Dashboard insights
As an administrator, when you first log into the SecureAuth® Identity Platform, an intelligence dashboard provides real time visibility to key metrics. The dashboard contains cloud service versions associated with your Identity Platform tenant. You also gain insights into the total number of logins. It includes a break down of logins by system, applications, data stores, and use of multi-factor method (MFA) options.
Until you get the Identity Platform up and running and in production, you might get a 404 error and have no or limited incoming data.
The dashboard data metrics reports all browser workflow transactions. You can include API transactions if you use the /authenticated endpoint and add the request ID to the transactions.
Dashboard metrics are also available for SecureAuth® RADIUS Server and Login for Endpoints transactions. These metrics include login information for VPNs, remote server access, and endpoint desktop access to Windows and Mac.
The data refreshes every 24 hours; to get updated data, you can refresh the page.
Identity Platform system overview
In the top right of the dashboard, there is an overview of how many applications, data stores, and MFA methods are set up in the Identity Platform. You can use the date picker to globally change the date filter in all dashboard views.
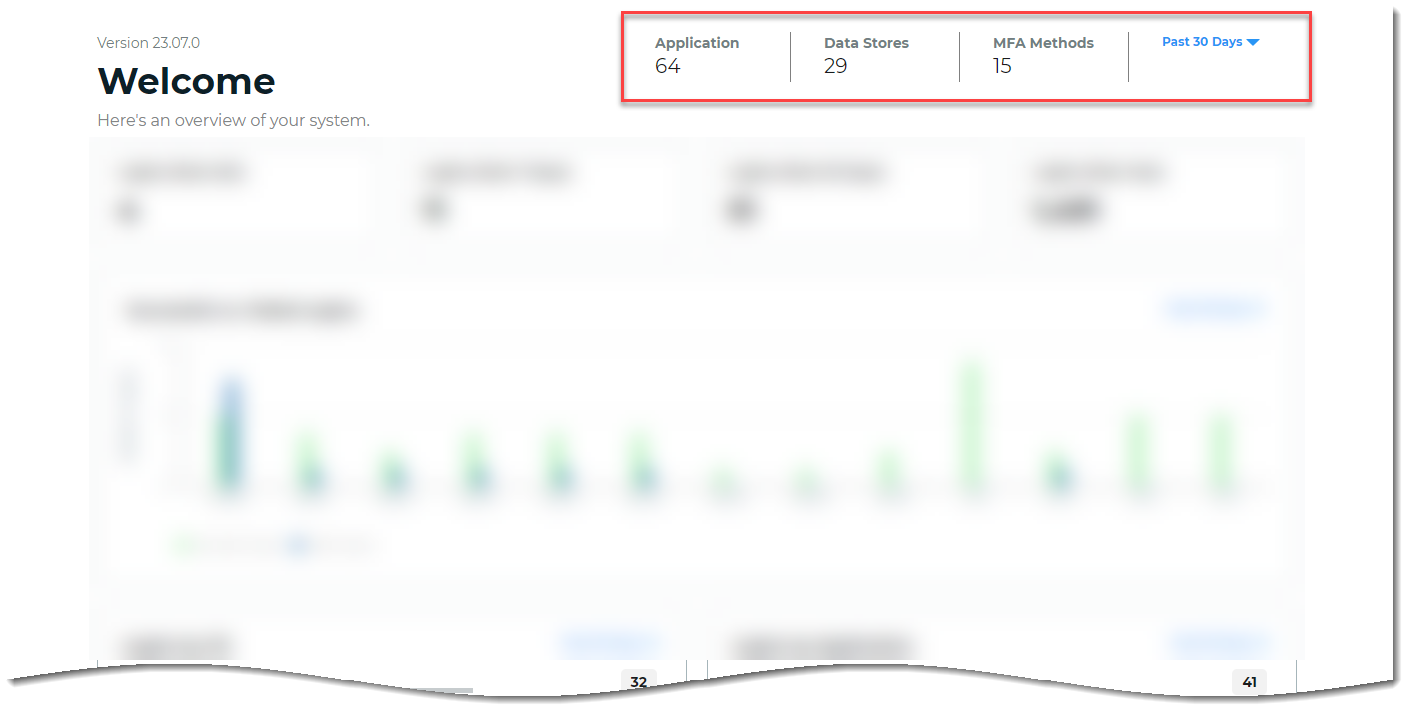 |
- Application
The number of applications integrated in the Identity Platform.
For example, applications like Office 365, Salesforce, Zoom, and so on.
- Data Stores
The number of data stores you have integrated in the Identity Platform.
For example, the user accounts for your organization are stored in Active Directory, Microsoft Entra ID (formerly Azure AD), Oracle DB, and so on.
- MFA Methods
The number of MFA methods used by end users for authentication into applications.
For example, you might have enabled up to ten (10) MFA methods in the Identity Platform, but only five (5) of them are being used by end users for authentication.
For a complete list of MFA methods like FIDO2 authenticators, Email (OTP), and SMS (Link-to-Accept) in use, see MFA Methods view section.
- Global date picker
Use the date picker to globally change the date filter in all dashboard widgets to view the past 24 hours, 7 days, 30 days, or year from today's date.
After you change the date filter, you can change the date filter in an individual dashboard widget.
