Add Oracle DB data store
In the SecureAuth® Identity Platform, you can add an Oracle Database (DB) data store to assert or manage user identity information.
Prerequisites
Identity Platform release 22.02 or later, cloud or hybrid deployment
SecureAuth Connector installed and connected for Identity Platform cloud deployment
Oracle database
Process
There are two parts to adding a data store in the Identity Platform — (1) adding the data store and (2) mapping the data store properties.
Step 1 of 2: Add a Oracle DB data store
The first part of adding an Oracle DB data store is configuring the data store name, connections, credentials, and search attributes.
On the left side of the Identity Platform page, click Data Stores.
Select the Data Stores tab.
Click Add a Data Store.
Set the Data Store Name and select the Connection Type as Oracle DB.
In the Connection Settings section, set the Connection String to Oracle DB.
The connection string format is:
Data Source=(DESCRIPTION=(ADDRESS_LIST=(ADDRESS=(PROTOCOL=TCP)(HOST=localhost)(PORT=1522)))(CONNECT_DATA=(SERVER=DEDICATED)(SERVICE_NAME=[DBNANAME])))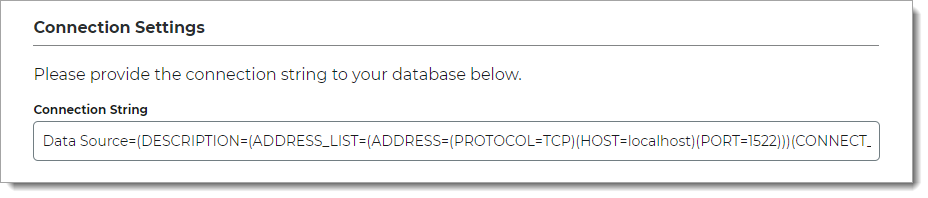
In the Credentials section, test your credentials or provide CyberArk Vault credentials to access the Oracle DB data store.
Test Credentials
Test the data store connection by clicking Test Credentials. (This button is available only in hybrid deployments of Identity Platform 22.02 and 22.12.)
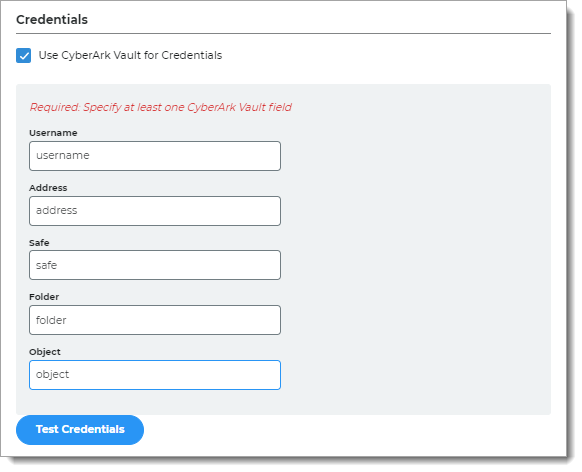
Use CyberArk Vault for Credentials
With this option, enter at least one field for the service account login:
Username – User name of machine to be scanned by CyberArk Application Identity Manger (AIM). This information appears on the Account Details page of the CyberArk Password Vault Web Access (PVWA) Admin Console
Address – Address of machine to be scanned by AIM
Safe – Name of Access Control Safe where credentials are stored
Folder – Name of folder where account resides (by default, it its the root folder)
Object – Unique identifier Object name for the account
Test the data store connection by clicking Test Credentials. (This button is available only in hybrid deployments of Identity Platform 22.02 and 22.12.)
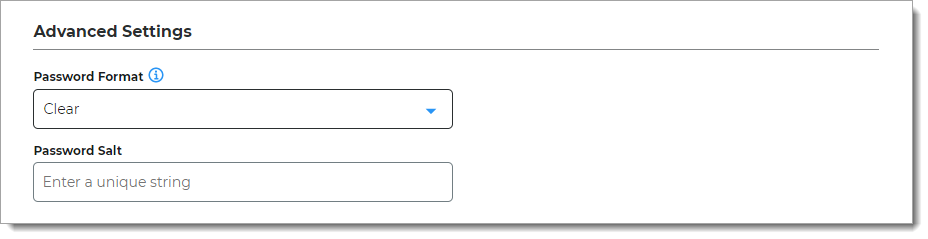
In the Advanced Settings section, define how the service account password is to be stored in the directory.
Password Format
Choose one of the following formats:
Clear – Password is stored as plain text. This improves performance of storage and retrieval but is less secure.
Encrypted – Password is stored as encrypted and can be decrypted for password comparison or retrieval. This is more secure, but requires additional processing or storage.
Hashed – Password is hashed using a one-way hash algorithm and random salt-value. When password is validated, it is hashed with the salt value of the dates for verification. Hashed passwords cannot be retrieved.
Password Salt
Enter a unique string for the Oracle service account password salt value.
