Configure role-based access control
Role-based access control (RBAC) can be enabled and managed in either the New Experience or in Advanced Settings (formerly the Classic Experience).
To learn more about the types of roles and their permissions, see Role-based access control overview.
Enable and manage RBAC in the New Experience
Note
If an administrator attempts to enable RBAC in the New Experience when it has already been enabled in Advanced Settings, the following warning message appears:
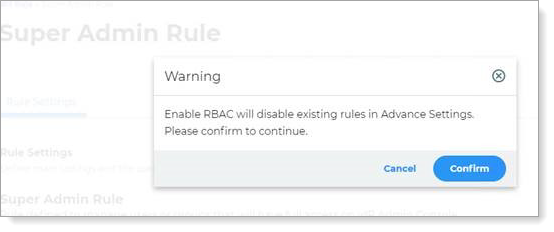 |
Prerequisites
Administrative access to hybrid or cloud deployment of SecureAuth® Identity Platform release 22.12 or later
Data store directory integrated with the Identity Platform Admin Realm (SecureAuth0) on the Data tab. RBAC in the New Experience supports the following data stores:
Active Directory
Microsoft Entra ID (formerly Azure AD)
Edirectory
Oracle
SQL
Generic LDAP
Groups established in the data store directory to which the role-based rules apply
Create Super Admins
In this section, you will create a Super Admin Rule which assigns the Super Admin role to selected users, groups, or both. Only Super Admins have full access to the Identity Platform console.
Log in to the Identity Platform as an Administrator.
Note
When RBAC is enabled, Administrators will have their roles changed to either the Super Admin or Application Owner role.
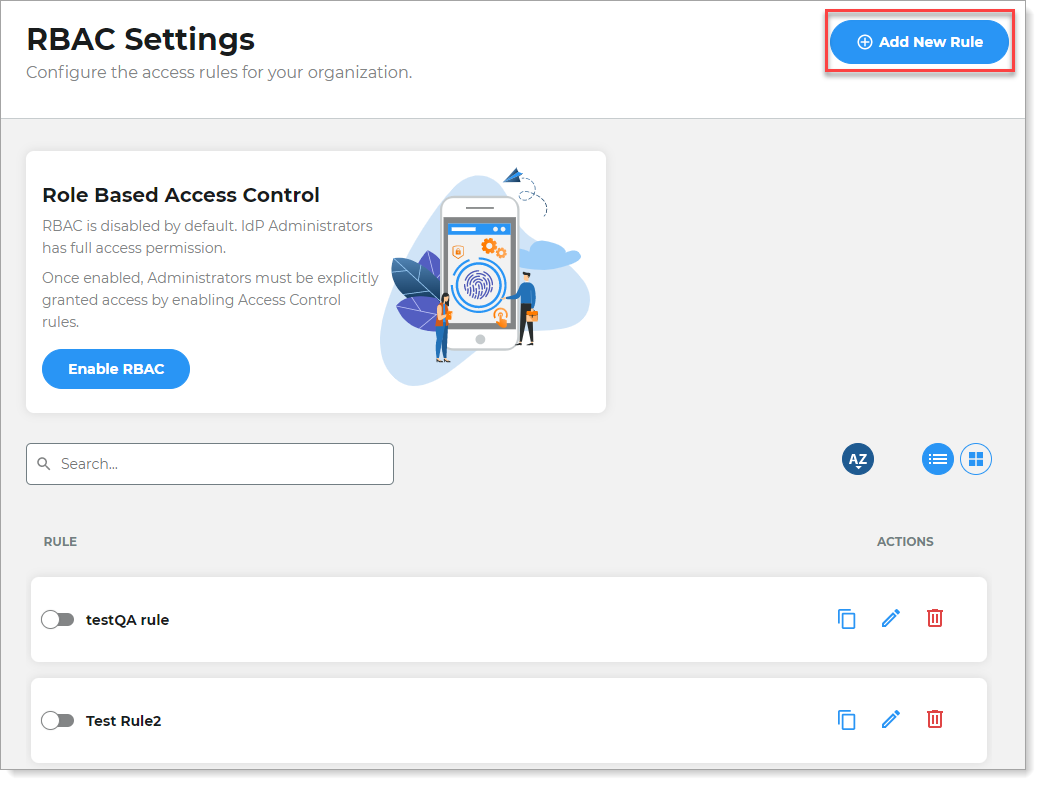
On the left side of the Identity Platform, click RBAC Settings.
