Set Up Sandbox IDP for User Authentication
Instructions on how to connect the Sandbox IDP to SecureAuth and how to enrich users' mock data.
About Sandbox IDPs
Sandbox IDP is a static IDP that gives you a possibility to test SecureAuth features without the need to configure connection to your identity provider. It allows you to create and define mock users that can be useful while testing or creating proofs of concept. You can add a Sandbox IDP on a workspace level. You can also enrich the user's authentication context by using the SecureAuth Update Static IDP API.
Note
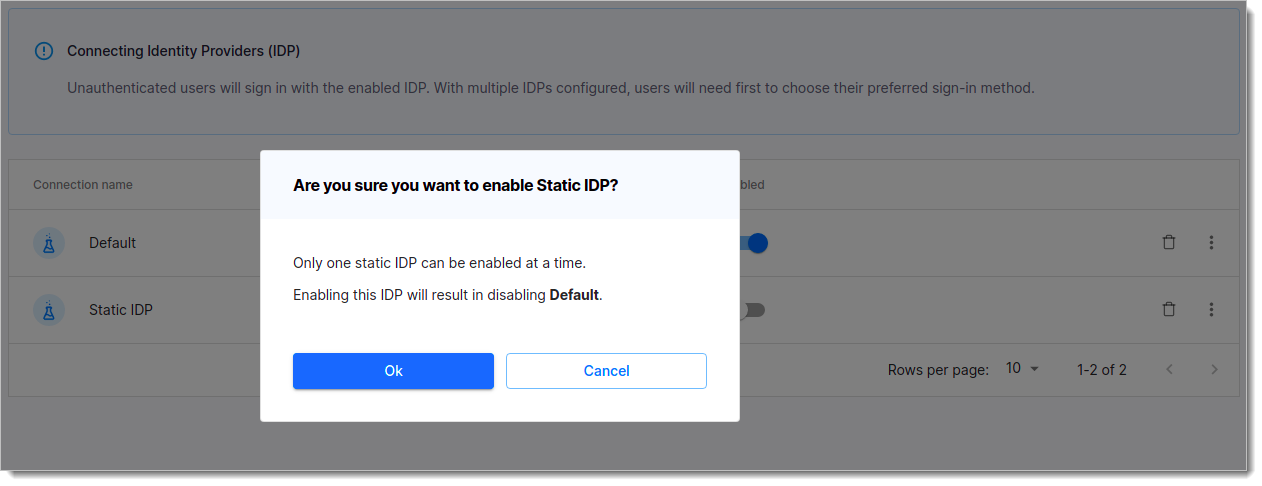
It is possible to have exactly one Sandbox IDP or an external datastore IDP enabled for a workspace, but you can create more of them. Enabling one of the IDPs results in disabling the one that was enabled so far.
 |
A Sandbox IDP can be created and connected in two ways:
During the workspace creation where you are led through all of the necessary steps
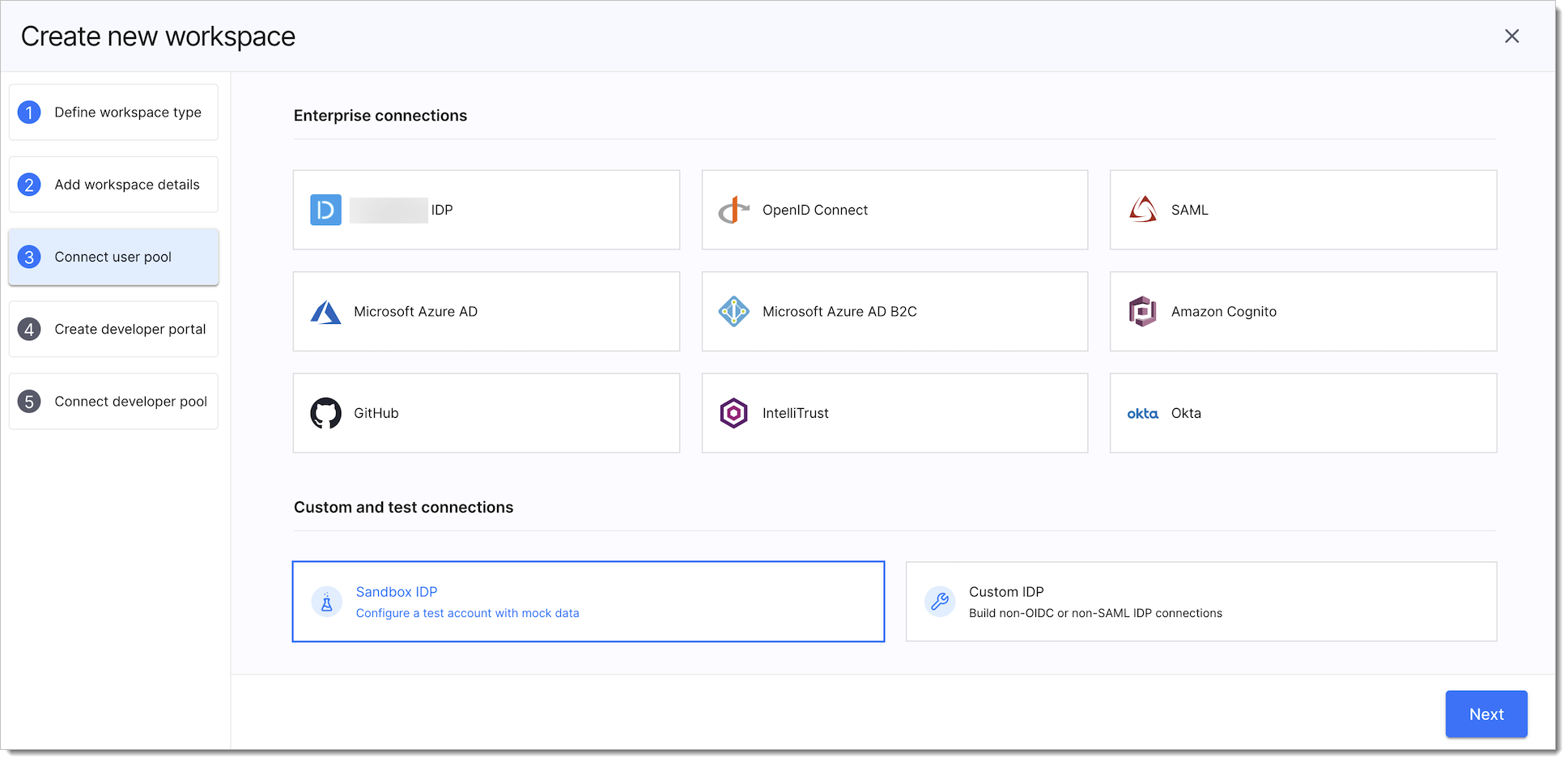
After a workspace had been created
Create Sandbox IDP
Go to Workspace > Identities.
Select CREATE IDENTITY.
Select Sandbox IDP.
Fill in the necessary fields and provide mock users.
Tip
You can enable the authentication context caching if you wish to store the user's authentication context locally. Learn more by reading the stateful authorization with SecureAuth documentation.
Example:
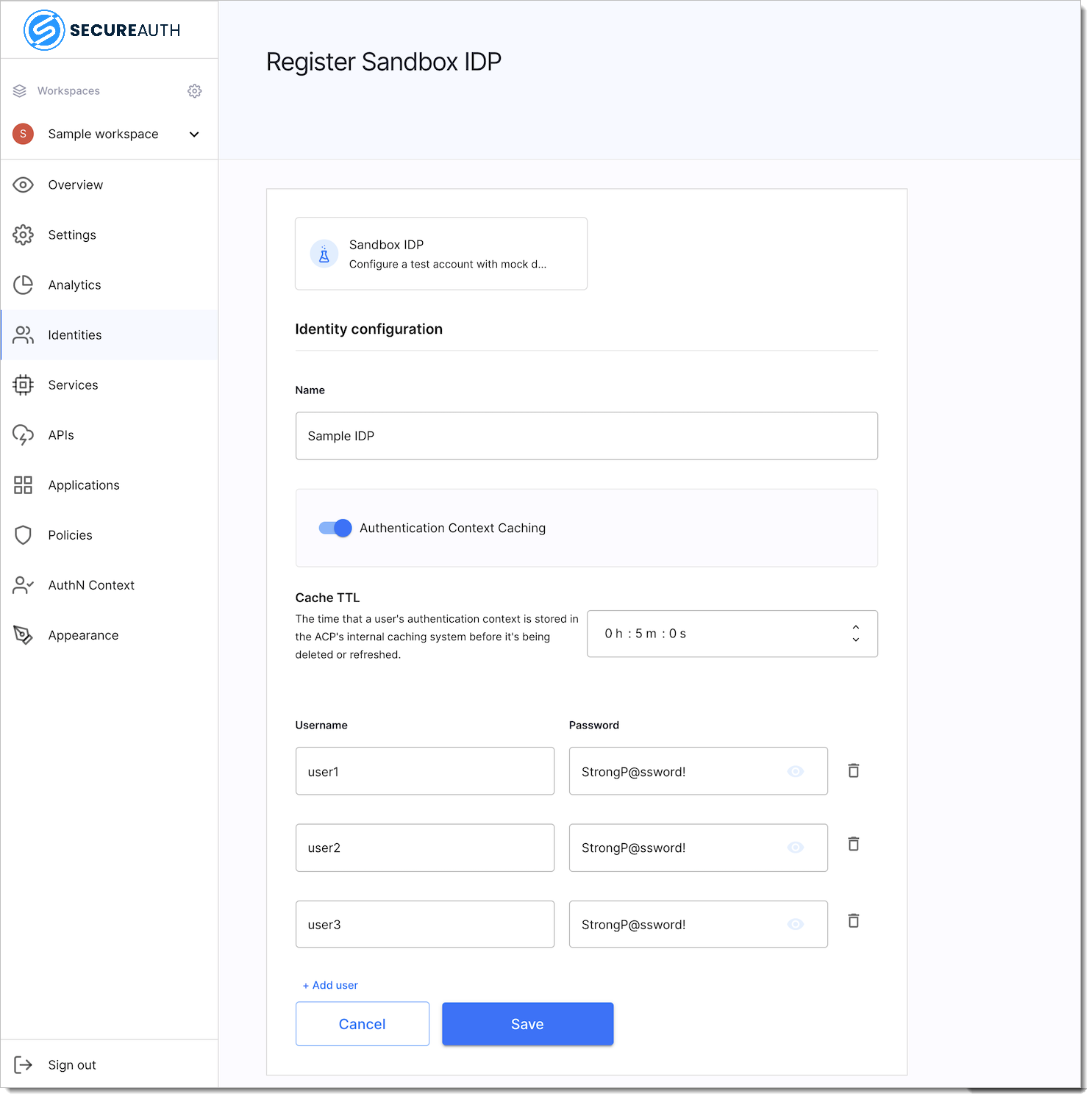
