Postman Reference Collection for Identity Pools APIs with ROPC Grant Type
Learn how to configure SecureAuth platform to obtain authorization tokens using the Resource Owner Password Credentials Grant type utilizing Identity Pools as the identity provider
Overview
Sometimes high traffic applications require OAuth flows that does not require redirecting the users and have high level of trust to interface directly with the OAuth authorization server for minting access tokens. Even though Resource Owner Password Credentials flow does not fit into the OAuth spectrum for delegated user authentication, it does serve its purpose for applications which do not want user redirect flows and want to still mint user access tokens at scale. This model can simply be compared as an equivalent to using a direct authentication API from the a provider that returns authentication tokens in the form of JWT represented as access and ID tokens to get the best of both worlds where apps do not want to sacrifice user experience and want to achieve peak scales.
In this tutorial, we will configure and run a Postman collection that showcases basic workflows using SecureAuth identity pools and configures resource owner password credentials flow to obtain access token from SecureAuth as the OAuth authorization server.
This Postman collection is provided as a stepping stone for developers or integrators to understand various API calls, payloads, and authentication mechanism which, in turn, allows developers to quickly prototype or codify into programming language of their choice.
Prerequisites
Access to Admin & System workspace - Reach out to
info@cloudentity.comif you are not a paid customer to get these enabled.
Configure SecureAuth API access
For making SecureAuth API calls, we need to provision one OAuth client application in the Admin workspace and another one in the System workspace. SecureAuth APIs are available for access using one of the tokens as mentioned in the API docs.
Admin OAuth API client
By default, client credentials grant type is disabled in Admin workspace. In the Admin workspace OAuth settings enable the
client_credentialsflow.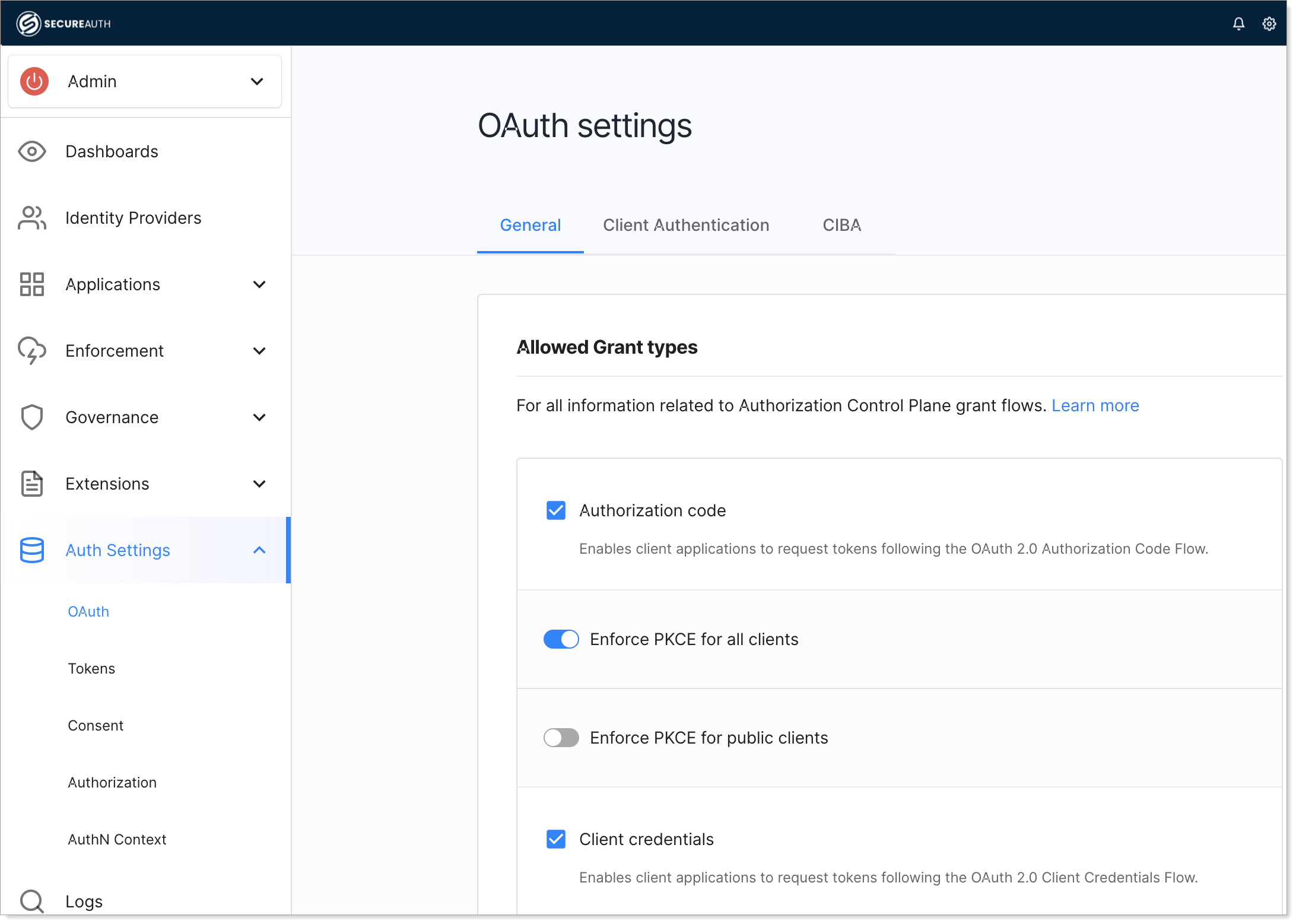
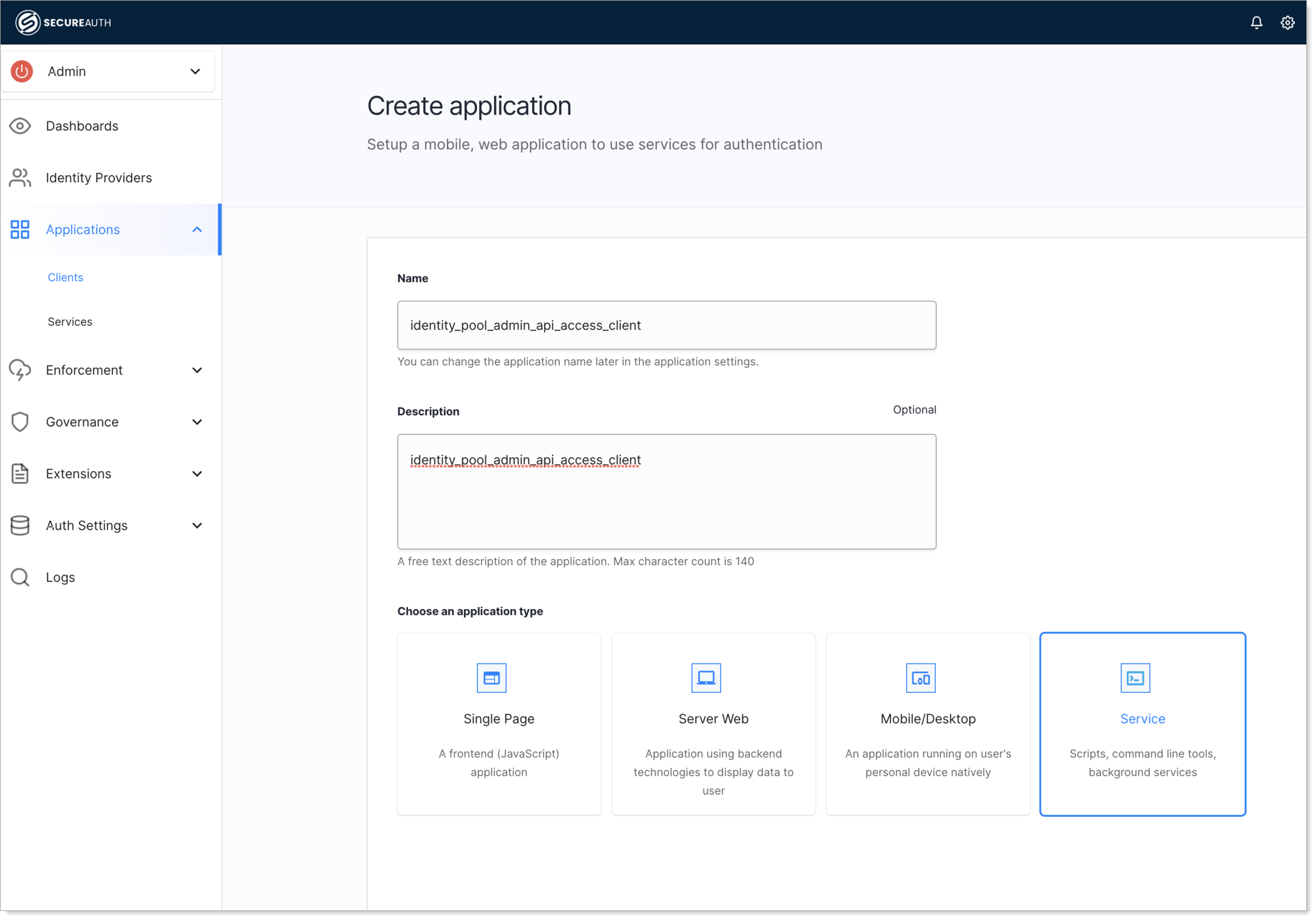
