SecureAuth cloud services
Applies to Identity Platform releases 23.07 and earlier
The SecureAuth® Identity Platform, end user browsers, and registered mobile devices connect with the SecureAuth cloud services to provide multi-factor authentication capabilities
Allowed URLs and IP addresses
This topic contains the allowed URLs and IP addresses you'll need when configuring the Identity Platform, servers, and devices.
Refer to the section appropriate for your product release for the list of allowed URLs and IP addresses.
You can also download the complete list of URLs and IP addresses: sa-idp-allowlist.json
The domain name system (DNS) resolution for the geo load balanced URLs returns one of the listed IP addresses, depending on the geographic location of the DNS resolver (client). To support SecureAuth cloud services site failover, allow all IP addresses for the URL in the firewall rules.
The domain name system (DNS) resolution for the Geo load balanced URLs returns one of the listed IP addresses. This depends on the geographic location of the DNS resolver (client). To support SecureAuth cloud services site failover, you'll need to allow all IP addresses for the URL in the firewall rules.
us-certs.secureauth.com / nge-cloud.secureauth.com
Purpose: Used for SHA-2 RSA (384) certificate services
IP Addresses:
75.2.72.232 99.83.164.204
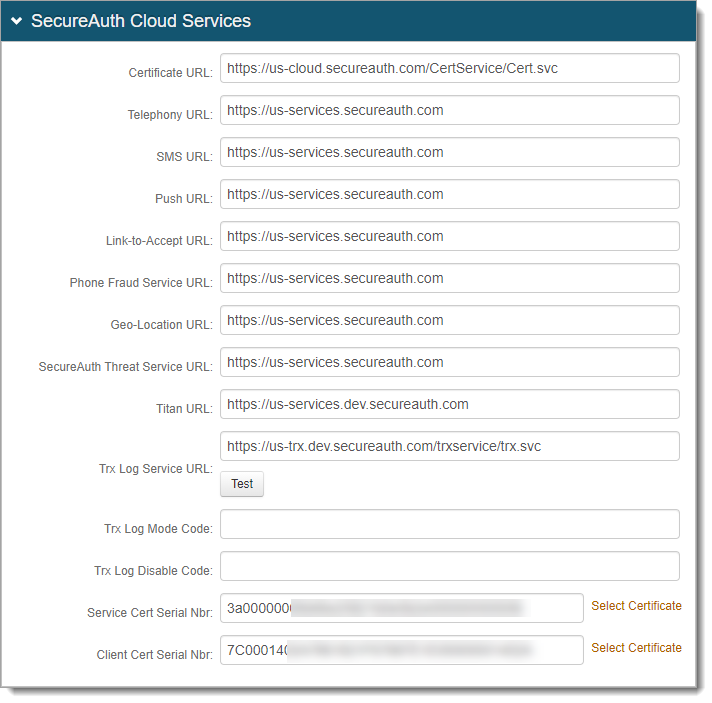
us-services.secureauth.com
Purpose: Used for cloud services in the System Info tab:
Telephony URL – Telephony Service (text-to-speech) to deliver one-time passcodes by voice call to user's phone number.
SMS URL – SMS Service to deliver one-time passcodes by SMS / text message to user's mobile phone number.
Push URL – Push Service to deliver one-time one-time passcodes in any of the following ways:
Push Notification to user's mobile device
Deliver mobile login requests (Accept / Deny) via SecureAuth Authenticate App to user's mobile device
Link-to-Accept URL – Link-to-Accept to deliver SMS text messages to user's mobile device. The link in emails and SMS text messages point to SecureAuth cloud.
Phone Fraud Service URL – Phone Number Fraud Prevention Service to retrieve user's phone number profile to use in phone number blocking.
Geo-Location URL – Geo-location Service to retrieve IP address geo-location (known as Dynamic Perimeter) information to use in Adaptive Authentication analysis.
SecureAuth Threat Service – SecureAuth Threat Service to retrieve IP address reputation / threat score to use in Adaptive Authentication analysis.
Alternatively, you can view the IP addresses listed in the Amazon EC2 service table. Take note that it lists all AWS IP addresses, and you only want to allow the IPs within EC2, us-east-1, and us-west-2 categories: ip-ranges.amazonaws.com/ip-ranges.json
us-audit.secureauth.com
Purpose: Used by SecureAuth servers to receive customer logs for dashboard services and user risk services.