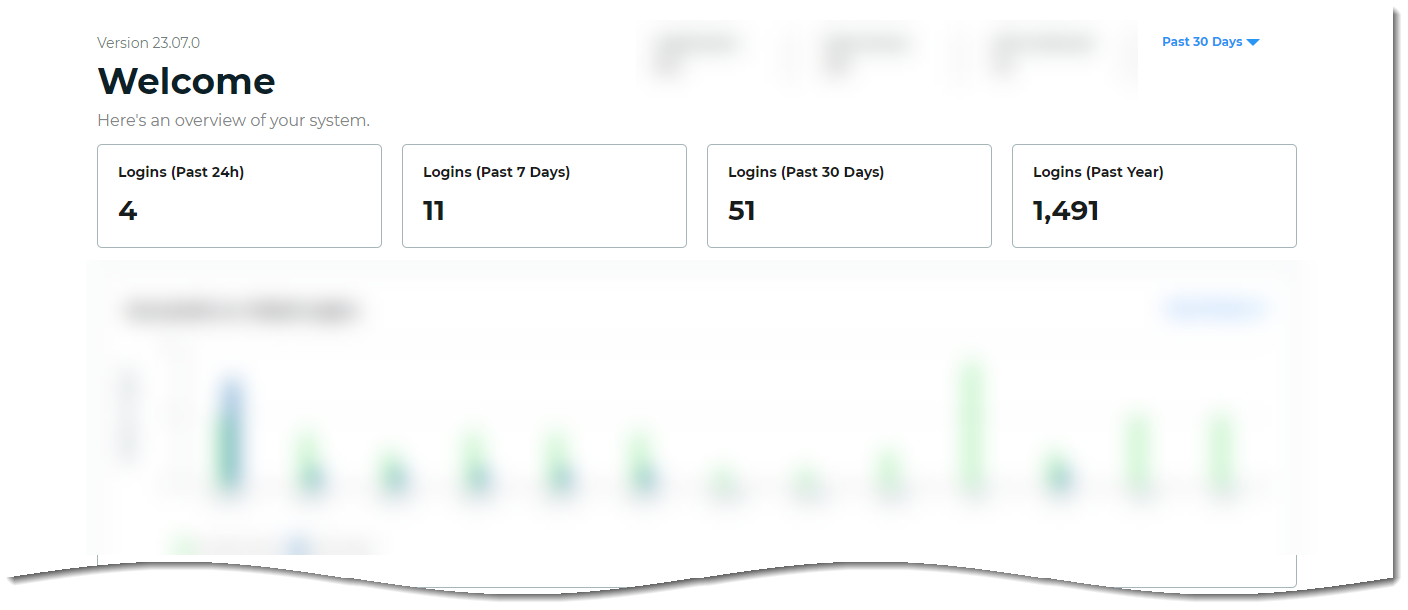
Number of logins to the Identity Platform
System overview of total logins, both successful and failed, processed by the Identity Platform.
View the number of total logins from the past 24 hours, 7 days, 30 days, and year from today's date. The login count includes transactions that are both logged as successful and failed.
 |
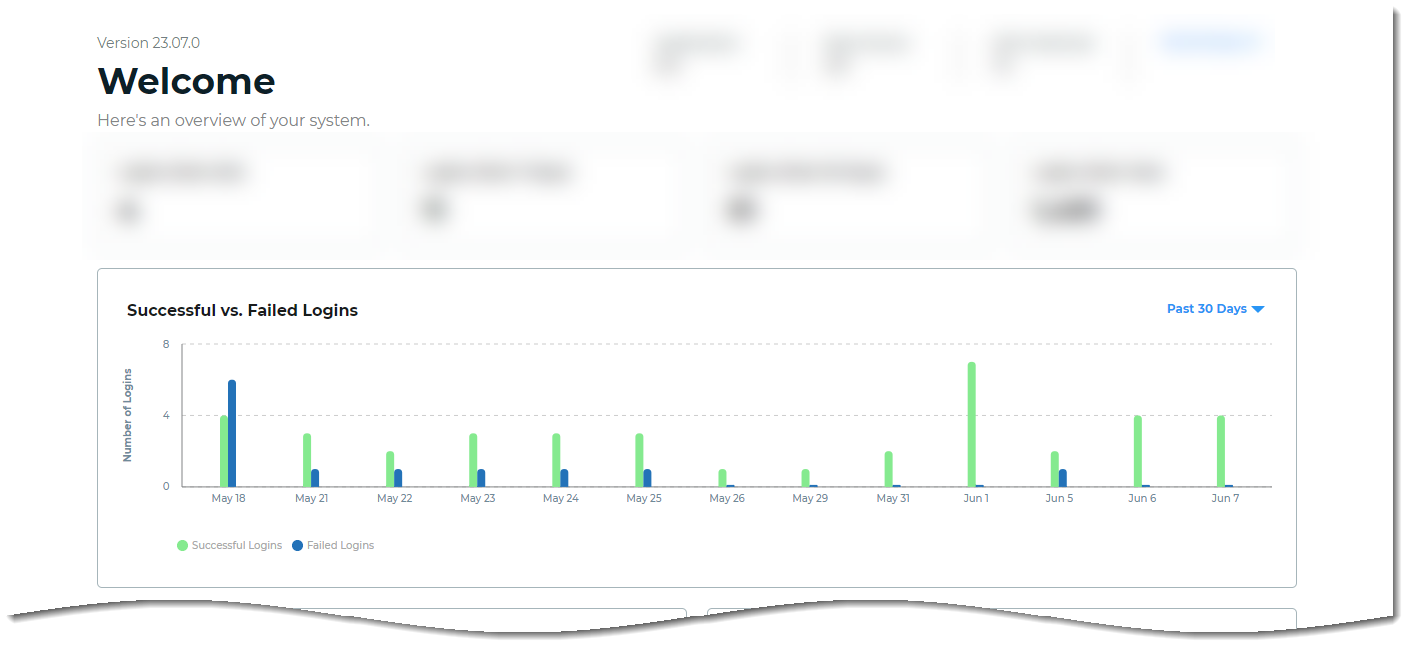
Successful vs. Failed Logins view
Bar graph displays the number of successful vs. failed logins processed by the Identity Platform.
