Adaptive authentication rules settings in a policy
Set your adaptive authentication rules to prompt or skip multi-factor authentication (MFA) in a policy. Each policy must have a minimum of two authentication rules. Rules are honored from top to bottom.
With a policy open in edit mode, select the Authentication Rules tab.
When modifying a rule, you can do any of the following:
Select Prompt for MFA (require another form of authentication) or Skip MFA (allow access) when the user login invokes this rule.
Click and hold the 8-dot icon on the left to drag and drop a rule up and down to change its hierarchy in the list.
To remove a rule, click the minus icon.
To change the properties of the rule, click the blue rule link.
To add a new rule, click Add New Rule and choose from the following rule types:
Dynamic Perimeter
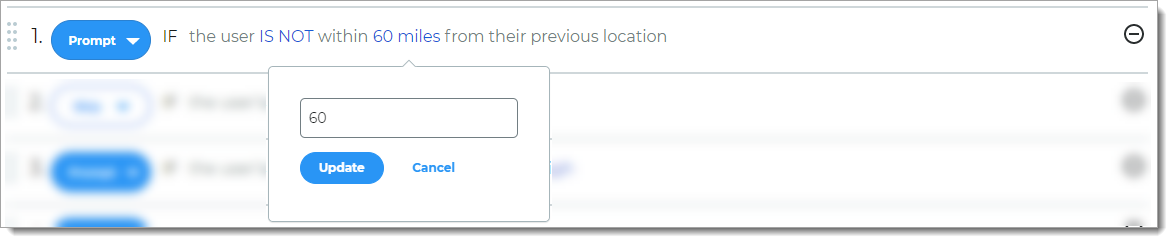
Rule to determine access based on whether the user login is or is not within a set distance from the previous location.
For example, if the user login is more than 60 miles from the previous location, then the user is prompted for another form of authentication.
Country
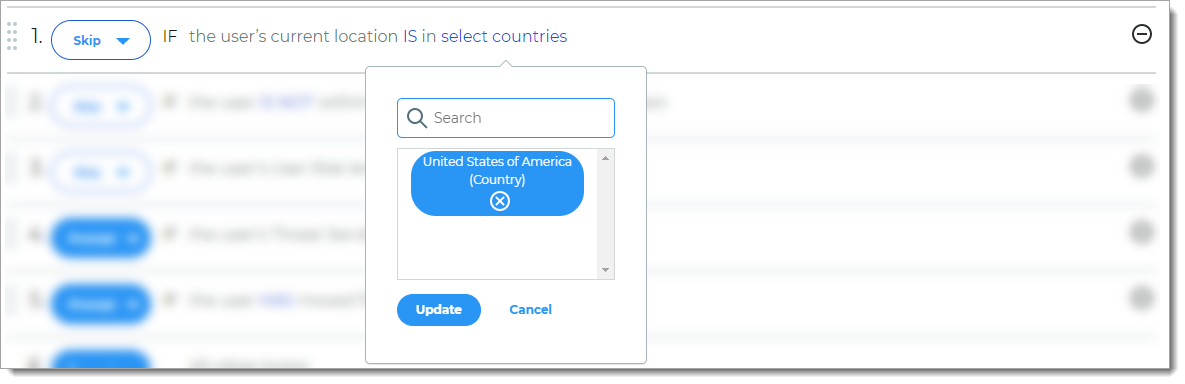
Rule to determine access based on whether the user login is or is not within a defined country.
For example, if the user login is in the United States, then the user is allowed access.
