Modern user authentication for SaaS applications
Add modern authentication features to your SaaS applications, including passwordless login, single sign-on (SSO), multi-factor authentication (MFA), and customizable login flows.
Authentication overview
SecureAuth CIAM provides user authentication and SSO for connected applications and APIs by default. Adding an application enables you to leverage these authentication services.
Authentication needs for SaaS applications
Nearly all SaaS applications require user authentication, especially multi-tenant services delivered by a SaaS identity platform..
Early-stage SaaS applications. Prioritize quick setup, scalability, and pay-per-use models for user authentication.
Mature SaaS applications. Focus on advanced authorization and access control to handle more complex use cases
Consumer vs. Business SaaS authentication
SecureAuth CIAM supports both consumer and business use cases, offering flexible login options like social login for consumers and SSO/SAML for enterprise scenarios.
Consumer SaaS applications. Passwordless login, social login, and simplicity.
Business Saas applications. SSO with delegated administration, enterprise identity providers, and SAML support.
SecureAuth excels in Business SaaS scenarios with its advanced authorization engine and multi-tenancy capabilities.
SecureAuth as an identity provider
SecureAuth supports user storage and authentication across various user populations. It also enables business accounts to connect external identity providers through self-service.
To learn more, see Authentication methods and External authentication providers in this topic.
Authentication methods
SecureAuth CIAM supports multiple secure login methods to help you protect access to your applications. Identity Pools connect users to workspaces, enforcing authentication before accessing your applications.
