SecureAuth Level of Assurance (LOA) Provider settings
SecureAuth® Identity Platform uses machine learning to consume end user information during authentication. It generates a level of assurance (LOA) confidence score. The score helps decide whether to increase or decrease user friction for the user login. Over time, it learns the patterns of user behavior and their devices, and if they are consistent, it increases their LOA score.
The LOA score quantifies how confident the user is the identity they claim to be.
The LOA confidence score falls within a range of 0 to 4, with 4 indicating a high degree of confidence, which is opposite of the user risk score. A high LOA score implies a low risk because there is high confidence in the user's identity. There are three confidence score levels: low, medium, and high.
In the authentication policy, you can use the LOA confidence score level (low, medium, and high) to determine access to applications in your organization.
What to expect from the AI/ML data models
This section explains how our AI/ML models learn User Behavior. They use unsupervised machine learning to improve authentication security. Learn about their initial learning phase and how it affects generating LOA scores in the Risk Engine.
AI/ML model learning
The Risk Engine models are User Behavior Models that use unsupervised machine learning. They need time to learn about each user before they can generate risk engine LOA scores for their authentication events. The default minimum number of data points for each model is 50, but this number can be adjusted based on a customer's environment.
AI/ML model cold start and training period
As mentioned earlier, unsupervised User Behavior Models need at least 50 data points for training. If this number is lowered, training may take several weeks for most users. When planning to go live, consider this training period to ensure models are trained before the Risk scores (for those data models) are available for most users.
Note
At this time, the Location Trust risk analyzer is not yet available in the Identity Platform.
Prerequisites
Identity Platform 23.07 with hotfix 5 or later
Identity Platform 22.12 with hotfix 10 or later
Prevent package license – contact SecureAuth Support
Set Level of Assurance (LOA) Provider score
On the left side of the Identity Platform page, click Risk and Assurance Providers.
Select the Assurance Provider tab.
Contact SecureAuth Support to set up your IdP access credentials; if already done, click the Activate LOA configuration link to proceed.
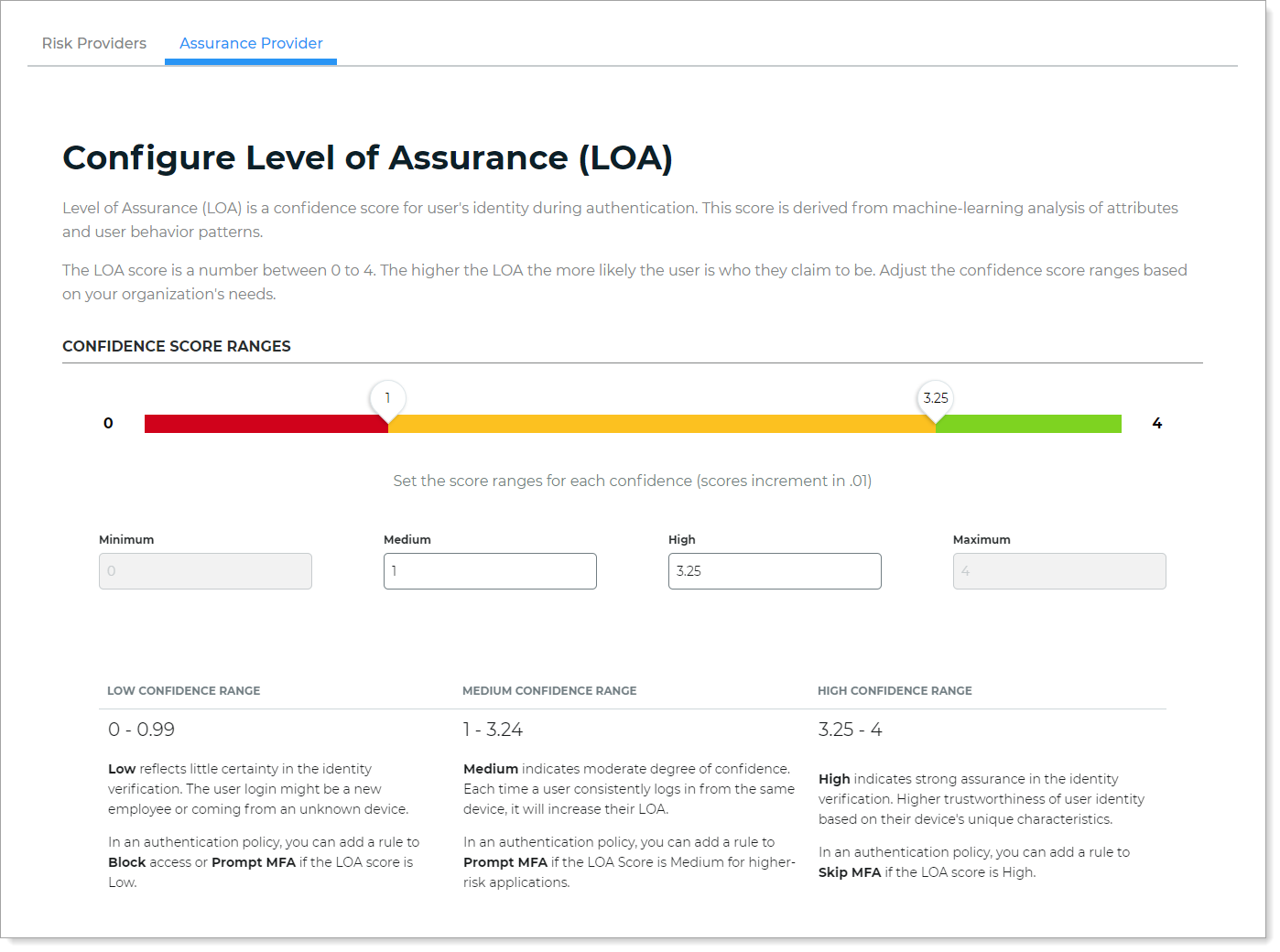
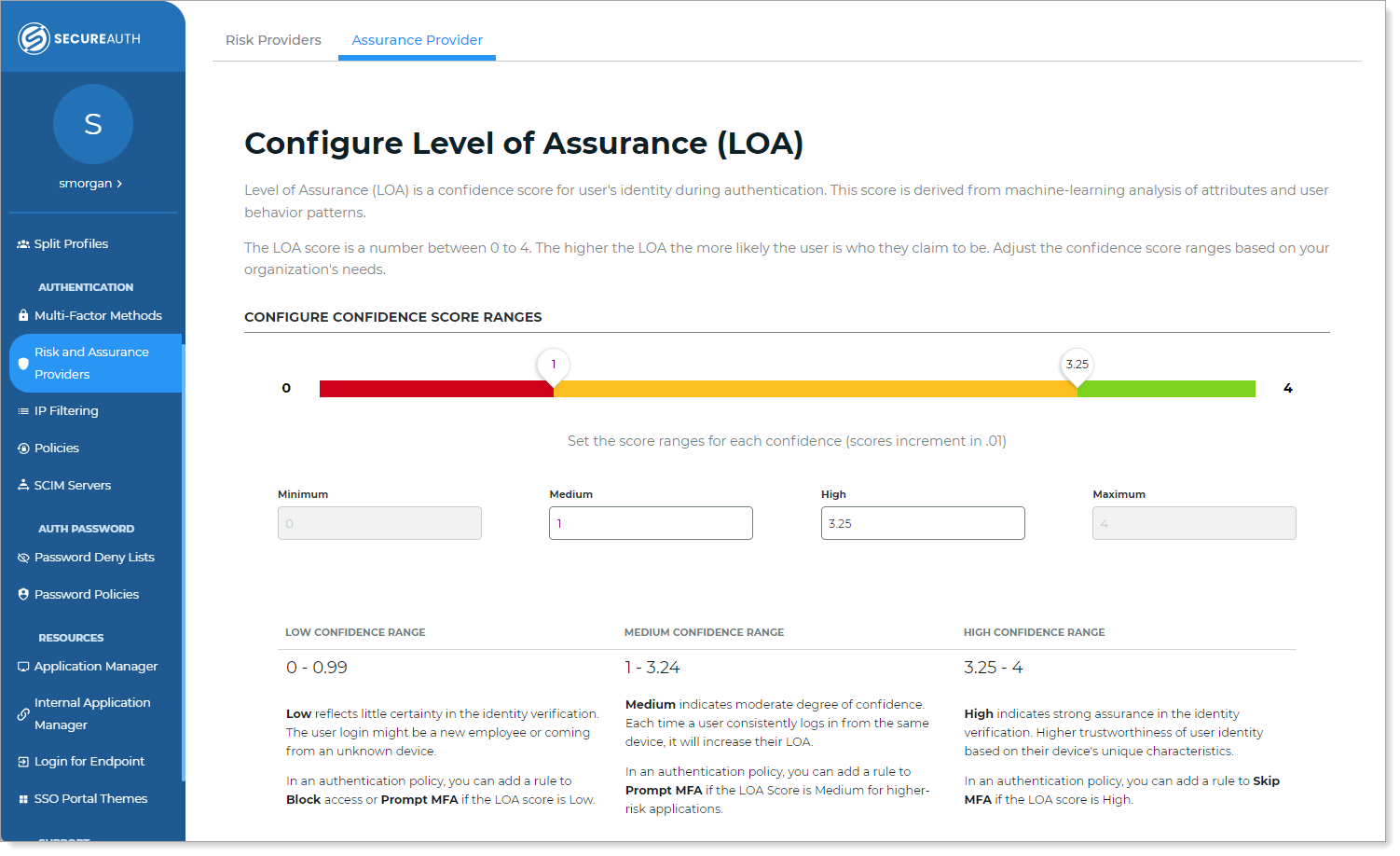
On the Configure Level of Assurance (LOA) page, adjust the confidence score ranges.
