How to establish trust for ACS redirects in SP-initiated SAML requests
For more security, we've added logic to restrict the incoming Assertion Consumer Service (ACS) URL in the SP-initiated SAML request by validating them against an allow list (whitelist).
Applies to
The following SecureAuth® Identity Platform product releases:
Identity Platform release 24.04 or later
Identity Platform release 23.07 with hotfix 23.07-1 or later
Identity Platform release 22.12 with hotfix 22.12-6 or later
Identity Platform release 22.02 with hotfix 22.02-11 or later
Identity Platform release 21.04 with hotfix 21.04-15 or later
Identity Platform release 20.06 with hotfix 20.06-18 or later
SP-initiated SAML integrations
Solution
For the ACS URL restriction to work correctly in the SP-initiated SAML integration, you must have have a SAML Target URL or SAML Consumer URL configured in the application realm. These two URL settings are parsed for their domain name which are the default entries of the full whitelist; you do not need to duplicate these domains in the SAML Whitelist setting.
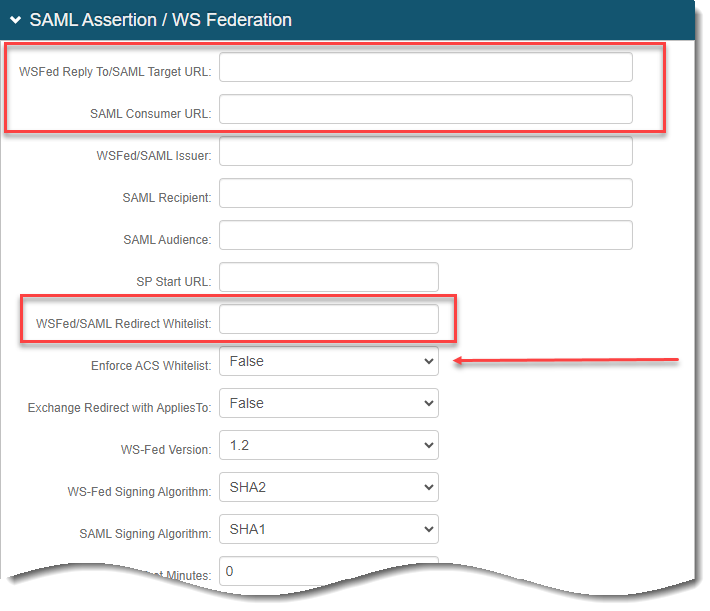 |
SAML integration in Advanced Settings > Post Authentication tab
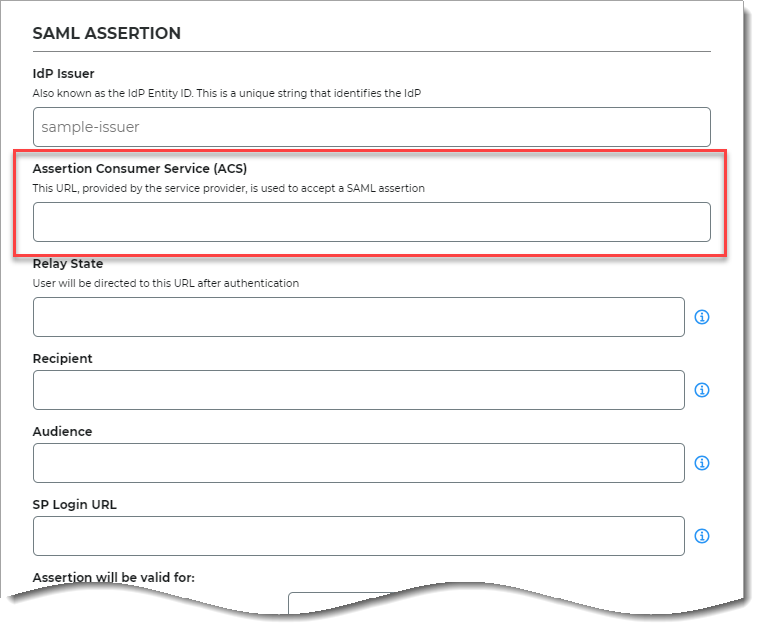 |
SAML integration in New Experience > Application settings
After you install the hotfix, the Enforce ACS Whitelist setting is set to False (OFF) by default.
Note
When you turn ON the Enforce ACS Whitelist setting, you must define the domains in at least one of the three fields, otherwise this feature will not work by turning it ON and then leaving the fields empty.
To turn this on for the integrated SP-initiated SAML application, go to Advanced Settings > Post Authentication tab.
In the SAML Assertion / WS Federation section, set the Enforce ACS Whitelist field to
True(ON)You must configure at least one of the following URLs in the SAML application.
SAML Target URL
The absolute URL of the target resource (the "relay state" in the Identity Platform). The user is redirected to this URL after authentication.
SAML Consumer URL
The URL provided by the SP to used to accept a SAML assertion.
NOTE: In the New Experience, this is the Assertion Consumer Service (ACS) field.
Next, if you expect to have multiple ACS targets in the SAML requests, then you must add each domain name to the WSFed/SAML Redirect Whitelist.
Each SAML request has one ACS URL, but it is possible to have more than one ACS URL using same realm.
WSFed/SAML Redirect Whitelist
Add every domain in a comma-delimited list.
For example,
secureauth.com,test.org,jira.netSee the following section for Whitelist examples.
Whitelist examples
If any part of the incoming domain (including subdomain) matches with any value in the whitelist, it is allowed.
Whitelist:
example.com,test.orgIncoming domain:
subdomain.example.comAllowed match: The incoming domain matches the value
example.comfrom the whitelist.Whitelist:
example.com,test.orgIncoming domain:
subdomain.test.orgAllowed match: The incoming domain matches the value
test.orgfrom the whitelist.Whitelist:
subdomain.example.comIncoming domain:
example.com,test.orgAllowed match: None. The incoming domain does not match any value in the whitelist.
Whitelist:
subdomain.example.comIncoming domain:
subdomain.example.com,example.comAllowed match: The incoming domain matches only
subdomain.example.comfrom the whitelist.