Release Updates
Product updates to SecureAuth® Identity Platform release 24.04.
For a complete list of fixes and known issues, see Enhancements and fixes, and Known issues.
Release date: January 9, 2026
Updates
Air-gapped deployment for SecureAuth IdP
Air-gapped SecureAuth IdP deployments running releases 9.2 through 20.06 can now upgrade to version 24.5.0, accessing years of security enhancements and features while maintaining strict network isolation. This release enables ongoing upgrades to future SecureAuth IdP versions without cloud connectivity requirements.
To understand the architecture and prepare for your deployment,complete installation and configuration guidance, see Air-gapped deployment overview.
FIDO2/Passkey support – Stop credential attacks even in isolated networks. Add phishing-resistant MFA for each application using built-in OS authenticators like Windows Hello and Touch ID
Help desk verification – Verify identities before account changes. Stop social-engineering account resets where attackers target help desks to reset passwords.
YubiKey HOTP – Enable users to enroll their own hardware tokens. HOTP is stronger than many soft tokens and works offline.
Latest SecureAuth IdP version support – Upgrade to version 24.5.0 and future releases without cloud connectivity requirements.
Windows Server 2022 support – Deploy on current operating systems with the latest security patches and compliance requirements. Windows Server 2025 support in pipeline.
Offline TOTP enhancements – Enable secure MFA when systems cannot reach the internet. Configure individual TOTP settings overrides that work with SecureAuth Authenticate App, Desktop App, and standard TOTP apps.
Password throttling enhancements – Block brute-force password attacks without connectivity.
Enhanced security – Reduce admin overhead while reinforcing air-gapped safeguards.
Government agencies and defense contractors requiring strict network isolation
Financial institutions with air-gapped production environments
Healthcare organizations managing sensitive patient systems
Any organization with regulatory requirements preventing cloud connectivity
Windows Server 2022 or later
SecureAuth IdP release 24.5.0 or later
Network isolation without internet connectivity
Next steps:
For architecture details and planning requirements, review Air-gapped deployment overview
Contact SecureAuth Support to request the air-gapped deployment package and schedule implementation
Release date: October 3, 2025
Updates
- Enhanced Transparent SSO with continuous authentication
Added logic to Transparent SSO on PostAuth pages to support continuous authentication. This ensures adaptive policies and group restrictions are re-evaluated after login, even when a user has a valid token.
With this enhancement, SecureAuth enforces adaptive rules such as IP risk score changes or group-based restrictions during session activity, not just at initial login. This closes a security gap where users could previously bypass restrictions with a valid cookie.
Benefits:
Applies Transparent SSO policies consistently throughout the session
Re-checks adaptive rules such as IP risk score changes
Prevents access to restricted applications even with a valid token
- Option to exclude password in SCIM payload
You can now use a new option in SCIM to exclude the user password from the payload sent to the SCIM provider. By default, the IdP includes the password field when creating users, as defined in RFC 7643 (SCIM Core Schema). If you select this option, the password is not sent during provisioning. Some SCIM providers require a password for account creation, so user creation may fail if you choose to exclude it.
Fixes
Fixed an issue in cloud deployments where the data store Test Credentials button sometimes returned a false negative, even when the data store connection was valid.
Fixed an issue where QR usernameless login with Push2Accept (biometric or push) sometimes returned an error message instead of completing successfully.
Fixed an issue that caused a timeout when logging into a realm configured with a SCIM server. The retry logic has been improved to prevent timeouts during connection attempts.
Release date: August 29, 2025
Updates
- API data store support
SecureAuth Workforce IdP now supports data stores through API access for authentication and profile data. This allows organizations using API-based authentication to upgrade without additional customization.
- LOA risk engine dashboard
Administrators can now view and analyze Level of Assurance (LOA) scores for users in a dedicated dashboard. This eliminates the need to search audit logs for individual user risk scores and provides clear visibility into how the Risk Engine evaluates authentication attempts.
To learn more, see SecureAuth Level of Assurance (LOA) Provider settings.