You can adjust the LOA score in .01 increments.
Low confidence – Indicates little certainty in the identity verification. the user login might be a new employee or coming from an unknown device. For example a low confidence score range could be 0 to 0.99.
Medium confidence – Indicates a moderate degree of confidence. Each time a user consistently logs in from the same device, it will increase their LOA. For example, a medium confidence score range could be 1 to 3.24
High confidence – Indicates strong assurance in the identity verification. This implies higher trustworthiness of user identity based on their device's unique characteristics. For example, a high confidence score range could be 3.25 to 4.
In the User Attribute section, set the mapped email attribute to link that user to their LOA score.
The attribute must be in email format. This is usually the
mailattribute in the data store properties. Once you set it, do not change it. If you need to change it, contact Support.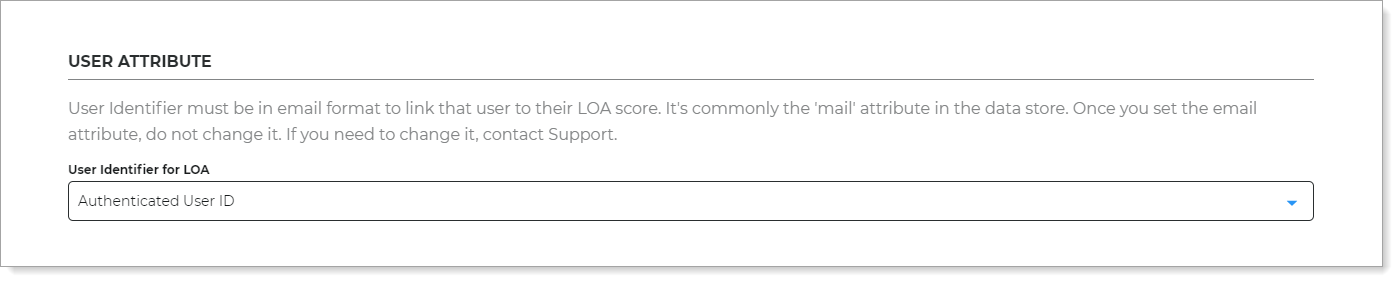
Save your changes.
Next, add LOA as an authentication rule in a policy to increase or decrease user friction.
Add LOA rule in authentication policy
After you define the LOA score ranges, you can add them in the authentication policy.
In the authentication policy, on the Authentication Rules tab, click Add New Rule. Select Level of Assurance (LOA).
