VMware Horizon integration guide with RADIUS
Use this guide to integrate VMware Horizon with SecureAuth® Identity Platform using RADIUS OTP as a second-factor.
Prerequisites
Have VMware Horizon (or VMware View) connection server version 5.x or later
Have SecureAuth Identity Platform configured with a Multi-Factor App Enrollment realm (URL or QR code)
Configure and enroll SecureAuth Apps
Configure the SecureAuth RADIUS Server
VMware Horizon configuration
You will need to configure the SecureAuth RADIUS Server appliance to point to the VMware Horizon View connection server IP address.
As the authentication type, use OTP_ONLY.
From a web browser, open VMware Horizon Administrator.
Go to to View Configuration > Servers > Connection Servers.
Select the Connection Server and click Edit.
Select the Authentication tab.
In the Advanced Authentication section, set the following: the 2-factor authentication option to RADIUS.
2-factor authentication
Set to RADIUS.
Authenticator
Select Create New Authenticator.
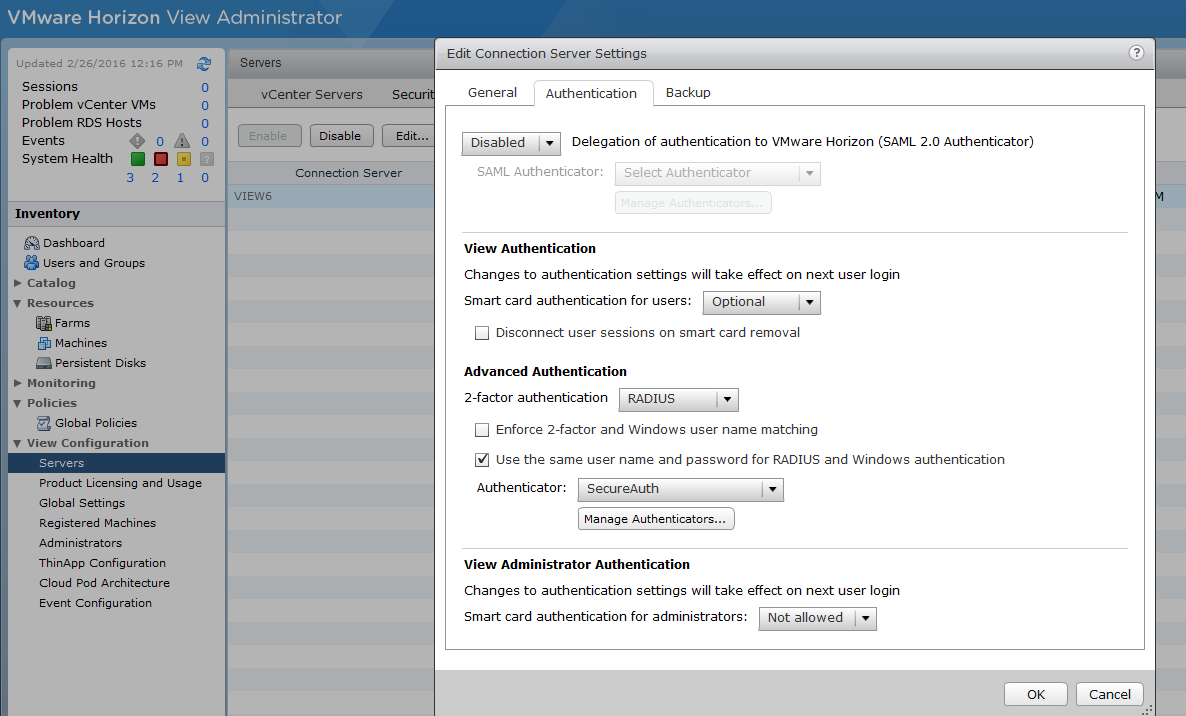
On the Edit RADIUS Authenticator window, set the following configurations.
Label
Enter a user-friendly name. This will be visible in the Horizon View Client.
Description
Enter a description. This will not be visible in the Horizon View Client.
