Okta IdP factor MFA integration
Acceptto integrates with Okta to enable increased security with Acceptto's intelligent Multi-factor Authentication. This integration uses Okta's Custom IdP Factor Authentication feature to enable Acceptto's intelligent MFA.
This allows administrators to configure their Okta SSO applications to require Acceptto's Smart MFA before authenticating users.
Acceptto's intelligent MFA uses many different signals to provide a low-friction increase in security.
Prerequisites
An Acceptto account with a configured Identity Provider and LDAP Agent.
For more information, see the LDAP Agent deployment guide.
A user with administrative privileges for the Okta panel.
A user with administrative privileges for the Acceptto services.
Okta's IdP Factor must be enabled as a multifactor type.
The Acceptto Base URL for your account.
Add a new IdP
In the Okta admin panel, add a new SAML Identity Provider. The Base URL is the SSO landing page for your account, in the format https://sso.acceptto.com/my-organization.
Select Security > Identity Providers
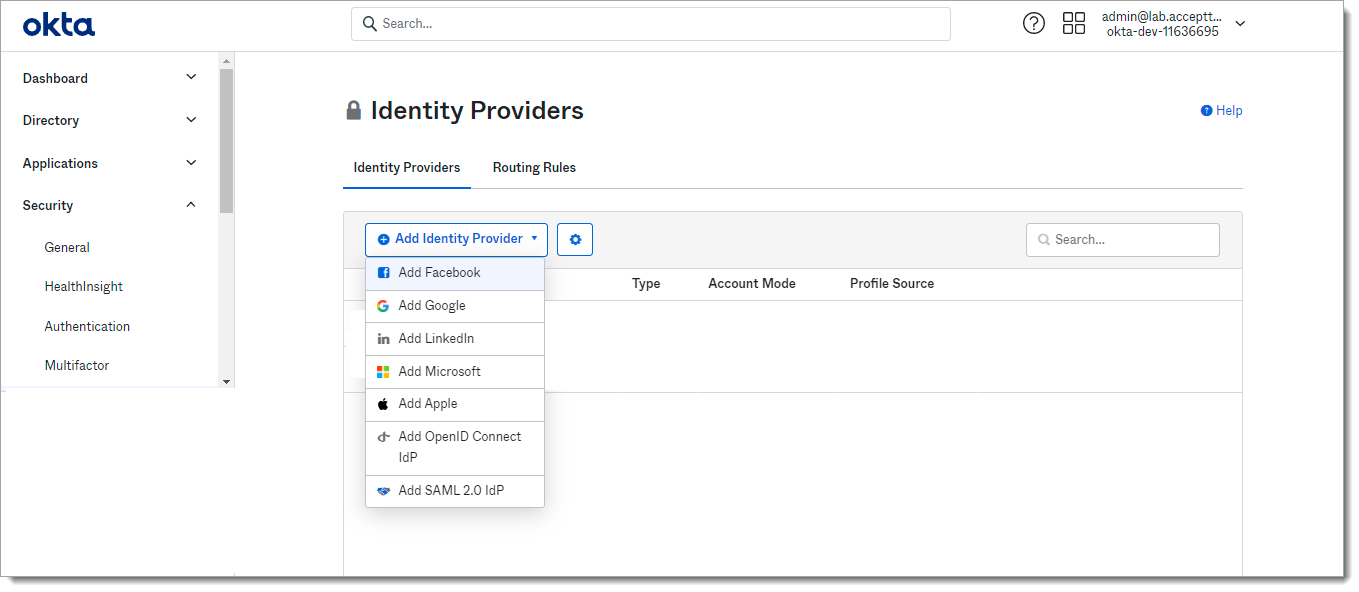
Click on Add Identity Provider button and select Add SAML 2.0.