Click Enable RBAC.
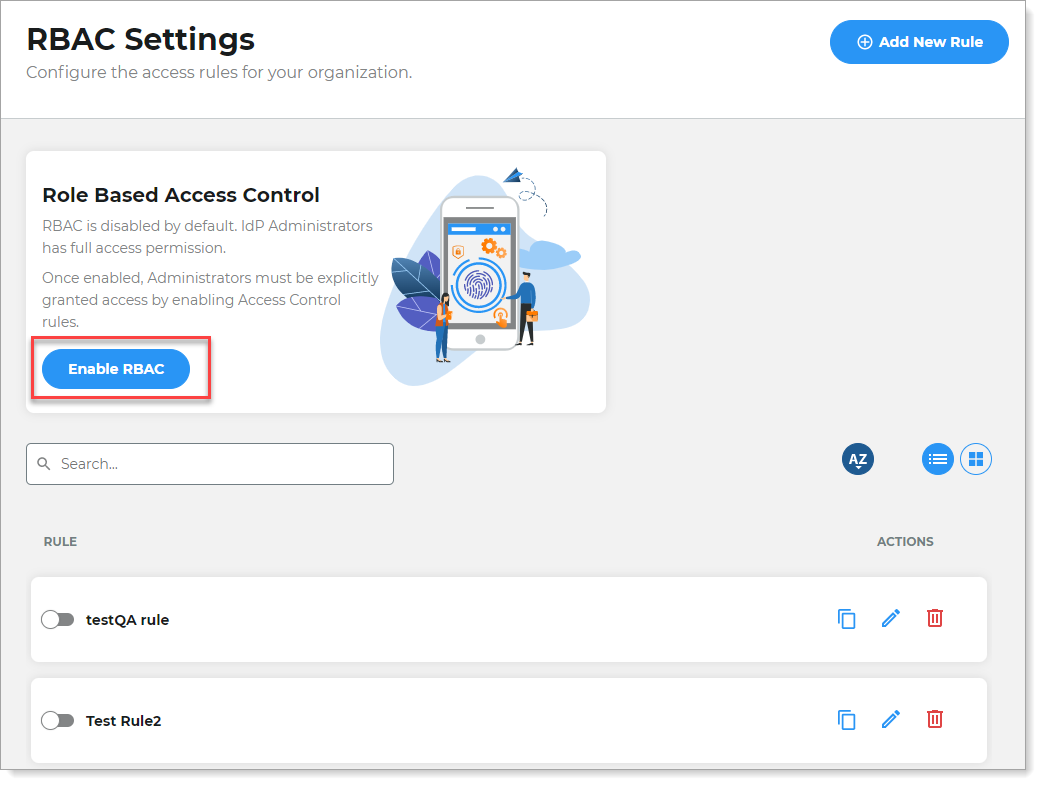
Do one of the following:
To assign the Super Admin role to individual users, type each username in the Enter Username field and press Enter.
To assign the Super Admin role to a user group, type the group name in the Enter Usergroup field and press Enter.
Note
For security reasons, the administrator that enables RBAC for the first time is automatically added as a Super Admin. They are unable to delete their name from the Enter Username field.
To remove themselves as a Super Admin, they must contact a local administrator.
