Identity Management for B2B, Partner and Hyper-Scale Consumer Use Cases
Businesses that provide services to other businesses and those which establish numerous partnerships require flexible and structured identity management and storage. SecureAuth comes with a flexible, hyper-scale identity stores to persist identities belonging to the organization, its business customers, partners and third party developers.
The B2B and Partner Identity Management Challenges
B2B2C and Partnership relationships require flexibility, the ability to reflect the business structure and relationships, as well as the possibility to delegate the administration of users for the solution to be complete.
 |
These days, every organization that provides services needs to store and manage different pools of users and delegate administration to minimize the effort of its own administrators. Just think about the users of every business customer, partners' users, developers, own employees, individual customers, and so on. The relationships between these pools may have various structure/hierarchy, too.
Identity management at hyper-scale must be ensured - think of a situation where your partner is a hype-marketing company, for example a shoe producer with a famous logo. On a product release day, you must expect a rapid burst of requests from the buyers, some of whom will want to create accounts. The identity store must be able to withstand this. It must be possible for the platform administrator to provide a multitude of such companies with identity stores for their users.
Let's take a look at problems of a B2B2C platform related to user registration.
Scalability must be ensured - e-commerce platforms, for example, experience massive request bursts upon popular product releases. Therefore, peak load handling and infrastructure autoscaling must be ensured.
Business customers must be able to manage the identities that use the service. Organizations must be able to apply their own settings, such as the password policy or corporate branding.
The user registration form must be embedded within the business site with different activation methods supported (phone, e-mail).
Every pool must be available as an identity source and define user attributes which can be used for making access decisions.
Sector-specific registration problems must be solved (in case of e-commerce partners - minimal data input from the user; in case of banking or insurance partners - a lot of data may be required).
Both admin initiated registration and user self-registration must be available. In B2B businesses, an administrator (for example a team leader) must be able to create accounts on behalf of team members.
User self-service functionality must be provided.
Users must be able to log in to applications
All pages that the users interact with must comply with the partner's branding style
SecureAuth does all of the above, by providing an out-of-the-box solution for user registration known as Identity Pools. Having defined those problems, let's dive deeper into the details and see how the SecureAuth platform can be of service.
Create User Pools for Customers, Employees, and Partners
Let's take a look at how Identity Pools can help provide the necessary identities for the ACME company. ACME needs to fulfill the following use-cases:
Enable their partners to register customers
Enable their business customers to register end customers
Finally, provide their own employees with the means to authenticate themselves.
With SecureAuth, this can be done within a single tenant by creating a dedicated identity pool for Partners and Businesses in your B2B2C model.
To create these pools, ACME administrator needs to do the following:
Create an Identity Pool. You can either create users or enable self-registration during the process.
Optionally, Modify Authentication Context Using Scripts.
That's it! Users can now log in via Identity Pools to client applications registered with SecureAuth.
Register Users in Identity Pools
Identity Pools allow for the persistent storage of user data within SecureAuth's infrastructure, thus providing the alternative to the Bring Your Own Identity (BYOID) approach. Having added an Identity Pool to your tenant, you can connect it as an Identity Source to specific workspaces so that the end-users can log in to SecureAuth or an application (or register in the Identity Pool first).
User self-registration is available with the Identity Pools. It can be turned on/off for each Identity Pool on demand.
Both e-mail and phone activation is supported for users registering with Identity Pools
Sector-specific registration with custom data is enabled by the customizable data schemas.
Administrators can register other team members using Identity Pools.
Scalability is provided via SecureAuth's autoscaling infrastructure so that you don't need to worry about peak load and request bursts.
Users registered in Identity Pools are governed by their status, which changes between new, active, inactive, and deleted. Users can be registered either by SecureAuth (either immediately or with OTP confirmation) or via the self-registration feature.
User Status | Description |
|---|---|
new | User status directly after creation in the UI (either by self-registration or administrator) |
active | User status after address confirmation (by entering an OTP sent text or e-mail). Administrators can also create active users. Only users with this status can log in. |
inactive | User who cannot log in. |
deleted | User who has been deleted. |
Address State | Description |
|---|---|
unverified | Unverified address (e-mail or phone) is created after an administrator creates an inactive user or directly after user self-registration request. |
verified | Verified address is created after an administrator creates an active user or after the user confirms their address. Verified address is the user's identifier |
The simplified state change flow is illustrated by the diagram below:
Additionally, you need to keep in mind that times when qwerty1234 was considered a safe password, are long gone! Make sure that your users fulfill all of the requirements for safe passwords with SecureAuth password policies. Such policies enable the Identity Pool administrators to specify, for example, the minimal length of a password, number of special characters, and many more.