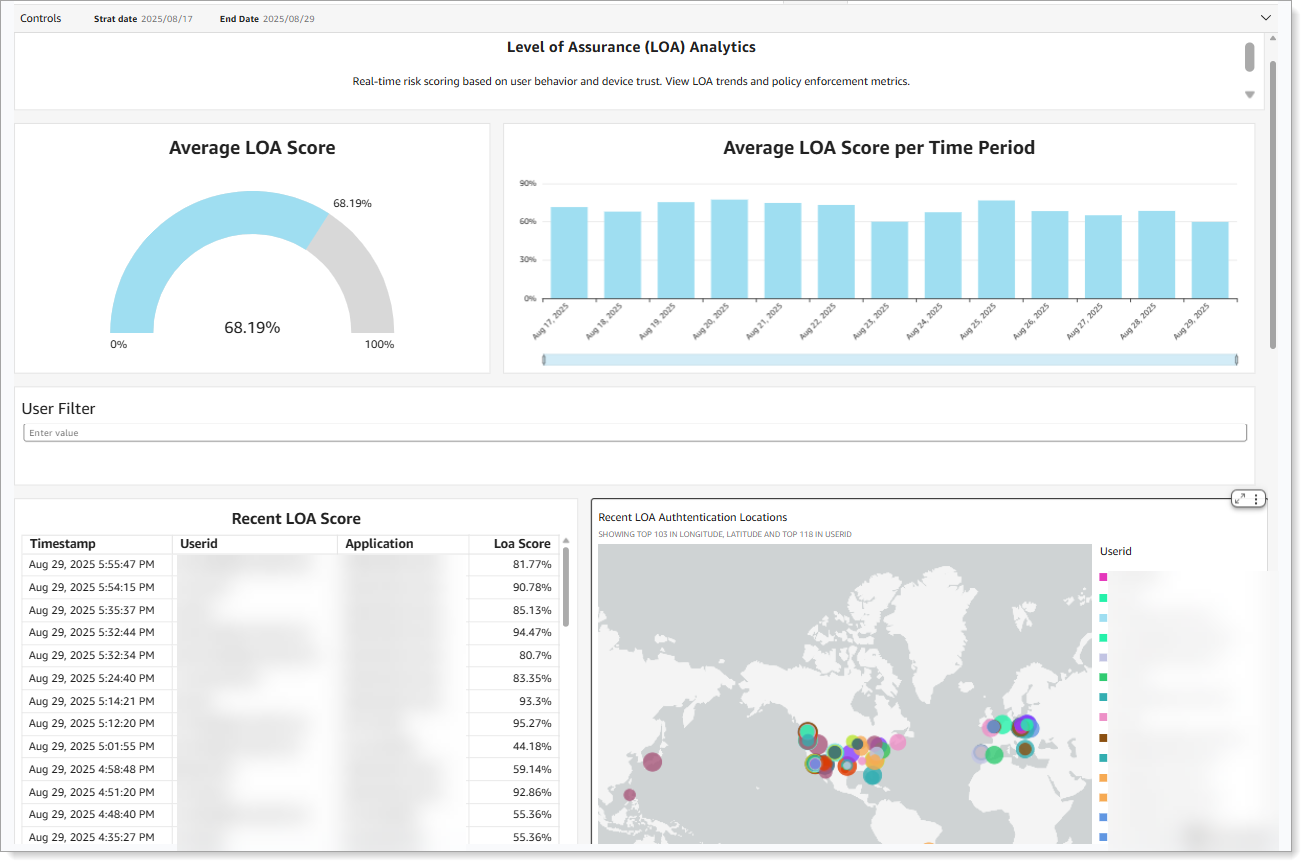
LOA dashboard with average scores, time-based trends, and authentication locations
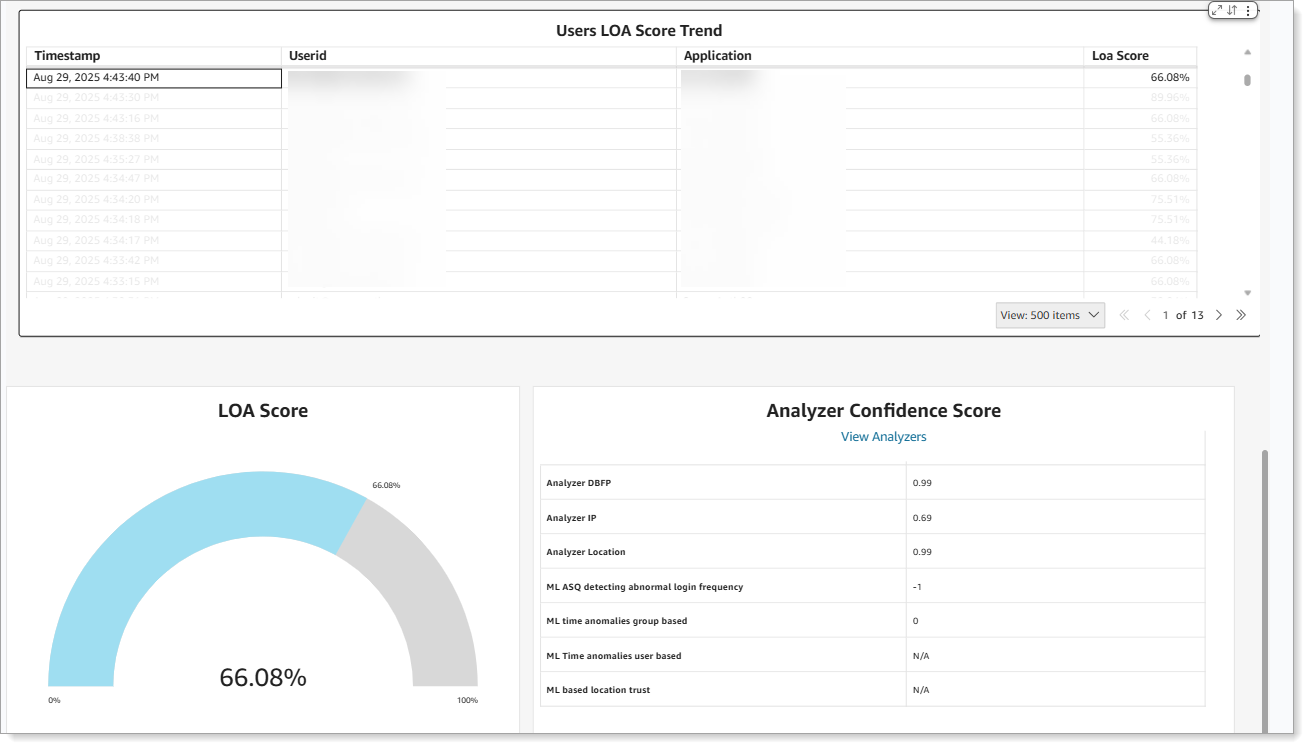
LOA score trend with analyzer confidence details.