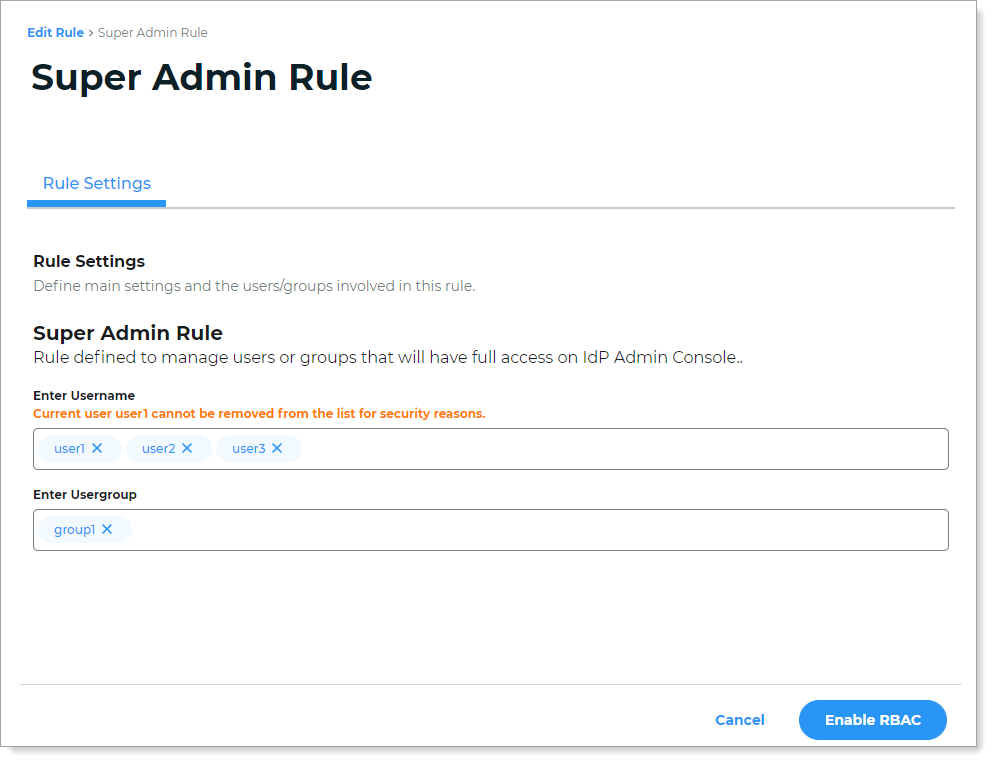
Click Enable RBAC.
Once RBAC is enabled, management options appear on the RBAC Settings page. You can do either of the following:
Click Disable RBAC to disable RBAC rules.
Click Edit Rule to edit the Super Admin rules.
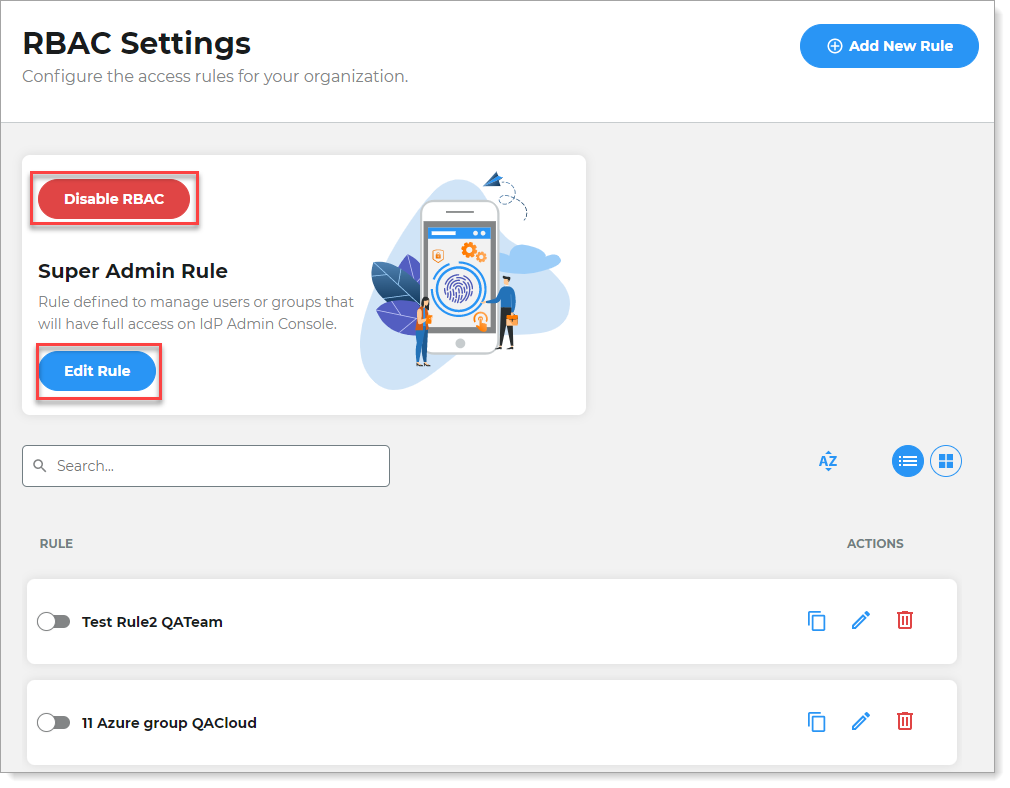
Create new rules
In this section, you will create rules to define roles in the appliance settings and restrict who has access and ability to view or change configurations.