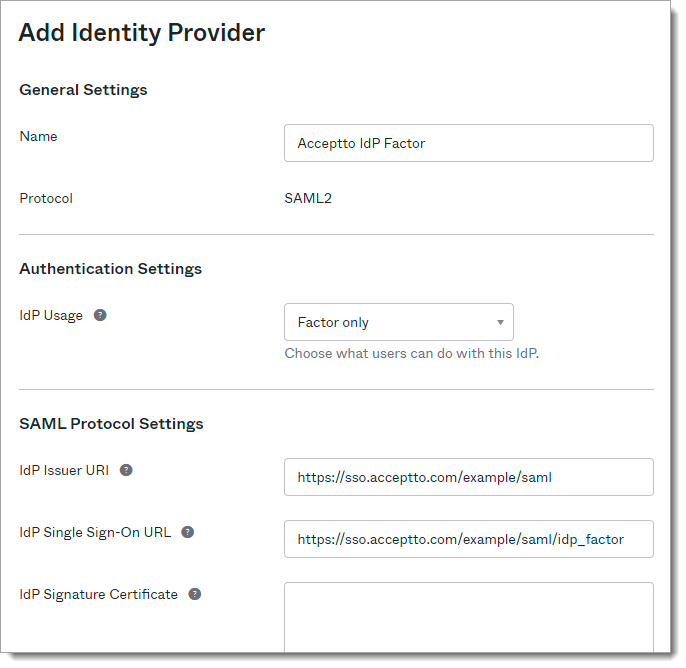
Fill in the Add Identity Provider form with the following:
Name: Acceptto IdP Factor (or your preferred name)
IdP Usage: Factor only
IdP Issuer URI: [Base URL]/saml
IdP Single Sign-On URL: [Base URL]/saml/idp_factor
IdP Signature Certificate: Download certificate at [Base URL]/saml/download/cert
Click Add Identity Provider to save.
Configure IdP Factor MFA
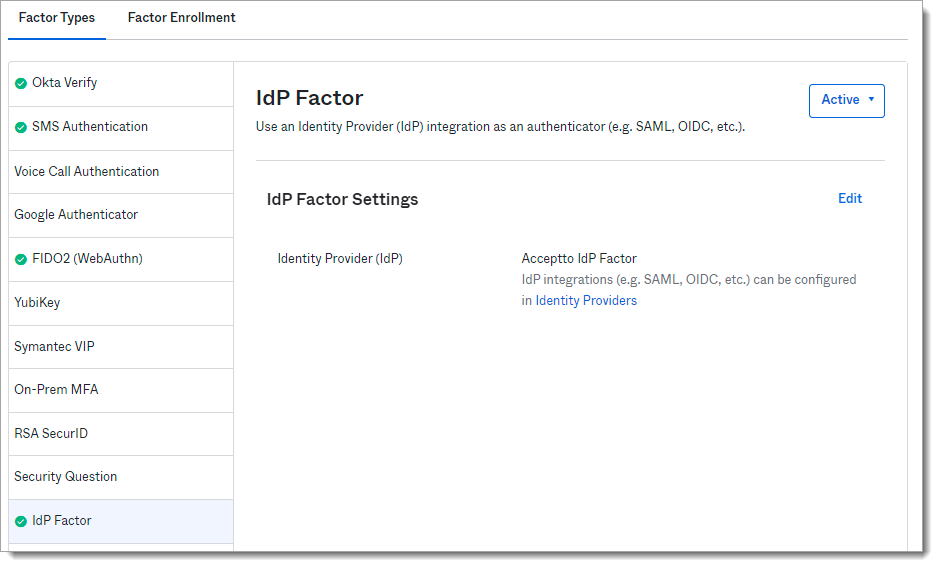
In the Okta admin panel, add the IdP as a custom MFA factor.
Select Security > Multifactor > IdP Factor
Click Edit
Select the Identity Provider that was created in the previous section (e.g. Acceptto IdP Factor)
Set Sign On Policy for Application
In the Okta admin panel, add a sign on policy to your application to force MFA for application logins.
Select the Applications menu then click the application you would like to enable Acceptto MFA for.
In the application settings click Sign On.
In the Sign On Policy section select click Add Rule.
Under Actions click the checkbox for Prompt for factor and select Every Sign on.
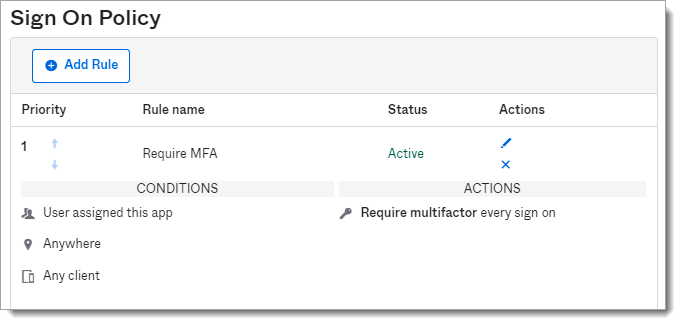
Click Save.
