Microsoft Entra ID configuration
Use this guide to configure Microsoft Entra ID (formerly Azure Active Directory) to allow read and optional write access and connect with the SecureAuth® Identity Platform.
After you complete this configuration, you can then add the Microsoft Entra ID data store in the Identity Platform.
Prerequisites
Identity Platform version 21.04 or later
Microsoft Entra ID and access to the Microsoft Entra admin center
Process
Step 1: Register the Identity Platform in Microsoft Entra admin center.
Step 2: Add API permissions in the Microsoft Entra admin center.
Step 3: Create a client secret in the Microsoft Entra admin center.
Step 4: Get the Microsoft Entra ID connection settings; you will need this in the Identity Platform.
Note
Microsoft changed the name from Azure AD to Microsoft Entra ID. The configuration screenshots may be out of date, but the process should be similar.
Step 1: Register the Identity Platform in Microsoft Entra admin center
To integrate Microsoft Entra ID (formerly Azure AD) with the Identity Platform, you need to register the Identity Platform in the Microsoft Entra admin center.
Log in to your Microsoft Entra account through the Microsoft Entra admin center.
Select Azure Active Directory.
Select App registrations.
Select New registration.
Set a Name and keep the default Supported account types selection option to a single tenant.
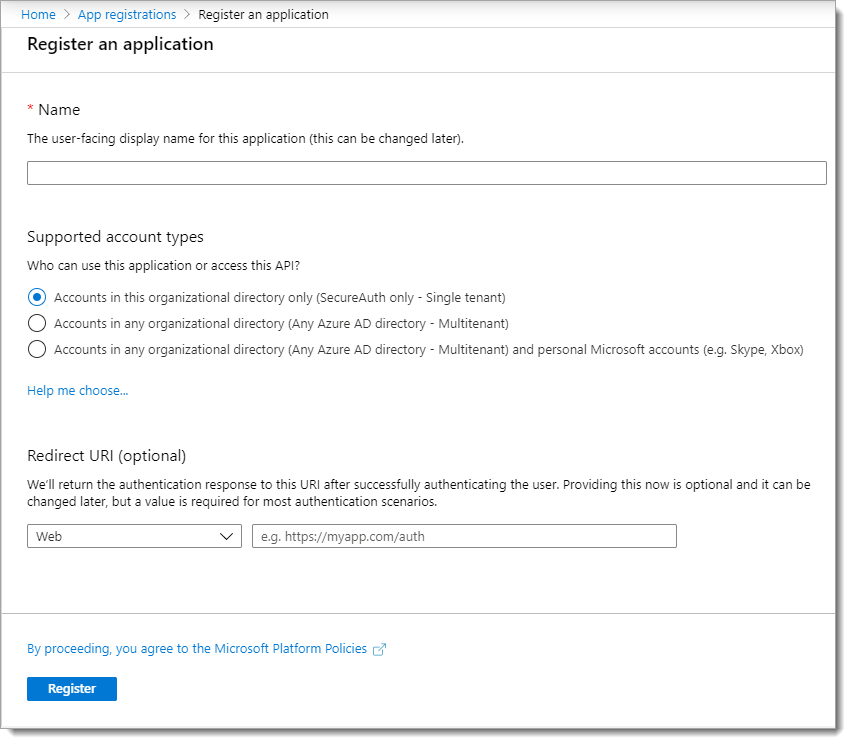
Click Register.
Step 2: Add API permissions
You will need to grant read and write permissions for the Identity Platform API calls to Microsoft Entra ID.
From the App registrations list, click name of the registered app that you just created.
