Use IdP redirect to change workflow
As a RADIUS administrator, you can use Adaptive Authentication in the Identity Platform to redirect users to different authentication workflows during RADIUS login. Starting in RADIUS version 24.07.07, new supported workflows let you define how users authenticate based on rules you set.
These supported workflows include:
TOTP– One-Time Passcode (TOTP/HOTP) onlyPINTOTP– PIN+OTPPASSWORD– Password onlyYUBICOOTP_ONLY– Yubico OTP only
Redirect users to a workflow based on identity
Use Adaptive Authentication in the Identity Platform to route users to different authentication workflows based on their ID. This setup supports a mixed authentication model.
For example, most users can use PIN+OTP, while certain users authenticate with a password entered in their VPN client and authenticate against the PASSWORD endpoint.
Prerequisites
Available in RADIUS version 24.07.07 or later
Supported on Identity Platform releases 22.02 or later
Step 1 – Configure the RADIUS Client
Open your RADIUS Server Client.
Set the Authentication Workflow to use PIN+OTP.
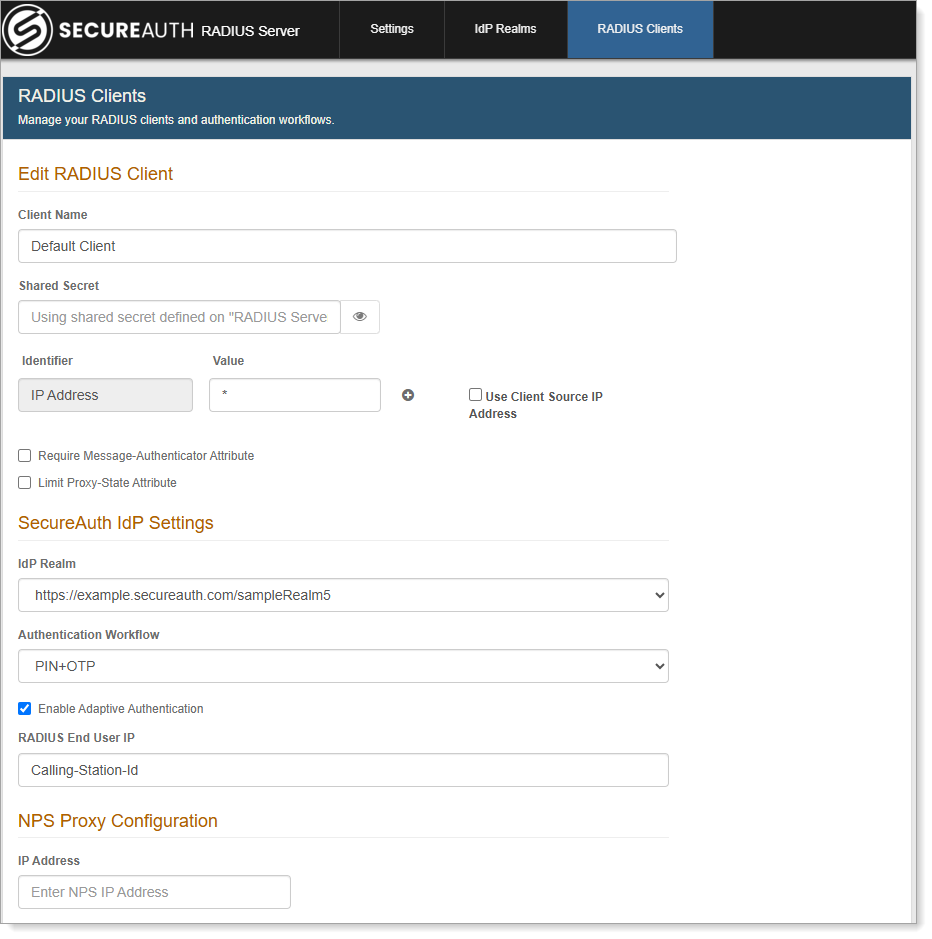
RADIUS Client configuration
Select the Enable Adaptive Authentication check box.
Save your changes.
Step 2 – Configure the authentication policy
In an authentication policy, go to the Authentication Rules tab.
Click Add New Rule and select User.