Select Save.
Result: Your Sandbox IDP is created and visible in the Identities.
About Enriching Mock Users Authentication Context
In SecureAuth, you can enrich your mock users' authentication context. You can do it by using the SecureAuth Update Static IDP API.
Prerequisites
You have created a Sandbox IDP.
You have created authentication context attributes for your IDP.
You have mapped attributes to an already existing AuthN context attributes or to newly created ones.
Enrich AuthN Context for Mock Users
Prepare a request body that you will use in your request to the update static IDP endpoint.
{ "id": "c2vjshp6ngjkelj1jftg", "tenant_id": "default", "authorization_server_id": "sample-workspace", "client_id": null, "name": "Sample IDP", "disabled": true, "method": "static", "attributes": null, "mappings": [ { "source": ".", "target": ".", "type": "any", "allow_weak_decoding": false } ], "static_amr": [], "transformer": { "enabled": false, "script": "" }, "config": { "enable_stateful_ctx": false, "stateful_ctx_duration": "0s" }, "settings": { "hint": false }, "credentials": { "users": [ { "username": "user1", "password": "StrongP@ssword!", "authentication_context": { "studentID": "f5cda932", "maritalStatus": "Married" } }, { "username": "user2", "password": "StrongP@ssword!", "authentication_context": { "studentID": "c8fe349e", "maritalStatus": "Single" } }, { "username": "user3", "password": "StrongP@ssword!", "authentication_context": { "studentID": "fafbdbc2", "maritalStatus": "Divorced" } } ] } }Tip