Log in to the Identity Platform as a Super Admin.
On the left side of the Identity Platform, click RBAC Settings.
Click Add New Rule.
In the Rule Settings section, set the following:
Rule Name
Enter a unique name.
Rule Description
Enter a description about this rule.
Enable / Disable
Slide the toggle to Enable or Disable this rule.
Enter Username
Type each username to apply this rule to and press Enter.
Enter Usergroup
Type each group to apply this rule to and press Enter.
Click Next Step.
In the Classic Realms section, set the permissions for each realm created in the Classic Experience. The options are:
None – This is the default setting. Users have no access and cannot view realm configurations.
Ready only – Users can see that realm in the list of realms and can click on that realm to read its configuration. They cannot save changes.
Read/Write – Users can see that realm in the list of realms, can click on that realm to view its configuration, and can edit and save configurations.
Note
To set the same permission for all realms, select the persmission in the Fill all permissions section.
Use the Search bar to find a specific realm number.
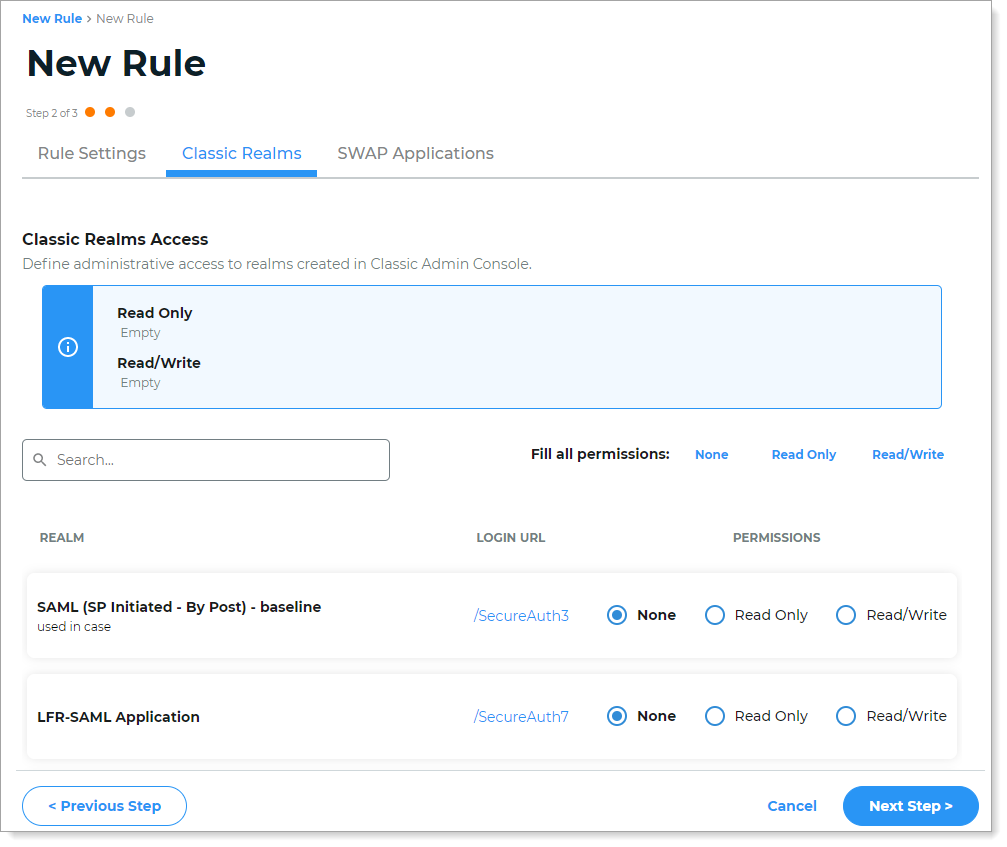
Click Next Step.
In the SWAP Applications section, set the permissions for each application created in the New Experience. The options are:
None – This is the default setting. Users have no access and cannot view realm configurations.
Ready only – Users can see that realm in the list of realms and can click on that realm to read its configuration. They cannot save changes.
Read/Write – Users can see that realm in the list of realms, can click on that realm to view its configuration, and can edit and save configurations.
Note
To set the same permission for all realms, select the persmission in the Fill all permissions section.
Use the Search bar to find a specific application name.
Select or deselect the Application Manager, Internal Application Manager, or Login for Endpoint buttons to filter applications by type.
