Overview
SessionGuardian provides security solutions that help organizations ensure only authorized users can access and view data in protected applications, devices, or environments. It also prevents end-users from copying, downloading, taking screenshots, or photographing sensitive data within these secure systems.
Continuous identity assurance
 |
SessionGuardian ensures that only the authorized user can view and access protected data such as:
Windows devices with SessionGuardian Desktop
VDI environments with SessionGuardian VDI
Web applications with SessionGuardian Web
iOS devices with SessionGuardian Mobile
Continuous identity assurance provides the following benefits:
Continuous facial authentication
User presence and liveness detection
Prevention of shoulder surfing
ID verification and validation
Continuous data protection
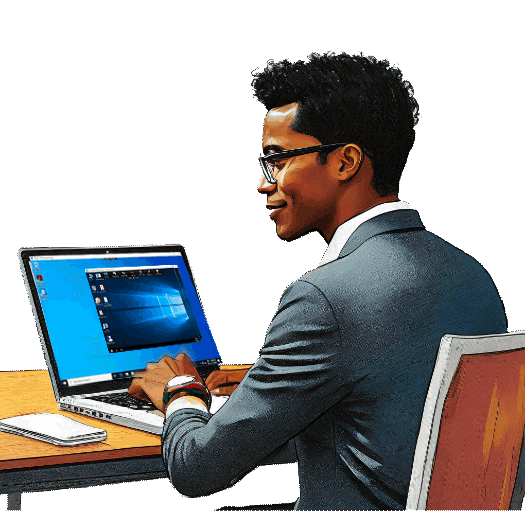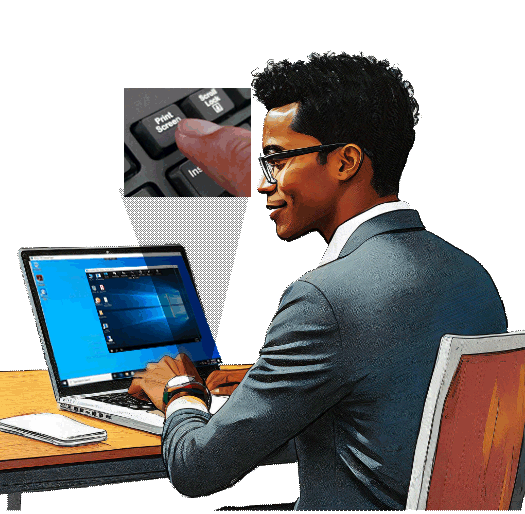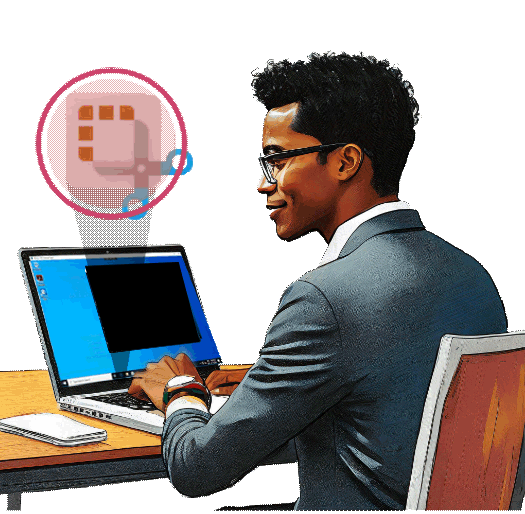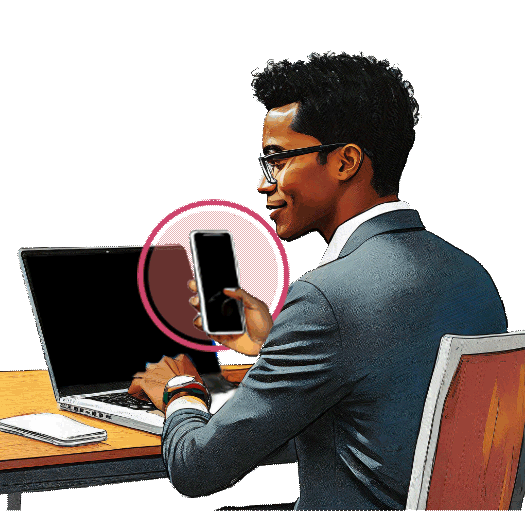 |
SessionGuardian prevents screenshare, screen capture, screen print, and use of mobile phones to take photo of screen when data is accessed through:
SessionGuardian VDI
SessionGuardian Web
SessionGuardian Desktop
SessionGuardian Mobile
SessionGuardian blocks copy/paste and file download attempts through:
SessionGuardian VDI
SessionGuardian Web
SessionGuardian Mobile
Continuous data protection provides the following benefits:
Prevents screenshare, screen capture, and screen print activities
Stops attempts to copy data and download files from secure systems and applications
Detects the use of mobile phones and cameras attempting to photograph the screen
Activates watermarks across all screens during secure sessions
Device and network posture verification
SessionGuardian actively checks that the device is healthy, secure, connecting from a safe network, and accessing at the correct location and time of day.
 |
Continuous device and network posture verification provides the following benefits:
Ensures device security
Limits access to known and approved networks (enforces IP/VPN restrictions)
Allows for geolocation approval/denial
Verifies that required/restricted applications are running
Regulates access based on approved time of day and day of the week