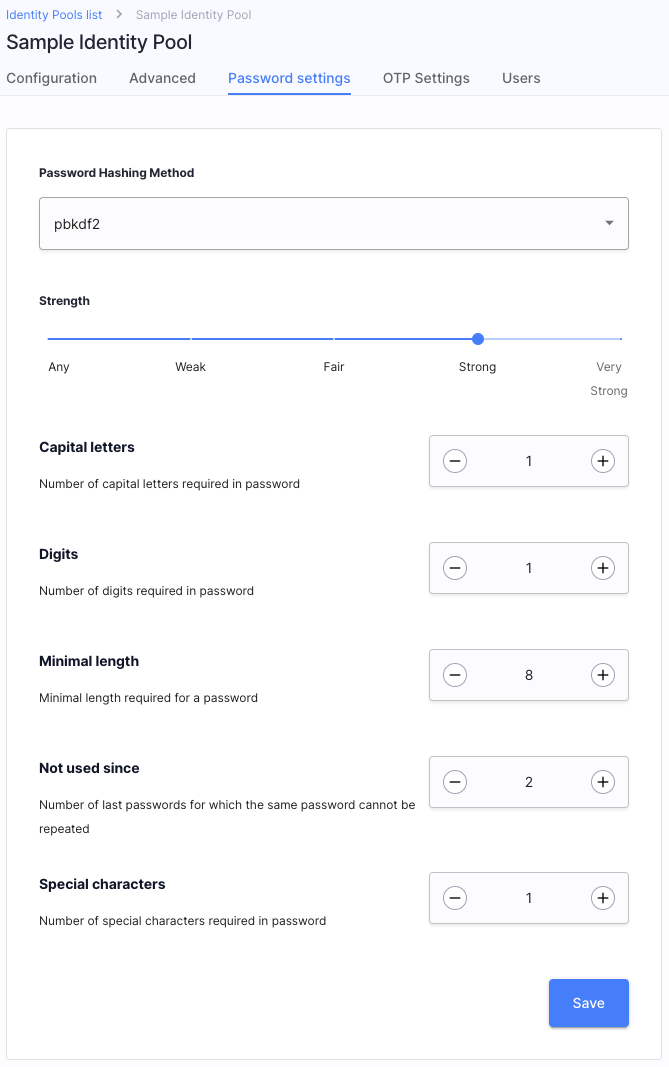 |
For more technical details related to Identity Pools, see Identity Pools.
Customize User Data with Identity Schemas
Identity Schema in SecureAuth is complementary to Identity Pools, allowing for the validation of user data being processed within the Identity Pool APIs. All Identity Pools have a schema assigned for user payload and user metadata - standard properties in most requests. Metadata allows for customizing the user properties, such as, for example, user name, email, but also groups or roles. Metadata can be later on used for setting up Role-based Access Control.
SecureAuth provides default Identity Schemas out of the box - those schemas are assigned to Identity Pools by default and cannot be modified or deleted. You can, however, create and assign a custom schema in order to use the APIs in a different way. This way, you can control what kind of data is processed in every Identity Pool.
Apply Your Branding
As a SecureAuth administrator, you need to keep in mind that different SecureAuth tenants and workspaces may serve different customers and partners for multiple use cases, be it Open Banking, consumer application protection, or third-party API integration. This fact may pose a branding challenge, where you need to consider the needs of:
Fintech users who grant their consents in the Open Banking space (OB consent pages)
Protected application users already accustomed to certain look and feel (User login pages)
Developers who integrate third-party applications via the developer portal
Overall, having a well-branded user interface is key to the commercial success of your company. SecureAuth meets this need, allowing you to apply branding globally (on the tenant level) or on the workspace level.