Geo-velocity
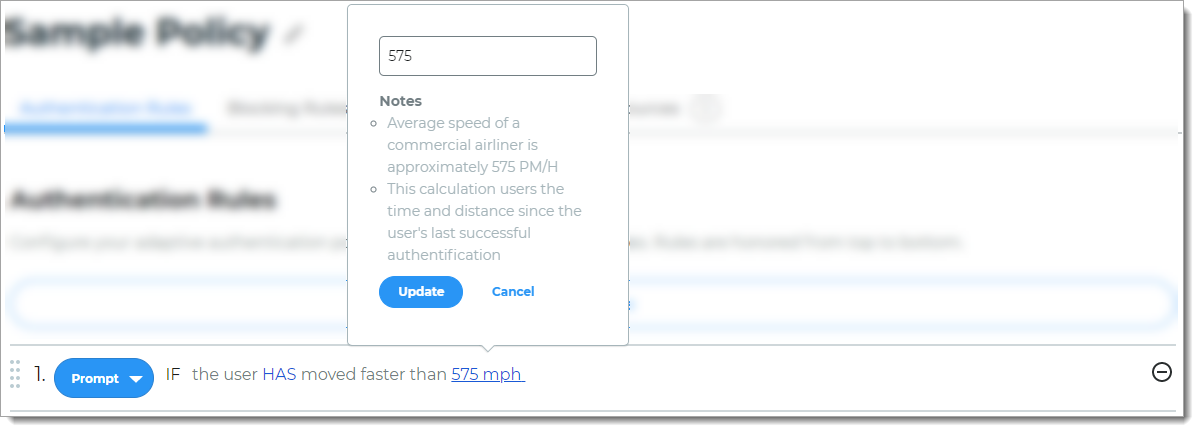
Rule to determine access based on the speed of travel between the previous login and current login attempt.
For example, if the user logged in from Los Angeles, California (point A) at 11:15 a.m. and then from New York, New York (point B) at 11:45 a.m. on the same day, then the user is prompted for another form of authentication.
Group
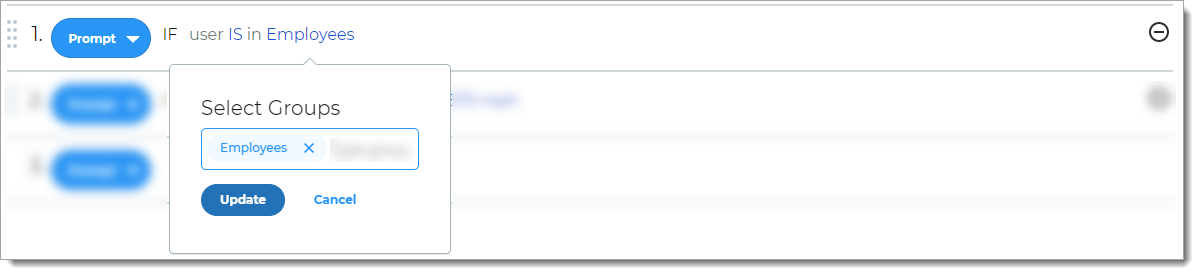
Rule to determine access based on group membership.
For example, if the user is a member of a specified group, then the user is allowed access.
Note
Before you can use this rule, groups must be defined in the data store for your organization.
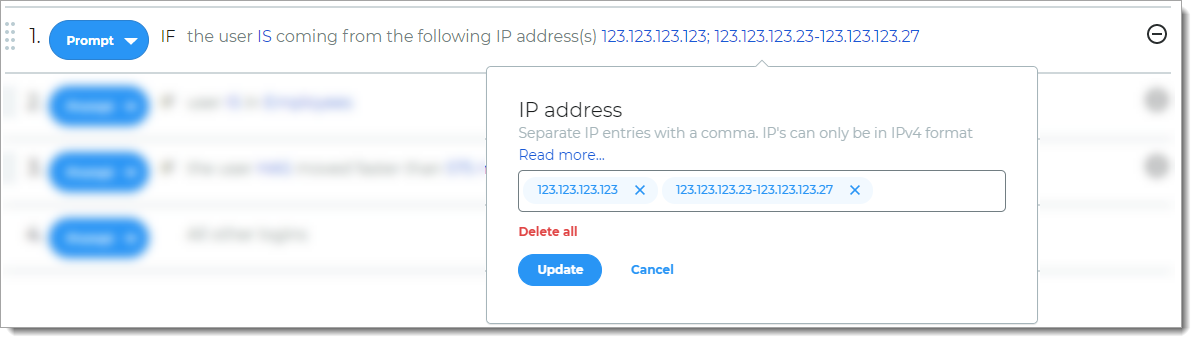
IP Range
Rule to determine access based on IP ranges. You can enter IPv4 addresses as individual values, a range of values, or use CIDR Notation.