IP Addresses:
us-trx.secureauth.com
Purpose: Used to deliver transaction operation communications to the SecureAuth cloud environment:
Trx Log Service URL – Transaction log service to deliver transaction operation communications to the SecureAuth cloud environment.
Trx Log Mode Code – Transaction log mode code automatically assigned to the instance during the build process to indicate whether the logging mode is transaction or user based.
Trx Log Disable Code – Transaction Log disable code provided by SecureAuth Support to temporarily disable transaction web service calls.
IP Addresses:
75.2.50.208 99.83.150.226
us-polaris.secureauth.com
Purpose: Used for New Experience Web Admin interface assets
IP Addresses:
15.197.205.255 3.33.245.231
sparkles-content.prod.secureauth.com
Purpose: New Experience Web Admin user interface assets and storage configuration.
IP Addresses:
To view the page of listed IP addresses, see CloudFront IP list
your-tenant-name.secureauth.com
Purpose: IDP services main endpoint (Cloudflare-protected tenant endpoints).
IPv4 Addresses:
173.245.48.0/20 103.21.244.0/22 103.22.200.0/22 103.31.4.0/22 141.101.64.0/18 108.162.192.0/18 190.93.240.0/20 188.114.96.0/20 197.234.240.0/22 198.41.128.0/17 162.158.0.0/15 104.16.0.0/13 104.24.0.0/14 172.64.0.0/13 131.0.72.0/22
IPv6 Addresses:
2400:cb00::/32 2606:4700::/32 2803:f800::/32 2405:b500::/32 2405:8100::/32 2a06:98c0::/29 2c0f:f248::/32
For the latest Cloudflare IP ranges, refer to:
Example of SecureAuth cloud services settings for 19.07 and later
 |
Important
Important information about MSG level encryption
The msg level encryption endpoints are deprecated (no longer appending /msg after .svc in the URL). Going forward, use https in the URL configuration.
The domain name system (DNS) resolution for the Geo load balanced URLs returns one of the listed IP addresses. This depends on the geographic location of the DNS resolver (client). To support SecureAuth cloud services site failover, you'll need to allow all IP addresses for the URL in the firewall rules.
us-certs.secureauth.com / nge-cloud.secureauth.com
Purpose: Used for SHA-2 RSA (384) certificate services
IP Addresses:
75.2.72.232 99.83.164.204
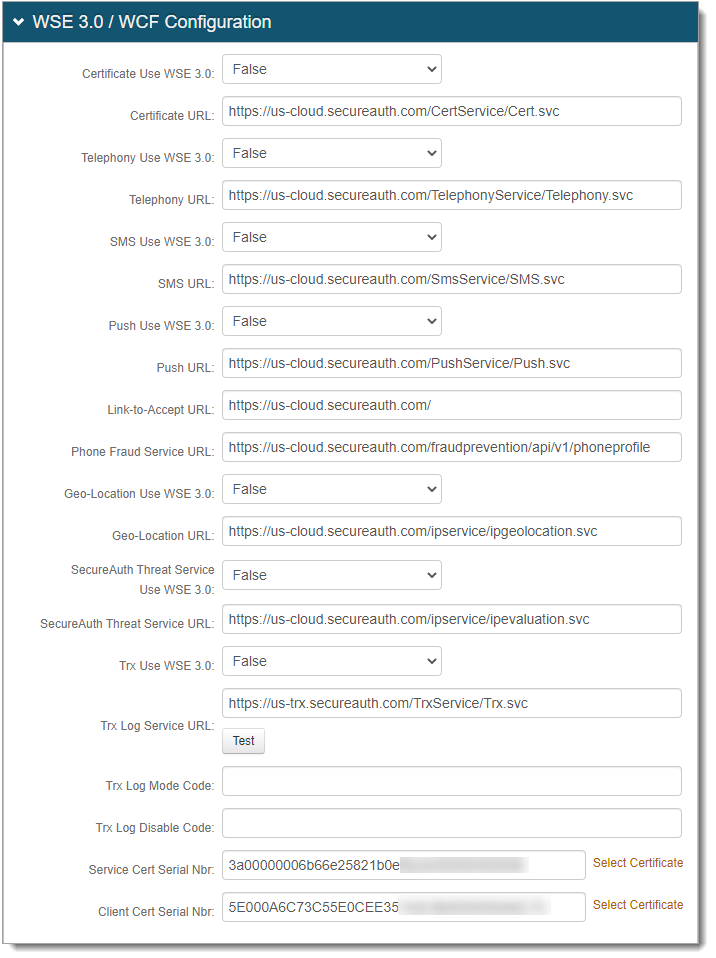
us-cloud.secureauth.com
Purpose: Used for cloud services for SecureAuth IdP 9.3 or earlier:
Telephony URL – Telephony Service (text-to-speech) to deliver one-time passcodes by voice call to user's phone number.
