Policy configuration - Login workflow
On the Login Workflow tab in a policy, you define the user login experience. You can configure other settings like not requiring a password if the user meets certain conditions, use Window SSO, allow the use of a QR scan to login.
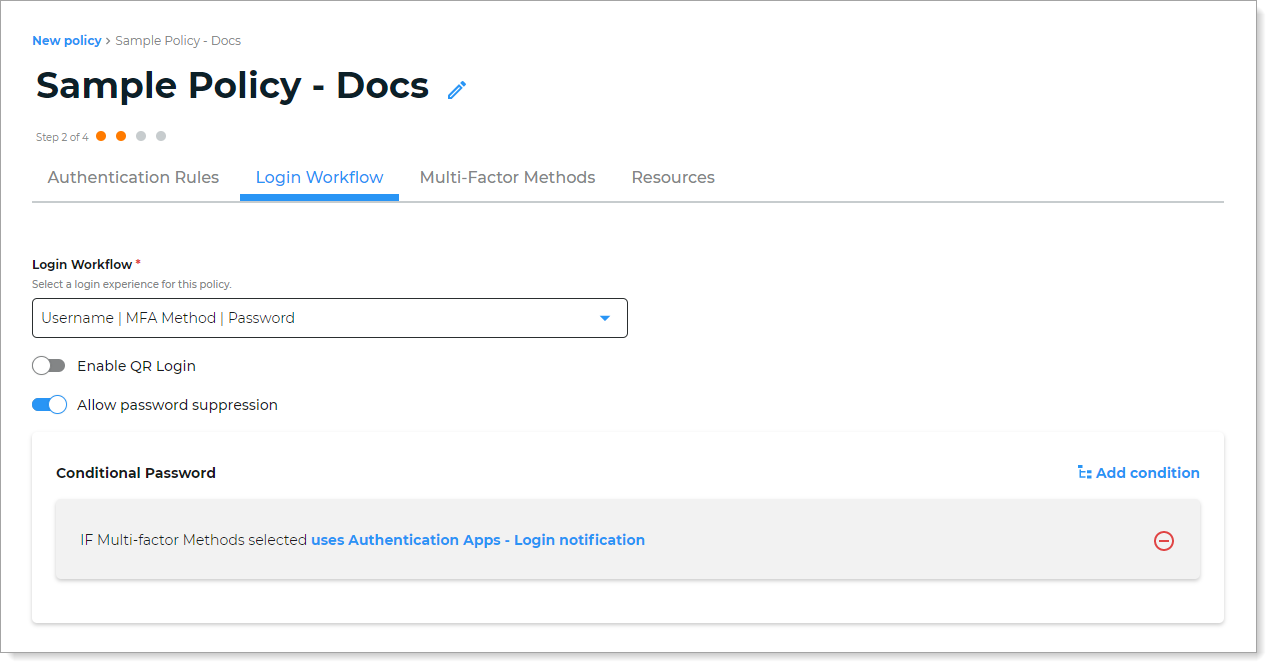
For example, you can allow users to login with a user name and approve a login notification they receive on their mobile device. If the user chooses a different MFA method, the user must enter their password.
The following is an overview of how to set this up:
For the login workflow, select Username | MFA Method | Password.
Move the slider to ON for Allow password suppression.
Add a condition to bypass the password entry. In this example, select Multi-Factor Methods > Authentication Apps - Login notification.
This condition indicates that if the user chooses to receive a login notification from an authentication app, they are not prompted to enter a password. Otherwise, if they choose a different MFA method, they must enter their password.
Setting up user login workflow
With a policy open in edit mode, select the Login Workflow tab.

Select the Login Workflow experience for users to access a resource attached to this policy.
Login workflow experience
Description
Passwordless
Includes Enable QR Login option to show a QR code on the login page. Requires Authenticate app version 23.03 or later.
For the end user, this the passwordless workflow login process:
Step 1: User provides username on the login page.
Step 2: User is prompted for multi-factor authentication on the next page.
The recommended authenticators for Passwordless login methods are:
FIDO2 security keys (Requires the Prevent licensing package.)
Phone as Token (timed passcode from an app, login notification, accept/deny method, select matching character displayed on device)
Biometric authentication (using SecureAuth Authenticate app)
One-time passcode
Scan QR code (using SecureAuth Authenticate app)
Username & Password | MFA Method
Includes Enable QR Login option to show a QR code on the login page. Requires Authenticate app version 23.03 or later.
When you add a new policy, this is the default login workflow selection. For the end user, this is the workflow login process:
Step 1: User provides username and password on the login page.
Step 2: User is prompted for multi-factor authentication on the next page.
Username | MFA Method | Password
Includes the following options:
Enable QR Login to show QR code on the login page. Requires Authenticate app version 23.03 or later.
Allow password suppression with any of these conditions:
Device Recognition
Group
Multi-factor Methods
User
Option 1: Do not use password suppression
For the end user, this is the workflow login process:
Step 1: User provides username on the login page.
Step 2: User is prompted for multi-factor authentication on the next page.
Step 3: User provides password on the next page.
Option 2: Use password suppression
For the end user, this is the workflow login process:
Step 1: User provides username on the login page.
Step 2: User is prompted for multi-factor authentication on the next page.
Step 3: User provides a password on the next page, unless they meet the defined condition and do not need to provide a password.
For example, the condition might be that they use a login notification from an authentication app.
(Valid Persistent Token) | MFA Method
For the end user, this is the workflow login process:
Step 1: User provides valid persistent token (in lieu of a username) on the login page. A persistent token could be a fingerprint.
Step 2: User is prompted for multi-factor authentication on the next page.
(Valid Persistent Token) | MFA Method | Password
Includes Allow password suppression option with any of these conditions:
Device Recognition
Group
Multi-factor Methods
User
For the end user, this is the workflow login process:
Step 1: User provides valid persistent token (in lieu of a username) on the login page. A persistent token could be a fingerprint.
Step 2: User is prompted for multi-factor authentication on the next page.
Step 3: User provides a password on the next page, unless they meet the defined condition and do not need to provide a password.
For example, the condition might be that they use a login notification from an authentication app.
Windows SSO | MFA Method
This option is available only in cloud deployments.
For the end user, this is the workflow login process:
Step 1: Windows SSO recognizes the username in the browser and proceeds to the next step.
Step 2: User is prompted for multi-factor authentication on the next page.
Otherwise, if Windows SSO is not recognized at login, it prompts the user for their username and password, then authenticates per policy rules.
You must have Allow Windows SSO integration turned on in the Identity Platform data store settings for Active Directory or Microsoft Entra ID (formerly Azure AD) to use this workflow configuration.
Save your changes.