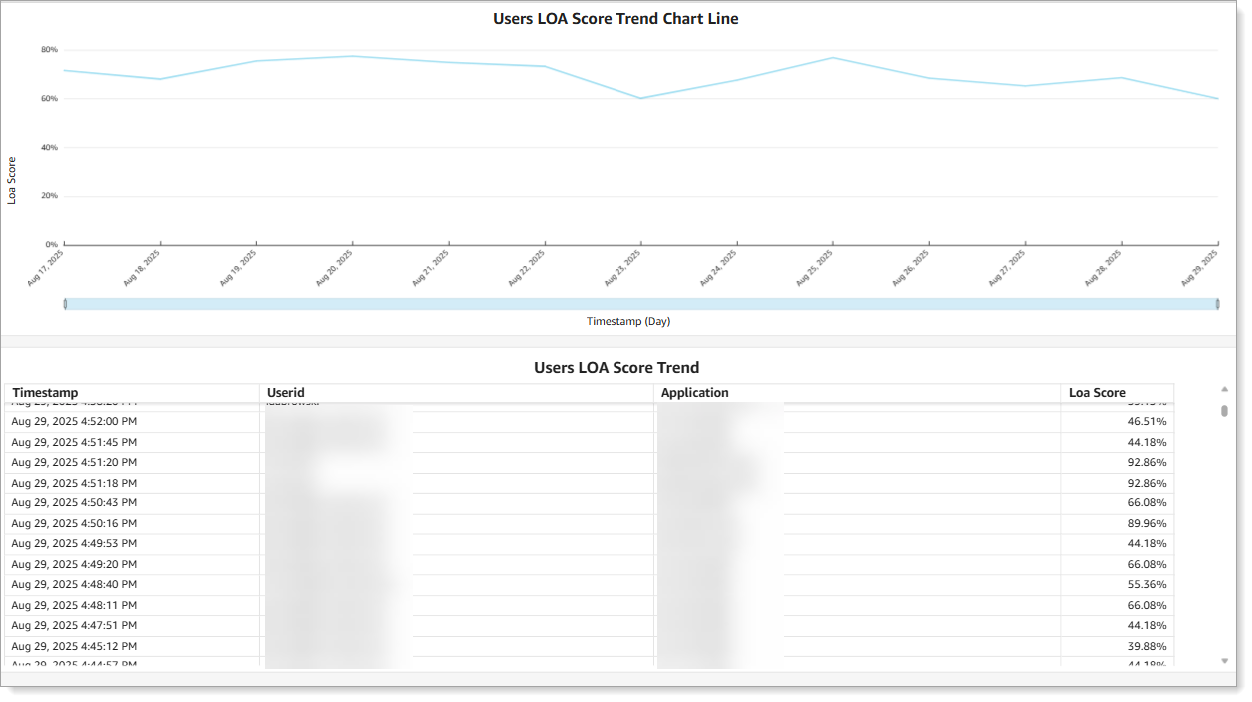
Line chart of LOA score trends with user score details
Fix
Resolved an issue where External Authentication Methods (EAM) did not work with certificate-based Windows authentication.