You can define your attributes and their values under the
authentication_contextnode.Send a request to the update static IDP endpoint.
curl -v -k -X PUT https://example.com/api/admin/default/servers/sample-workspace/idps/static/c3k1nl8ppd6re169h590 -H "Authorization: Bearer $AT" -d '{ "id": "c3k1nl8ppd6re169h590", "tenant_id": "default", "authorization_server_id": "sample-workspace", "client_id": null, "name": "Sample IDP", "disabled": false, "method": "static", "attributes": null, "mappings": [ { "source": ".", "target": ".", "type": "any", "allow_weak_decoding": false } ], "static_amr": [], "transformer": { "enabled": false, "script": "" }, "config": { "enable_stateful_ctx": false, "stateful_ctx_duration": "0s" }, "settings": { "hint": false }, "credentials": { "users": [ { "username": "user1", "password": "StrongP@ssword!", "authentication_context": { "studentID": "f5cda932", "maritalStatus": "Married" } }, { "username": "user2", "password": "StrongP@ssword!", "authentication_context": { "studentID": "c8fe349e", "maritalStatus": "Single" } }, { "username": "user3", "password": "StrongP@ssword!", "authentication_context": { "studentID": "fafbdbc2", "maritalStatus": "Divorced" } } ] } } 'Result: Authentication context of your mock users is enriched with additional attributes.
