OAuth2 mTLS Client Authentication
Learn how to configure SecureAuth so that it verifies client application's root certificates instead of the system root certificates in case the mTLS client authentication method is enabled.
About Certificates in mTLS
If your application is configured to use mutual Transport Layer Security (mTLS), you can add trusted client certificates that are verified by SecureAuth when the TLS handshake happens. If you add a trusted client certificate, SecureAuth trusts any certificates issued by that particular Certificate Authority (CA). Then, SecureAuth only verifies if the certificate had not expired prior to the TLS handshake and that the certificate is signed by the CA that your workspace (authorization server) is configured to recognize.
If you add your own client certificates, they are used instead of system root certificates that can be found in your SecureAuth's configuration files.
Enable Root CAs
In your workspace, go to OAuth > Authorization Server > Client Authentication.
Navigate to the Trusted client certificates section.
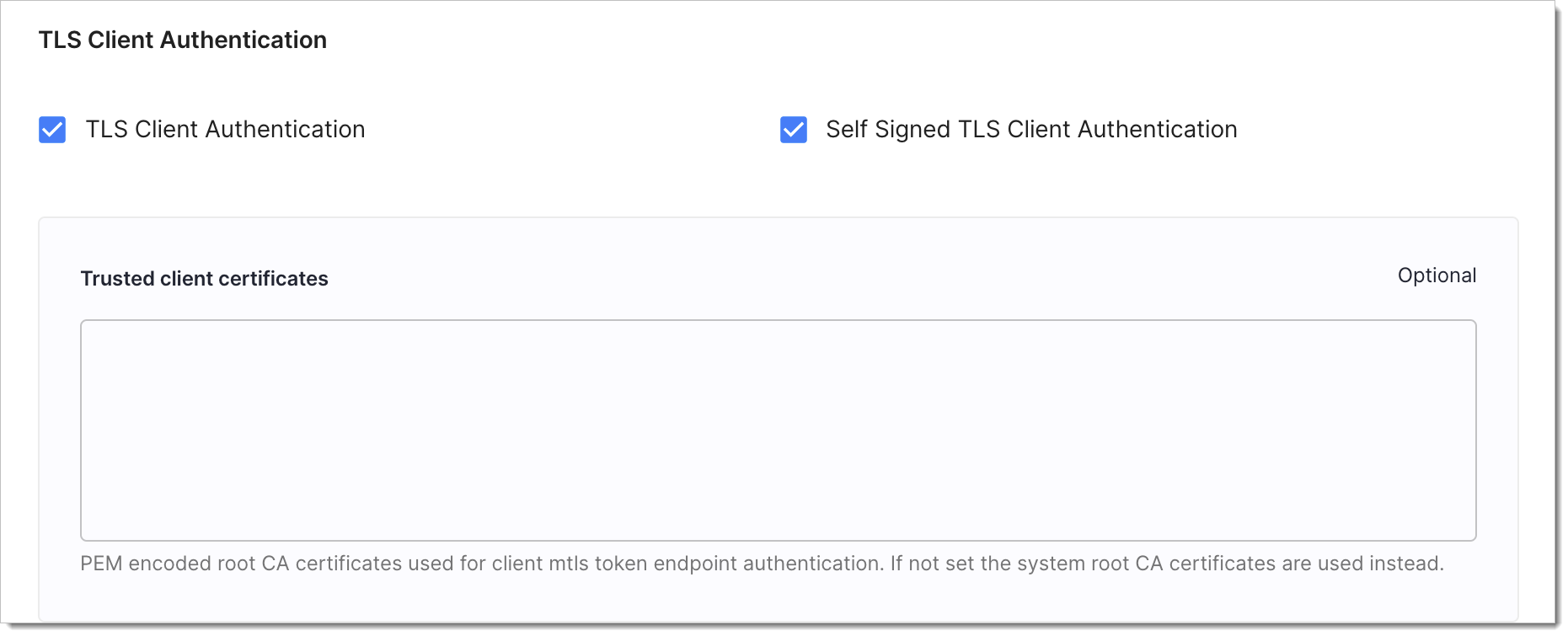
Enter a PEM-encoded root CA certificate into the Root CAs field and select Save changes.
Result: For client applications with the tls_client_auth method enabled, root CA certificates are used instead of system root certificates.