox for email

Click Next
Click Configure Adapter Contract
Click Next on Attribute sources & User Lookup
Fill in the Adapter Contract Fulfillment form with the following sources:
acceptto_result: Adapter
email: Adapter
username: Adapter

Click Next
Click Next on Issuance Criteria
Click Done
Click Next
Click Save
Add Application to Acceptto
Add PingFederate IdP Factor as a service provider in the Acceptto admin panel. Some required information can be found in PingFederate.
In the eGuardian user dashboard, select Applications > Create New Application
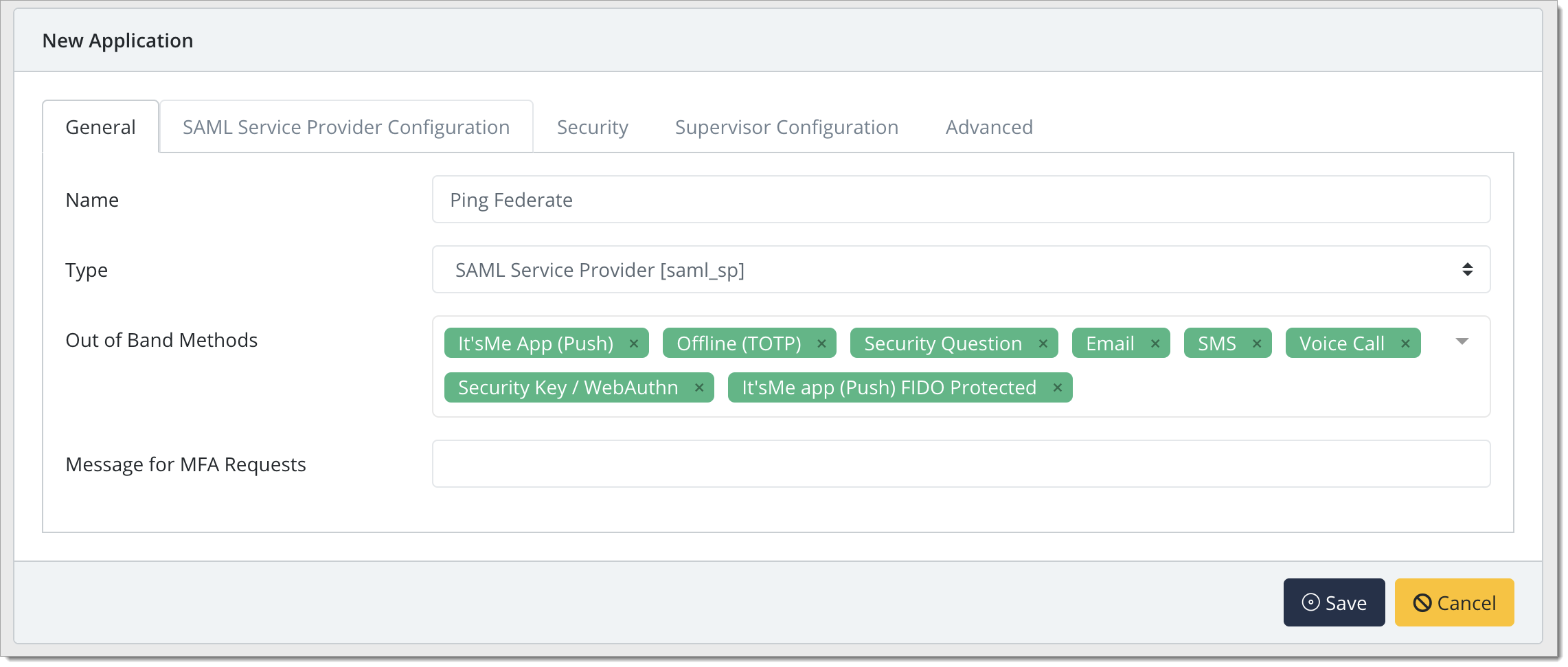
In the New Application form, enter the following values under the General tab
Name - Ping Federate (or your preferred name)
Type - Select "SAML Service Provider" from the options
Out of Band Methods - Select the allowed methods for approving MFA requests
Message for MFA Requests - Enter the user-facing message for Push, SMS, and e-mail MFA requests (optional)
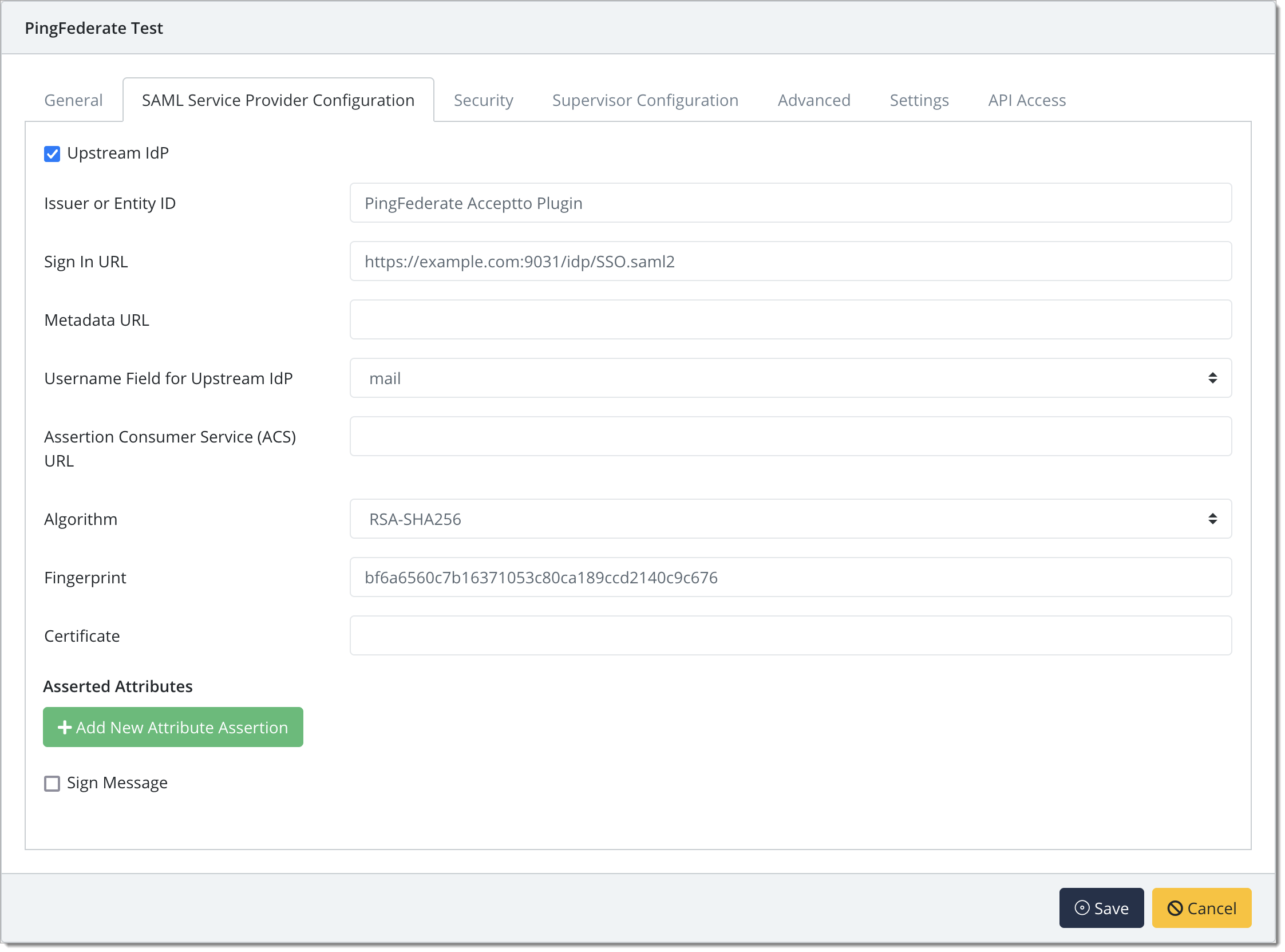
Under the SAML Service Provider Configuration tab, enter the following values
Select the checkbox for Upstream IdP
Issuer or Entity ID – The Application Issuer ID from PingFederate
Sign in URL - From PingFederate
Metadata URL - Leave blank
Username Field for Upstream IdP - mail
Assertion Consumer Service (ACS) URL - Leave blank
Certificate - the X.509 public certificate from PingFederate
Configure additional settings as desired, then click Save
User Experience
After the admin has enabled IdP factor MFA, the user will be prompted to add this custom factor on their next login via PingFederate.
The user then selects the IdP Factor option and is taken to a QR pairing screen.
They can then download the Acceptto It'sMe mobile application from Google Play Store or Apple App Store.
The user opens the mobile application and is prompted to scan the displayed QR code.
After scanning the QR the user's device is paired.
On subsequent authentication attempts, the user will be asked to confirm the Idp factor MFA and be taken to the select MFA option by PingFederate.
Upon approval of MFA, the user will be authenticated to their application.