Define login workflow and multi-factor methods settings in a policy
The default and custom policies contain all the globally enabled multi-factor (MFA) methods. For each policy, define the user login workflow experience. This includes selecting the MFA method options for your users.
With a policy open in edit mode, select the Multi-Factor Methods tab.
Select the Login Workflow experience for users to access a resource attached to this policy.
Passwordless
(formerly named Username | MFA Method in version 19.07)
For the end user, this a passwordless workflow login process:
Step 1: User provides username on a page.
Step 2: User is prompted for multi-factor authentication on a subsequent page.
The recommended authenticators for Passwordless login methods are:
FIDO2-enabled devices (Available in the Identity Platform version 20.06 or later. Requires the Prevent licensing package.)
Phone-as-a-Token (timed passcode, one-time passcode, login notification to accept, deny or matching displayed character)
Biometric (using SecureAuth Authenticate app)
Username & Password | MFA Method
When you add a new policy, this is the default workflow selection. For the end user, this is the workflow login process:
Step 1: User provides username and password on a page.
Step 2: User is prompted for multi-factor authentication on a subsequent page.
Username | MFA Method | Password
For the end user, this is the workflow login process:
Step 1: User provides username on a page.
Step 2: User is prompted for multi-factor authentication on the next page.
Step 3: User provides password on a subsequent page.
(Valid Persistent Token) | MFA Method
For the end user, this is the workflow login process:
Step 1: User provides valid persistent token (in lieu of a username) on a page.
Step 2: User is prompted for multi-factor authentication on a subsequent page.
(Valid Persistent Token) | MFA Method | Password
For the end user, this is the workflow login process:
Step 1: User provides valid persistent token (in lieu of a username) on a page.
Step 2: User is prompted for multi-factor authentication on the next page.
Step 3: User provides password on a subsequent page.
Next, define the multi-factor method option users can choose to authenticate into a resource.
If you do not see a certain multi-factor method, it is not globally turned on. On the left pane in the Identity Platform, go to Multi-Factor Method settings and turn it on. For more information, see Global multi-factor authentication (MFA) methods overview.
For documentation purposes, all multi-factor methods for a policy are described next.
FIDO2 (WebAuthn)
(Available in version 20.06)
Select to allow a user to register and use a FIDO2 authenticator to authenticate access:
FIDO2 Devices – user receives notification prompt from their registered FIDO2 authenticator (for example, security key or built-in authenticator in their mobile phone)
YubiKey
Select to allow a user with a YubiKey to authenticate access:
Yubico OTP – use YubiKey to generate an encrypted one-time passcode (OTP)
OATH HOTP – use YubiKey to generate an encrypted six- eight-, or nine-character one-time (OTP) event-based passcode using OATH-HOTP. This means a new one-time passcode is generated for each event.
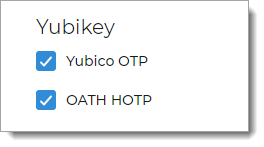
Authentication Apps
Select to allow a user with an authentication app such as SecureAuth Authenticate to authenticate access:
Timed passcode from app – user receives soft token generated by SecureAuth Authenticate app
One-time passcode – user receives push notification from SecureAuth Authenticate app with one-time passcode
Login notification – user receives push notification from SecureAuth Authenticate app
Accept Method – choose one of the following:
User selects accept or deny
User selects matching character displayed on device
Biometric identification – user can use biometric identification like facial recognition and fingerprint by means of the Authenticate app
Text Message
Select to allow a user to receive SMS / text message to a mobile number associated with their profile, to authenticate access:
User receives a Login confirmation link
User receives a One-time passcode
Email
Select to allow a user to receive an authentication email to an email address associated with their profile, to authenticate access:
User receives a Login confirmation link
User receives a One-time passcode
Voice Phone Call
Select to allow a user to receive a voice phone call to a phone number associated with their profile, to authenticate access:
User receives a One-time passcode
Security Questions
Select to send security questions to a user to verify who they are, to authenticate access:
User receives Security questions to which they must answer correctly
PIN
Select to allow a user to receive a PIN (personal identification number) associated with their profile, to authenticate access:
User receives a request to enter a PIN
Symantec VIP
Select to allow a user with a Symantec Validation and ID (VIP) token to authenticate access:
Click Save.