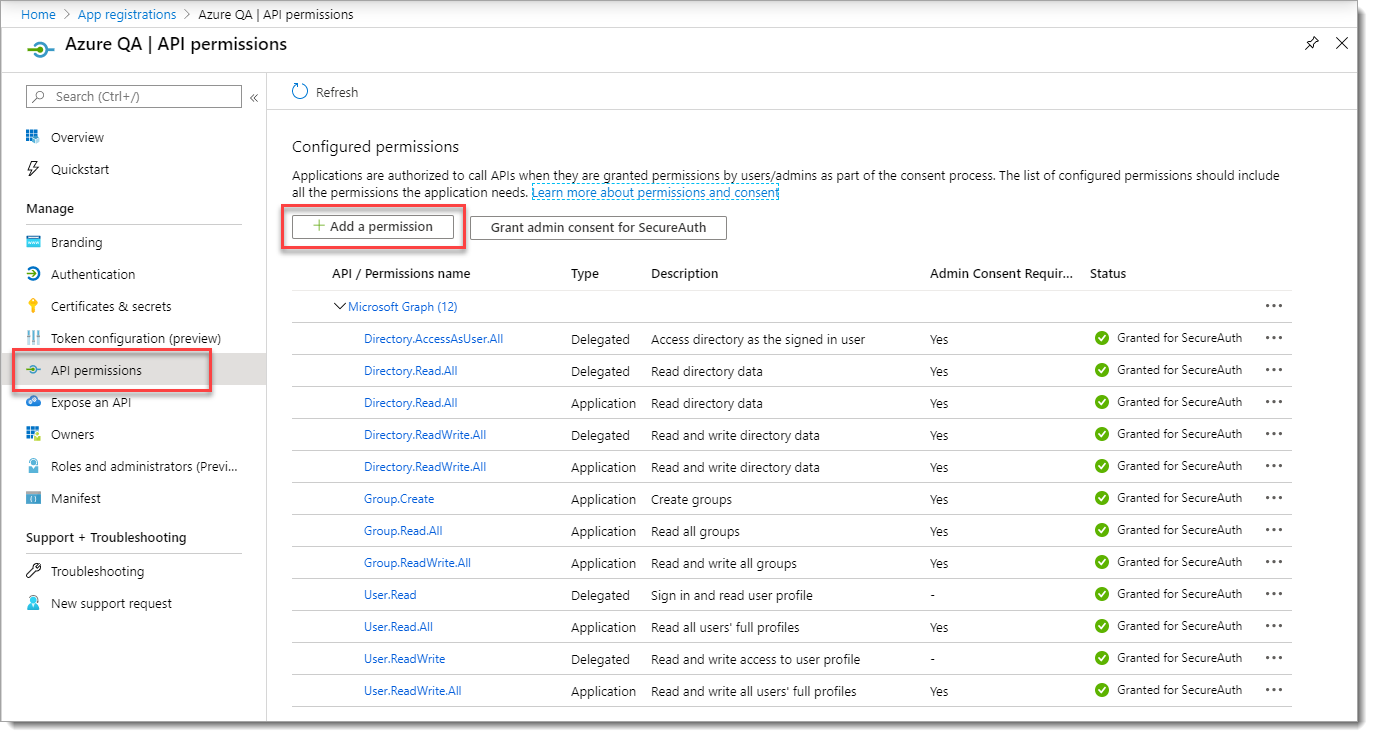
In the left pane, click API Permissions. Then, click Add a permission.
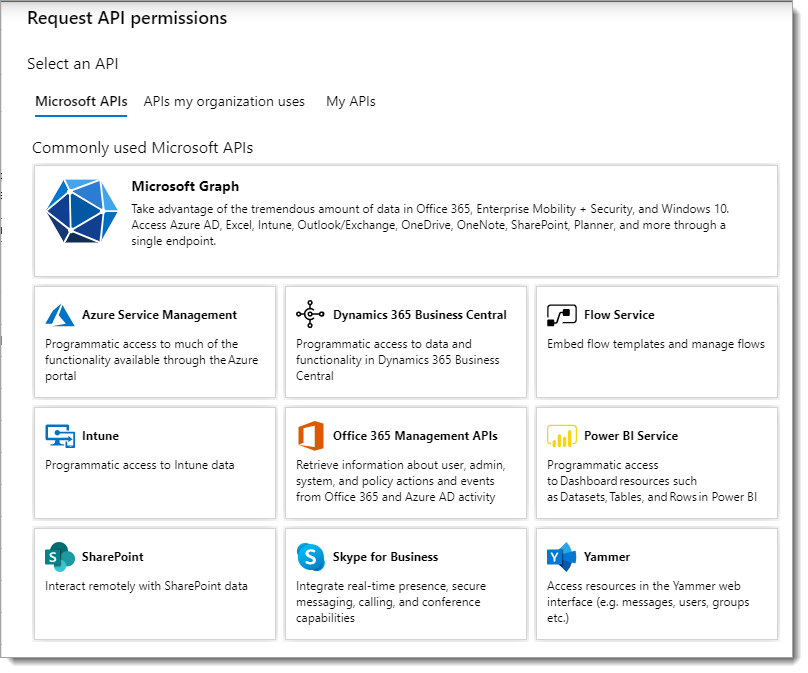
Select Microsoft Graph.
