Optional configurations in SecureAuth RADIUS
The following are optional configurations you can make to customize the SecureAuth RADIUS Server.
Use HTTPS in RADIUS admin console
You can configure the RADIUS admin console to use HTTPS instead of HTTP.
Before you begin, make sure you have the following:
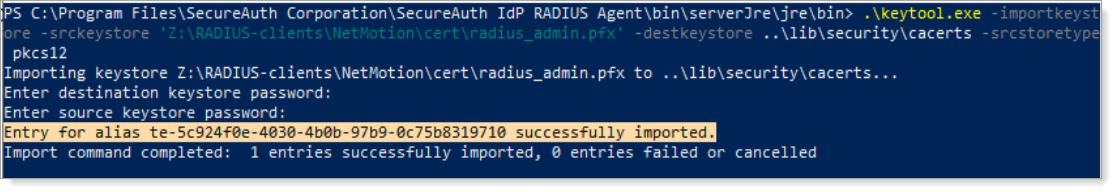
SSL certificate via PKCS12 file (PFX_FILE). This can be a self-signed certificate.
RADIUS Server installed.
To configure the RADIUS admin console for HTTPS, follow these two short procedures.
SecureAuth RADIUS properties
The following are configuration properties available in SecureAuth RADIUS. These properties are in the appliance.radius.properties file.
To modify a property do the following:
In a text editor, open the
appliance.radius.propertiesfile.This file is located in the conf folder. For example: C:\Program Files\SecureAuth Corporation\SecureAuth IdP RADIUS Agent\bin\conf
Find the property you want to add or modify. See List of SecureAuth RADIUS properties.
Save your changes.
List of SecureAuth RADIUS properties
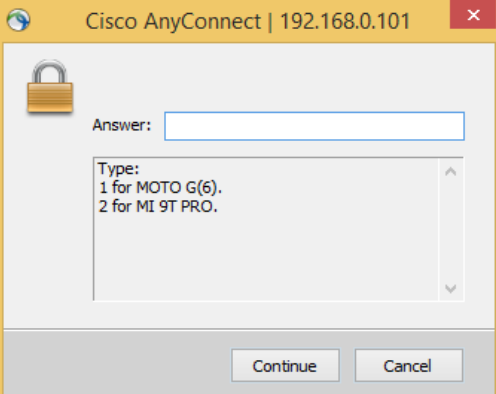
- Display multiple authentication devices
Allow end users to select their authentication device if they have more than one device.
Property:
radius.oath.strategy=ask_by_otp_deviceEnd user experience: When an end user who has multiple devices authenticate, the following screen appears:
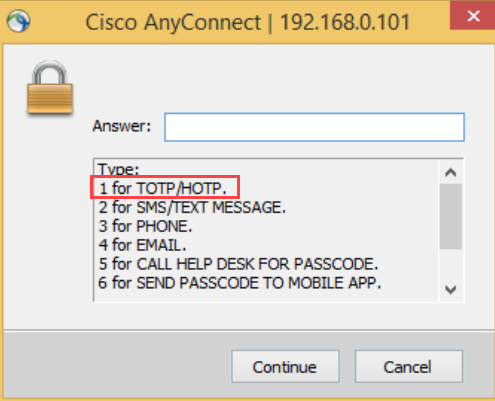
The SecureAuth RADIUS server supports two types of authentication: HMAC-based one-time password (HOTP) and time-based one-time password (TOTP) in seed and token modes. As a result, the authentication type displayed is TOTP/HOTP instead of OTP.
- Maximize login requests with timeout value
Set a timeout value to maximize successful login requests to the SecureAuth Identity Platform.
Property:
idp.api.timeout=n(wherenis the timeout value in milliseconds)For example,
idp.api.timeout=50000Default: 50000
- Number of UDP processor threads
SecureAuth RADIUS can use a set number of User Datagram Protocol (UDP) processor threads to get access-request packets.