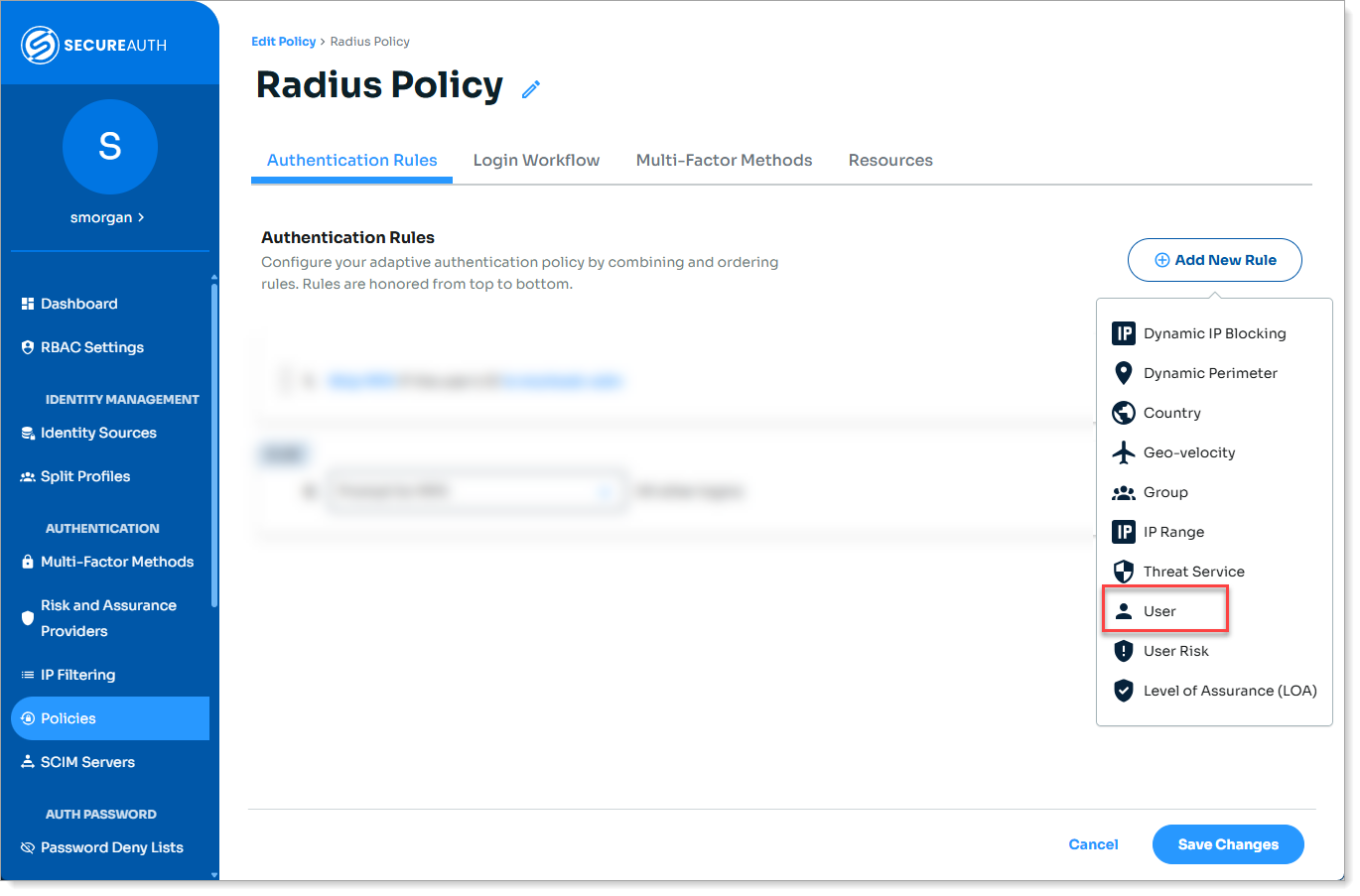
Authentication policy > add User rule
On the New Rule - User dialog:
Set the Condition Rule to Redirect To.
In the Add URL field, enter the alternate workflow, like password.
Define the user IDs the rule applies to.
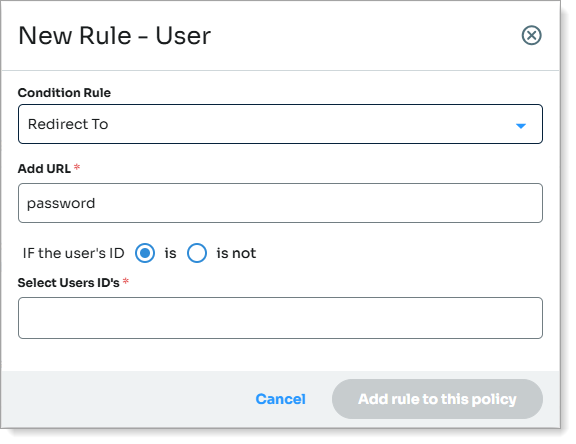
Redirect rule to "password"
Save your changes.
Result
Users who match the redirect rule authenticate using the password entered in their VPN client. All others use PIN+OTP. You manage both experiences within the same Identity Platform realm, VPN server IP, and RADIUS client.