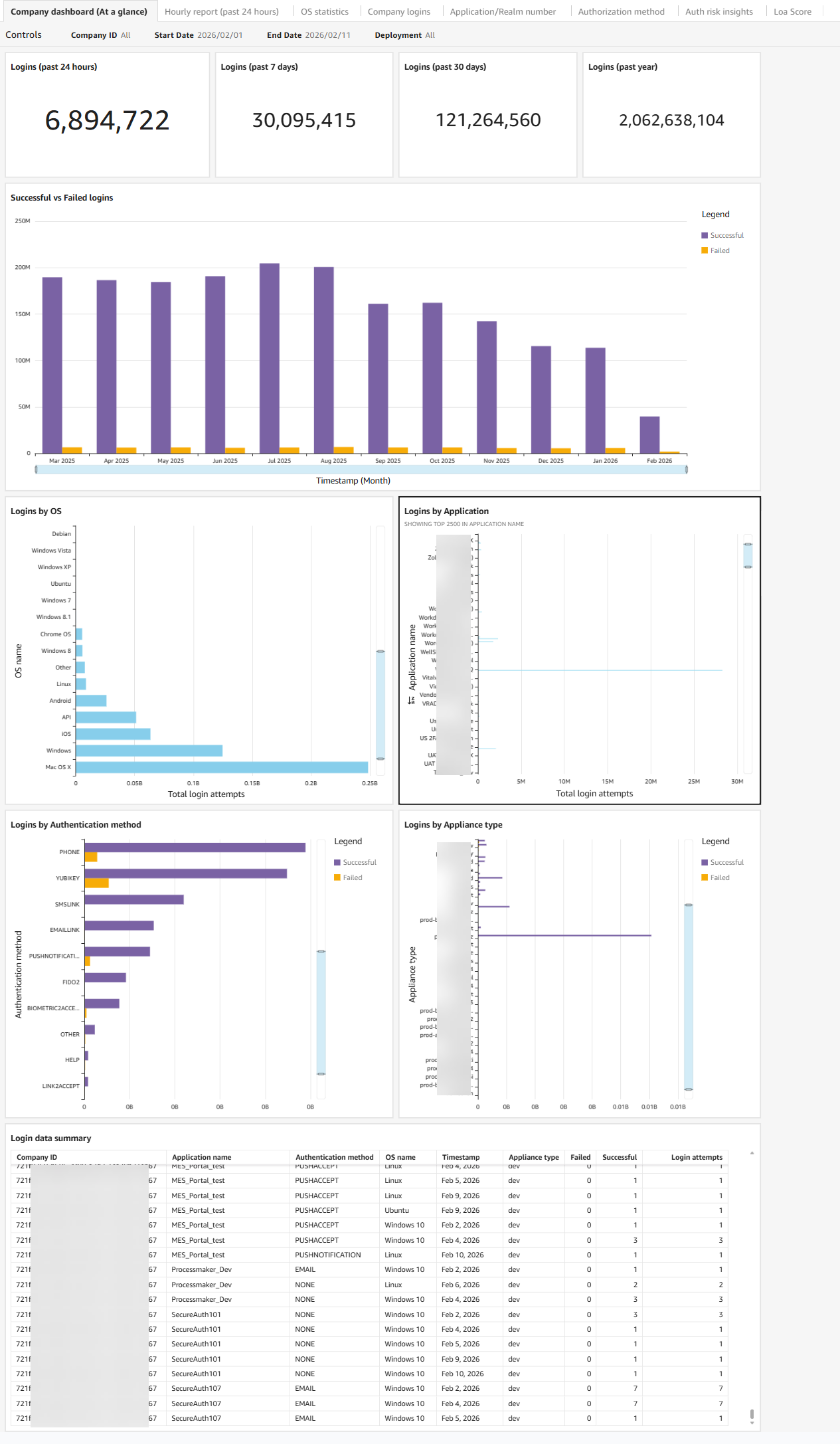
Dashboard: Login data overview
The Company dashboard (At a glance) tab provides a high-level view of authentication health across your SecureAuth IdP environment. It covers login volume, success and failure trends, authentication method usage, and device and appliance activity.
Use this guide to understand what normal activity looks like and recognize patterns that warrant investigation.
What the Company dashboard shows
The dashboard displays authentication activity across several areas: login volume over time, OS and device distribution, application usage, authentication method adoption, appliance performance, and a login data summary covering geographic distribution and Level of Assurance (LOA) scores.
Use the Controls section to filter by date range or company.
 |
What healthy activity looks like
Healthy authentication activity across the Company dashboard typically shows these patterns:
Stable success rates with proportional growth. Login volume grows gradually over time, and failed login rates remain low relative to successful logins. If your organization is adding users or rolling out new applications, you expect login counts to increase — but failure rates should not increase at the same pace.
Modern, managed OS distribution. The majority of logins come from current, managed operating systems. Seeing a consistent mix of Windows, macOS, iOS, and Android that aligns with your known device fleet is expected.
Login volume distributed across applications as expected. Applications show stable login counts that align with business usage patterns. High-traffic applications like your primary SSO target or HR platform will naturally show more activity than internal tools.
Strong authentication methods gaining adoption. Phishing-resistant methods such as FIDO2 and biometrics represent a growing share of logins. Passwordless and MFA adoption trend upward over time.
Appliance activity aligned with your deployment. Production appliances carry the expected share of traffic. Test or staging appliances show minimal activity.
Geographic distribution matches your user base. Logins originate from locations consistent with where your workforce operates. LOA scores remain stable over time.
Warning signs to watch for
The following patterns indicate something may be wrong and warrant further investigation.
Sudden spike in failed logins without matching user growth. A sharp increase in failed attempts that is not accompanied by a corresponding increase in successful logins often indicates a brute force or password spray attack in progress. Check the Auth risk insights tab to confirm.
High login activity from unknown, legacy, or outdated operating systems. Unexpected OS entries or a surge in logins from unsupported systems may indicate unmanaged devices accessing your environment, or an attempt to exploit OS-specific vulnerabilities.
Sharp increase in failed logins to a specific application. If one application shows a disproportionate spike in failures while others remain stable, it may be under targeted attack or experiencing a misconfiguration. Check the Application/Realm number tab.
Weak authentication methods dominating while strong options show low adoption. If password-only logins are increasing while MFA and passwordless adoption stagnates or declines, your authentication security is weakening. This is also a compliance and audit concern.
Unexpected appliance activity. A sudden spike of failed logins on a production appliance, especially one not associated with a known deployment or change, may indicate an attack or an outage affecting failover behavior.
Unusual geographic distribution or LOA score decline. Logins from unexpected regions, or a downward trend in average LOA scores, can indicate compromised accounts or policy changes that are weakening authentication confidence.
What to do next
When you see a warning sign, use the other dashboard tabs to investigate further before escalating.
If the Auth risk insights tab shows active threat data, see Dashboard: Authentication risk insights for details on each threat type and the features required to block them.
Warning sign | Where to investigate next |
|---|---|
Spike in failed logins | Auth risk insights tab, then Password Throttling configuration |
Unusual OS or device activity | OS statistics tab |
Application-specific failure spike | Application/Realm number tab |
Authentication method concerns | Authorization method tab |
User-level investigation needed | Company logins tab |
Hourly pattern or off-hours spike | Hourly report tab |