For example, if the user login comes from any of the specified IP addresses, you can set it to prompt the user for a form of authentication or allow the user to skip MFA.
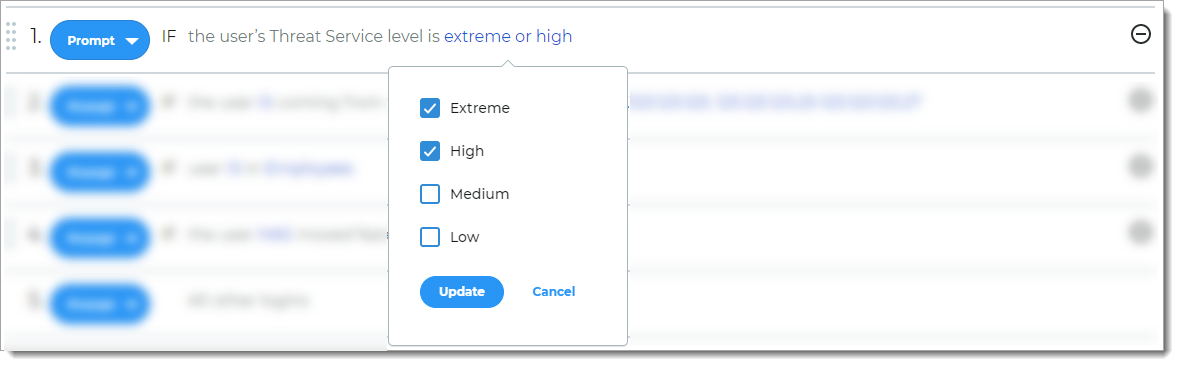
Threat Service
Rule to determine access based on known risks associated with the login attempt as determined by the SecureAuth Threat Service.
For example, if the user login is associated with a known threat, then the user is prompted for another form of authentication.
Note
You must have a license to use this feature. To learn more about the Threat Service rule, contact your SecureAuth Account Manager.
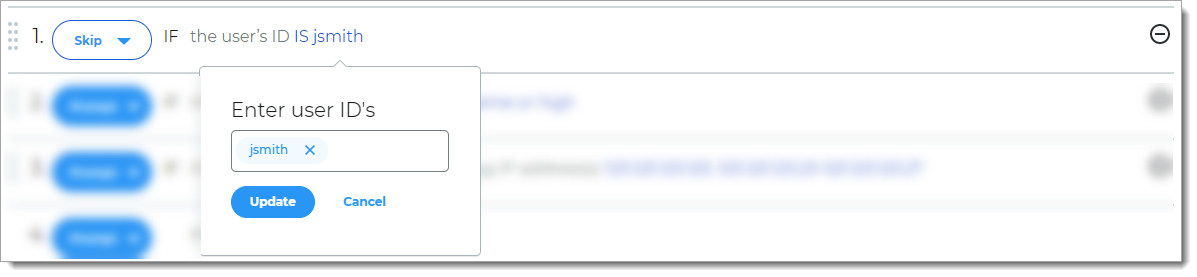
User
Rule to determine access based on whether the user login is the same as the specified user ID.
For example, if the user login matches the user ID, then the user is allowed access.
