Add Microsoft Entra ID data store
In the SecureAuth® Identity Platform, you can add an Microsoft Entra ID (formerly Azure AD) data store to assert or manage user identity information. This requires registering the Identity Platform in Microsoft Entra admin center to communicate with Microsoft Entra ID.
Note
The SecureAuth Connector is not required for Microsoft Entra ID data store in the Identity Platform.
Prerequisites
Identity Platform release 24.04, cloud or hybrid deployment
Identity Platform is registered in Microsoft Entra admin center with application read/write permissions to Microsoft Entra ID. For more information, see Microsoft Entra ID configuration. You will need to capture the connection IDs and client secret key from the Microsoft Entra admin center.
Data store limitations
Note the following issues with Microsoft Entra ID data stores:
Login workflows that include a password is not supported for guest accounts on Microsoft Entra ID. Use passwordless login workflow.
The username and password login workflow is not compatible with conditional access and MFA. For more information, see this Microsoft article.
You can only use Microsoft Entra ID in applications created in the New Experience.
Password complexity rules set up in the Identity Platform cannot be applied to Microsoft Entra ID.
Process
There are two parts to adding a data store in the Identity Platform — (1) adding the data store and (2) mapping the data store properties.
Step 1 of 2: Add Microsoft Entra ID data store
The first part of adding an Microsoft Entra ID data store is configuring the data store name, connections, credentials, and search attributes.
On the left side of the Identity Platform page, select Data Stores.
Select the Data Stores tab.
Click Add a Data Store.
Set the Data Store Name and select the Connection Type as Microsoft Entra ID.
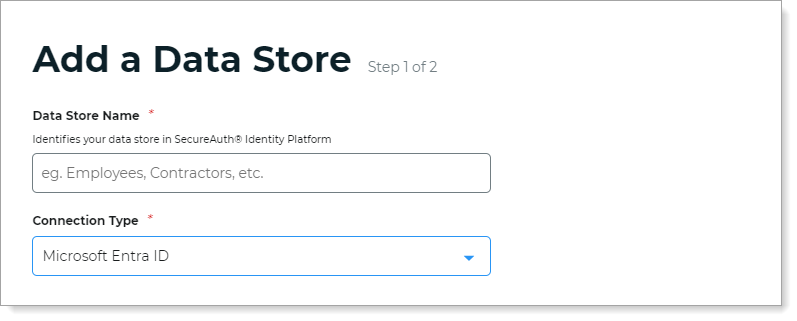
In the Connection Settings section, enter the connection information for your configured Microsoft Entra ID data store.
Note
For information about how to get the connection settings for Microsoft Entra ID, see Microsoft Entra ID configuration.
Azure Tenant Domain
The domain of the Microsoft Entra ID (formerly Azure AD) directory.
For example, company.onmicrosoft.com
Directory Tenant ID
The Directory (tenant) ID value copied from the Microsoft Entra admin center for the registered Identity Platform application.
Client ID
The Application (client) ID value copied from the Microsoft Entra admin center for the registered Identity Platform application.
Client Secret
The client secret copied from the Microsoft Entra admin center for the registered Identity Platform application.
Use National Cloud Deployment
Select check box and set to the regional instance for your Microsoft Entra ID data store. Options are:
Public (default)
China
Germany
US Government
Test Credentials
Test the data store connection by clicking Test Credentials.
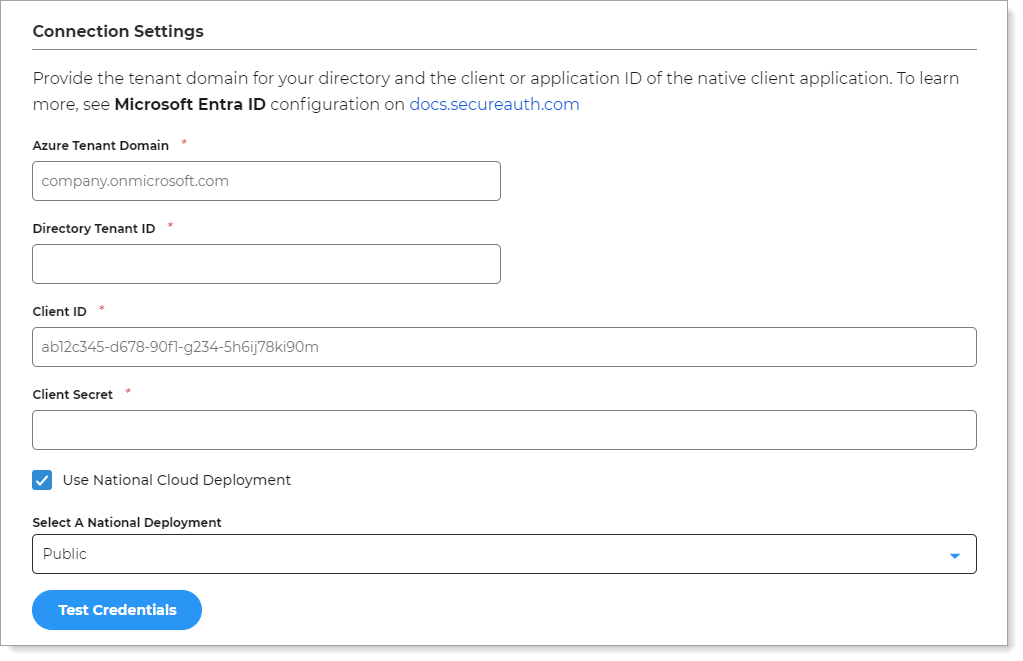
In the SecureAuth IWA Service Settings section, define the settings to use Windows SSO for your resources.