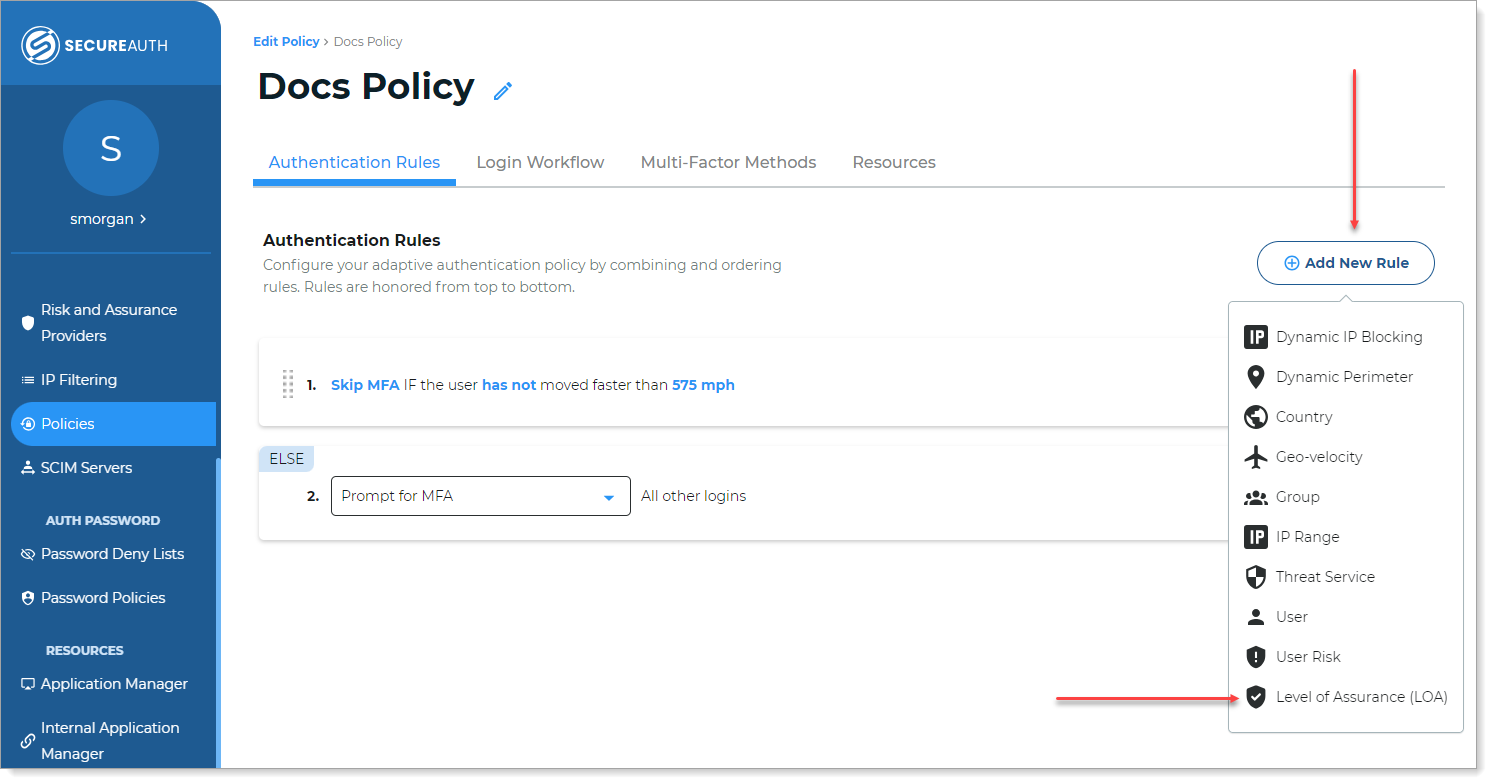
From the list, select Level of Assurance (LOA).
For the LOA rule, select what action to take when the LOA score meets a certain confidence level.
Condition Rule – Select the action to take such as Prompt for MFA, Skip MFA, Block MFA, or Redirect To
Confidence level – If the LOA score meets either Low, Medium, or High, it will enforce the selected action on the user.
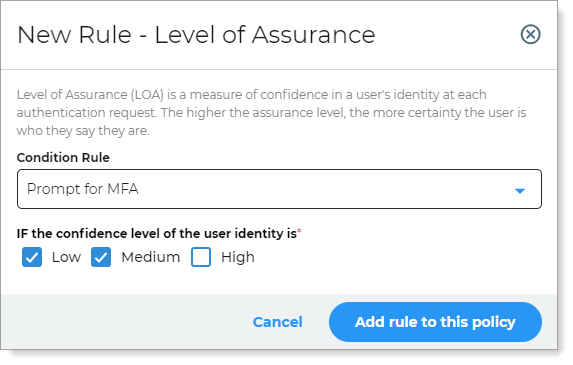
Save your changes.