Click Delegated permissions. Then, scroll down to find and select the following check boxes:
Directory.AccessAsUser.All
Directory.Read.All
Directory.ReadWrite.All
User-PasswordProfile.ReadWrite.All
User.Read
User.ReadWrite
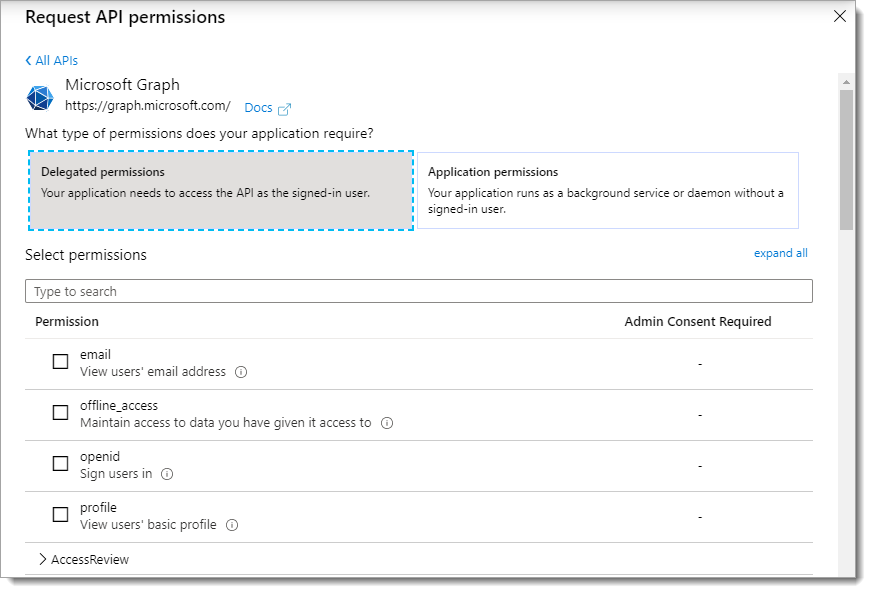
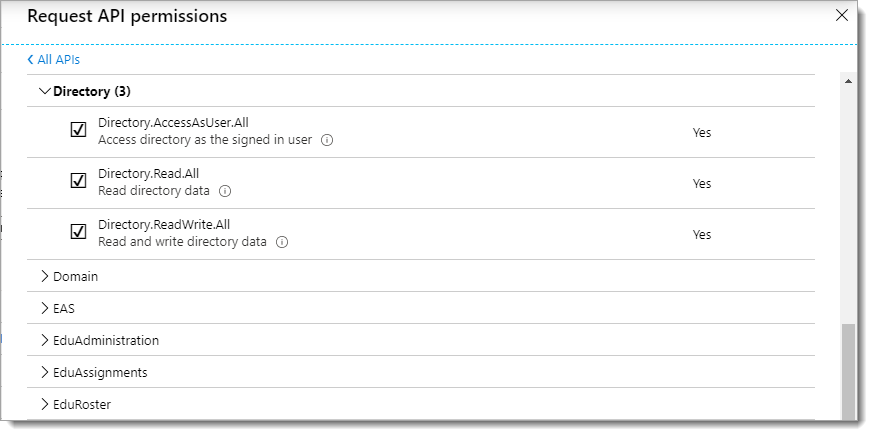
When you are done making your selections for delegated permissions, click Add permissions at the bottom of the page.
Click Application permissions. Then, scroll down to find and select the following check boxes.