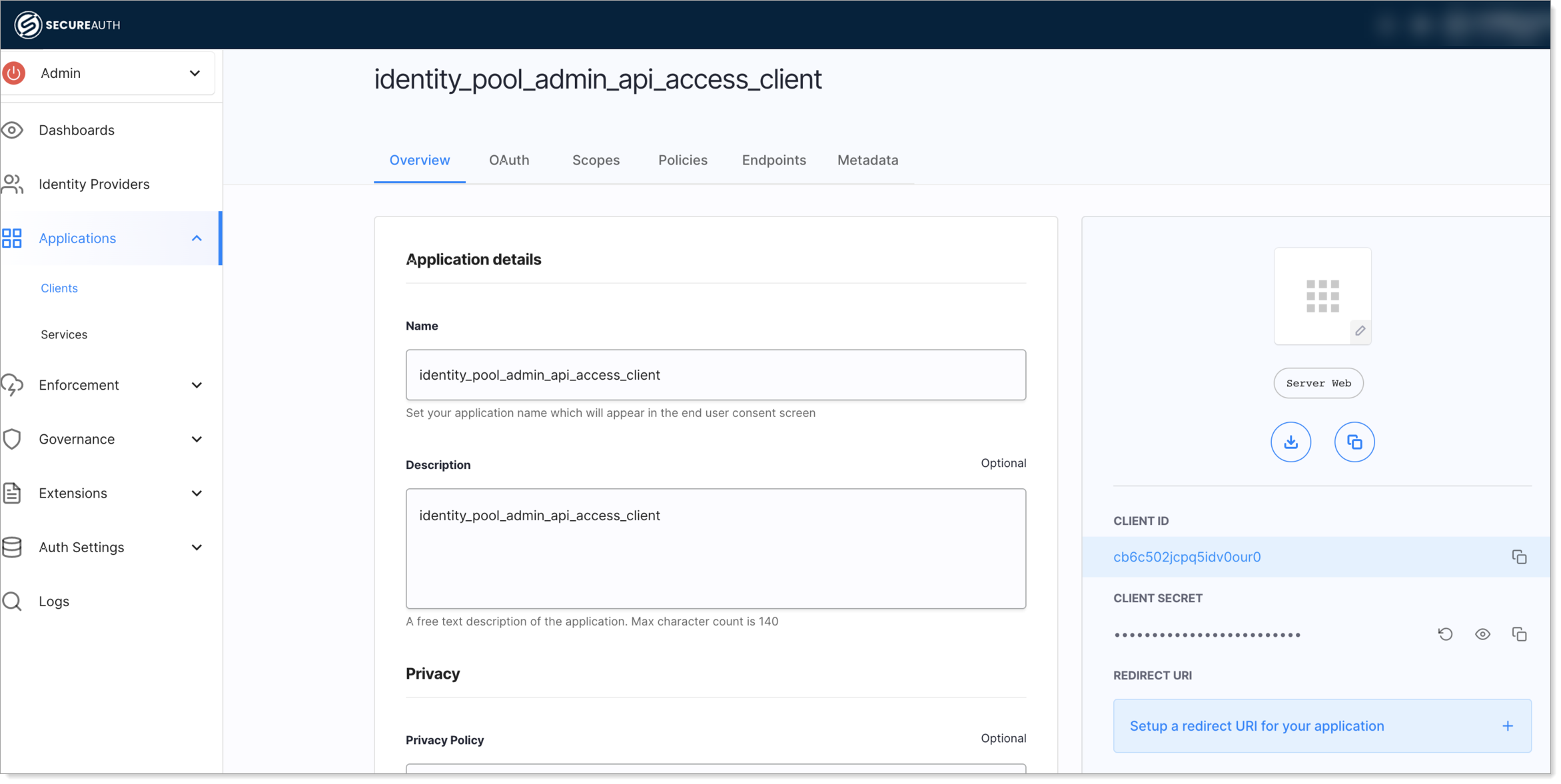
Navigate to the Admin workspace and create an OAuth client application of the service type.
System OAuth API client
Navigate to the System workspace and create an OAuth client application of the service type.
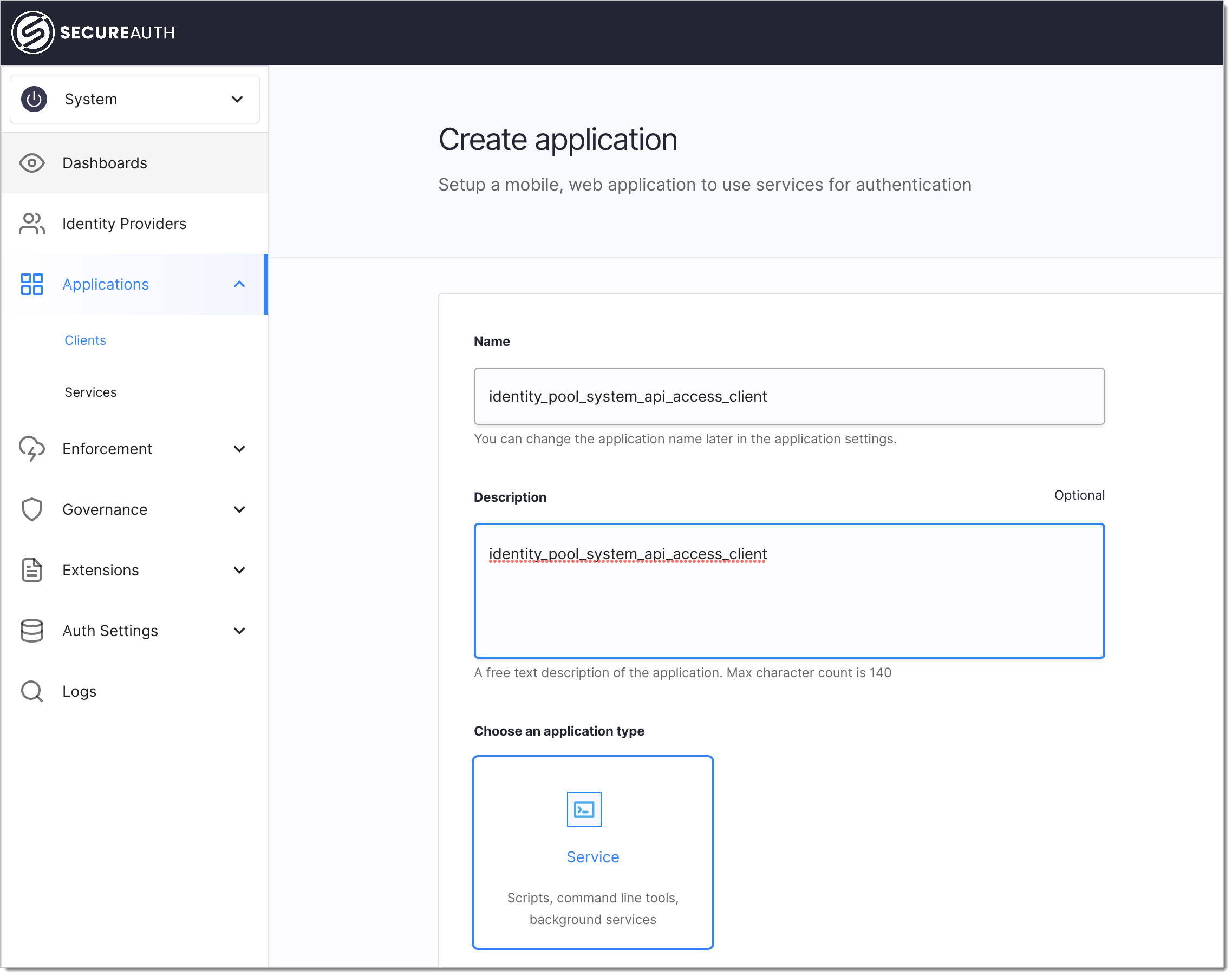
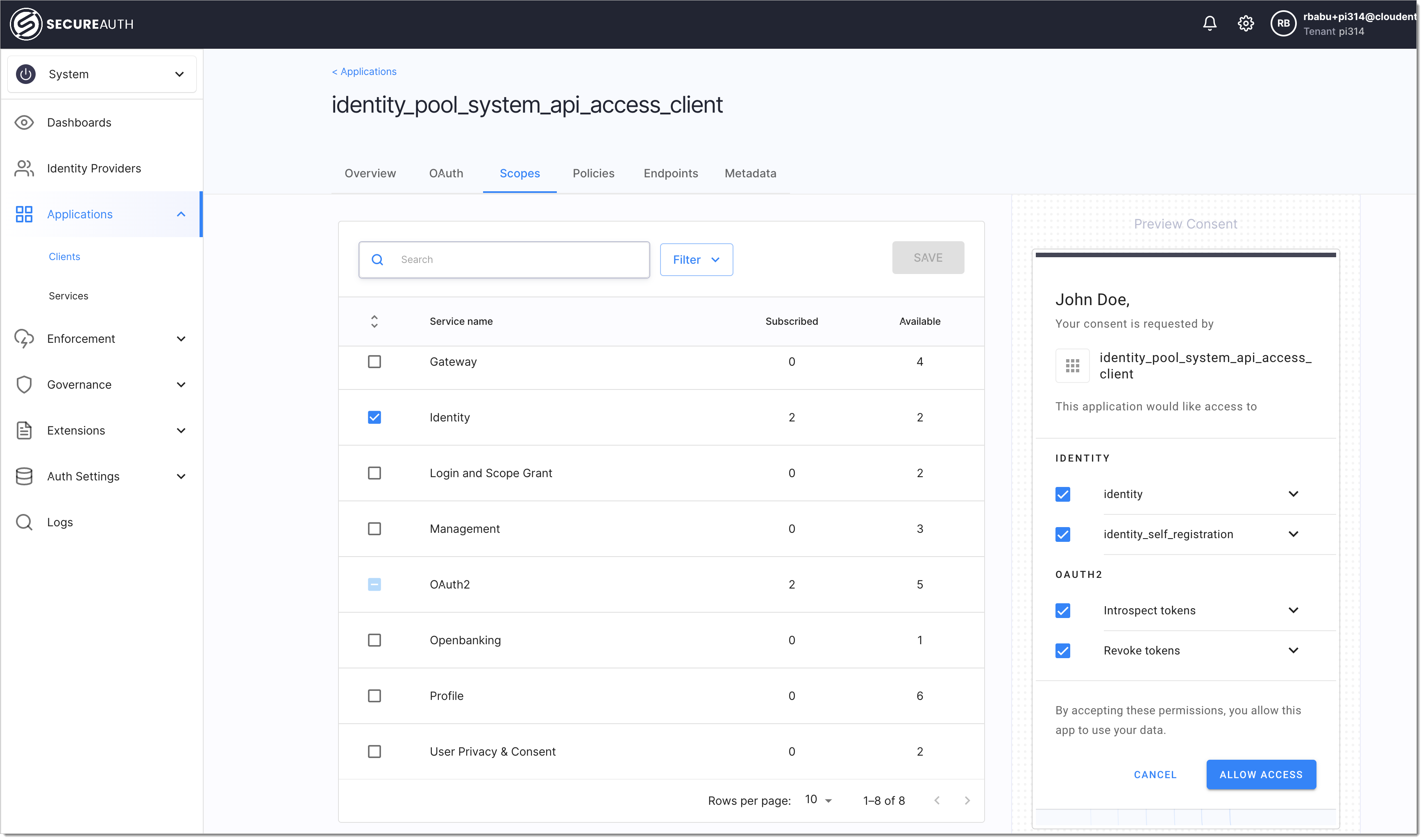
Subscribe to Identity API scopes as highlighted below:
Use SecureAuth Identity Pools APIs
Import Postman collection from the following URL: Identity Pool API
Configure the following environment variables in your Postman:
Env Variable
Description
Sample Value
url
Tenant host url
pi314.us.connect.secureauth.com
tenant_id
Tenant identifier
pi314
admin_client_id
Admin API client id
