End user login experience on Windows
Updated December 2024
This topic provides a detailed overview of the Windows login experience for your end users. It is designed to help you determine the best configurations for your organization.
Important
If using a proxy that becomes unavailable, Login for Windows behaves as if it is offline. This can affect laptop users connecting to networks where the proxy is unavailable.
First-time login experience
Enter your username and password on the Windows login screen.
Choose your authentication method.
The first time you log in, Login for Windows displays only OATH-based methods, if at least one is available. For example, TOTP or HOTP.
If you need to log in when your machine is offline, you must choose an OATH-based method during your first login. After selecting a timed authentication option and entering your password, TOTP and HOTP passcode options will be available for offline logins.
Choose where you will receive your timed passcode.
If you have multiple mobile phones or YubiKeys, you can choose which device or token to use when online. For offline logins, any OATH-based method you used online will also be available.
Enter your timed passcode and submit.
The next time you log on to the same machine, the Login for Windows page will show all the multi-factor authentication methods you’ve enrolled in. See Subsequent login experience to learn more about each authentication method.
Subsequent login experience
In future logins on the same machine, the Login for Windows page will show all the multi-factor authentication methods you’ve enrolled in.
Note
The login screen defaults to the authentication method used in the last login session.
The image below displays some of the available authentication methods:
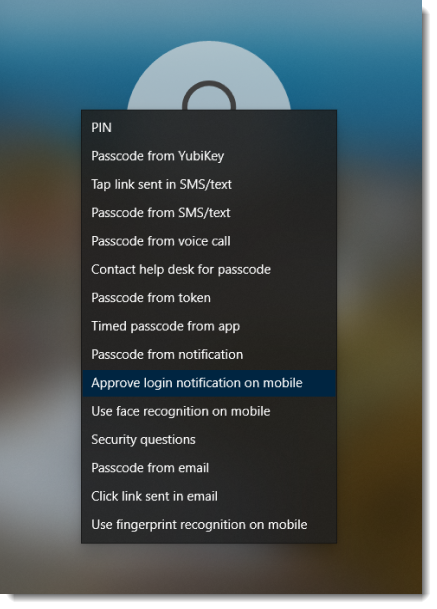 |
You can also click Sign-in options to view available passwordless authentication methods.
Click any of the common authentication methods below to see log in instructions and demonstration videos. For help with methods not seen on this list, contact SecureAuth Support.
Use biometric face recognition to authenticate access to your Windows workstation.
Note
Face recognition option shows only when face recognition is set up in Windows Hello.
Login icon | Login instructions | Demonstration | |
|---|---|---|---|
|
|
Use biometric fingerprint recognition to authenticate access to your Windows workstation.
Note
Fingerprint recognition option shows only when fingerprint is set up in Windows Hello.
Login icon | Login instructions | Demonstration | |
|---|---|---|---|
|
|
Use a smart card to authenticate access to your Windows workstation.
Login icon | Login instructions | Demonstration | |
|---|---|---|---|
|
|
Approve the login notification sent to Authenticate app on your mobile device to log in.
Login instructions | Demonstration |
|---|---|
Approve login notification on mobile
|
Use a passcode sent to your email.
Login instructions | Demonstration |
|---|---|
Passcode from email
|
Use fingerprint recognition on your mobile device to log in.
End users must use the Authenticate mobile app to use fingerprint recognition.
Login instructions | Demonstration |
|---|---|
Use fingerprint recognition on mobile End users must use the Authenticate mobile app to use fingerprint recognition.
|
Contact the help desk in your organization to receive a passcode to log in.
Login instructions | Demonstration |
|---|---|
Contact help desk for passcode
|
Use a passcode sent in an Authenticate app notification on your mobile device to log in.
Login instructions | Demonstration |
|---|---|
Passcode from notification
|
Use a passcode sent to your SMS to log in.
Login instructions | Demonstration |
|---|---|
Passcode from SMS / text
|
Tap the link sent to your SMS to log in.
Login instructions | Demonstration |
|---|---|
Link from SMS
|
Use a passcode in a token like a HOTP security key to log in.
Login instructions | Demonstration |
|---|---|
Passcode from token
|
Use a YubiKey to log in.