Add Application to Acceptto
Add Okta IdP Factor as a service provider in the Acceptto admin panel. Some required information can be found in Okta under Security > Identity Providers by clicking on the arrow next to the Acceptto Identity Provider that was created earlier.
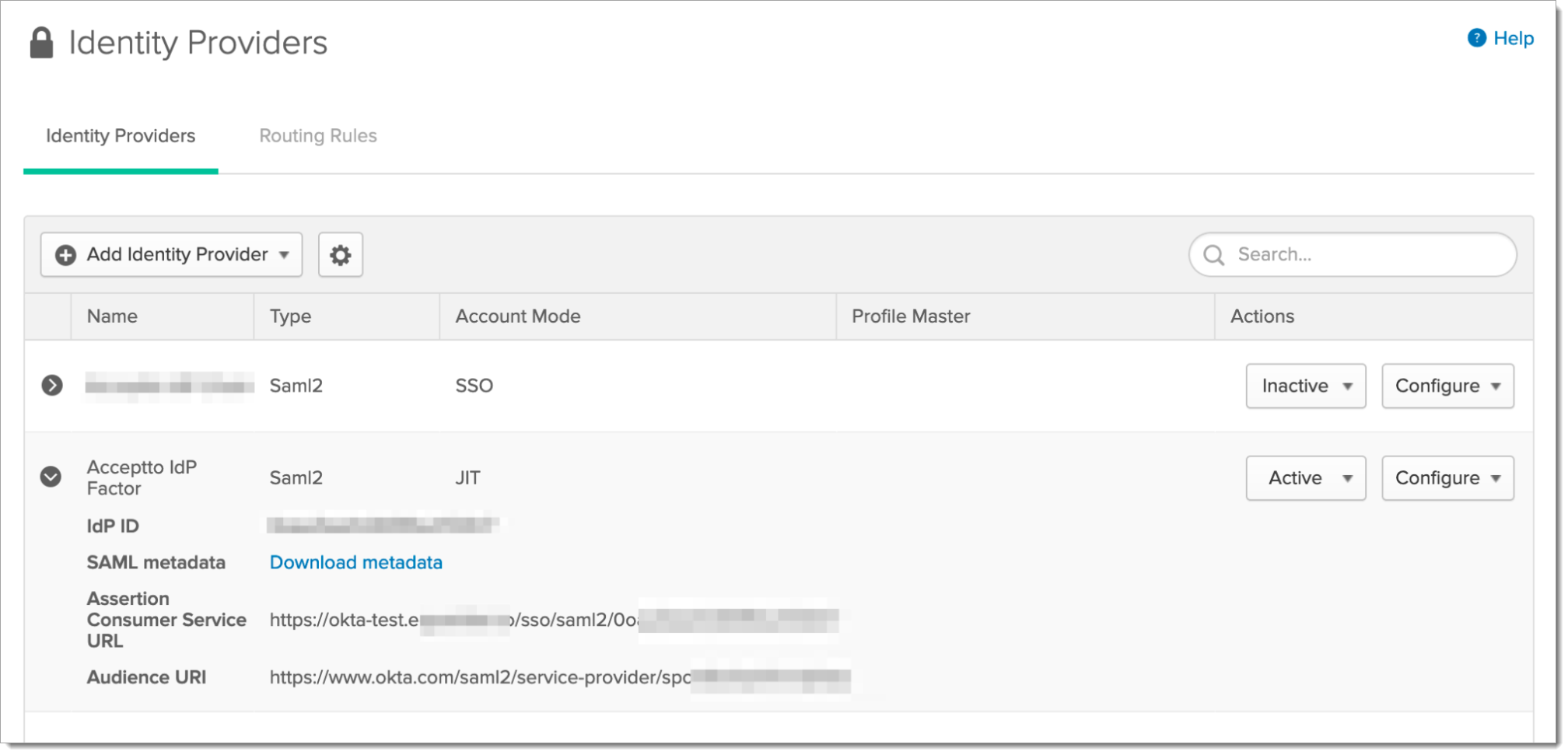 |
Login to the Acceptto Dashboard with an administrative account and go to Applications.