Brand Tenants
Making changes on the tenant level is easily done from the tenant's setting menu, where you can use the dedicated UI to make simple changes in the following pages:
Application login page
Application consent page
MFA verification page
User portal
Developer portal
Error page
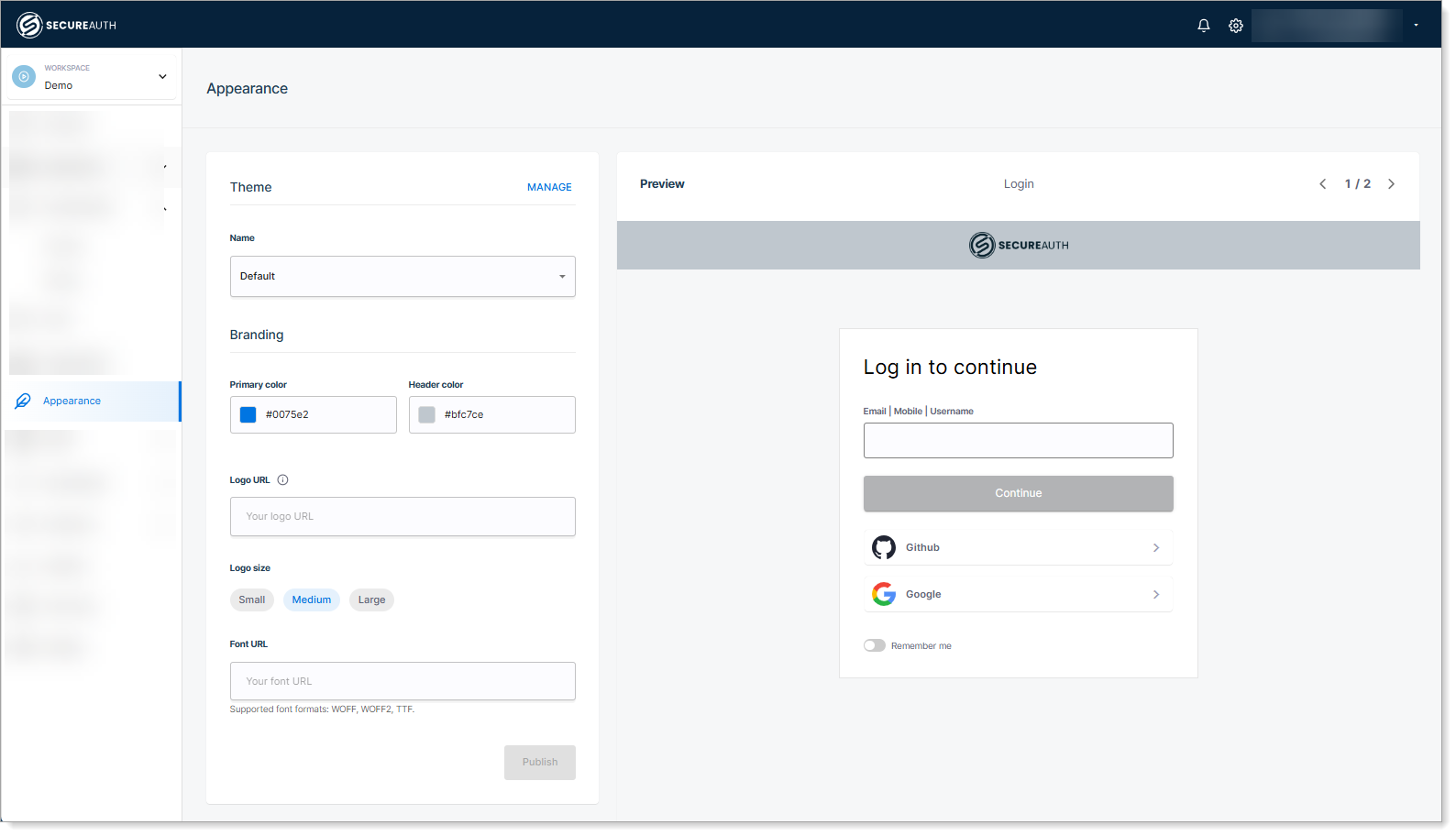 |
After making your changes, you can see the live preview:
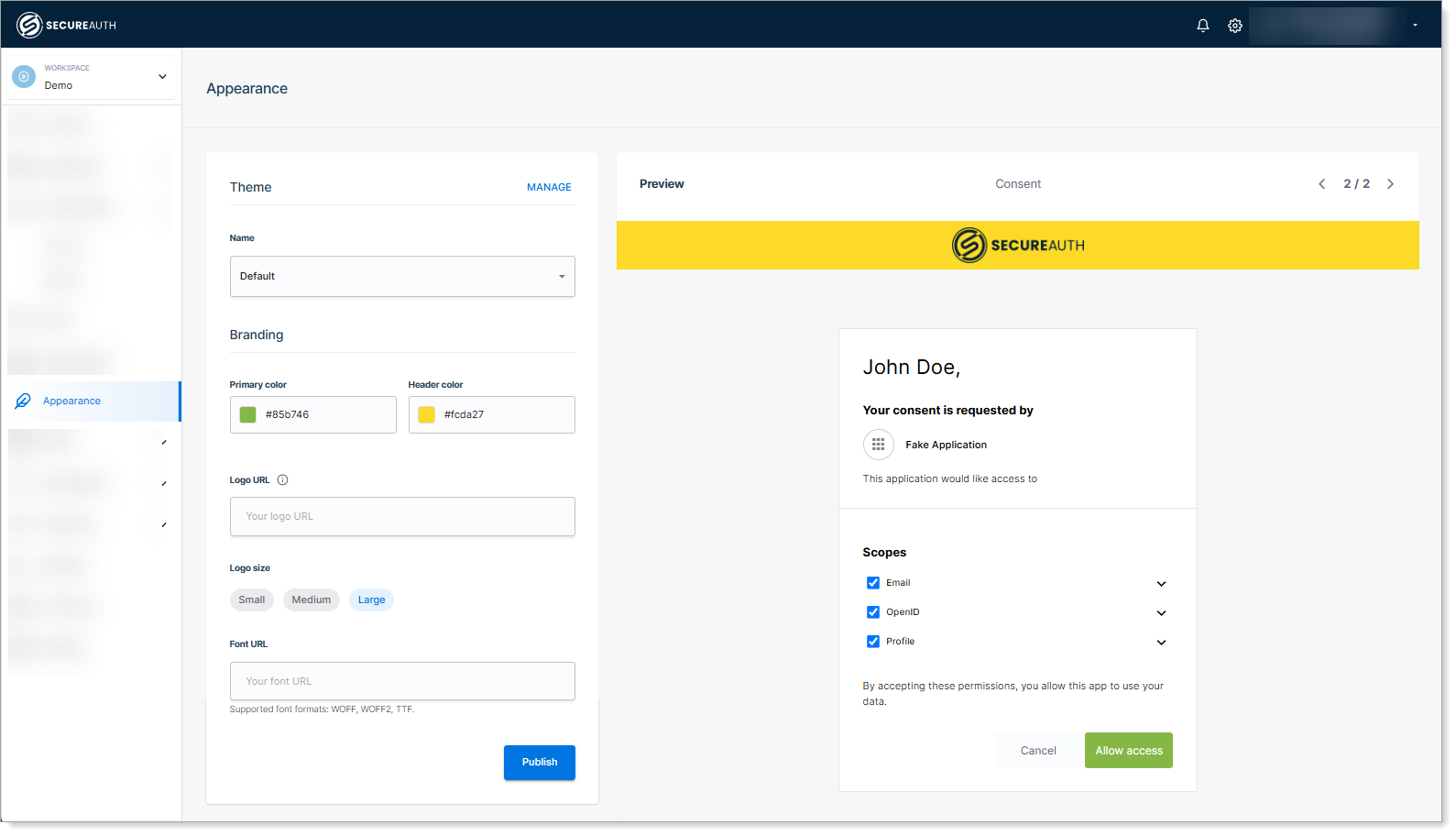 |
Having made your changes, save your changes to propagate them across all workspaces in this tenant.
Brand Workspaces
Workspace Branding applies to individual workspaces serving specific use cases, such as Open Banking compliance or external application protection. Custom workspace themes can be created and assigned workspaces to meet a specific use-case.