Release date: July 25, 2025
Updates
- Inline initialization now supports more MFA options
You can now set up additional MFA methods during login without leaving the authentication page. Users can register mobile Push/TOTP, FIDO2, Yubikey, and HID devices directly in the login flow when these methods are required but not yet enrolled
This makes it easier to onboard users and move them to stronger authentication methods without redirecting them to other pages.
- LOA risk engine dashboard (Coming soon)
Administrators can now view and analyze Level of Assurance (LOA) scores for users across their organization through a dedicated dashboard. This eliminates the need to manually search through audit logs to find individual user risk scores.
The dashboard helps administrators fine-tune their LOA rules to better balance security requirements with user experience by providing clear visibility into how the Risk Engine is scoring user authentication attempts
- Updated LOA confidence scoring to 0-100% scale
The Level of Assurance (LOA) confidence score now uses a 0-100 scale instead of the previous 0-4 range. This provides more granular scoring and clearer interpretation. You can customize the score ranges for each confidence level, for example:
Low confidence (0-39): Little certainty in identity verification, typically new users or unknown devices
Medium confidence (40-79): Moderate confidence level as users establish consistent login patterns
High confidence (80-100): Strong assurance in user identity based on established behavior patterns
Fixes
Fixed issue in Advanced Settings where Profile service account settings were incorrectly overwritten with Membership service account values in split profile configurations
Resolved AD-LDS authentication failures in New Experience that were incorrectly returning invalid password and unknown user errors
Resolved data store connection issue causing password reset failures that required app pool recycling to restore service
Windows SSO breaks enrollment realms
Added support for modern authentication methods for SMTP email connections to replace deprecated basic authentication
Resolved metadata inconsistencies across different download methods to ensure uniform SAML metadata generation
Security enhancements and fixes
Release date: March 31, 2025
Enhancements
- QR code-only login option
You can now configure the login experience to show only the QR code and hide the username field. This setting speeds up authentication and reduces phishing risks by using unique, session-based QR codes that expire after use.
Enable this option in the authentication policy on the Login Workflow tab to provide a faster, more secure login flow for your users.
- View access history for user profiles in the Dashboard
From the Dashboard > User Profile Data tab, admins can now click the number in the Access History column to view detailed login activity for each user. This includes timestamps and access records, making it easier to audit user behavior and investigate login patterns.
Available only in cloud deployments.
- Identity Pools | New Cloud Directory (Free Trial)
Identity Pools let you manage temporary or dynamic users without relying on enterprise data stores. Easily add, scale, or remove users—ideal for contractors or short-term access.
You can also create and manage groups within Identity Pools to organize users and streamline access control. Link Identity Pools to applications for seamless authentication.
To learn more, see Add an Identity Pool as an identity source
- Content and localization support for User Account page
You can now customize field labels and enable language support on the modernized User Account page.
Update labels such as User ID, First Name, Email, Phone, and Aux IDs to match your organization's terminology. You can also configure translations in supported languages like English, Spanish, French (Canadian), Japanese, and more.
To learn more, see Customize Content and Localization
- Risk Engine updates
This release includes performance and accuracy improvements to the Risk Engine, enhancing how LOA (Level of Assurance) scores are generated using a combination of rule-based analysis and machine learning.