Directory.Read.All
Directory.ReadWrite.All
Group.Create
Group.Read.All
Group.ReadWrite.All
User-PasswordProfile.ReadWrite.All
User.Read.All
User.ReadWrite.All
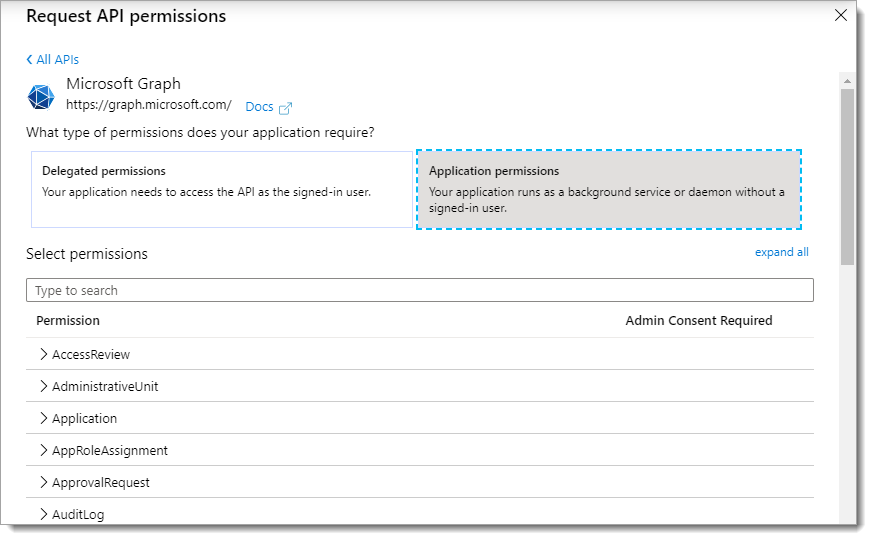
When you are done making your selections for application permissions, click Add permissions at the bottom of the page.
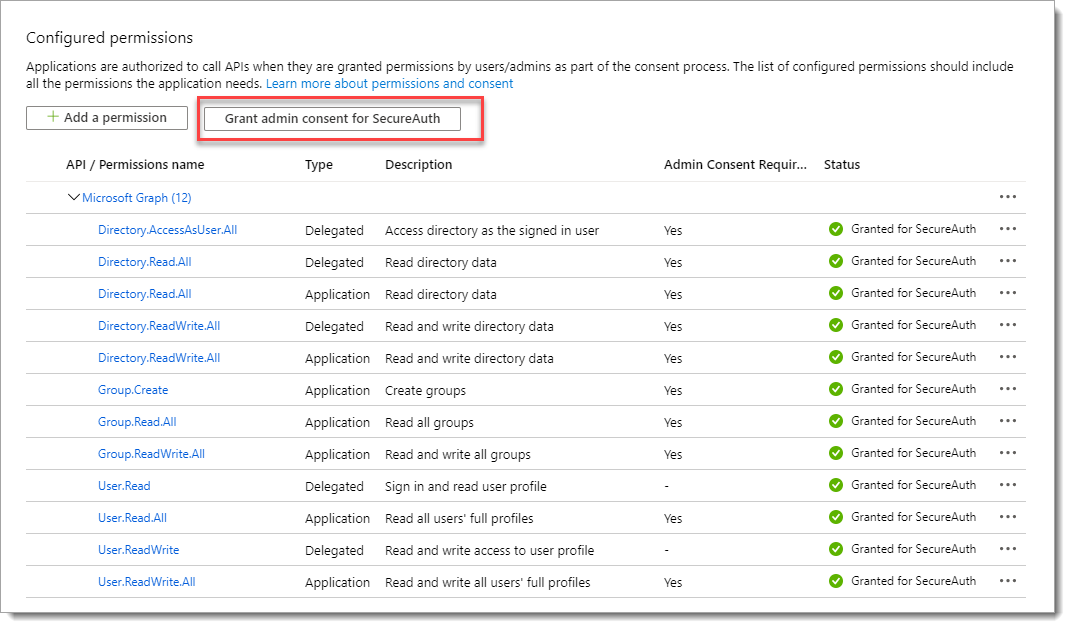
View and verify the list of configured permissions and click Grant admin consent.
Step 3: Create client secret
Create an application secret key so the Identity Platform can connect to Microsoft Entra ID. You will need to copy and paste this client secret in the connection settings when you add the Microsoft Entra ID data store in the Identity Platform.
From the left pane, click Certificates & secrets. Then, click New client secret.