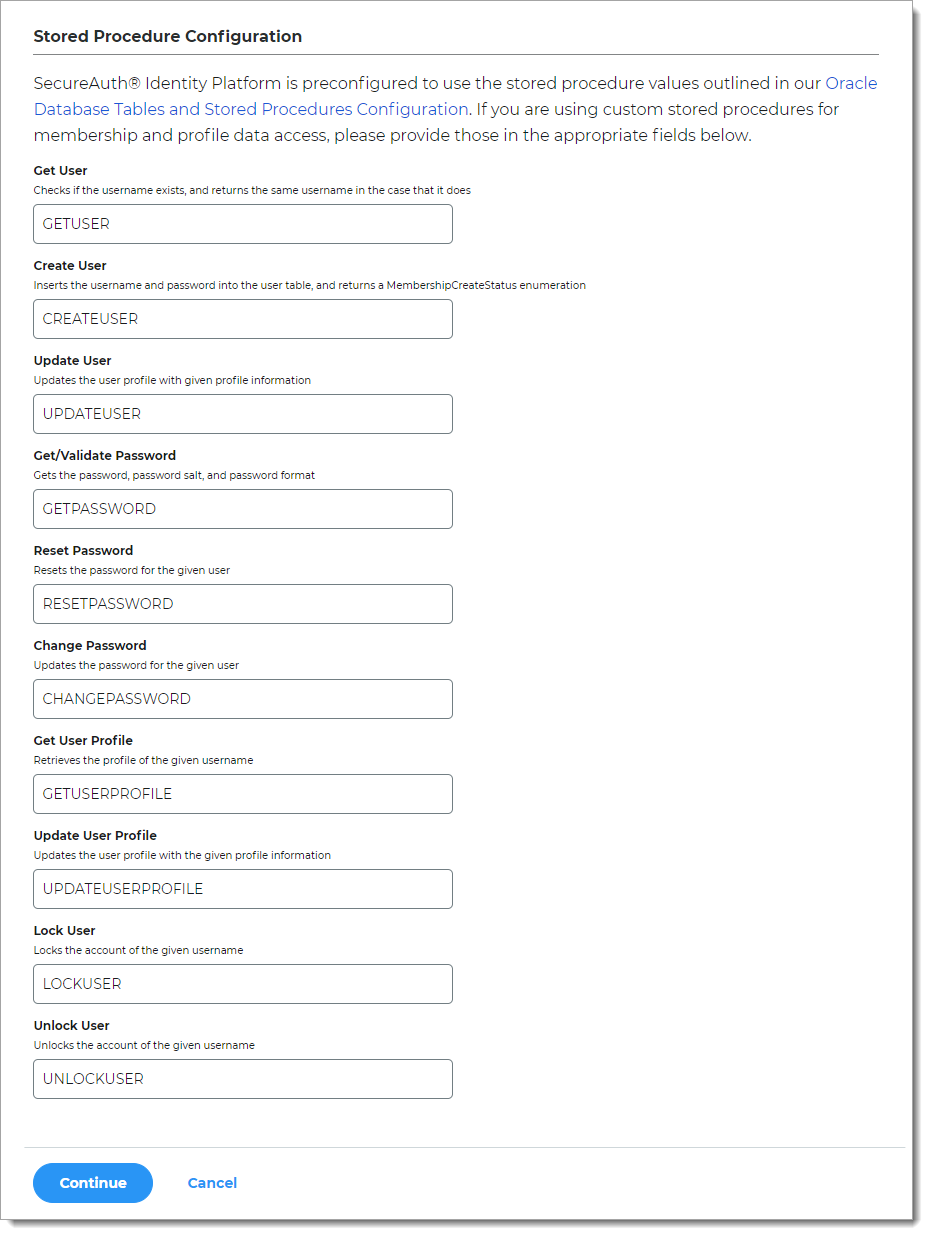
In the Stored Procedure Configuration section, use the default values unless custom stored procedures are used for membership and profile data access.
The Identity Platform is preconfigured to use the stored procedure values outlined in Oracle database tables and stored procedures configuration.
Get User
Checks if a username exists, and returns the same username in the case that it does.
Create User
Inserts the username and password into the user table, and returns a MembershipCreateStatus enumeration.
Update User
Updates the user profile with given profile information.
Get/Validate Password
Gets the password, password salt, and password format.
Reset Password
Resets the password for the given user.
Change Password
Updates the password for the given user.
Get User Profile
Retrieves the profile of the given username.
Update User Profile
Updates user profile with the given profile information.
Lock User
Locks the account of the given username.
Unlock User
Unlocks the account of the given username.
Click Continue.
The Map Data Store Properties page opens.