You can change the view to past 24 hours, 7 days, 30 days, or year from today's date. Hover the mouse over a specific time period to view the number of successful logins and the number of failed logins.
 |
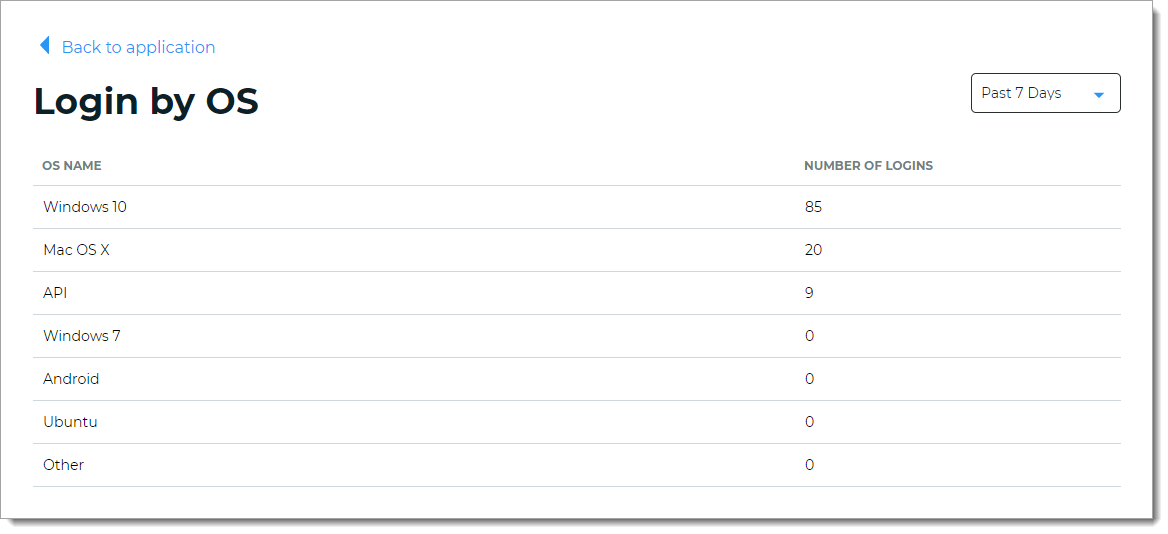
Logins by OS (operating system) view
Get insights into the number of logins on specific operating systems processed by the Identity Platform. For example, a user login to a resource occurred on Windows 10, Mac OS X, or Android mobile device.
The list includes API logins (displayed as "API" in the view) when the transaction is from an API workflow. If "Other" shows up on the list, it can mean an unrecognizable operating system.
Note
To add API transactions into dashboard reporting, it requires the Identity Platform 20.06 or later and the new /authenticated endpoint.
You can change the view to past 24 hours, 7 days, 30 days, or year from today's date. The list displays the top five commonly used operating systems for logins in a given date range.