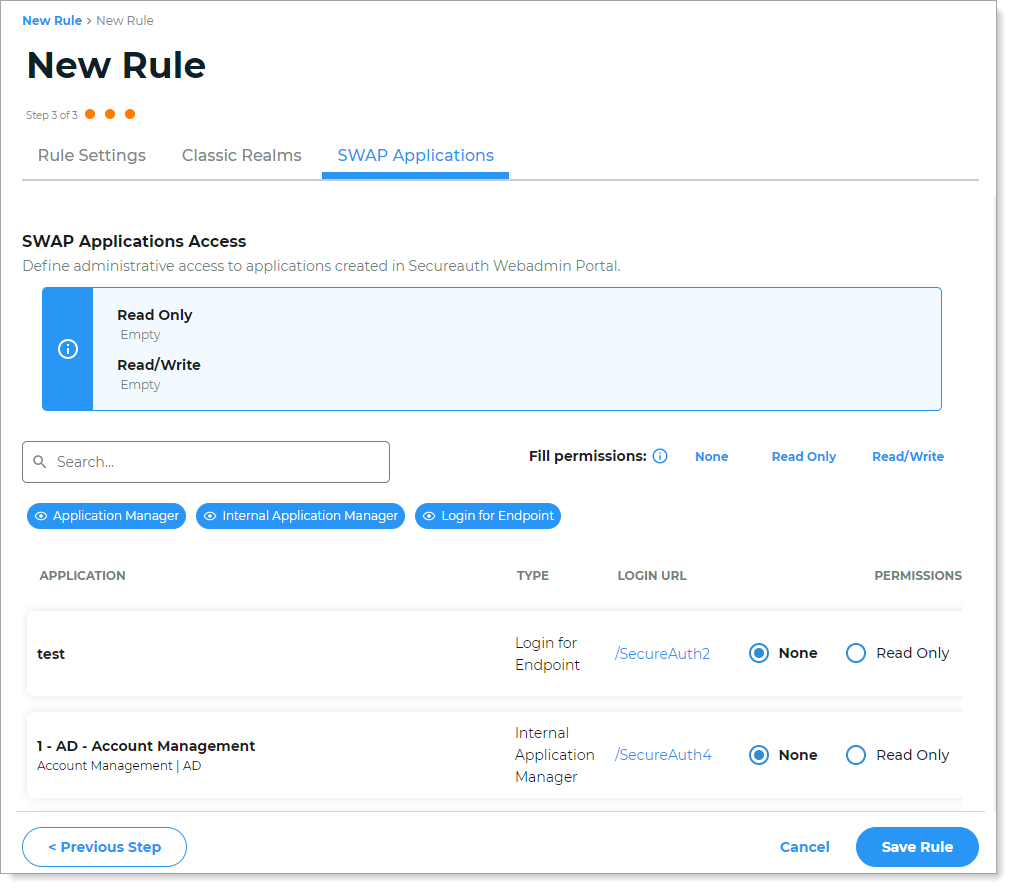
Click Save Rule.
Manage rules
Manage your RBAC rules in the RBAC Settings section. You can add, copy, edit, delete, enable, or disable rules.
Note
Use the Search bar to search for a rule by number, name, or description.
On the left side of the Identity Platform, click RBAC Settings.
Do one of the following:
To add a new rule, click Add New Rule.
To enable or disable a rule, slide the toggle next to the rule you want to enable or disable.
To copy a rule, click the copy icon next to the rule you want to copy.
To edit a rule, click the pencil icon next to the rule you want to edit.
To delete a rule, click the delete icon next to the rule you want to delete.
Enable and manage RBAC in Advanced Settings
The following workflow only applies to the hybrid deployment of the Identity Platform. Enabling RBAC via Advanced Settings is not currently supported for cloud deployment.