Obtained from above step after admin api client create
admin_client_secret
Admin API client secret
Obtained from above step after admin api client create
system_client_id
System API client id
Obtained from above step after system api client create
system_client_secret
System API client secret
Obtained from above step after system api client create
workspace_id
Workspace id created by scripts
pool-demo-workspace
schema_id
Schema created by postman scripts
pool-demo-schema
pool_id
Pool id created by postman scripts
pool-demo-identity-pool
{ "id": "58247b42-7e9a-4598-8fe7-f137138a6526", "name": "CE Identity Pool APIs Env", "values": [ { "key": "url", "value": "", "enabled": true }, { "key": "tenant_id", "value": "", "enabled": true }, { "key": "admin_client_id", "value": "", "enabled": true }, { "key": "admin_client_secret", "value": "", "enabled": true }, { "key": "system_client_id", "value": "", "enabled": true }, { "key": "system_client_secret", "value": "", "enabled": true }, { "key": "workspace_id", "value": "pool-demo-workspace", "enabled": true }, { "key": "schema_id", "value": "pool-demo-schema", "enabled": true }, { "key": "pool_id", "value": "pool-demo-identity-pool", "enabled": true } ], "_postman_variable_scope": "environment", "_postman_exported_at": "2022-07-12T03:47:47.667Z", "_postman_exported_using": "Postman/7.36.6" }Run the collection.
Now that you have the collection imported and environment variables configured, you can go ahead and try the APIs from top to bottom.