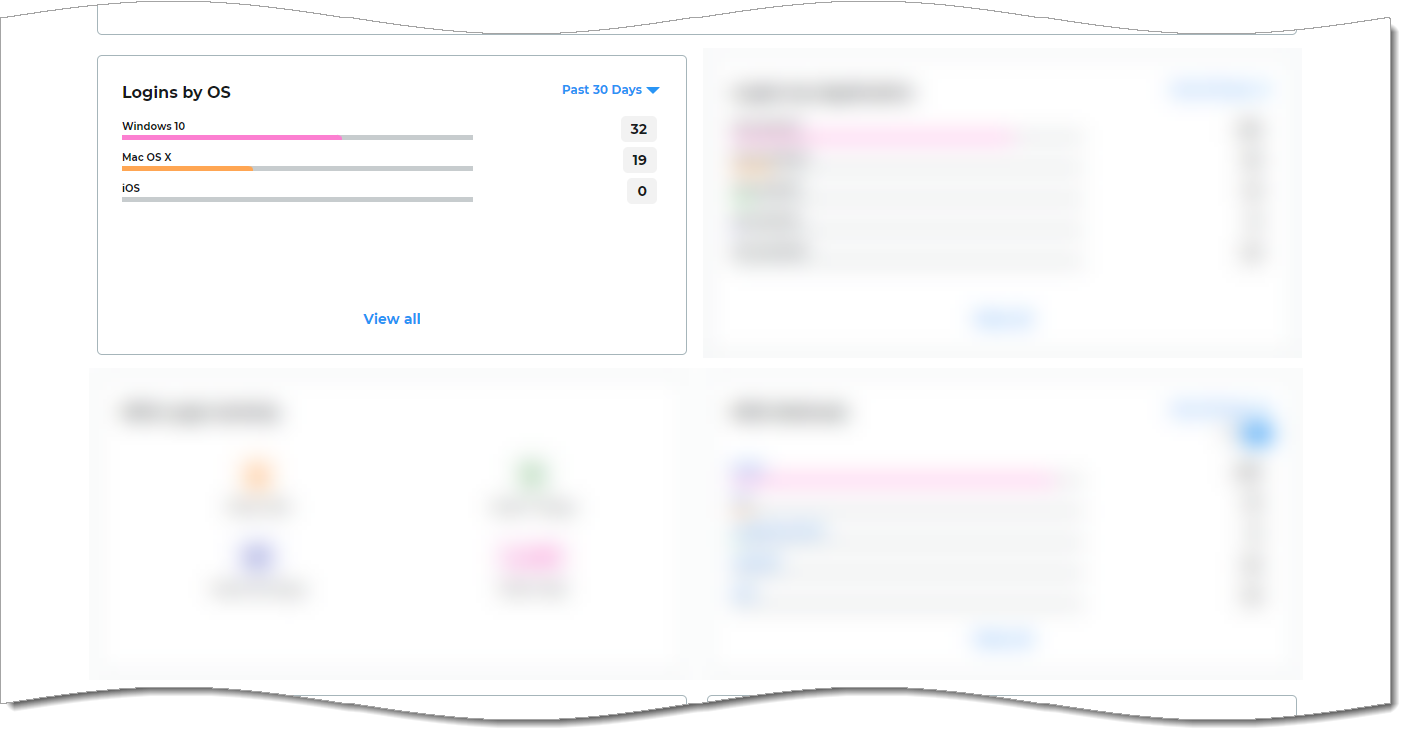 |
To see the entire list, click View all. The list sorts in descending order, the most commonly used operating systems for logins in a given date range.
 |
MFA Login Activity view
Displays the number of total MFA logins from your user base.
View the number of total MFA logins (failed and successful by all users) from the past 24 hours, 7 days, 30 days, and year from today's date.
 |
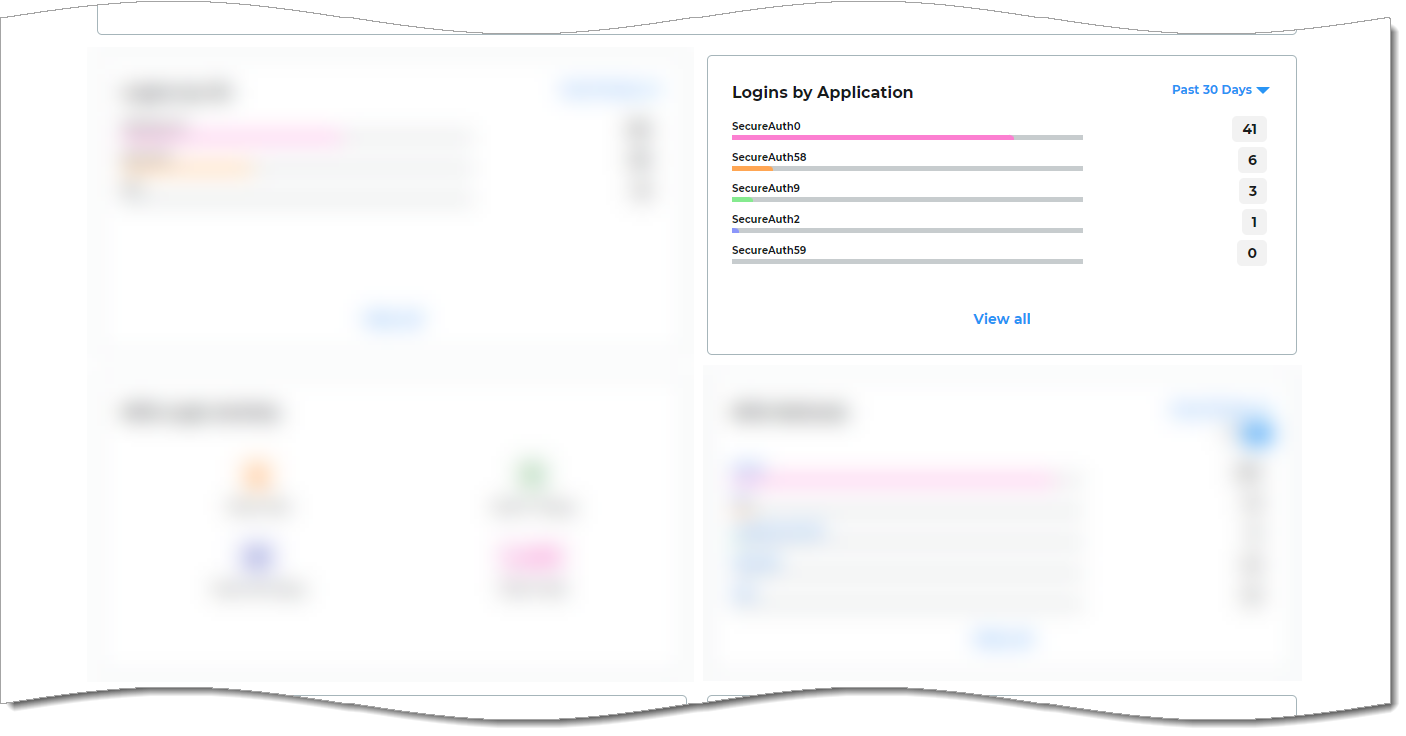
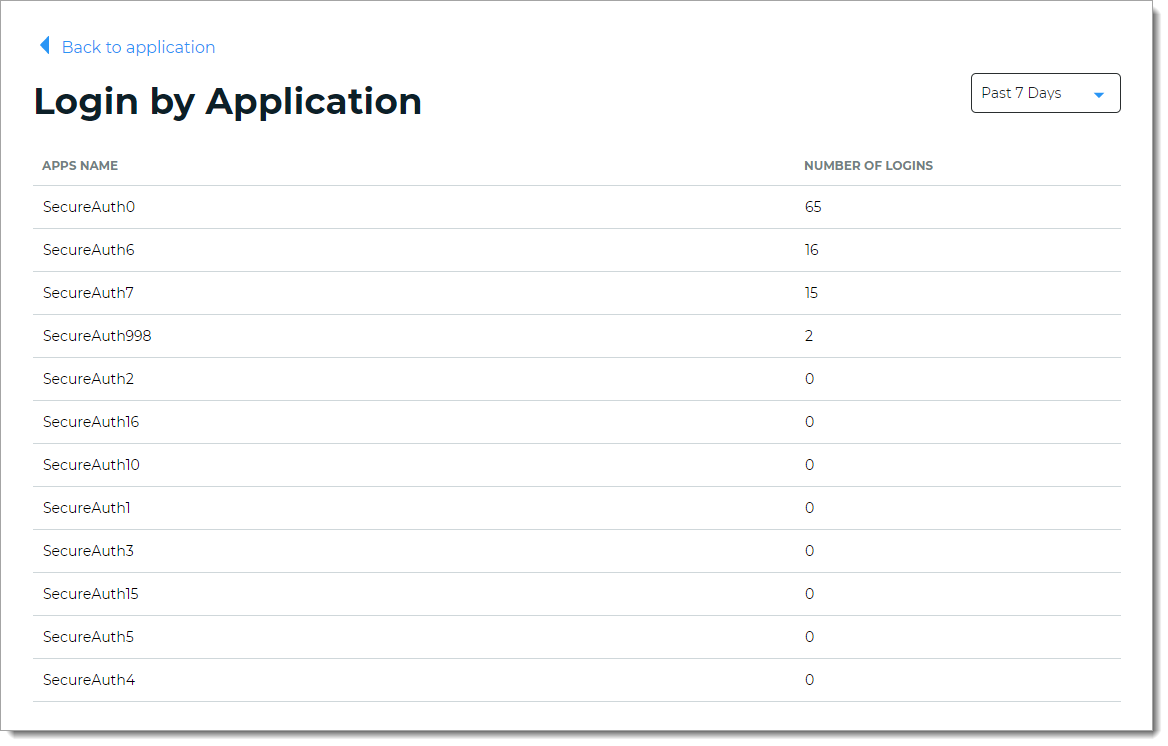
Logins by Application view
Get insights into the number of logins for each application (shown by its realm name). For example, Office 365, Salesforce, and Zoom. The list displays the top seven most commonly accessed applications in a given date range.
You can change the view to past 24 hours, 7 days, 30 days, or year from today's date.
 |
To see the entire list, click View all. The list sorts in descending order, the most commonly accessed applications in a given date range.