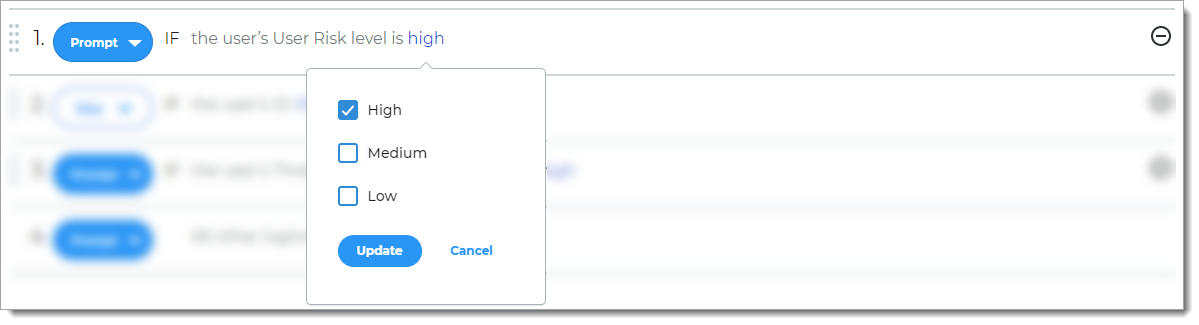
User Risk
Rule to determine access based on user reputation and behavior factors associated with the login attempt.
For example, if the login reputation and behavior of the user falls into the specified risk level, then the user is prompted for another form of authentication.
Note
You must have a license to use this feature. To learn more about the Threat Service rule, contact your SecureAuth Account Manager.
All other logins
This rule will always be evaluated last and is a catch-all rule to determine access if none of the other rules are triggered. This rule cannot be deleted or reordered in the list.
As an addition to the Skip and Prompt rule options, Run DR (Run Device/Browser Recognition) is another rule option. This runs device/browser recognition under the following conditions:
Skip MFA when the device or browser profile matches the user profile
Prompt for MFA when the device or browser profile do not match
Prompt for MFA when device recognition is not enabled
Prompt for MFA when the Login workflow includes "Valid Persistent Token"
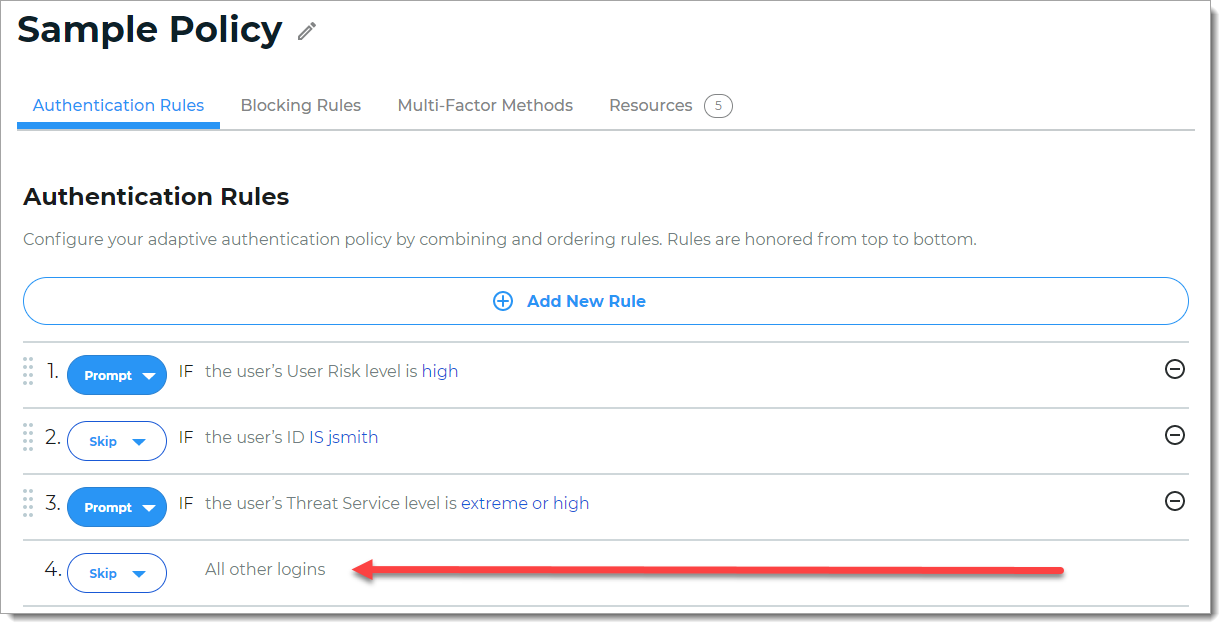
After you add and reorganize the authentication rules, click Save.