Authoring Access Policies Using REGO or Visual Editor
SecureAuth enables developers to implement authorization policies using Open Policy Agent's REGO language or using SecureAuth built-in visual editor.
Authorization Policy Visual Editor
SecureAuth’s intuitive built-in visual editor makes policy formulation both flexible and user-friendly, but, at the same time, allows for advanced policy definition.
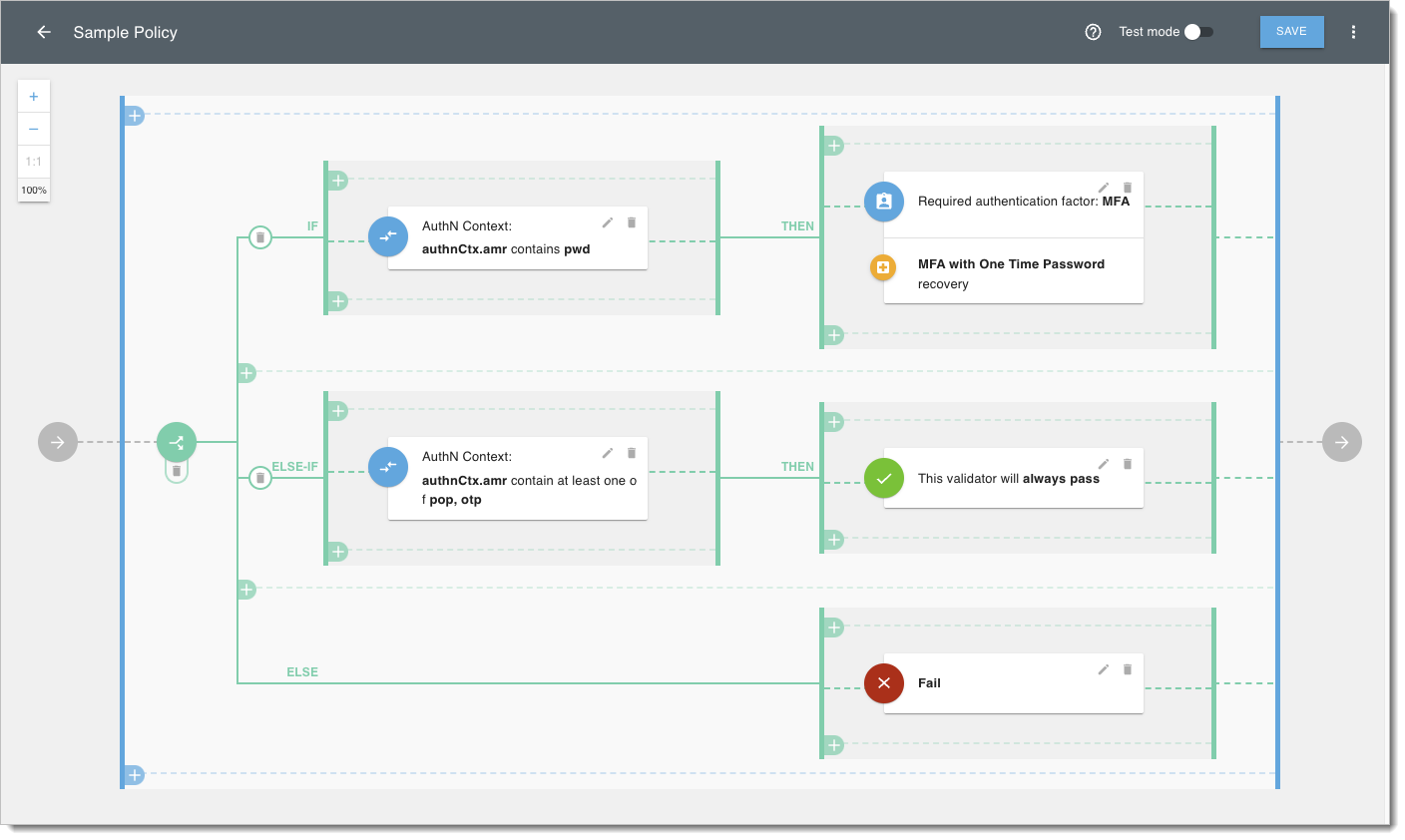 |
The visual editor provides a more straightforward avenue for individuals who may not be proficient in scripting, thus democratizing the policy definition process across different skill levels within an organization. You create a logical structure composed of validators (provided out of the box by SecureAuth) where each validator returns true or false based on the checks it performs. As a result, SecureAuth can evaluate whether to pass on or block the request.
