Understanding schemas in CIAM
Schemas shape every identity in SecureAuth CIAM. Schemas determine what data you collect for each user, how you store it, and how it flows across registration forms, authentication tokens, and integrated applications. Whether you manage customers, partners, or employees, schemas help you organize identity data to meet your business and security requirements.
What are schemas and why do they matter?
In SecureAuth CIAM, schemas form the foundation of how your system understands and organizes user identity data. Think of schemas as blueprints that define what information you collect, how you structure it, and how you use it throughout the user lifecycle.
When you implement the right schemas, you ensure consistent data collection, improve user experience, and meet business and compliance requirements.
Schemas directly support critical processes such as:
User registration
Profile management
Authentication
Role-based or delegated access
Integration with enterprise tools like Salesforce or ServiceNow
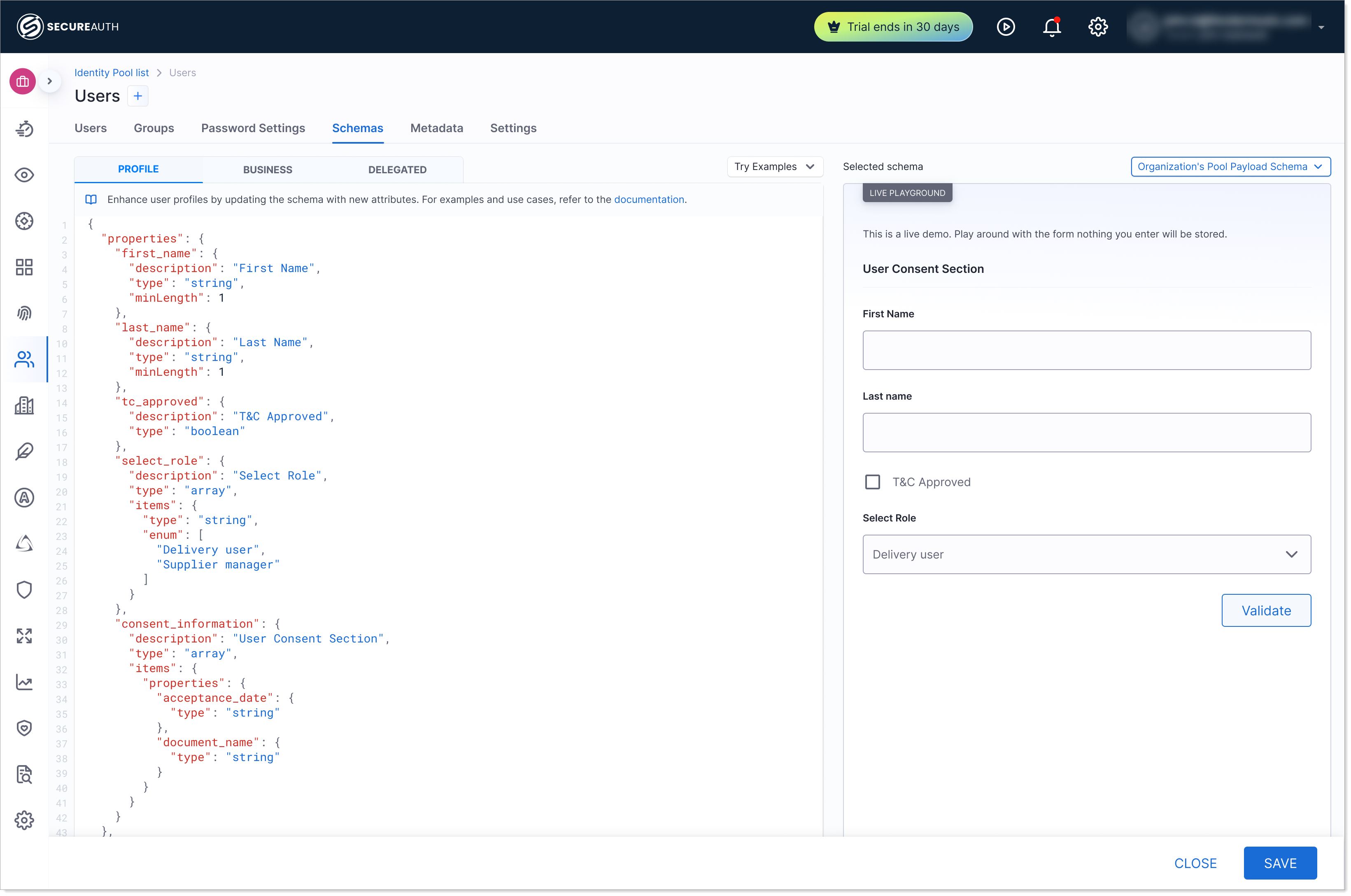 |
Example of a Profile schema for users in an identity pool
Example real-world use case
IdentMobile, a fictional mobile carrier brand, uses SecureAuth CIAM to manage identity across its customer portals, partner agents, and internal tools. IdentMobile uses all three schema types: profile, delegated, and business, to create a unified and flexible identity model.
Consumers
Consumers access the IdentMobile web and mobile portals to manage personal accounts. This schema captures the basic identity and preference data so IdentMobile can personalize the experience and meet compliance obligations. These users follow the profile schema, which includes:
first_name,last_name,emailpreferred_language,terms_accepted_atnotification_opt_in
The schema ensures:
Compliance with legal requirements
Personalization through language preferences
Preference management for communications
The system validates any login or self-service update against this schema.
Partner retail agents
Authorized agents in stores or call centers access a delegated admin portal. This schema defines administrative permissions and ensures agents can only access customer operations within their scope. Their accounts follow the delegated schema, which includes:
org_id– the partner organization they representdelegated_role– the role assigned to the agent, such as “Account Manager” or “SIM Technician”allowed_actions– the list of approved tasks the agent can perform, such as activating a SIM or suspending an account
The schema controls:
Which organization the agent represents
Which role defines their administrative access
Which actions the agent can perform
Internal operations staff
Employees in billing, support, or engineering use SecureAuth CIAM to connect to internal tools like ServiceNow and Datadog. This schema enriches internal logins with business-specific attributes that drive workflows and visibility in enterprise systems. You structure their identity using the business schema, which might include:
employee_id,department,support_tierregion,on_call_rotation
The schema supports:
Which identifiers and organizational units are used for internal routing
Which support levels and locations apply to user roles
Which operational data you include in tokens or assertions (digital certificates that contain user information)
Summary of schema types
Profile schema – you use this for end users and consumers
Business schema – you use this for internal teams connected to enterprise systems
Delegated schema – you use this for partner admins who act on behalf of others
Next step: Learn how to implement these schemas in Using Identity Schemas to define custom user attributes.