SMS URL – SMS Service to deliver one-time passcodes by SMS / text message to user's mobile phone number.
Push URL – Push Service to deliver one-time one-time passcodes in any of the following ways:
Push Notification to user's mobile device
Deliver mobile login requests (Accept / Deny) via SecureAuth Authenticate App to user's mobile device
Link-to-Accept URL – Link-to-Accept to deliver SMS text messages to user's mobile device. The link in emails and SMS text messages point to SecureAuth cloud.
Phone Fraud Service URL – Phone Number Fraud Prevention Service to retrieve user's phone number profile to use in phone number blocking.
Geo-Location URL – Geo-location Service to retrieve IP address geo-location (known as Dynamic Perimeter) information to use in Adaptive Authentication analysis.
SecureAuth Threat Service – SecureAuth Threat Service to retrieve IP address reputation / threat score to use in Adaptive Authentication analysis.
IP Addresses:
75.2.72.232 99.83.164.204
us-trx.secureauth.com
Purpose: Used to deliver transaction operation communications to the SecureAuth cloud environment:
Trx Log Service URL – Transaction log service to deliver transaction operation communications to the SecureAuth cloud environment.
Trx Log Mode Code – Transaction log mode code automatically assigned to the instance during the build process to indicate whether the logging mode is transaction or user based.
Trx Log Disable Code – Transaction Log disable code provided by SecureAuth Support to temporarily disable transaction web service calls.
IP Addresses:
75.2.50.208 99.83.150.226
Example of SecureAuth cloud services settings for 9.3 and earlier
 |
Important
Important information about MSG level encryption
The msg level encryption endpoints are deprecated (no longer appending /msg after .svc in the URL). Going forward, use https in the URL configuration.
Test the Identity Platform endpoint availability
To verify that these endpoints are available from the Identity Platform instance, browse (from the instance) to the following URLs:
Instrafructure details
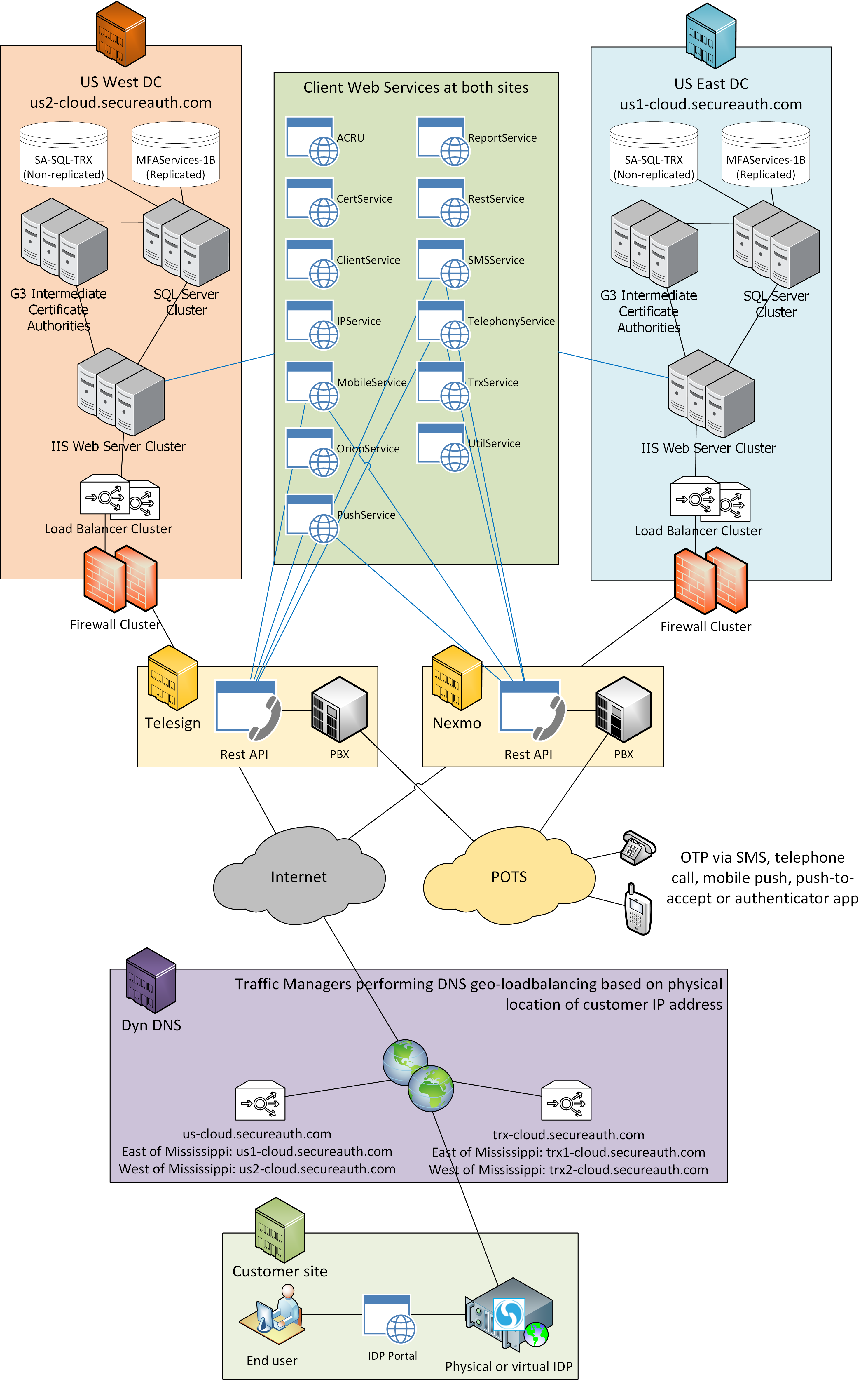
SecureAuth cloud services are hosted in two geographically separated, SSAE16 Type II certified data centers: US-East and US-West. Both facilities provide redundant infrastructure at the site and service levels, including power, cooling, network, and internet connectivity, to ensure high availability.
An industry-leading, cloud-based geo-location load balancing solution routes Identity Platform and SecureAuth cloud access communications to the most efficient facility. In the event of a site-level outage, all communications are seamlessly transferred to the backup facility.