Hostname/Address
Set to the FQDN or IP address of the SecureAuth Identity Platform / RADIUS Server
Authentication port / Accounting port
Default ports are 1812 / 1813 respectively, but this can be changed in the SecureAuth RADIUS configuration.
Note: Set the Accounting port to 0 (zero) if not using accounting.
Firewall
If changing ports for the RADIUS server, be sure to check the local firewalls of both the Identity Platform appliance and the VMware Horizon connection server, as well as any firewall between these endpoints.
Authentication type
Must be set to PAP. At this time, the SecureAuth RADIUS Server only supports PAP.
Shared secret
This value must match the one defined in the SecureAuth RADIUS configuration.
Server timeout
Set the value in seconds before the VMware Horizon connection server times out the RADIUS request.
Recommended value is 30 seconds.
Max retries
Number of tries the VMware Horizon connection server will retry after a timeout.
Recommended value is 3 retries.
Realm prefix
Leave blank. Not used in the SecureAuth implementation.
Realm suffix
Leave blank. Not used in the SecureAuth implementation.
If there is a secondary RADIUS server, complete the settings for the secondary server.
If you have replica Connection Servers, they can also be set up for RADIUS authentication and reuse an existing RADIUS authenticator configuration.
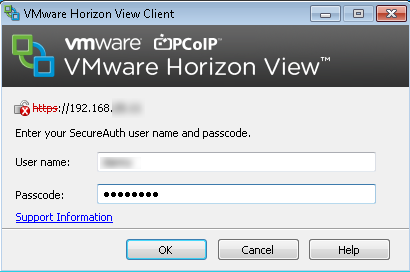
Horizon View Client for Windows
Test the connection from any Horizon View Client.
Where possible, use Horizon View Client for Windows 5.1 or later. Older Horizon View Clients still work, but will refer to RSA SecurID in text prompts.
Horizon View Clients with RADIUS support show the appropriate token label in text prompts, which is the label configured in Horizon View Client for this authenticator.
 |
Tips and warnings
- Access challenge prompt
After authenticating to SecureAuth RADIUS, you might get another prompt if the RADIUS server responds with a supported access challenge. Full generic RADIUS challenge and response is not supported, it supports a limited access challenge for a string token code.
- Username and password matching
In the Advanced Authentication section, if the Enforce 2-factor and Windows user name matching check box is selected, then after RADIUS authentication, the Windows login prompt will force you to use the same username as the RADIUS username. You cannot modify this username. This is the same feature used with RSA SecureID authentication.
With the RADIUS authentication using the same Windows username and password, you will not be prompted for Windows credentials.
This feature occurs in cases where the initial RADIUS authentication uses Windows authentication. This triggers an out-of-band transmission of a token code used as part of a RADIUS challenge. In this case, you do not need to reenter your Windows username and password after RADIUS authentication.
This feature does not work in Horizon View Client earlier than version 5.1.
- RADIUS accounting requests
To turn off sending RADIUS accounting requests from Horizon View Client, set Accounting port to 0.
If the RADIUS server does not support accounting requests, it most likely ignores them, resulting in authentication delays while retrying these accounting requests. Set the Accounting port a non-zero value only if the RADIUS server supports accounting requests.
- Connection delay
Once you establish a connection in the Horizon View Client, and it takes 4 to 5 minutes to establish a connection, check the RADIUS server log. If the RADIUS server log shows a match in the connection time with the Horizon View Client, then the client is waiting for a time out.
To resolve the delay, open the connection server and change the accounting request to 0 (zero).
- Connection server configuration updates
In Horizon View Client 7.13, each time you make an adjustment to the connection server configuration, it requires you to retype the shared secret.
Otherwise, if you do not retype the shared secret, there will be a mismatch between the RADIUS server and the Horizon connection server.
- Realm prefix / Realm suffix
If the authenticator has a specified Realm prefix string, it sends this in the beginning of the username to the RADIUS server.
For example, in the Horizon View Client, the username is jdoe with a Realm prefix of DOMAIN-A\. Then, it sends the username of DOMAIN-A\joe to the RADIUS server.
Also, if there is a specified Realm suffix string like @mycompany.com, then it sends the username of jdoe@mycompany.com to the RADIUS server.