Validators can perform the following actions:
Check attributes from the request context (including authentication context, ID and access tokens, secrets, and scopes)
Check request header parameters
Check dynamic scopes
Embed existing policies into the current policy
Add if/else logic to the policy
Provide MFA checks with OTP recovery
Match values based on wildcards, i.e.
admin-*matchingadmin-123
Authorization Policies in OPA's REGO Language
The Open Policy Agent (OPA) is an open source, general-purpose policy engine that enables unified, context-aware policy enforcement across the entire stack.
OPA gives you a high-level declarative language called Rego to author and enforce policies across your stack. When you query OPA for a policy decision, OPA evaluates the rules and data (which you provide) to produce an answer. The policy decision is sent back as the result of the query.
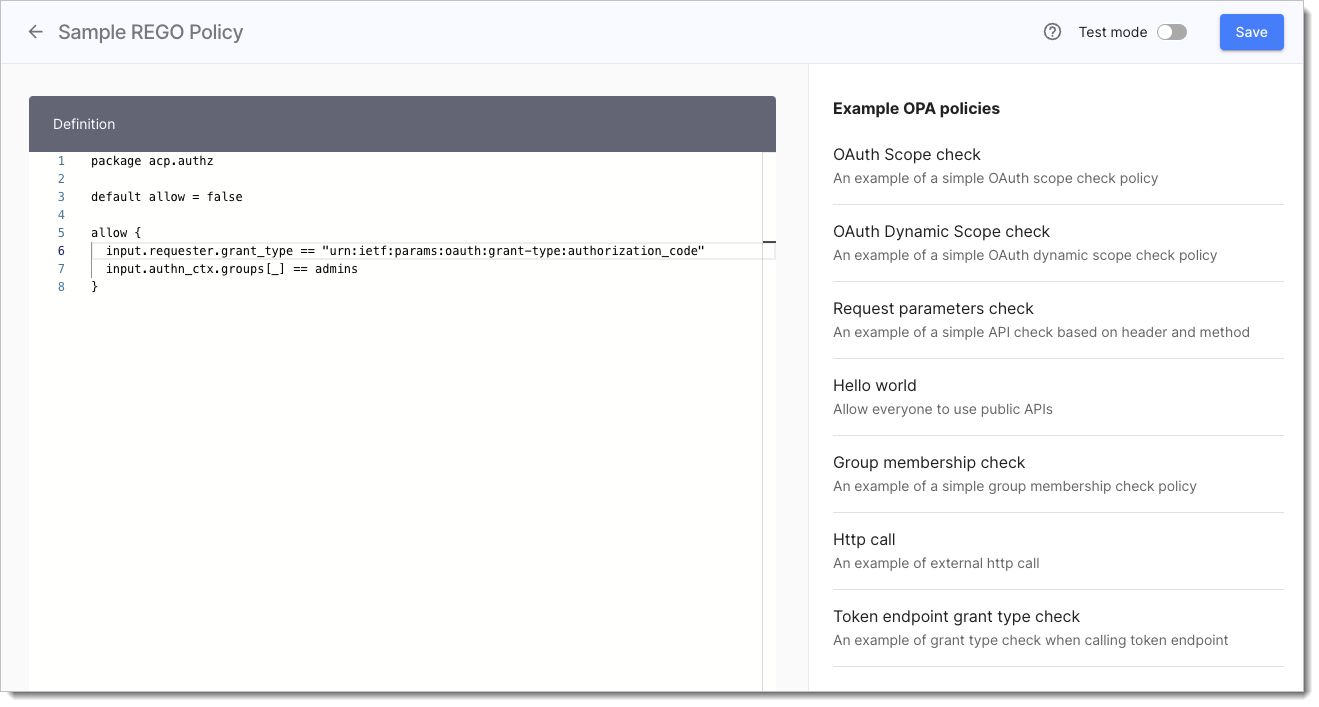
SecureAuth platform contains an embedded Rego editor which also includes code samples to help you get started. When creating policies in SecureAuth platform, keep in mind to take the policy type into account.
 |
Policy Types
Policy type | Description |
|---|---|
User | User policies validate requests involving user interaction. They can be assigned on a workspace level (Token issue policy), application level (User policy) and service scope level (Consent grant policy). |
Developer | Developer policies validate client registration and developer subscriptions to a given scope. They can be assigned on a workspace level (Client registration policy) and service scope level (Client assignment policy). |
Machine to machine | These policies validate a token request coming from a client using the Client credentials OAuth 2.0 flow. They can be assigned on a workspace level (Machine token policy) and service scope level (Machine to Machine policy). |
Dynamic Client Registration | DCR policies are used to validate Dynamic Client Registration requests. |
API Request | An API policy validates requests coming to APIs protected by a gateway bound to SecureAuth. |