 |
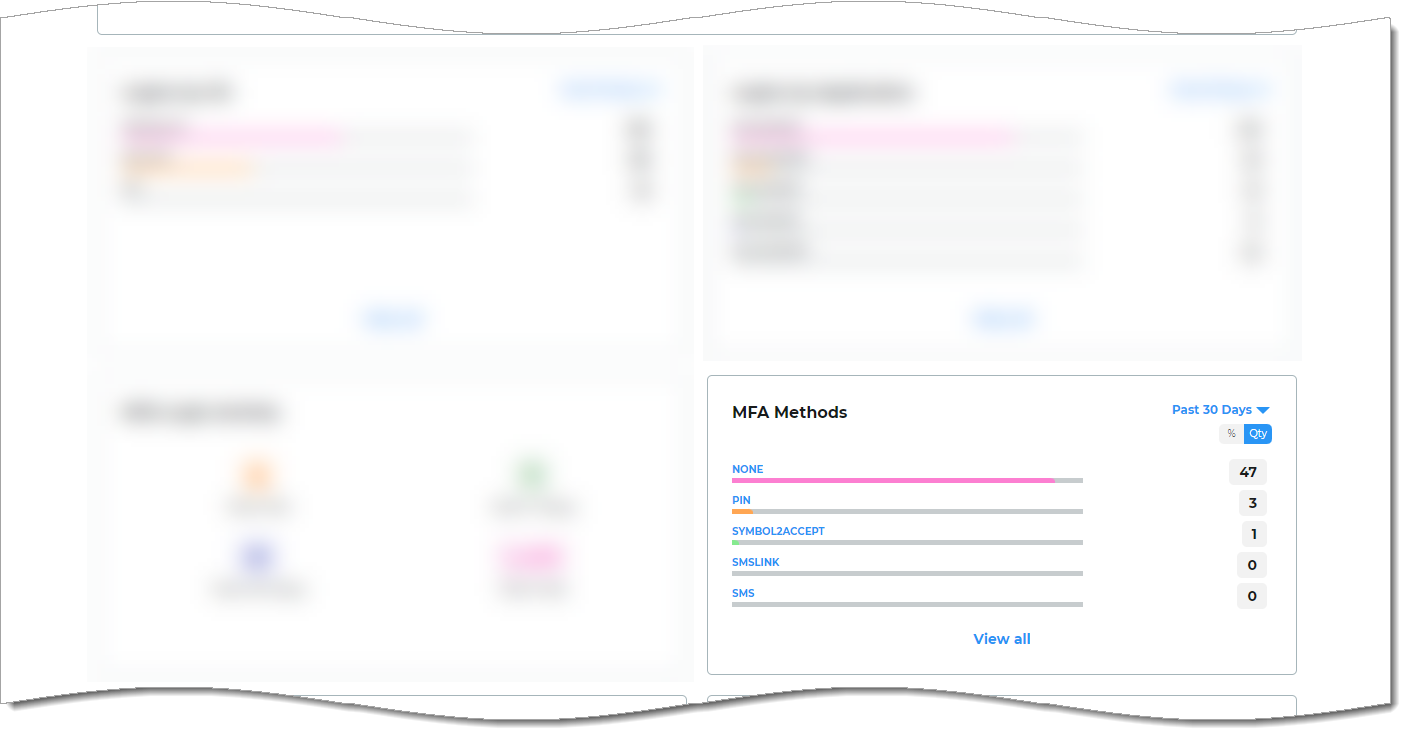
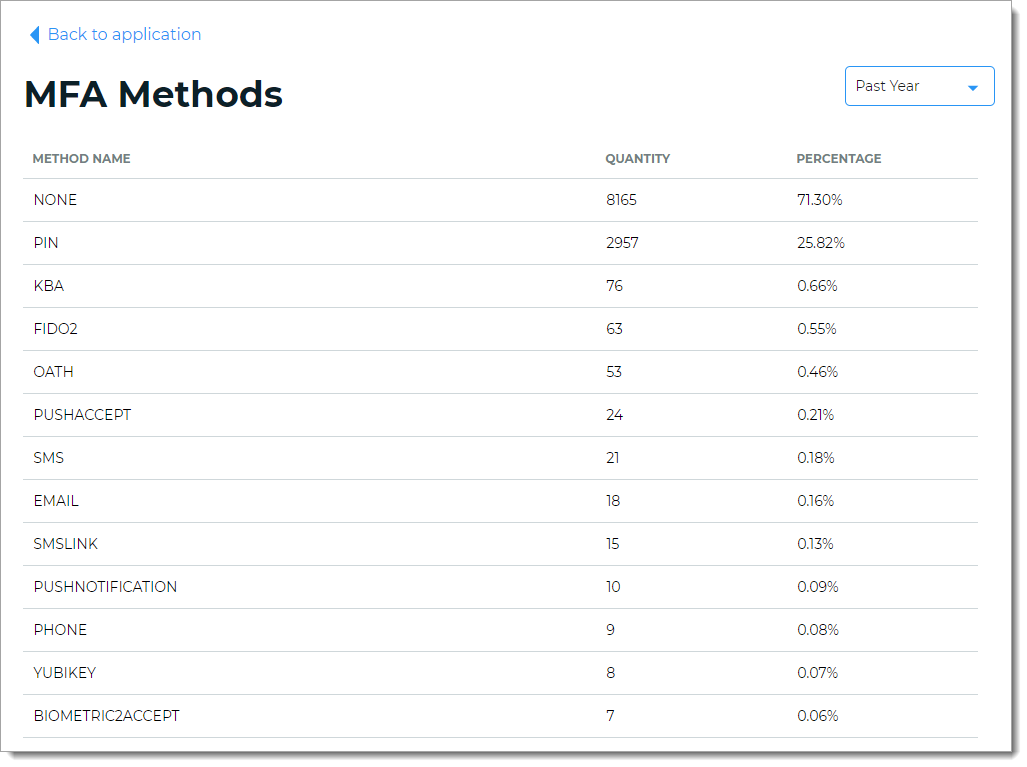
MFA Methods view
Get insights into the MFA options selected by end users to authenticate their access to applications. For example, FIDO2 authenticators, Email (OTP), SMS (Link-to-Accept), and so on.
You can change the view to past 24 hours, 7 days, 30 days, or year from today's date. The list displays the top five most commonly used MFA methods in a given date range.