Passwordless authentication with passkeys
Users log in using a device’s built-in biometric or PIN, such as a fingerprint or face scan. This method replaces passwords and supports a smoother, more secure experience.
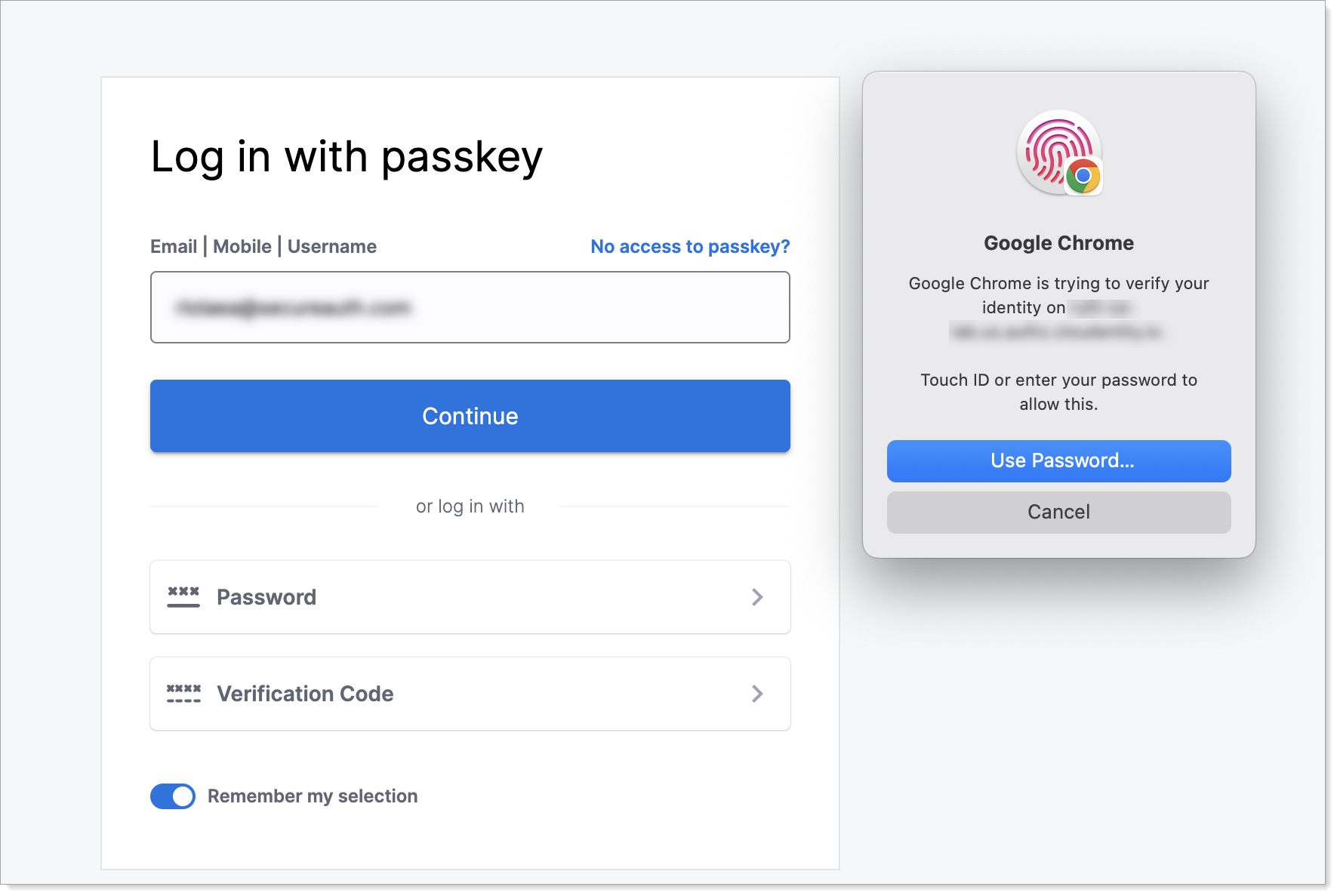 |
Login using passkey
Passkey login follows the WebAuthn protocol, developed by W3C, FIDO. It uses public-key cryptography to ensure strong, phishing-resistant authentication across devices.
Authentication with verification codes
Users receive a unique, time-limited code by email or SMS. They enter the code, along with an identifier (such as email or phone number), to log in.
Custom apps can also generate and send codes. These codes are single-use and expire quickly, making them more secure than passwords.
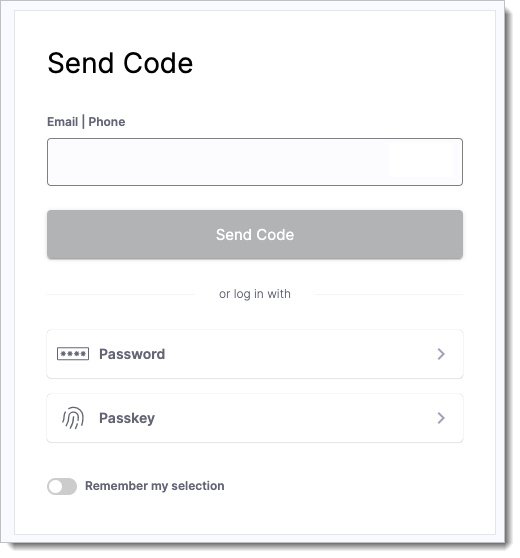 |
Login using verification code
Authentication with magic links
SecureAuth generates a unique, time-limited link and sends it to the user’s email or phone. Clicking the link logs the user in and redirects them to the application.
Note
Magic links require API integration or a custom login page. They are not currently supported through the standard UI.
Authentication with identifier and password
Users enter a username, email, or phone number along with a password. SecureAuth checks these credentials and grants access if they match stored values.
This is a standard and widely supported method but is more vulnerable compared to passkeys or verification codes.
External authentication providers
Connect external identity providers to enable users to log in with accounts they already use. Choose from social or enteprise providers to streamline authentication for different user types.