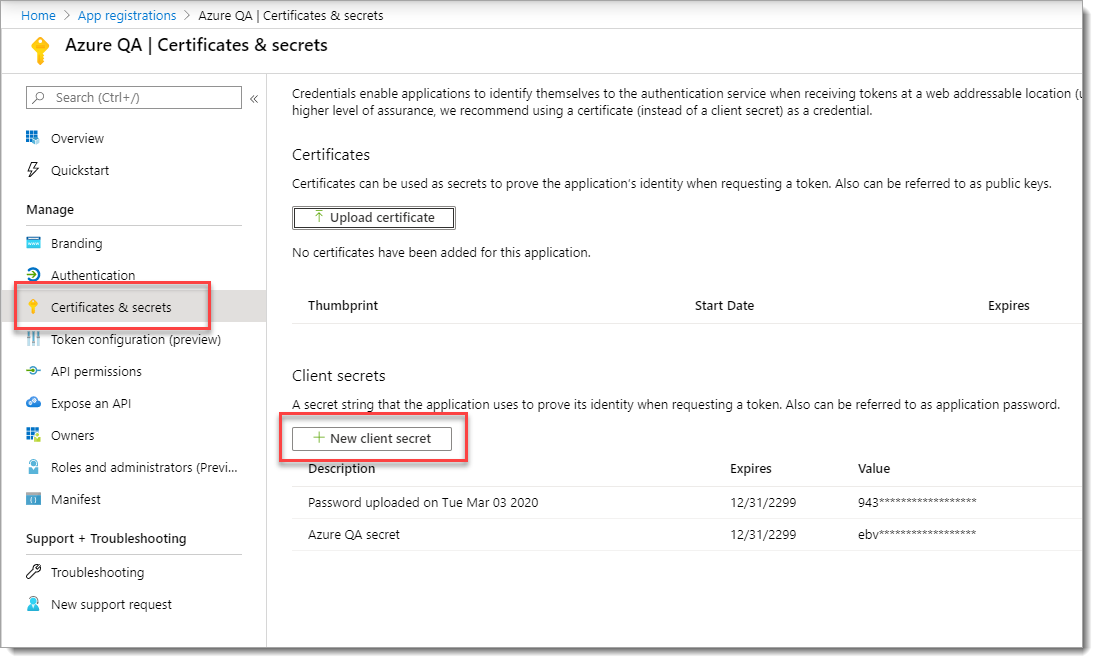
Add a description for the client secret and choose Never for the expiration.
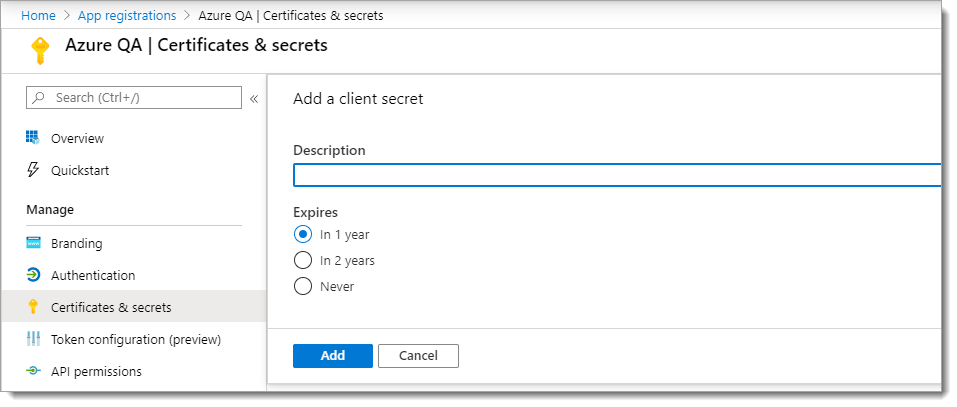
Click Add.
Copy the client secret key, before it gets masked when you leave the page.
From the left pane for this app registration, click Authentication.
In the Advanced settings section, select Yes.