For documentation purposes, the following table lists all the available MFA Methods in the Identity Platform. On the dashboard, it only displays the MFA methods actively used by end users.
 |
MFA Method name | Authentication type |
|---|---|
BIOMETRIC2ACCEPT | Biometric identification via Authenticate App |
One-time passcode (OTP) | |
EMAILLINK | Link-to-Accept |
FIDO2 | Registered FIDO2 authenticator |
HELP | Help Desk OTP |
KBA | Knowledge-based answer |
NONE | No MFA method used |
OATH | Time-based one-time passcode (OATH-TOTP and OATH-HOTP) |
<OTHER> | Placeholder for custom integration |
<Empty or invalid value> | Empty or not valid MFA method NoteIf the |
PHONE | Voice OTP |
PIN | Personal identification number |
PUSHACCEPT | Push-to-Accept |
PUSHNOTIFICATION | Push OTP |
SMS | OTP |
SMSLINK | Link-to-Accept |
SYMBOL2ACCEPT | Symbol-to-Accept |
VIPCREDENTIAL | Symantec VIP |
YUBIKEY | Non-FIDO2 YubiKey |
To see more detail about the MFA method used, click the name of the MFA method in the view. Two bar graphs display total of successful vs. failed logins and the volume of logins requests in given date ranges.
Hover the mouse over a specific time period to view the number of successful logins and the number of failed logins.
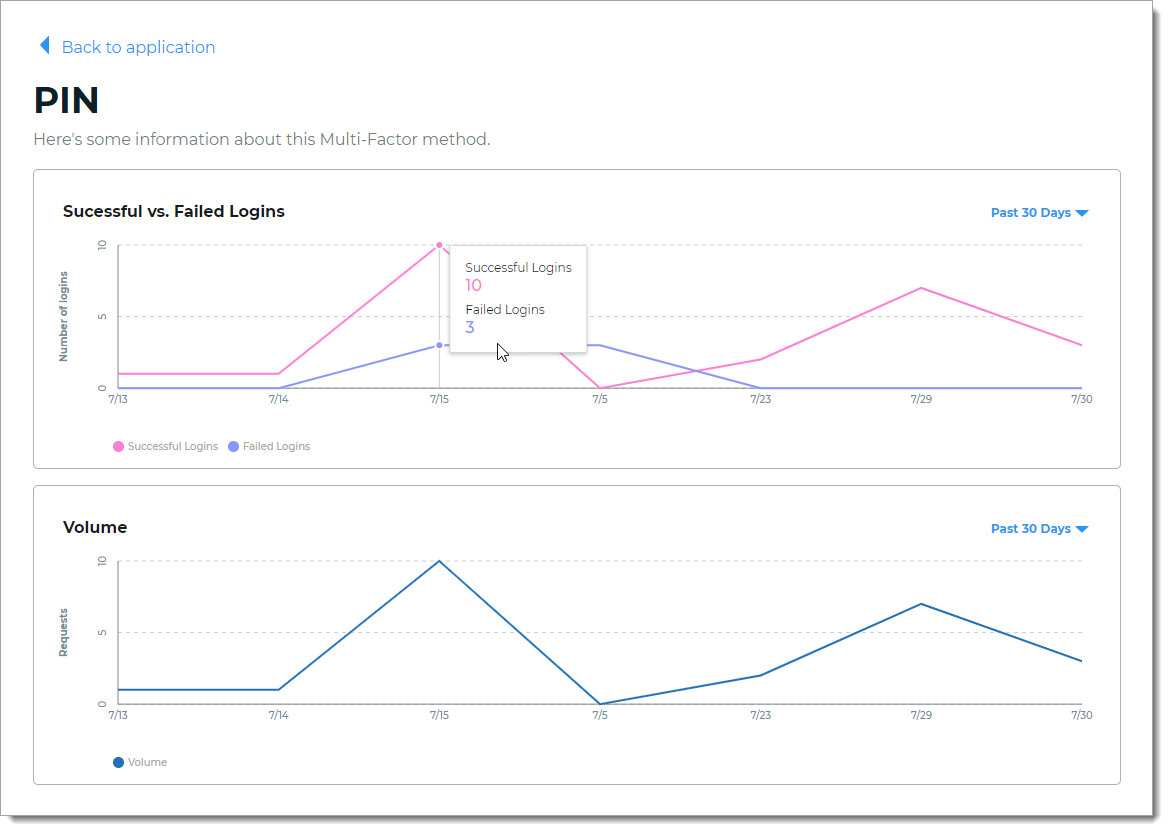 |
To see the entire list of MFA Methods actively used by end users, click View all. The list sorts in descending order, the most commonly used MFA methods in a given date range.
 |
Mobile Enrollments view
Get insights into the number of mobile devices end users have enrolled to authenticate their access to applications. For example, an end user's smartphone or tablet.