Note
If an administrator attempts to enable RBAC in Advanced Settings when it has already been enabled in the New Experience, the following error message appears:
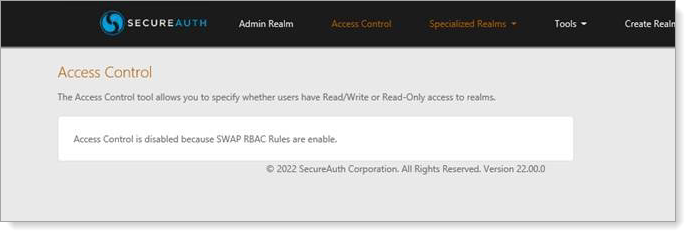 |
Prerequisites
Identity Platform hybrid deployment
Access to the Identity Platform appliance via Remote Desktop Protocol (RDP)
Data store directory (for example, Active Directory like LDAP) integrated with the Identity Platform Admin Realm (SecureAuth0) on the Data tab
Groups established in the data store directory to which the role-based rules apply
Activate the Access Control panel
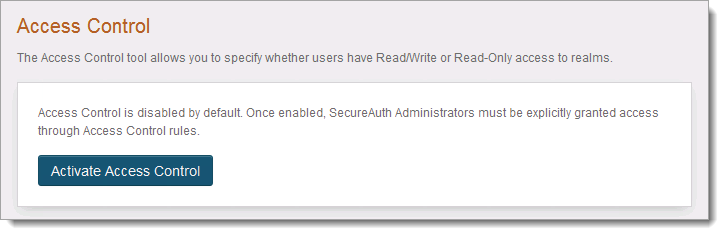
To create role-based rules for access, you will need to first activate Access Control in the Identity Platform and then create the role-based rules.
Use RDP to connect the Identity Platform appliance, and then access the Web Admin.
On the Web Admin home page, in the top menu bar, click Access Control.
This option is only accessible by means of RDP access.
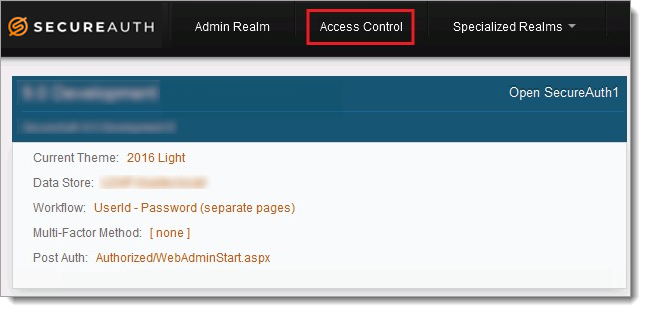
Click Activate Access Control.
Create and activate the first rule
Once Access Control is activated, you can create, activate and manage role-based rules.
Set the following:
Name
Set the name of the rule.
This rule displays on the Access Control Panel page.
Description
Provide descriptive text about the rule.
Realms
Select the Identity Platform realms to which this access control rule applies.
User Groups with Read and Write Permissions
Select the data store (LDAP) directory user groups to give read and write permissions to the specified realms.
The Access Control Rule form pulls information from the directory for auto-fill options.
User Groups with Read-Only Permissions
Select the data store (LDAP) directory user groups to give read-only permissions to specified realms.
It is not required to select a user group in this field, but at least one field must be set.

Click Save Rule.
When the first rule is created, a notification from the Identity Platform is sent to the Super Admin indicating that the Access Control is enabled.
In the Access Control panel, move the rule slider to publish and activate the rule.
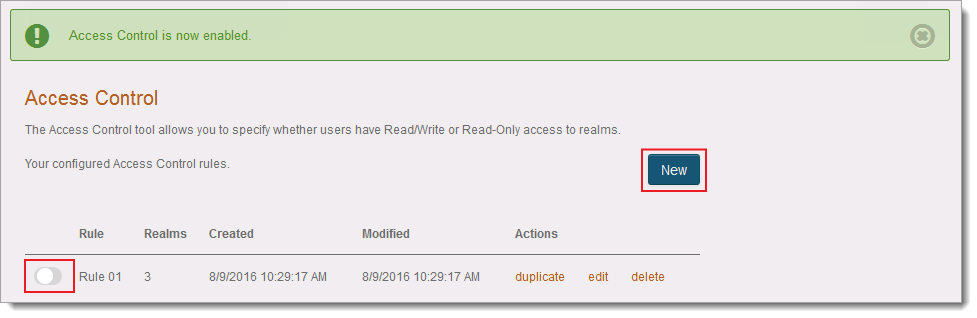
Create a new rule
After the first rule is created and activated, you can create more role-based permission rules.
In the Access Control panel, click New.
Set the following:
Name
Set the name of the rule.
This rule displays on the Access Control Panel page.
Description
Provide descriptive text about the rule.
Realms
Select the Identity Platform realms to which this access control rule applies.
User Groups with Read and Write Permissions
Select the data store (LDAP) directory user groups to give read and write permissions to the specified realms.