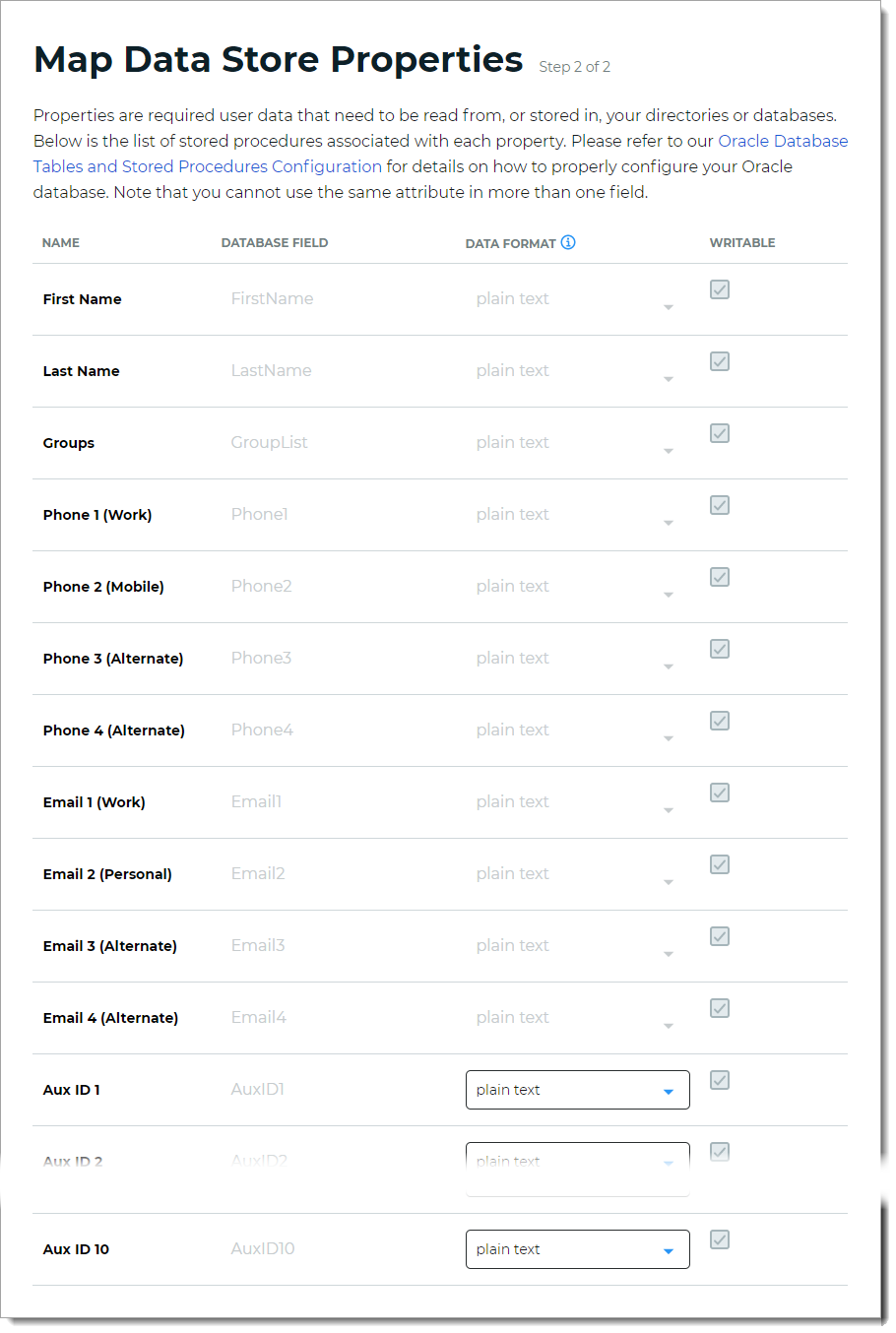
Step 2 of 2: Map the Oracle DB data store properties
The second part of adding an Oracle DB data store is mapping the data store properties.
Each user is uniquely identified by profile data that is read from or stored in your directories and databases.
The Identity Platform does not store user profiles, so your Oracle DB attributes must be mapped to the Identity Platform profile properties to be read and updated in the directory by the Identity Platform. The Oracle DB attribute mapped to the property is retrieved only when required for authentication or assertion purposes.
You cannot modify the Writable properties for the SQL Server data store from the Identity Platform UI. Refer to your database provider for this configuration.
For more information about how data store profile properties are stored for on-premises, hybrid, or cloud Identity Platform deployments, see List of stored profile field properties.
For the mapped profile properties like Aux ID 1 through Aux ID 10, specify the Data Format to define how data is encrypted and stored in the directory.
For cloud deployments, any profile properties mapped to Aux ID 1 through Aux ID 10 are stored in the cloud. These properties are generated and used by SecureAuth, such as device recognition profiles, push tokens, PIN, and access histories.
The selection options are:
plain text – store data as regular, readable text (default)
standard encryption – store and encrypt data using RSA encryption
Note
Standard encryption format is not supported for the Oracle DB in cloud deployments.
advanced encryption – store and encrypt data using AES encryption
standard hash – store and encrypt data using SHA-256 hash
Click Save Data Store.
The Oracle DB data store you just added appears in the User Data Stores list.