SecureAuth exposes its default themes and allows you to modify them directly in the tenant settings menu in order to create a use-case specific theme. You can see your modifications in the live preview page:
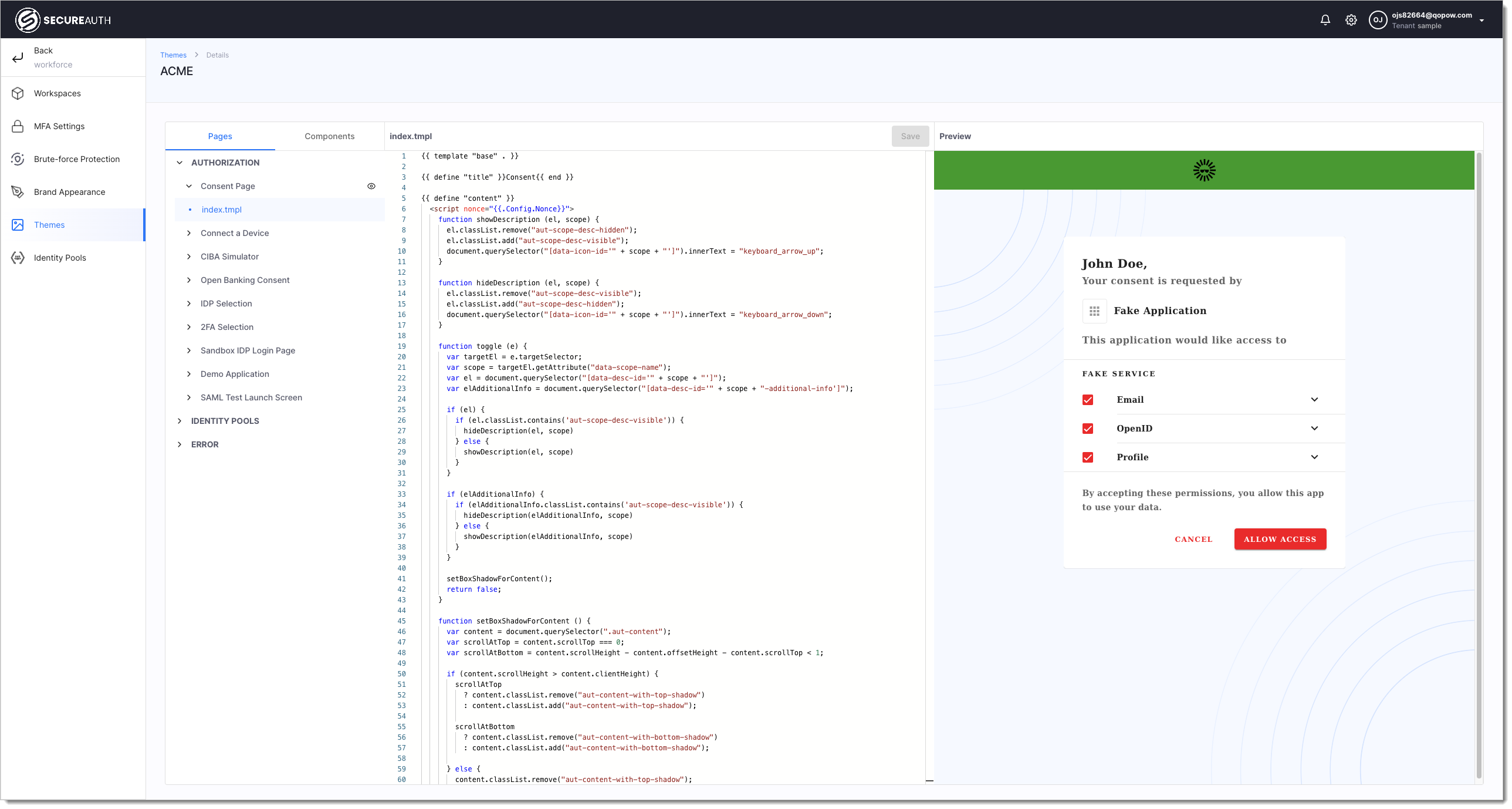 |
When ready, your theme can be assigned to a workspace so that the end users can consume it.
Check It Out Yourself - Free of Charge
As you can see, SecureAuth offers a powerful set of tools for Identity Management. Register for free to get access to a tenant and explore its Identity management capabilities!
Launch a tenant with SecureAuth and get the full range of out-of-the-box capabilities:
Peak load handling with infrastructure autoscaling capabilities.
Complete user administration and options to delegate administration, distributing administrator efforts.
Individual identity pools within a single tenant for diverse user categories: end-users, employees, or partners. User attribute definition for precise access decisions.
Admin-initiated and user self-service registration with the option to adjust the registration process to sector best practices and requirements.
Embedded activation methods for the user registration form.
Corporate branding and individual configuration support, including flexibly customizable password policies and styling for specific screens and user and developer portals.
Workspace templates for various industry sectors ready for further customization.