Each SecureAuth data center includes:
Load-balanced web service APIs for SMS, TTS, Push, Push-to-Accept OTP, Threat Intelligence, and X.509 certificate signing services
Redundant hardware security module (HSM) protected certificate authorities
Clustered (failover) database services
Redundant backend services (LDAP Directory, DNS, Firewall, IDS/IDP, content inspection, etc.)
All communications between the Identity Platform, SecureAuth cloud access, and SecureAuth cloud services are secured via TLS/HTTPS over TCP Port 443
 |
Transport Layer Security
Transport Layer Security (TLS), a cryptographic protocol, is designed to provide communications security over a network. Using X.509 certificates, asymmetric cryptography is employed to verify the relationship between a certificate and its owner, and to negotiate a symmetric session key.
SecureAuth cloud services
The Identity Platform instance and cloud access portals communicate with SecureAuth cloud for the following services:
Service | Purpose |
|---|---|
X.509 Certificate Services (SHA 1 and SHA 2) | Issue user certificates. |
Telephony Service (text-to-speech) | Deliver OTPs via voice call to user's phone number. |
SMS Service | Deliver one-time passcodes (OTPs) via SMS / text message to user's mobile phone number. |
Push Service | Deliver OTPs via Push Notification to user's mobile device and / or deliver mobile login requests (Approve / Deny) via SecureAuth Authenticate App to user's mobile device. |
Link-to-Accept | Deliver SMS text messages to user's mobile device. The link in emails and SMS text messages point to SecureAuth cloud. |
Phone Number Fraud Prevention Service | Retrieve user's phone number profile to use in phone number blocking. |
Geo-location Service | Retrieve IP address geo-location (known as Dynamic Perimeter) information to use in Adaptive Authentication analysis. |
SecureAuth Threat Service | Retrieve IP address reputation / threat score to use in Adaptive Authentication analysis. |
App Enrollment Service | Generate QR code to use in Multi-Factor App Enrollment (SecureAuth Authenticate App). |
SecureAuth Authenticate App v5.3+
URLs supported for push notifications and device enrollment QR codes
A complete callback URL is included in the API payload for device enrollment QR codes and Push-to-Accept Notifications. When responding to either a QR code device enrollment request or Push-to-Accept request, the SecureAuth Authenticate App returns the URL with a DNS prefix such as us1-.
Example callback URL:
"https://us1-cloud.secureauth.com/mobileservice/api/v1/pushaccept"