Note
This option is available only in cloud deployments.
For more information about Windows SSO integration, see Windows SSO integration with Microsoft Entra ID.
Allow Windows SSO integration
You can use Windows SSO to allow secure access to your resources. Move the slider:
On – Allow Windows SSO integration.
The Identity Platform connects with the SecureAuth IWA service to validate user credentials and allow Windows SSO access to resources.
Off – Do not allow Windows SSO integration.
The Identity Platform uses the authentication policy login workflow to allow access to resources.
Microsoft Entra Domain Services (AADDS) Domain
The Microsoft Entra domain for this service account.
Service Account Password
Password for the SPN-assigned service account in Microsoft Entra Domain Services.
Note
If the password changes for this SPN-assigned service account in Microsoft Entra Domain Services, you must update the password in this field.
The password must be in sync in both places to maintain a Windows SSO connection between the Microsoft Entra Domain Services and SecureAuth IWA service.
Service Account Name
Name of the service account in Microsoft Entra Domain Services used to establish a connection with the SecureAuth IWA service.
The service account must have an assigned Service Provider Name (SPN). For more information, see Configure Microsoft Entra Domain Services for SecureAuth IWA service.
It is recommended to use a service account with least privilege access for Windows SSO and SecureAuth IWA service.
This optional field is not validated in the Identity Platform. Use this field to help you remember the name of the service account used for the Windows SSO integration with the Identity Platform.
Click Continue.
The Map Data Store Properties page opens.
Step 2 of 2: Map the Microsoft Entra ID data store properties
The second part of adding an Microsoft Entra ID data store is mapping the data store properties.
Each user is uniquely identified by profile data that is read from or stored in your directories and databases.
The Identity Platform does not store user profiles, so your Microsoft Entra ID attributes must be mapped to the Identity Platform profile properties to be read and updated in the directory by the Identity Platform. The Microsoft Entra ID attribute mapped to the property is retrieved only when required for authentication or assertion purposes.
For more information about how data store profile properties are stored for on-premises, hybrid, or cloud Identity Platform deployments, see List of stored profile field properties.
Note
Each mapped profile property needs to have its own directory attribute. You cannot map the same directory attribute to more than one property.
For example, you cannot map the mobilePhone attribute in Phone 3 because that attribute is already mapped to Phone 2.
Refer to the following table about attribute mapping and other information.
Column | Description |
|---|---|
Name and Directory Field | Map the following required Directory field attributes:
Map the following recommended Directory field attributes:
|
Data Format | For mapped profile properties (for example, Push Notification Tokens, Behavioral Biometrics, and Device Profiles), specify the Data Format to define how data is encrypted and stored in the directory. For cloud deployments, certain profile properties (for example, Push Notification Tokens, Behavioral Biometrics, and Device Profiles) are generated and used by SecureAuth, and stored in the SecureAuth cloud database. Selection options listed below may vary depending on your Identity Platform deployment:
|
Writable | Define whether a profile property can be writable (select check box) or not writable (cleared check box) according to your Active Directory configuration. For example, if you want to allow users to update their personal email address on the self-services page, select the Writable check box. Some profile properties are disabled by default in the system; for example, biometric profile properties used by SecureAuth cloud services. |
Use Cloud Storage Available only in cloud deployments. | Store values in Aux IDs to the cloud profile database. When you select this check box, enter a description about the purpose of the Aux ID. To learn more, see How to set up Aux ID for cloud storage. |