You can change the view to past 24 hours, 7 days, 30 days, or year from today's date. The list displays enrolled devices categorized by whether they are enabled for push notifications or time-based one-time password only.
 |
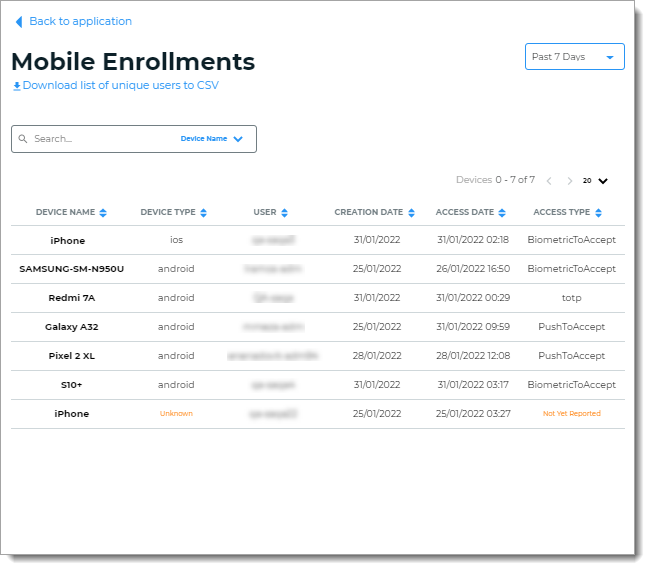
To see the entire list, click View all. The list can be sorted by Device Name, Device Type,User, Creation Date, Access Date, and Access Type in a given date range.
 |
Platform Product Versions
Provides real-time visibility of product service versions deployed with your Identity Platform tenant. The following are descriptions for each product service.
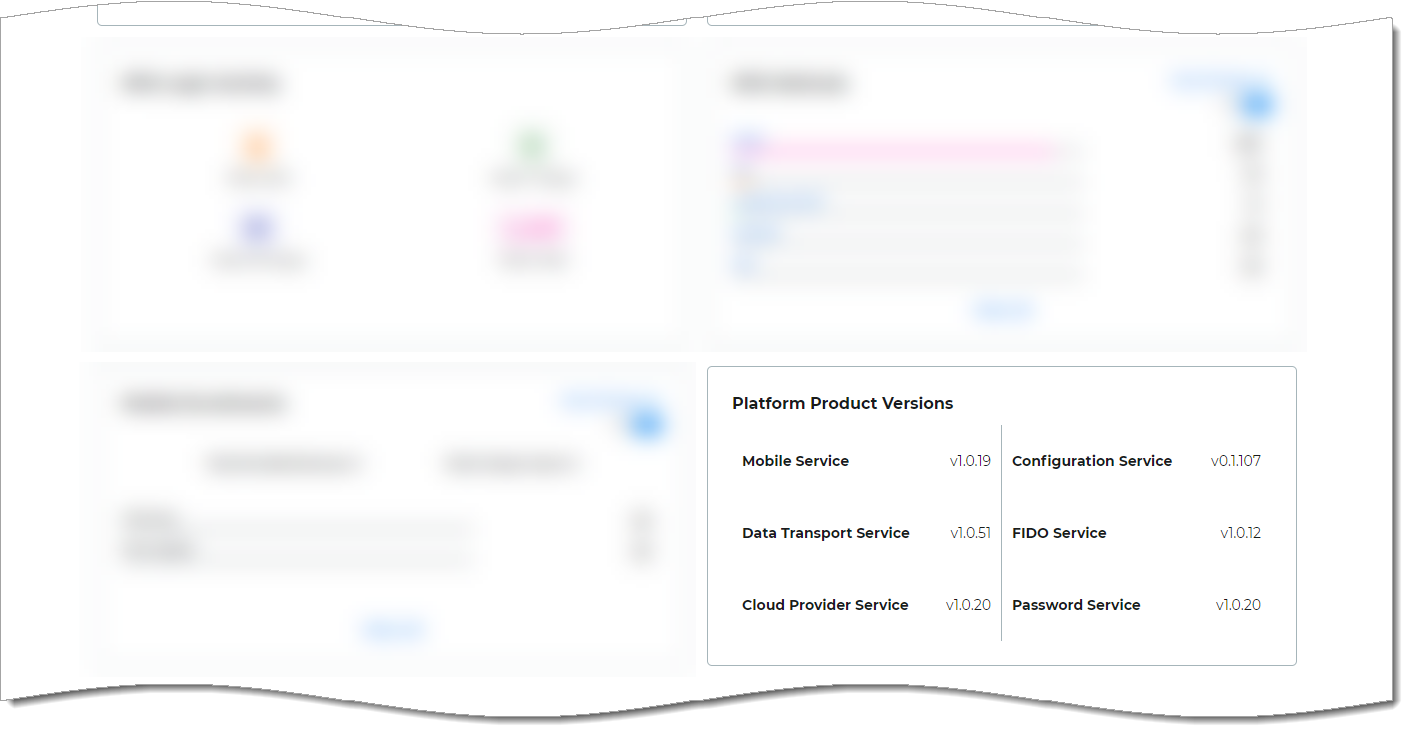 |
- Mobile Service
Maintains user mobile device and all other TOTP device enrollments and handles the authentication through those devices.
- Data Transport Service
Responsible for transporting user requests from the Identity Platform to either the SecureAuth Connector or the Cloud Provider Service depending on the data connection type. Also maintains user data related to Identity Platform features.
- Cloud Provider Service
Provides connection support to various cloud platforms including the Microsoft Entra ID (formerly Azure AD) data store and SCIM services. Does not have direct connection to the Identity Platform, requests are routed from the Data Transport Service.
- Configuration Service
Maintains encrypted administrative settings of the Identity Platform. All features look to this service for their configuration settings.
- FIDO Service
Maintains user FIDO device enrollments and handles the authentication through those devices.
- Password Service
Maintains password deny lists and password restriction rules during a Self-service Password reset.