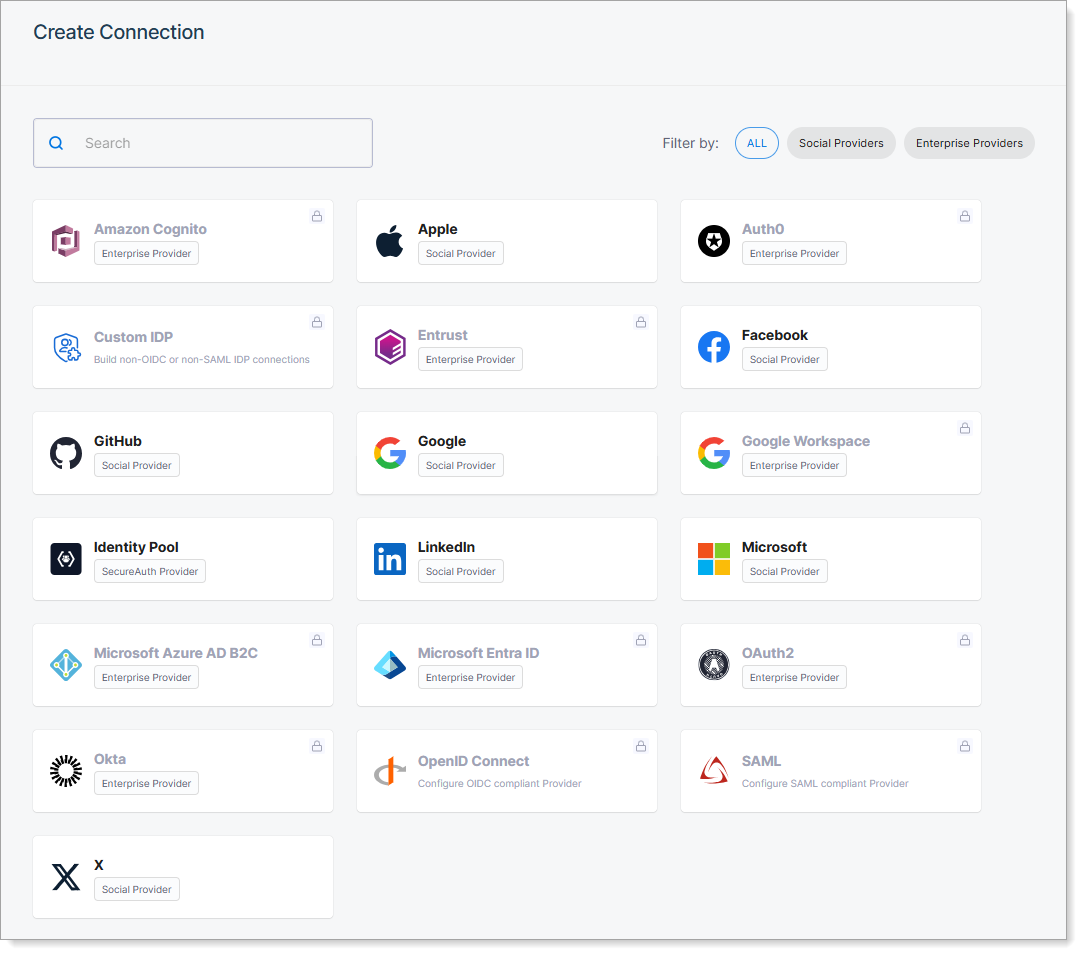 |
Select a social or enterprise identity provider to create a connection
Enterprise identity providers
Use enterprise Identity providers to enable SSO and centralized authentication for your workforce.
Supported enterprise providers include:
Amazon Cognito
Auth0
Custom IDP
Entrust
Google Workspace
MIcrosoft Azure AD B2C
Microsoft Entra ID
OAuth2
Okta
OpenID Connect
SAML
Configure these providers in a selected workspace under Authentication > Providers > Create Connection. Select an enterprise provider type and follow the prompts to complete setup.
Single sign-on (SSO) and enterprise authentication
Businesses often require identity federation to manage identities across multiple domains or enterprises. SecureAuth enables you to:
Integrate with SAML-based applications
Standardize user data from different IDPs into a unified authentication schema
Approach to authentication
Developers must choose between a universal login flow or an embedded login flow for user authentication.
Universal login. Redirects users to a central domain for authentication before returning them to the application.
Embedded login. Keeps users on the same page, displaying a login widget and sending credentials to the authentication provider via a cross-origin request.
SecureAuth recommends using universal login for secure authentication. This method reduces the risk of cross-origin attacks andaligns with OAuth best practices.
Social login providers
Users can log in with accounts they already use, such as Google or GitHub. This removes the need to create and manage new credentials.
Supported social login providers:
Apple
Facebook
GitHub
Google
LinkedIn
Microsoft
X (Twitter)
Each provider supports two connection types:
Option
Description
Embedded
Uses a pre-registered client application from SecureAuth. Setup is fast and requires no external configuration.
Social identity provider - Embedded configuration example
Bring your Own
Uses credentials from a client application registered by your organization. This option allows you manage your application configuration.
Social identity provider - Bring your Own configuration example