Manage signing keys
SecureAuth lets you manage signing keys to secure your system. Learn what signing keys are and how managing them enhances security.
Keys management overview
OAuth 2.0/OpenID Connect relies on signed tokens, such as access tokens or ID tokens, to authenticate and authorize users or clients. These tokens, signed with cryptographic keys, provide temporary credentials. While more secure than user credentials, these tokens can be vulnerable if not managed properly.
SecureAuth allows you to manage signing keys to protect against compromised tokens. You can rotate or revoke keys manually or set up automatic rotation based on a schedule.
Recommendation: Set up periodic signing key rotation to strengthen security.
How SecureAuth handles signing keys
SecureAuth uses one signing key at a time but can store multiple keys in the JSON Web Key Set (JWKS) for your application.
Key Rotation: Rotated keys stop signing new tokens but remain valid for token validation.
Key Revocation: Revoked keys are immediately invalid, preventing any authentication attempts with tokens signed by them.
This approach lets you respond quickly to potential security breaches by rotating or revoking compromised keys.
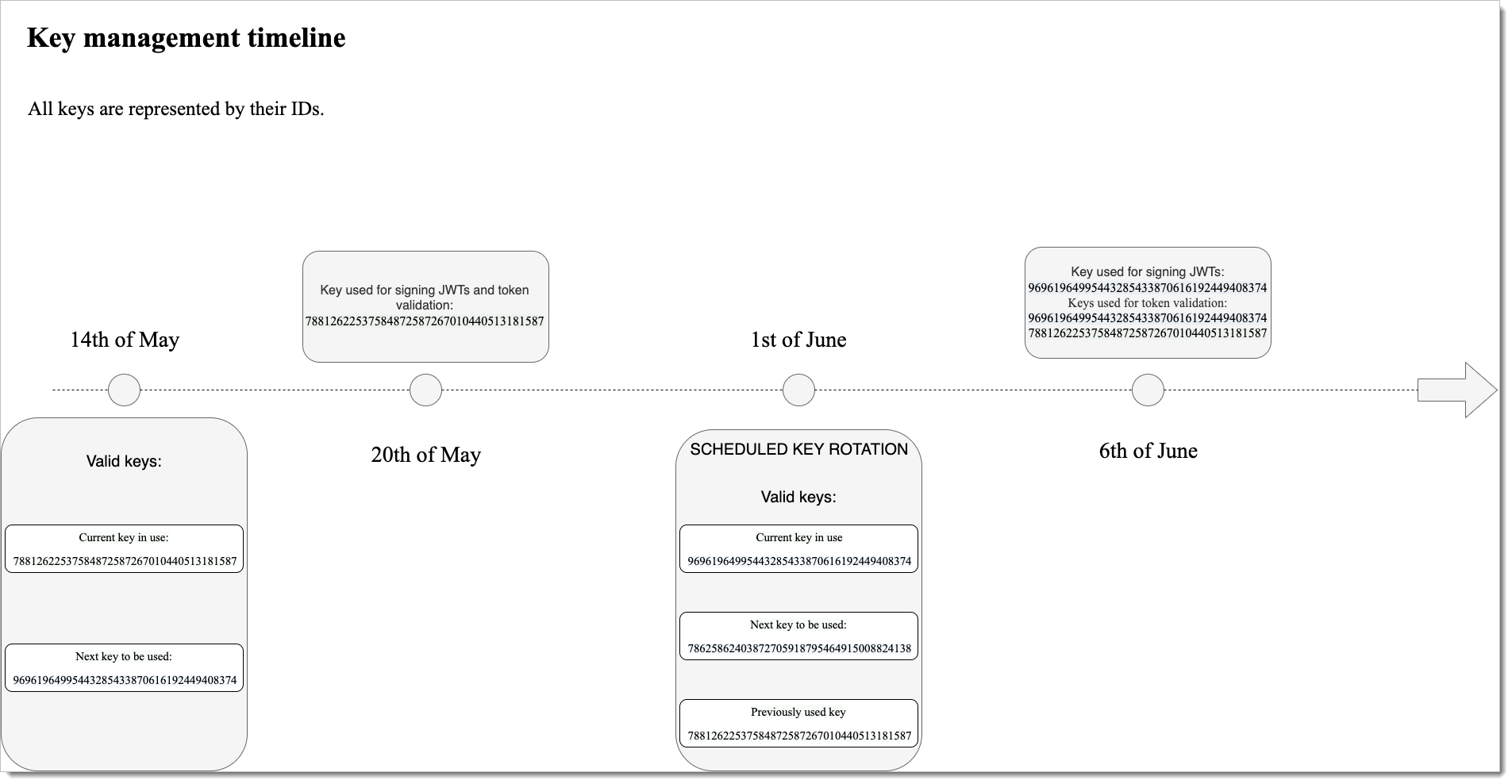
Automatic key rotation example
The following timeline shows an example of automatic key rotation, with signing keys identified by key IDs.
 |
Key rotation in depth
In web environment, proper and secure management of cryptographic keys, in this case, signing keys, is crucial for the effective use of cryptography for security.
Cryptoperiods
The National Institute of Standards and Technology (NIST) defines a cryptoperiod as the valid timespan for a key. After this period, the key should be rotated or revoked to maintain security..
Private Keys: Use for 1–3 years, then revoke.
Public Keys: Use for a few years, but longer validity increases vulnerability.
SecureAuth allows public keys to verify tokens even after their corresponding private keys expire, as long as the tokens' timestamps fall within the cryptoperiod..
For details, see NIST Recommendation for Key Management, section 5.3.5.
Key rotation in SecureAuth
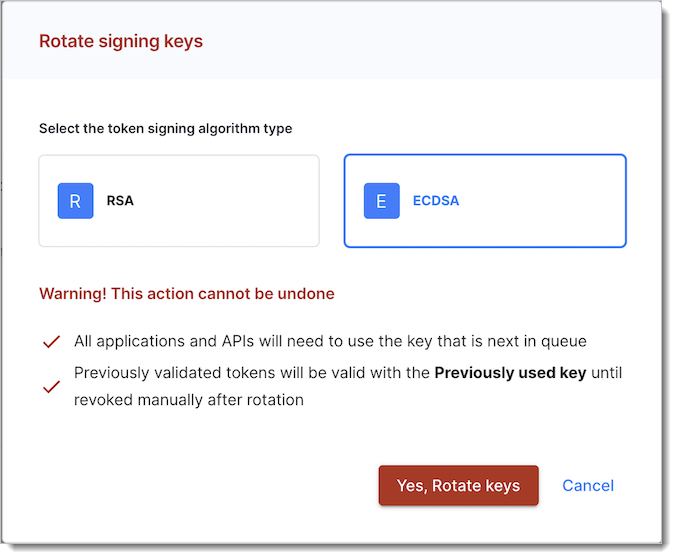
You can configure signing keys and automatic rotation in your workspace settings. Manually rotate keys when needed to improve security.
Rotate the active key or rotate and revoke it.
SecureAuth stores up to 8 rotated keys and 16 revoked keys.
Choose between ECDSA and RSA algorithms for signing tokens. By default:
Authorization servers use ECDSA
Workforce servers use RSA
Once you select a key type, future rotated keys will use the same type.
 |
Warning
If you change key types (e.g., from ECDSA to RSA), update your client configurations, including the ID Token Signing Algorithm and JARM Signing Algorithm.
Effective key management enhances security and ensures smooth token authentication and authorization.