YubiKey global MFA settings
At the global level, configure the non-FIDO2 YubiKey device method. Users can use a YubiKey device made by Yubico to authenticate into a resource.
To use FIDO2-compliant YubiKeys use the FIDO2 WebAuthn global MFA settings.
You can limit the use of this MFA method in a policy.
On the left side of the Identity Platform page, click Multi-Factor Methods.
Click the pencil icon for YubiKey.
The configuration page for YubiKey appears.
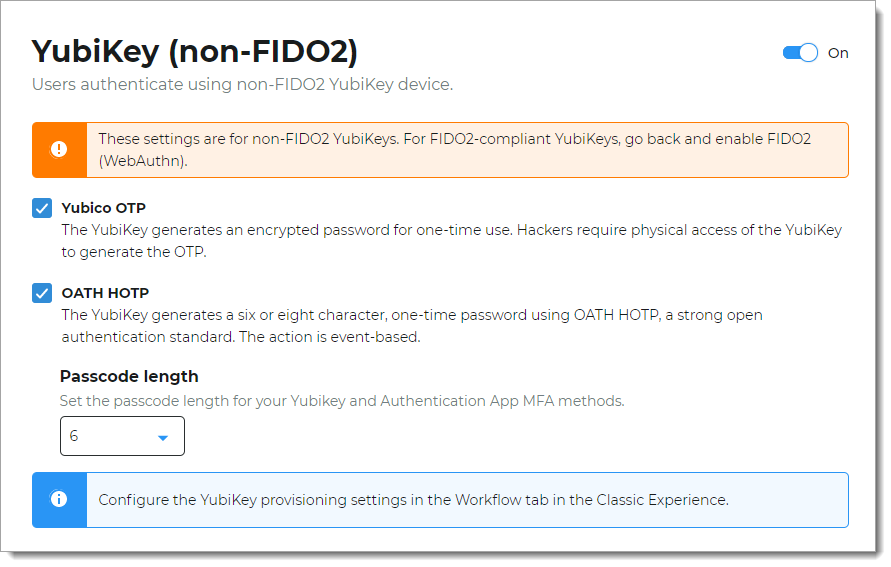
To enable or disable the global YubiKey multi-factor method, slide the toggle On or Off.
Set any the following configurations.
Yubico OTP
Select this option to give access to a user who has a YubiKey to generate an encrypted one-time passcode (OTP).
OATH HOTP
Select this option to give access to a user who has a YubiKey to generate an encrypted six-, eight-, or nine-character one-time (OTP) event-based passcode using OATH-HOTP. This means that a new one-time passcode is generated for each event.
Passcode length
Set the passcode length at six, eight, or nine digits for your YubiKey and Authentication App methods.
Click Save.
Next steps
Configure a policy on the Multi-Factors Methods tab to allow users to authenticate using non-FIDO2 YubiKeys in the login workflow.