You’ll also see a new Refresh LOA Configuration link in the LOA provider settings. Use this option only if instructed by SecureAuth Support. It re-syncs the LOA configuration with the Risk Engine and helps resolve backend configuration issues—such as after a tenant change—without requiring manual updates in webconfig.
This action does not affect LOA data or user authentication flows.
- Show or hide waiting page during authentication
You can now choose whether to show a waiting page during authentication with a toggle setting in the application configuration.
Fixes
Includes security enhancements, performance improvements, and bug fixes
Release date: January 22, 2025
Enhancements
- User Account page
The User Account page includes more features. You can seamlessly register and manage authentication devices, including enhanced phone and email verification methods, all in one page.
To learn more, see User Account page configuration.
Available in hybrid and cloud deployments.
- New Metadata Functionality
We have added new capabilities to manage metadata when integrating SAML applications. You can now:
Specify a global domain that applies to every SAML application
Import Service Provider metadata through URL
Export Identity Platform metadata as URL
Update Service Provider metadata by importing a new file
- Early Access: OIDC Support
Explore the new OpenID Connect and OAuth management features in the New Experience. Dive in, try it out, and provide your feedback to help shape the final release.
To learn more, see OIDC Manager
- Manage approved FIDO devices by AAGUID
Administrators can approve and manage FIDO Alliance-verified devices using their AAGUID. End users can view the approved devices on the FIDO enrollment page, as configured by their administrator..
To learn more, see FIDO2 WebAuthn global MFA settings
- Login for Windows improvements
Login for Windows updates include:
Configuration update. Admins can now enable the Ctrl+Alt+Delete password change option in the Login for Window endpoint. This allows users to update their password through the self-service password reset page or they must authenticate before they can change their password.
Improved user login experience. We've improved the login performance and standardized the Login for Windows interface for a seamless and consistent user experience across all flows. To learn more, see the demo videos in End user login experience on Windows.
- Regular Expression improvements
We have expanded the list of available regular expressions you can add to a password deny list. You can also add a custom expression.
- Help Desk update - Generate Password button
The Help Desk Password Reset page now includes a Generate Password button for creating a secure system-generated password.
- New SAML attributes
In the previous release, we expanded the list of available SAML attributes in Advanced Settings to include
Browser Session ID,Client IP Address, andAuthentication Method.In this release, these additional SAML attributes are supported within SAML integrations in the New Experience.
- Wildcard support for users and groups
You can now use wildcards for user and group names in policy settings:
Advanced Settings – Adaptive Authentication > User/Group Restriction
New Experience – Authentication Policies > Users and groups (as rules or conditions)
Examples:
adm*matches names starting with "adm"*mmatches names ending with "m"m*nmatches name starting with "m" and ending with "n"
- Custom Application URL field
In the New Experience, you can now create a unique URL alias for applications to simplify access and provide a user-friendly path for logins.
- Coming Soon: SecureAuth Risk Engine updates
Enhancing efficiency and accuracy of our integrated analyzers to analyze login patterns of users. It generates a Level of Assurance (LOA) confidence score for each user. The LOA score helps decide whether to increase or decrease user friction at the time of login.
Fixes
Fixed an issue where a data store could not be re-added to a Connector group after removal.
Known issue
You must update to RADIUS version 24.07.03 before upgrading to SecureAuth Identity Platform release 24.4.2 or later.
Release date: July 18, 2024
Enhancements
- User Account page
We've redesigned and renamed the Self-Service Account Update page to User Account. It's now part of the New Experience, where you can attach a modern theme and customize field visibility.
To learn more, see User Account page configuration.
Available only in hybrid deployments. Coming soon for cloud deployments.
- Microsoft Conditional Access
Support for external authentication methods (EAM) in Conditional Access with Microsoft Entra ID.
To learn more, see Microsoft Conditional Access External Authentication Method (EAM) integration guide.
- Localization support
Localization support for French-Canadian language.
- Theming configuration
Global theming configuration SSO Portal Themes is now Modern Themes, allowing theme creation for more Identity Management (IdM) pages with modern layouts.
- Session timeout improvements
For pages with the Modern Theme (SSO Portal and User Account), users now receive a session expired warning. They can choose to wait or the system will automatically restart the login process, ensuring a smoother experience.