Property:
radius.processorThreads=n(wherenis the number of processor threads)For example,
radius.processorThreads=50Default: 50 (maximum value is 1000)
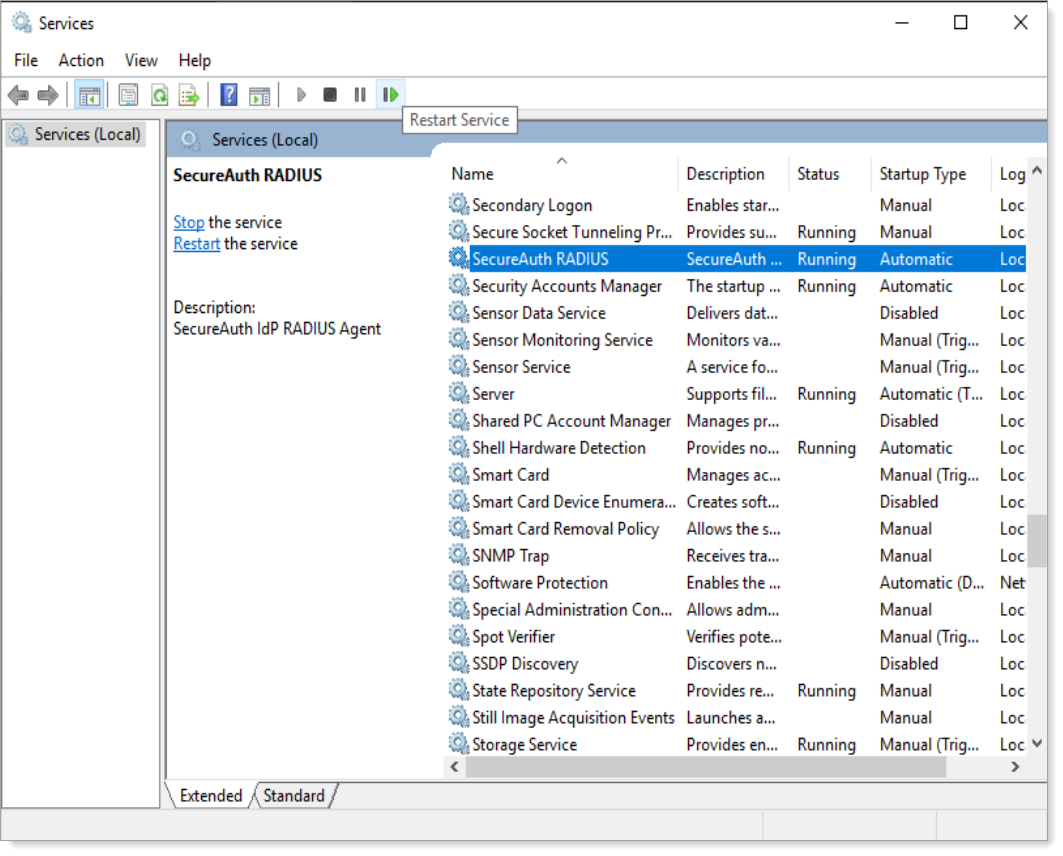
Save your changes to the
appliance.radius.propertiesfile.Open the Task Manager and select the Services tab.
Right-click secureAuthRadius and click Restart.
When you lose connection, cancel out of the reconnect dialog.
Select the Services tab and copy the PID for the
java.exeprocess.Open PowerShell as an Administrator.
Append the PID for the
java.exeprocess tojconsole.exeand run the command.jconsole.exe <PID>
For example:
jconsole.exe 4648
- PIN length for PIN + OTP authentication
Set the PIN length for your end users for the PIN + OTP authentication workflow.
Property:
pin.length=n(wherenis the PIN length)For example,
pin.length=8Default: 4 (maximum value is 18)
- Preferred MFA
Enable Preferred Auto-Submit method set by an Admin in a policy. To learn more about this setting in the Identity Platform, see Automatically submit preferred MFA method.
Property:
enable.preferred.mfa=true/falseDefault: false
When set to false, it shows enabled MFA methods to the end user during the login workflow. User must choose their preferred MFA method each time.
When set to true, the admin chooses the preferred auto-submit MFA method for their end users. The MFA list will display other enabled MFA methods to choose from.
- Push-to-accept (P2A) notification configuration
This property controls how to handle pending P2A notifications.
For example, the user initiates the authentication process. It sends a notification message to the user "A notification is in progress. Accept it. If you do not have a notification, it might be lost. Discard it. (You must request a new one.) Discard? (Y|N)"
Property:
offer_discard_current_push_authentication_request=true/falseDefault: false
When set to false, it will prompt the user to discard the P2A before sending a new one.
When set to true, it will not prompt the user to discard the P2A and send a new one every time.
- Single-factor authentication auto-submit method
For single-factor authentication, you can enable or disable the auto-submit method for RADIUS.
Property:
auto.submit.if.single.available=true/falseDefault: true
- Special character support in user IDs
Support for special characters in the user ID like @ ' " `. Especially if the username is an email address.
If you use SecureAuth IdP 9.2, you need to turn off special character support. If you don't, users with special characters in their IDs won't be able to log in.
Property:
enable.special.characters.for.userid=true/falseDefault: false
- UPNSuffix conversion
Enable or disable the username conversion from domain\username to username@domain.
For example, if the User-Name attribute is in the domain/username or domain\username format, it converts to username@domain format.
Property:
enable.username.upnsuffix.conversion=true/falseDefault: true