Customer Deployed SecureAuth - Overview
Learn about customer deployed SecureAuth platform. Get familiar with all deployment models and different ways of installing our platform
Deploying SecureAuth
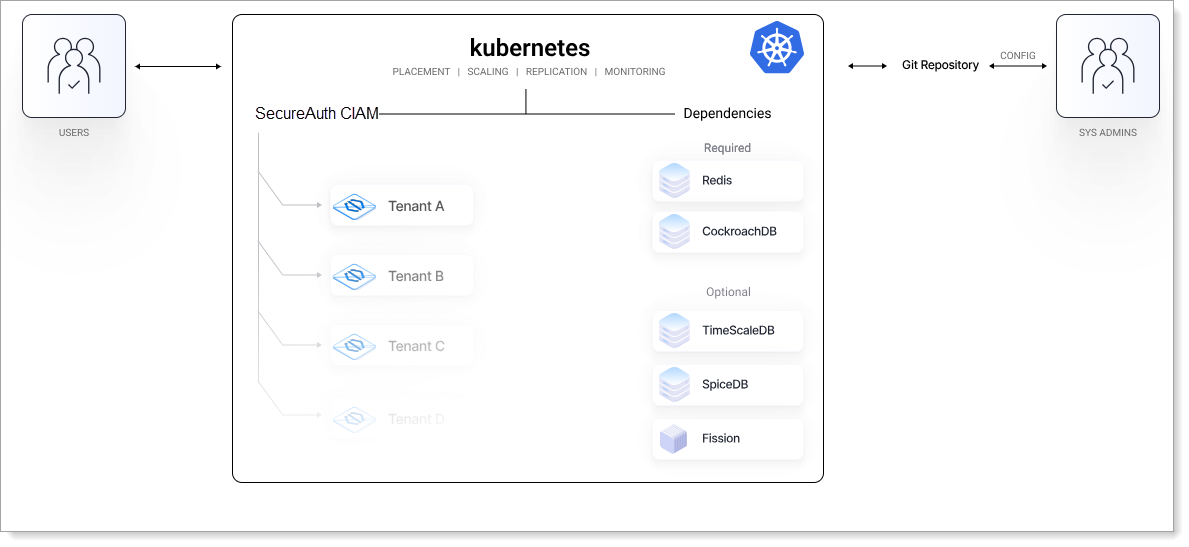
Deploy the SecureAuth platform on Kubernetes (K8s) using Helm's Charts. For streamlined infrastructure management, we've adopted the GitOps approach, centralizing configurations in a Git repository. Check out our regularly updated acp-on-k8s repository, which reflects our live production setup.
Warning
SecureAuth does not recommend running the example setup for production purposes without first making sure your deployment is hardened and production ready.
 |
Easily deploy SecureAuth and its infrastructure with our three deployment modes, tailored for your convenience:
Dev: Quick setup for testing SecureAuth
Base: Deploys SecureAuth and dependencies in a High Availability configuration.
Full: Extends the base mode by adding observability features, including traces, logs, and metrics.
Don't know which mode to run? Check the comparison.
Try It Now
You can find all necessary source code in the acp-on-k8s repository. This repository mirrors our own production environment and receives daily updates.
Dependencies
SecureAuth deployment comes with the following dependencies:
Required:
cockroachdb - to store various types of data, such as users added to SecureAuth Identity Pools, configuration of client applications connected to a workspace, information about consent grants, and many more.
redis-cluster - to store a variety of data types that are well-suited for key-value storage like access or ID tokens.
Optional:
TimescaleDB - to store audit and analytics/metrics data because it is a powerful and efficient tool for handling large amounts of time-series data.
SpiceDB - to enable creating and managing fine-grained authorization for applications.
Fission or Self-Managed Direct FaaS Environment to enable executing Extension Scripts in an isolated secure environment.