- Profile field visibility
On the User Account page, profile fields set as "Visible (read-only)" will not display if the field is empty. This improves the user experience by reducing clutter and focusing on relevant information.
- New SAML attributes
We have expanded the list of available SAML attributes in Advanced Settings to include
Browser Session ID,Client IP Address, andAuthentication Method. These new attributes are also available in the Open ID Connect ID Token Claims configuration for a profile property mapping.In the upcoming release update, these additional SAML attributes will be available for SAML integrations in the New Experience.
- Run Windows SSO warning
Added a warning that an authentication policy can only have one "Run Windows SSO" conditional rule.
- New branding
We've updated the platform with our new branding while keeping the familiar layout. Enjoy a fresh and modern look.
Fixes
Resolved an issue with Custom Controls in Conditional Access.
Resolved an issue with external authentication methods (EAM) in Conditional Access.
Fixed a SAML metadata file export issue.
Fixed an issue with the users API endpoint to modify user accounts with a Microsoft Entra ID data store.
Fixed a known issue in 24.4.1 where updating data store information in cloud deployments with SecureAuth IWA Service for Windows SSO wiped out the IWA service account password.
Fixed issues where editing an existing Split Profile data store caused an error. And creating a new Split Profile data store prevented data store selection.
Fixed issues with migrating realms from the Classic Experience to the New Experience, where it did not retain the selected data stores.
Known issue
You must update to RADIUS version 24.07.03 before upgrading to SecureAuth Identity Platform release 24.4.2 or later.
Release date: June 4, 2024
Enhancements
- Audit log update
Includes new Event ID for the SecureAuth LOA score and Confidence Level for each user.
See the Viewing LOA data section in the SecureAuth Level of Assurance (LOA) Provider settings topic.
- New conditional rule
In the authentication policy, we've added a new conditional rule, Continue to next rule. Use this rule when the Risk Engine is in its learning phase.
See step 3 in Add LOA rule in authentication policy.
- Authentication apps global MFA
New setting to Prevent re-use of TOTP to prevent unauthorized use of a previously generated TOTP.
- FIDO2 WebAuthn global MFA
New setting to Validate device registration with FIDO Alliance that enhances security.
Fixes
Resolved an issue where users had to manually clear cookies due to excessive growth from hitting multiple realms.
Updated installer to streamline updates to SecureAuth Identity Platform
Fixed an issue where saving email settings in the admin UI would clear out SMTP relay information, causing customers to stop receiving emails.
Fixed an issue where the Adaptive rule "Run Windows SSO" incorrectly prompted for MFA despite settings to skip MFA.
Resolved security issue where the IWA service account password was exposed in the data store list payload in the New Experience.
Known issue
In cloud deployments with SecureAuth IWA Service enabled for Windows SSO, updating any data store information might wipe out the IWA service account password.
Workaround: Re-enter the IWA service account password.
Note
This issue is resolved in the 24.4.2 release.
Release date: April 3, 2024
See also a list of hotfixes from previous releases that were rolled into this release and a list of known issues:
Enhancements
- Add external identity provider (IdP) in policy
New setting in the authentication policy allows you to delegate SAML-based authentication to an external identity provider, like Arculix.
To learn more, see SecureAuth IdP and Arculix integration (IdP Chaining) and SecureAuth IdP and Arculix integration (IdP Factoring).
- Aux ID for cloud storage
The data store properties have a new setting, Use Cloud Storage. Instead of storing this value in your data store, you can store this value in an Aux ID to the cloud profile database.
To learn more, see How to set up Aux ID for cloud storage.
- Dashboard enhancements
We've improved the look and feel of the Identity Platform dashboard. Some updates include:
Data organization: The dashboard now categorizes data into the following four tabs to optimize analysis:
Login Data – Explore data related to logins by system, applications, or users.
User Profile Data – Explore cloud profile data associated with each user name.
Authentication Types – Explore data on enrolled mobile and authenticator devices, and view push notifications blocked by users.
Deployment Data – View product versions for services deployed with your Identity Platform tenant.
Quicker data refresh: Dashboard data now refreshes every 3 hours for quicker visibility to key metrics such as user logins.
To learn more, see Dashboard insights.