The Access Control Rule form pulls information from the directory for auto-fill options.
User Groups with Read-Only Permissions
Select the data store (LDAP) directory user groups to give read-only permissions to specified realms.
It is not required to select a user group in this field, but at least one field must be set.
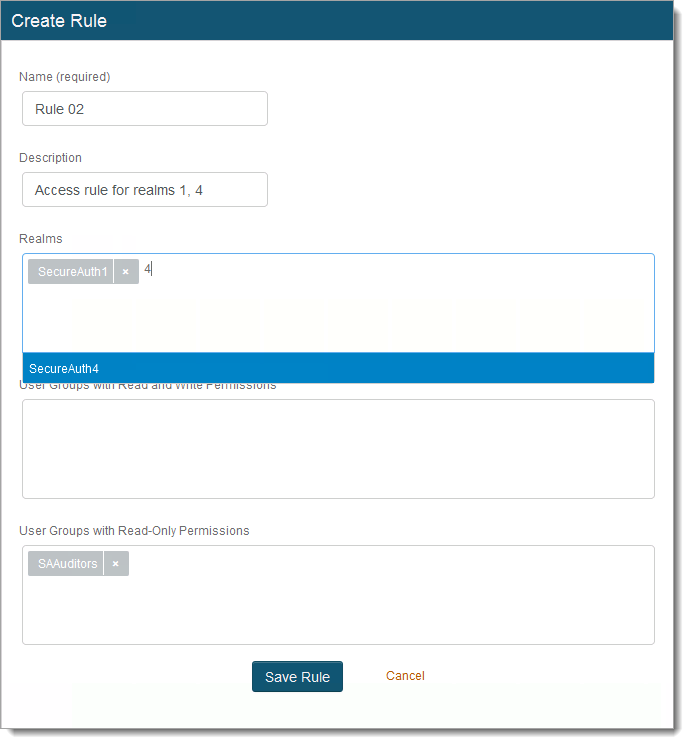
Click Save Rule.
Manage rules
From the Access Control page, you can duplicate, edit, or delete a rule.
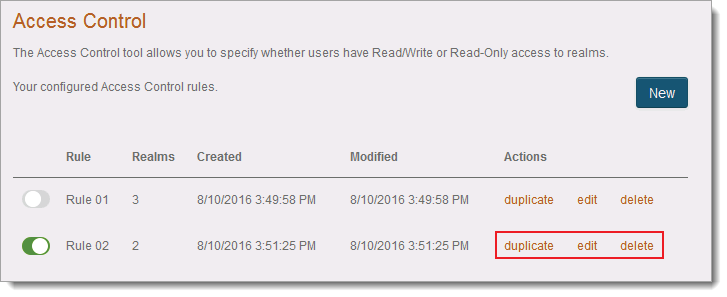 |
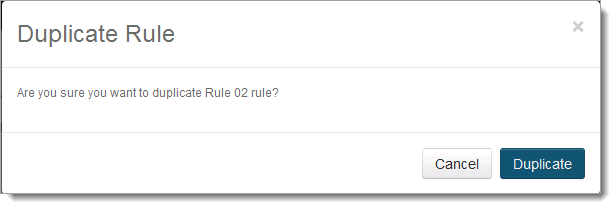
To duplicate a specific rule, click the duplicate link.
Confirm the action by clicking Duplicate.
The duplicated rule displays in the list.
To edit a specific rule, click the edit link.
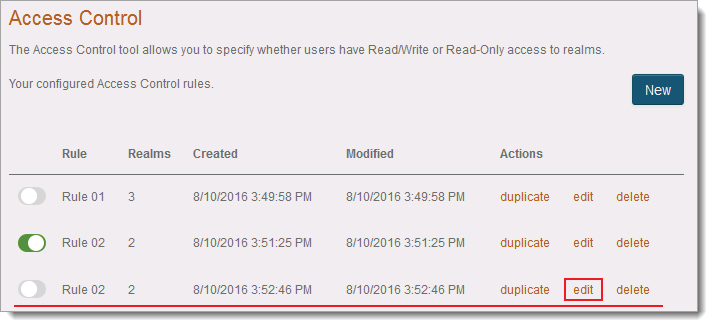
To delete a specific rule, click the delete link.
Confirm the action by clicking Delete.

All access controls defined by the rule are removed and the rule no longer displays in the list.