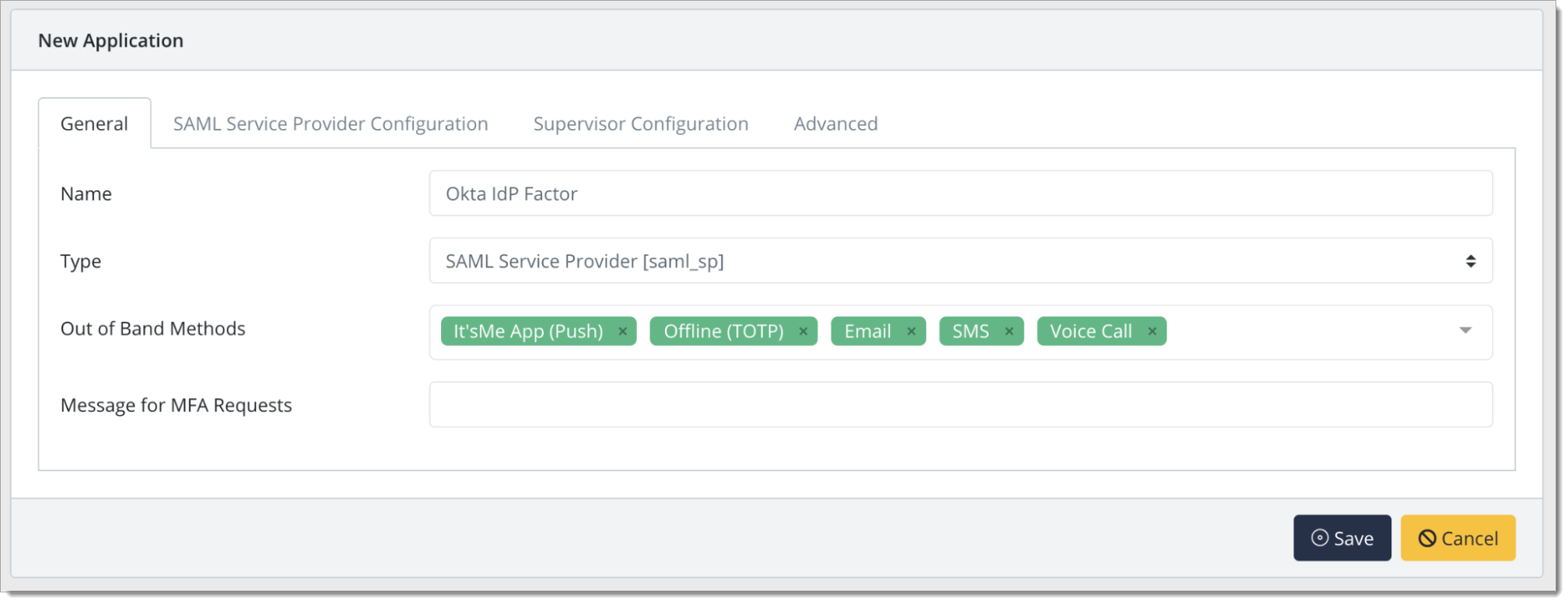
In the New Application form, enter the following values under the General tab.
Name - The application name displayed in the admin panel and application portal and used for push notifications and audit logs. (e.g. Okta Idp Factor)
Type - Select "SAML Service Provider" from the options
Out of Band Methods - Select the allowed methods for approving MFA requests
Message for MFA Requests - Enter the user-facing message for Push, SMS, and e-mail MFA requests (optional)
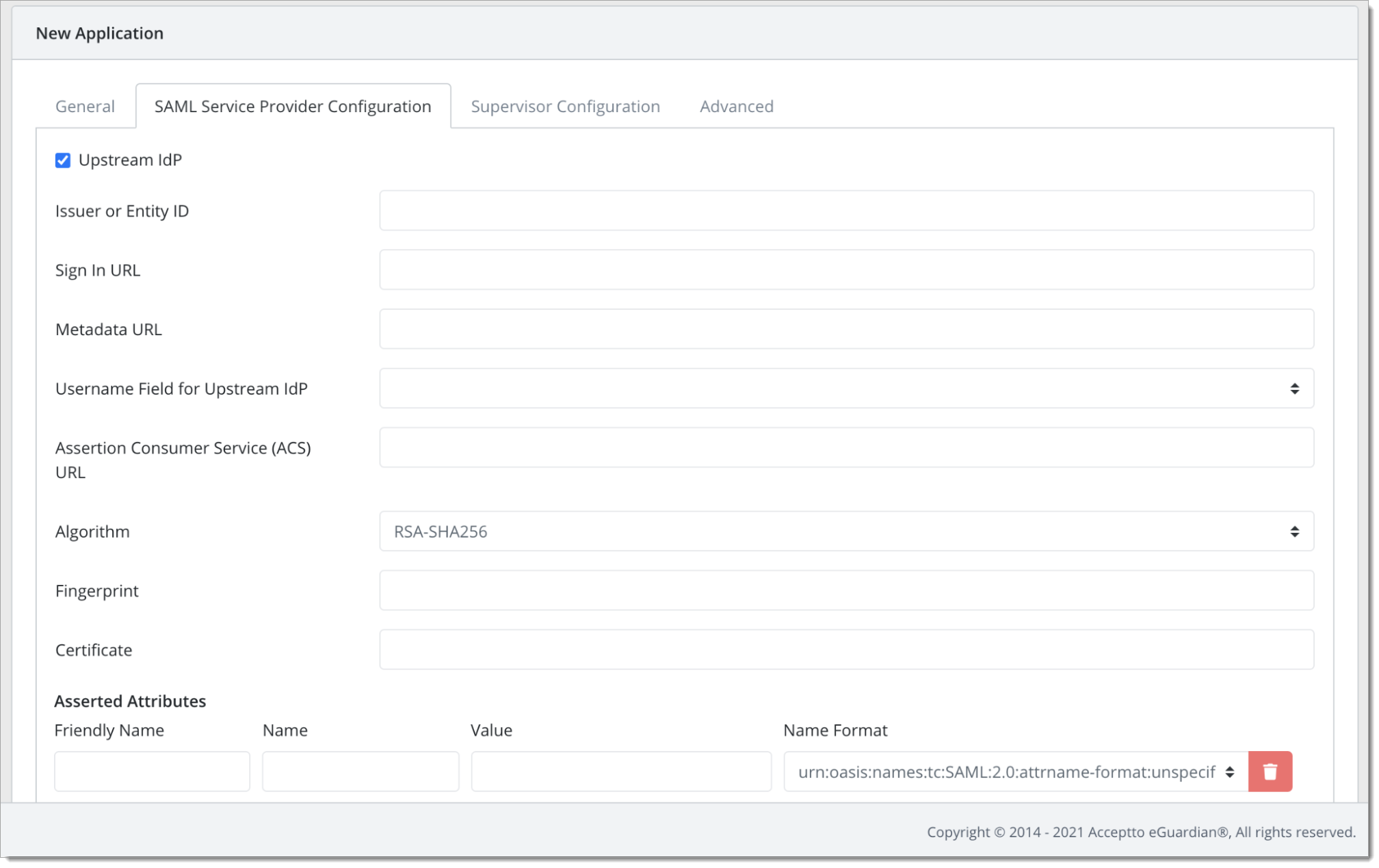
Under the SAML Service Provider Configuration tab, enter the following values
Select the checkbox for Upstream IdP
Issuer or Entity ID – The Audience URI from Okta
Sign in URL - The Audience URI from Okta
Metadata URL - Copy the URL from Download Metadata on Okta
Username Field for Upstream IdP - Select the Active Directory field that is configured as your organization's Okta username
Assertion Consumer Service (ACS) URL - Copy the Assertion Consumer Service URL from Okta
Certificate - Enter the X.509 public certificate from Okta.
Configure additional settings as desired, then click Save
User experience
After the admin has enabled IdP factor MFA, the user will be prompted to add this custom factor on their next login via Okta.
The user then selects the IdP Factor option and is taken to a QR pairing screen.
They can then download the Acceptto It'sMe mobile application from Google Play Store or Apple App Store.
The user opens the mobile application and is prompted to scan the displayed QR code.
After scanning the QR the user's device is paired.
On subsequent authentication attempts, the user will be asked to confirm the Idp factor MFA and be taken to the select MFA option by Okta.
Upon approval of MFA, the user will be authenticated to their application.
Support
If you have questions or need assistance, contact SecureAuth Support.
Sales
Want to learn more about our MFA solutions? Contact our Professional Services for a demo today.
Disclaimer
All product names, trademarks, and registered trademarks are the property of their respective owners.
All company, product, and service names used in this document are for identification purposes only. The use of these names, trademarks, and brands do not constitute an endorsement by the SecureAuth Corporation.