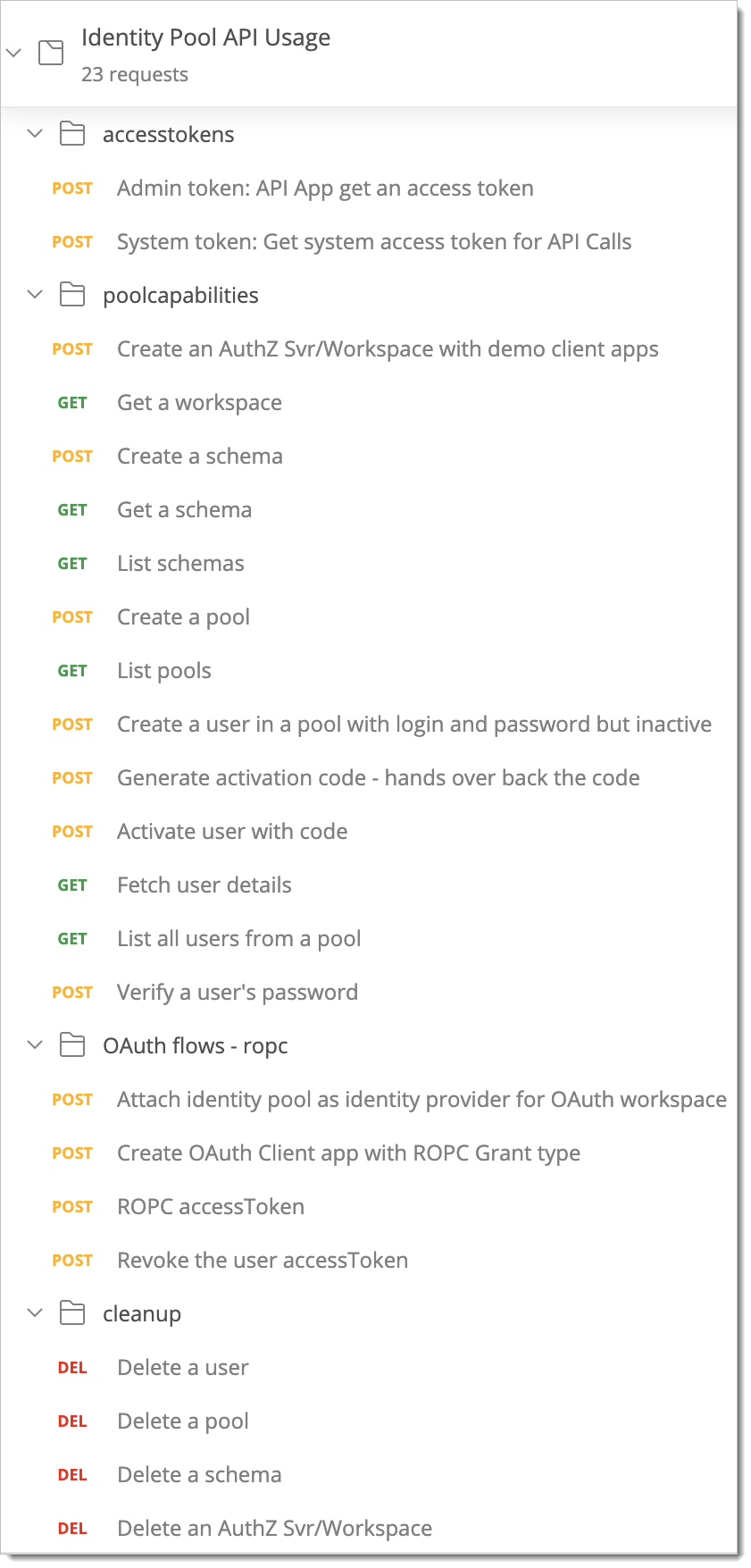
Summary
Now, you can either automate or codify these API calls into your applications based on the workflow you are looking for.