Verify AuthN Context
To test if you have enriched the authentication context for mock users correctly, perform one of the following steps:
Use the SecureAuth get static IDP API . By using it, you can get the configuration of your static IDPs in the response body. Verify if the configuration from the response matches the configuration you had provided in the request to the
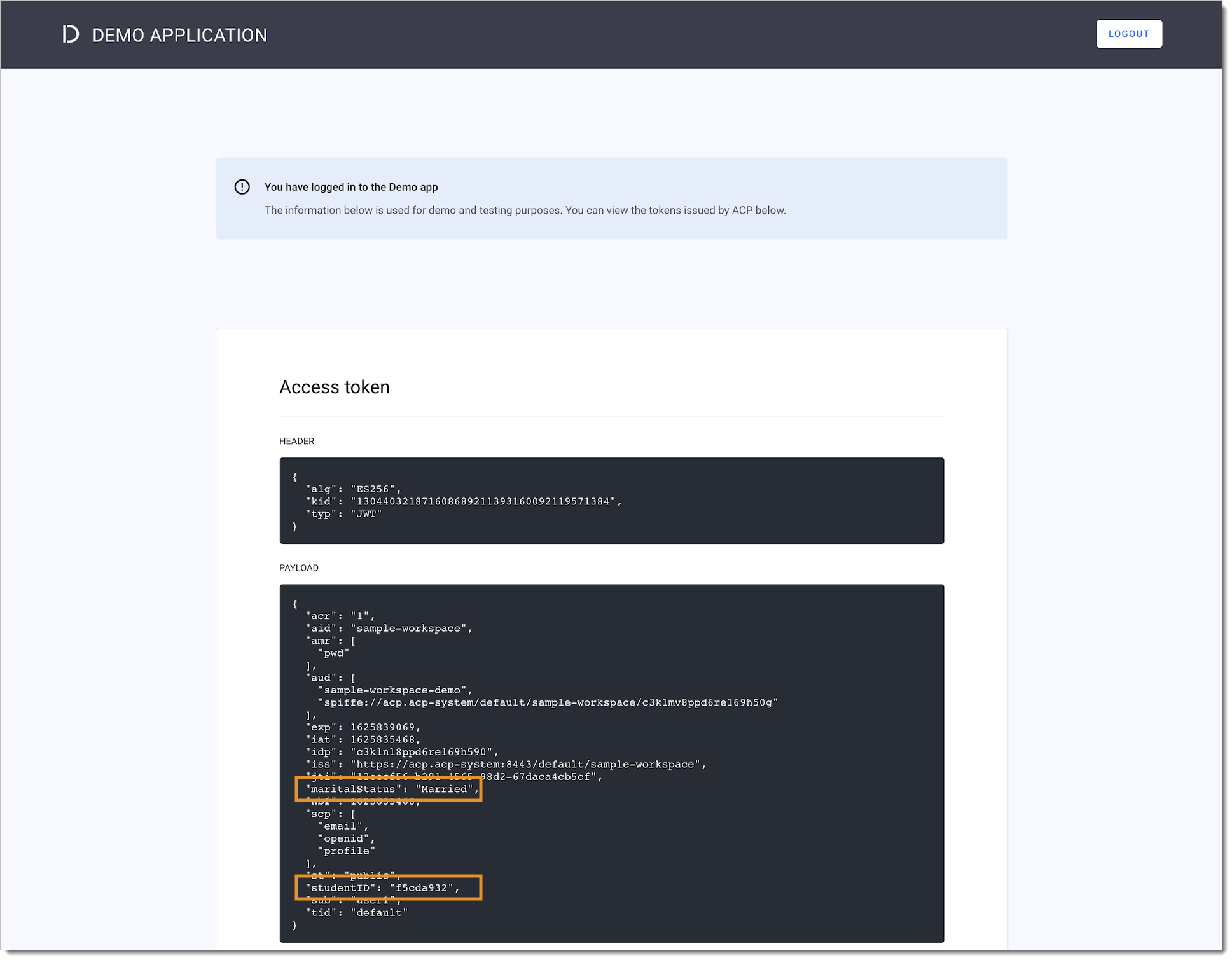
updateStaticIDPendpoint.Configure claims for access tokens to include your authentication context attributes and log in to the Demo Application using your Static IDP and one of the user credentials you had defined. Verify that the additional attributes are available, as in the example below.