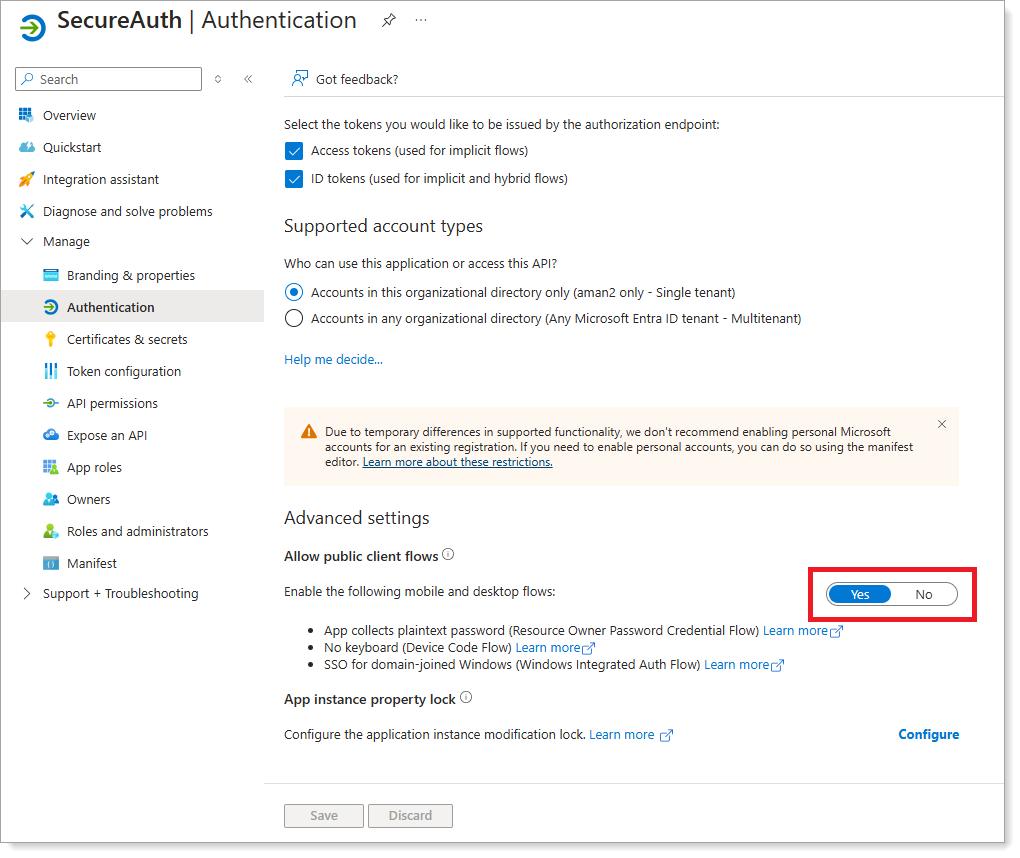
Fixing app visibility in Conditional Access
Important details
When you set Allow public client flows to Yes, the application no longer appears in the app picker for Conditional Access policies. The Conditional Access option is also removed from the application settings in your Entra ID tenant.
If a Conditional Access policy requires MFA for All resources (formerly All cloud apps), you can't exclude this application from the policy. The Identity Platform won’t be able to validate user passwords because non-interactive calls can’t perform MFA.
To fix this, update at least one of the following conditions in your Conditional Access policy:
Instead of choosing All resources, select specific resources/cloud apps.
Exclude a required set of users.
Exclude these IP addresses:
3.93.106.14/32 34.193.74.174/32 18.235.146.118/32 54.221.73.164/32 18.210.166.159/32 13.222.85.211/32
Step 4: Get Microsoft Entra ID connection settings
When you add a Microsoft Entra ID data store in the Identity Platform, you will need to capture and provide the following information in the Identity Platform data store connection settings.
Microsoft Entra Tenant Domain (for example, company.onmicrosoft.com)
Directory Tenant ID
Client ID
Client secret key (when you created a client secret key in the Micrsoft Entra admin center, you should have copied this value)
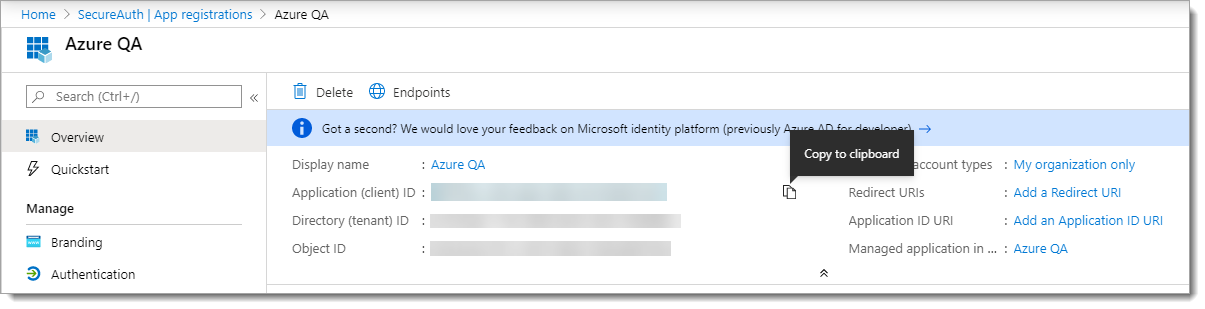
Capture connection IDs in Microsoft Entra admin center
Select Microsoft Entra ID (formerly Azure Active Directory).
Select App registrations.
From the list, click the application name link.
Hover your mouse to the right of the ID strings and select Copy to clipboard.