SecureAuth security advisory – RADIUS vulnerability CVE-2024-3596
Update: July 26, 2024
A vulnerability has been found in the RADIUS server, the criticality of which is currently being evaluated as part of the government NIST vulnerability website at https://www.cve.org/CVERecord?id=CVE-2024-3596. Industry details can be found at https://www.blastradius.fail/.
The vulnerability is in the underlying RADIUS protocol, it is not a vulnerability in the implementation. The recommended documented mitigation is to configure TLS-based authentication on client end and server, for example, PAP/CHAP with EAP-TLS or PEAP.
If you use any of the following authentication protocols, review the impacts described next.
- PAP, CHAP, MSCHAPv2 (without TLS)
These authentication flows are vulnerable.
Remediation is upgrade SecureAuth RADIUS Server and vendor VPN products; and enable the short-term solution configurations.
Long-term solution is to migrate to TLS based authentication flows as described below.
For MSCHAPv2 in particular, Microsoft recommends not using MSCHAPv2 and moving to PEAP or EAP-TLS methods. See https://learn.microsoft.com/en-us/windows/security/identity-protection/credential-guard/considerations-known-issues#wi-fi-and-vpn-considerations.
- PAP, CHAP, PEAP, EAP with TLS (PEAP, EAP-TLS, PAP/CHAP with EAP-TLS)
Not vulnerable. No changes needed.
Short-term solution
This applies to you if you are not using EAP-TLS or PEAP.
SecureAuth has a fix to the SecureAuth RADIUS server provided to its customers.
A short-term solution is to require the Message-Authenticator attribute in all access requests. When this configuration is set up in the RADIUS client, it will discard any requests not containing the new attribute.
VPN vendors need to update their products to add this attribute in requests.
As a SecureAuth customer, you will need to upgrade to SecureAuth RADIUS 24.07.02. And you will also need to upgrade your VPN product (contact your VPN vendor about this).
After you upgrade SecureAuth RADIUS and your VPN, you will need to turn on the setting for the Message-Authenticator attribute in both products. The attribute setting is off by default.
Select the Limit Proxy-State Attribute check box. It secures all authentications in the SecureAuth RADIUS server until all VPN products are updated.
To learn more, see InkBridge Networks Blast RADIUS white paper.
What to do
Go to the Product Downloads page, download and install the latest update for SecureAuth RADIUS Server 24.07.02.
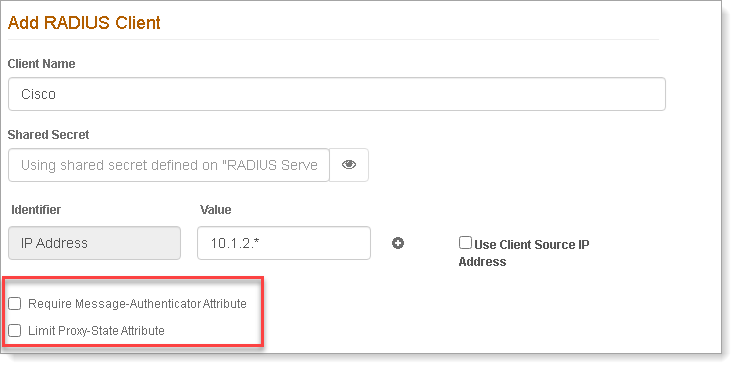
In the SecureAuth RADIUS admin console, for each VPN client, select one of the following check boxes:
Require Message-Authenticator Attribute
Select this check box to require all PAP/CHAP access requests for this client to contain the Message-Authenticator attribute.
Legacy RADIUS clients that don't include this attribute will be silently discarded.
Limit Proxy-State Attribute
Select this check box to require all PAP/CHAP access requests containing the Proxy-State to include the Message-Authenticator attribute. If the request contains the Proxy-State attribute and not the Message-Attribute, it will be silently discarded.
If the request contains both the Proxy-State and Message-Authenticator, it will not be discarded.
Save your changes.
Long-term solution
Use PEAP/EAP-TLS. No changes required from our side, SecureAuth already supports this.
To configure the PEAP settings in SecureAuth RADIUS, refer the PEAP Settings section in the Configure SecureAuth RADIUS settings document.
To configure PEAP in VPN products, see the NetMotion Mobility RADIUS configuration guide; this should work as a reference for other VPN vendors.
Questions?
If you have questions or require assistance upgrading your RADIUS server, please contact SecureAuth Support:
Support Portal: support.secureauth.com
Email: support@secureauth.com
Phone: (866) 859-1526