Login instructions | Demonstration |
|---|---|
Passcode from YubiKey
|
If you have VPN clients and you enabled a pre-logon access provider by setting the Auto add pre-logon access providers option, end users can connect to your VPN server before logging into Login for Windows. The frequency that end users must log into the VPN client depends on settings completed by the administrator. When end users log into their machine, they will first select the VPN login icon, called Network sign-in, which is shown in the following image surrounded by a red box:
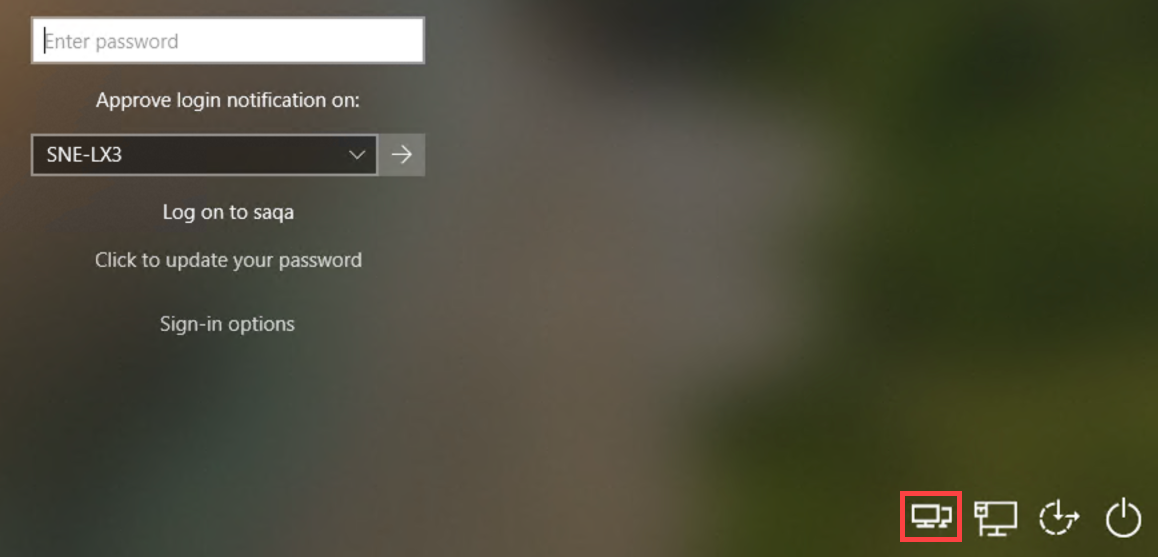 |
End users can then authenticate with Login for Windows.
Admin login experience
To log in to a privileged account as an administrator (using "Run as administrator") on the same machine where you're logged in as a regular user, you will be prompted to complete multi-factor authentication. To view the available options, right-click on an executable.
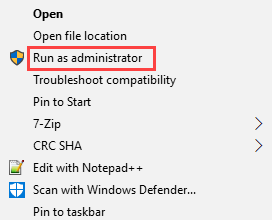 |
Select one of the options and then enter the admin password.
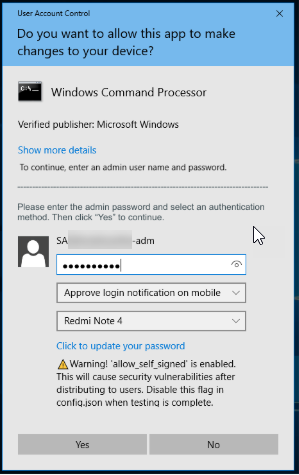 |
Note
Users with access to privileged accounts are not prompted for additional MFA when logging into their normal user accounts; however, it is possible to configure UAC policies to prompt administrators for password or MFA when they log into their normal user accounts. To learn more, see UAC - Require a Password for Administrator.
First login with password only
If enabled, end users can log in without second-factor authentication for the number of days specified by the administrator in the Grace Period setting. This allows users to log in with just a password, typically after the Login for Windows installation.
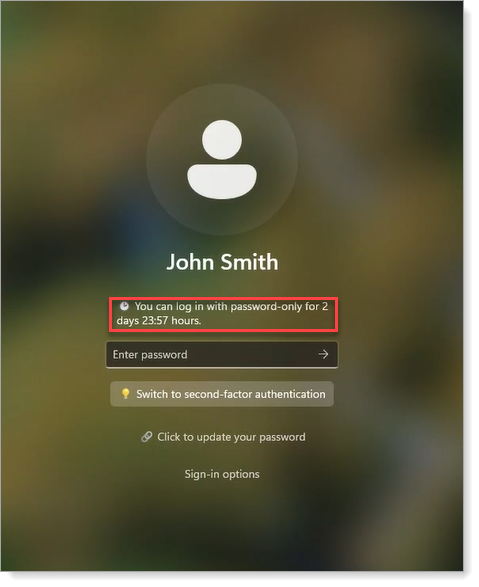 |
During this period, users can set up their two-factor authentication methods, such as push-to-accept or Security Questions, before they need to authenticate to access their device.
Password-only login is helpful for new employees who receive a laptop on their first day. For example, if Login for Windows is already installed but the Grace Period is not set, new employees may not be able to log in if they cannot connect to the SecureAuth Identity Platform to register their mobile phone.
Login without connection to Identity Platform
End users can log in to their machine without a connection to the Identity Platform if the Install Login for Endpoint without connection to Identity Platform and Grace Period options are enabled. This allows them to log in using only a password, without needing second-factor authentication, for the number of days specified as the grace period.
This is useful when a third-party company sets up machines without connecting to the Identity Platform. For example, if Login for Windows is installed without the required settings, new employees may not be able to log in when they first receive their machine.