Use case
In this use case, you have a new employee login in your organization. Because this is their first login, the LOA will be low. They will be asked to provide a form of MFA.
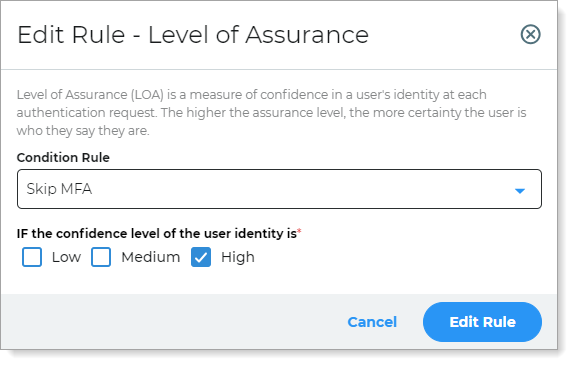
Over time, it learns the patterns of user behavior and their devices. If they are consistent, it increases their LOA score. When the user LOA confidence is high, you can allow the user to skip MFA.
The following is an outline about how to set this up.
In Risk and Assurance Providers > Assurance Provider, configure the LOA confidence score ranges.
In the authentication policy on the Authentication Rules tab, add an LOA rule to Skip MFA when LOA is high.
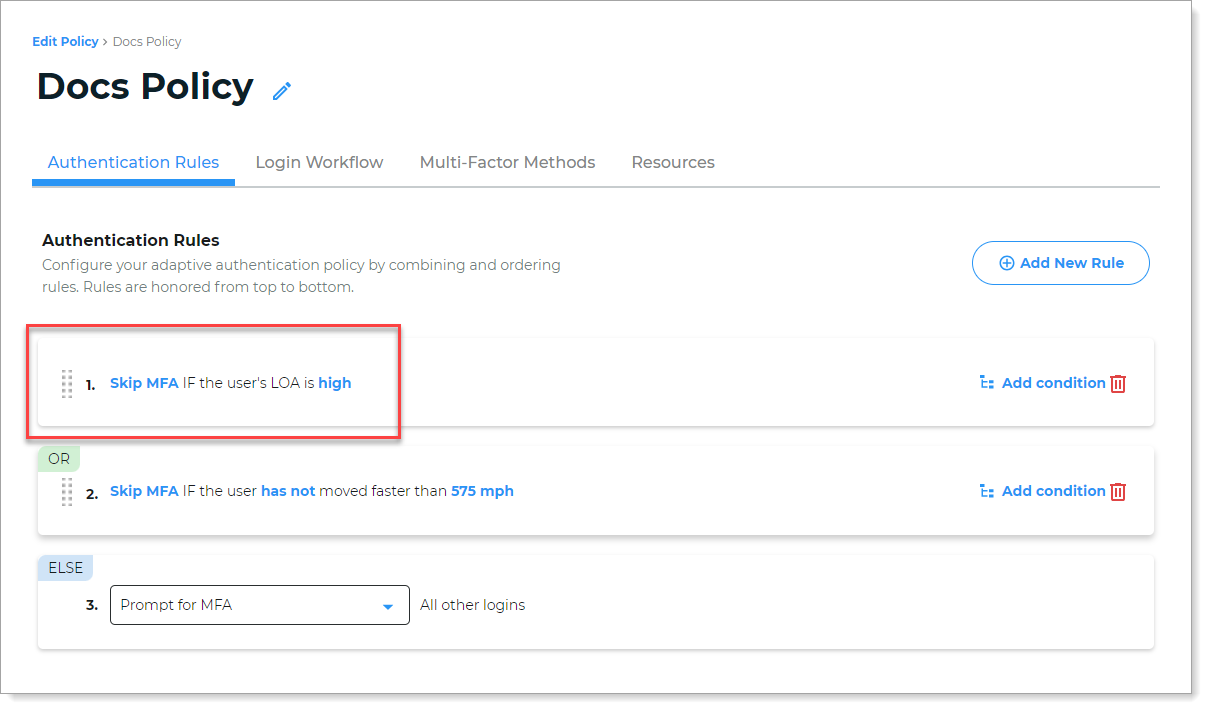
Save your changes.
Configure other policy settings as needed; make sure you have applications attached on the Resources tab.