- Password Policy updates
Some password policy updates include:
Password Policy change. Before, the password policy was linked to the application in the Application Manager. We changed where password policies are linked, which is now in the authentication policy. It's on the Login Workflow tab. The password policy is no longer restricted to the Password Reset page at the application level. You can now set a password policy for all applications attached to the authentication policy. This includes Account Management pages and SAML applications.
Real-time password rules. Users can now see the password rules in real-time when they change their password in the application.
Inline password change. Setting now available in the New Experience for authentication policies. It's on the Login Workflow tab. The setting allows users to change their password inline without leaving the page.
To learn more about setting up password rules, see How to configure and display password rules for users.
- SAML Logout
Provides seamless termination of user sessions in the Identity Platform (IdP) when they log out of a service provider (SP).
To learn more, see How to configure SAML Logout.
- Single Logout (SLO)
Provides seamless termination of connected SPs within the corporate SSO ecosystem when the user logs out of an SP.
To learn more, see How to configure Single Logout (SLO).
- SecureAuth Risk Engine updates
We've integrated a machine-learning based Assurance Provider to analyze login patterns of users. It generates a Level of Assurance (LOA) confidence score for each user. The LOA score helps decide whether to increase or decrease user friction at the time of login.
To learn more about configuring and using LOA, see SecureAuth Level of Assurance (LOA) Provider settings.
- Send FIDO2 confirmation email
Send a confirmation email to the user when they enroll or remove a FIDO2 authenticator in their profile.
To learn more about configuring this setting, see How to send a confirmation email about a FIDO2 device.
- Send password change notification
Send a notification to the mobile app to let the user know about a password change.
To learn more about configuring this setting, see How to send a notification about a password change.
- SSO Portal page improvements
Customize the look and feel of your organization's SSO Portal. You can edit the default portal theme, or create custom themes, and set how application tiles appear. Apply your theme when you configure an SSO Portal page in the Internal Application Manager.
For more information, see Customize a Modern Theme and SSO Portal configuration.
- Windows SSO as an adaptive rule
Windows SSO as an MFA method has moved to the Authentication Rules tab in the authentication policy. You can use Run Windows SSO as a condition in an authentication rule for Country, IP Range, or Threat Service.
Other improvements and fixes
- Copy data store
We've added the ability to copy a data store. This makes it easier to clone a data store and change attributes for other applications.
- Deprecate Create New From Template
In the Advanced Settings (formerly Classic Experience), we've deprecated the Create New From Template feature.
- Extend realm limit
Added improvement to extend the realm limit beyond 999.
- FIDO2 device card view
New admin setting to set how users will view their devices on the FIDO2 Enrollment page. Admins can choose the card view or table view for their users.
- FIDO2 device restriction options
More options to restrict how many FIDO2 devices a user can enroll. Available settings are No limit, or 1 through 10.
- Microsoft Conditional Access Custom Controls
Added out of the box integration with Microsoft Conditional Access and the Identity Platform.
- Mobile services updates
We've added some configurations that relate to mobile services features.
Override company display name – In the application configurations, you can override the default company name that is set in the Multi-Factor Methods > Authentication Apps settings. This setting is in the Application Manager and Internal Application Manager.
Enable blocking of push notifications – New admin setting allowing users to block unknown login requests. This setting is in the Multi-Factor Methods > Authenticate Apps configuration.
To learn more, see How to block and unblock login requests in Authenticate.
Prevent third-party app scan of QR code – You can prevent users from using third-party apps to scan the QR code on the QR enrollment page. This setting is in the Internal Application Manager for QR enrollment page configuration.
Only allow enrollment from MDM devices – You can only allow QR and URL enrollment from mobile device management (MDM) devices. This setting is in the Internal Application Manager for QR or URL enrollment page configuration.
- New OTP Validation field for Login for Endpoints
We've added a new OTP Validation field in the data store properties. For end user authentication in Login for Endpoints, you will need to map to this field instead of an Aux ID.
- SAML post-auth message
During a SAML post-auth login workflow, it displays a message to users to be patient. To customize this message, see Customize the authentication waiting page message.
- SecureAuth Connector Installer UI updates
When generating the Connector configuration files, we added the ability to confirm or change the email address where you receive the passcode.
- Split profiles
In the New Experience, we've improved the ability for applications to pull Membership information and Profile information from different data stores.
- Theme
Changed the default theme to SA IdP on the Overview tab in the Advanced Settings. This is the theme for the pre-authentication login page that displays MFA options.