FIDO2 WebAuthn global MFA settings
You can allow users to register their FIDO2-enabled devices as a login multi-factor authentication (MFA) option. When you configure and save the global settings for FIDO2, it automatically generates a FIDO2 registration and management page.
Note
The FIDO2 registration and authentication web page for your end users requires HTTPS in the URL.
The FIDO2 registration and management page is localized and translated based on the user's browser language settings.
To guide end users to register their devices as FIDO authenticators, share the FIDO2 registration page URL. Once end users register their device on that page, it becomes available as a FIDO2 login option to authenticate their access to resources.
On the left side of the Identity Platform page, click Multi-Factor Methods.
Click the pencil icon for FIDO2 (WebAuthn).
The configuration page for FIDO2 (WebAuthn) appears.
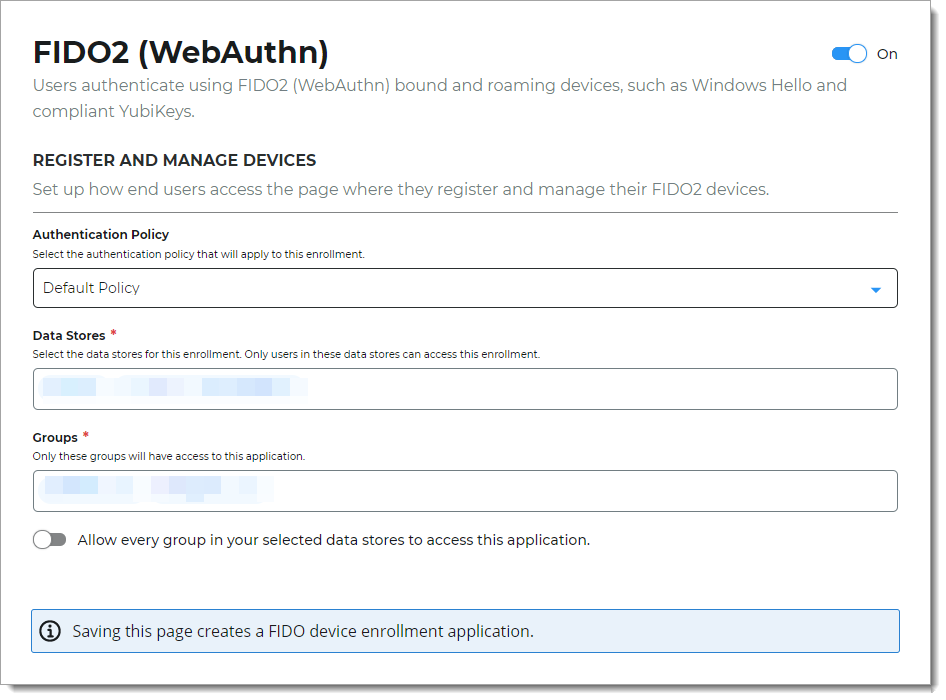
Set the following configurations.
Authentication Policy
Select the login authentication policy for the FIDO2 registration page.
The authentication policy includes the login workflow to register the FIDO2 device.
Data Stores
Enter the data stores to to authenticate and allow user access to register their FIDO2 device. Start typing to bring up a list of data store names. You can enter more than one data store.
Groups
Use one of the following options:
Slider in the On position (enabled): Allow users from every group in your selected data stores access to this FIDO2 registration page.
Slider in the Off position (disabled): Enter the specific groups who are allowed access to this FIDO2 registration page.
Click Save.
This creates the FIDO2 registration page and provides the registration URL. Share this URL with your end users to register and manage their FIDO2 devices.
Note
If you turn off FIDO2 as a login method, it prevents end users from seeing it as an MFA choice during login. The FIDO Enrollment URL page stays active for end users to manage their FIDO2 devices.
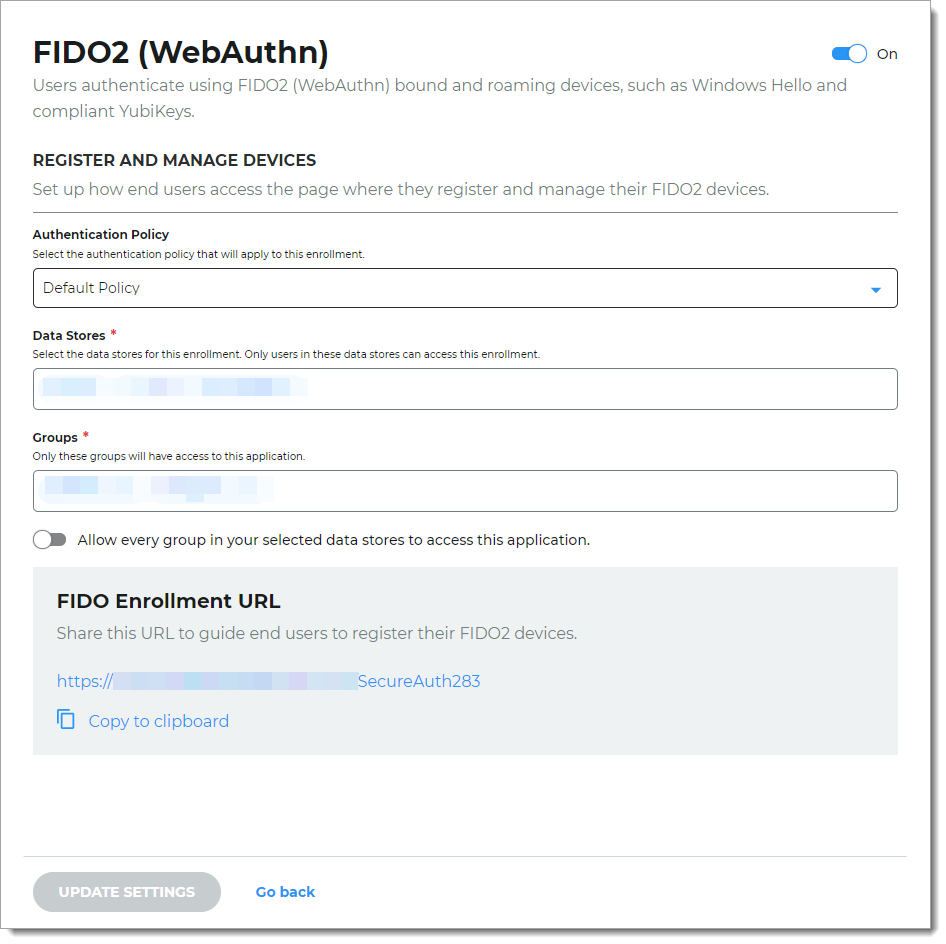
Next steps
Configure a policy on the Multi-Factor Methods tab to use FIDO2 as an authenticator in the login workflow.
Copy and share the FIDO Enrollment URL with your end users. For example, to encourage end users to register their FIDO2 devices, customize the "Passwordless with FIDO2" setup instructions available in the SecureAuth Onboarding Toolkit.
Note
The FIDO2 registration and authentication web page for your end users requires HTTPS in the URL.