Prerequisites
Before you set up Login for Mac in the SecureAuth® Identity Platform, review the following prerequisites.
Administrator
Biometric authentication. If you want to set up biometric authentication for your end users to authenticate by using face (iOS) or fingerprint recognition, review the list of requirements.
Identity Platform release. Biometric authentication in Login for Mac requires the Identity Platform release 19.07 or later.
Biometric authentication. To use biometric fingerprint and face (iOS only) recognition, Login for Mac requires you to use the 2019 theme in the Identity Platform.
Enable Biometric identification method. Enable the biometric identification authentication method for the Authenticate app. In the Identity Platform, from the left navigation, click Mult-Factor Methods > Edit Authentication Apps > select the Biometric identification check box.
SecureAuth Authenticate app. Download and install the SecureAuth Authenticate app:
For more details, see the Prerequisites topic in the SecureAuth Authenticate mobile app document.
Upgrading to Identity Platform 19.07 or later. Your end users who already use the SecureAuth Authenticate app must reconnect their accounts to add the ability to accept biometric push notifications to use face (iOS) or fingerprint recognition through the mobile app.
Personalize the Login for Mac experience. You can customize the Login for Mac experience by setting or changing configuration options in Configure Identity Platform and Login for Endpoints.
Load balancer. If you use a load balancer:
When you use Push-to-Accept, Symbol-to-Accept, or Link-to-Accept MFA methods with Login for Mac, you must enable session persistence ("sticky sessions") on the load balancer to maintain state with the Identity Platform.
Login for Mac supports cookie-based persistence only.
Other setup requirements. See the following for other set up requirements.
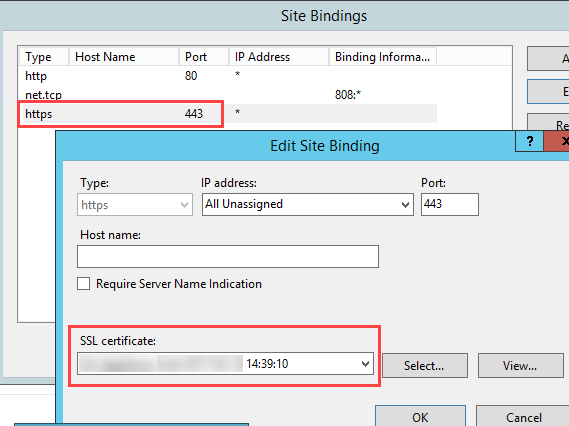
Set up requirement. Ensure the SecureAuth IdP 9.3 or Identity Platform 19.07 or later is running and is using a SHA2 or later third-party publicly trusted certificate bound to Microsoft Internet Information Services (IIS).
For example, in the IIS Management Console's Default Web Site section, check the Site Bindings section to ensure the https/443 type and port settings have a valid and trusted SHA2 certificate selected in the SSL certificate field.
The following example shows the SSL connection being terminated on the SecureAuth server.
Alternatively, you can also terminate the SSL connection on the load balancer, and then your publicly-trusted certificate will reside on the load balancer.
Note
Do not remove the SecureAuth certificates from the certificates console or the SecureAuth appliance will no longer function.
Compatibility. Ensure target end user machines are running on supported OS versions in the SecureAuth compatibility guide.
User account and Mac workstation requirements. See the following items:
The Active Directory profile for the end user must be accurately configured on the Mac. This is important so that the endpoint can retrieve the AD end user profile during the login process.
In an enterprise WiFi environment, before setting up Login for Mac on end user workstations, you must configure the he system level policy must to allow the Mac to connect to the enterprise Wi-Fi. This setup lets Login for Mac get the OATH seed used to authenticate the end user.
If an end user is already using a YubiKey device for YubiKey multi-factor authentication on a SecureAuth Identity Platform realm, the OATH seed and associated YubiKey device must be removed from the end user's account to prevent a conflict when the end user attempts to use a YubiKey device for HOTP authentication. (See the steps under "End user multi-factor authentication" in the YubiKey HOTP Device Provisioning and Multi-Factor Authentication Guide to remove the YubiKey device from the user account profile.)
Note
If an end user is disabled on Active Directory, the local account will not know the history of the AD account, and the user will not be able to log on the Mac.
To prevent and troubleshoot end user lockouts, see Troubleshooting Login for Mac.
End user account and Mac workstation requirements
Important
Before installing Login for Mac
For end users, their local username and password on the Mac must be the same as their Active Directory username and password. If they use a different local username than their Active Directory username, they should work with IT to synchronize the IDs.
If their user IDs are synchronized, make sure they can log in to the Mac before installing Login for Mac.
This section details the first-time usage requirements.
End users can log in without second-factor authentication for the number of days set by the administrator. This allows end users to log in with a password only so they can set up their two-factor authentication methods before they must authenticate to access their device. After end users set up 2FA, the following is the authentication workflow.
Login for Mac requires end users to use one OATH-based method (i.e., TOTP, HOTP), if at least one method is available to end users. If at least one OATH-based method is not available to end users, they can use any other available method, but offline login will not be available.
To meet this requirement, end users must use one of the following accounts provisioned with an application integrated in the Identity Platform that enables their device to generate timed passcodes for multi-factor authentication:
SecureAuth Authenticate app on a phone or tablet or
YubiKey HOTP or TOTP security key
Refer to the YubiKey HOTP Device Provisioning and Multi-Factor Authentication Guide or the YubiKey OATH-TOTP Device Provisioning and Multi-Factor Authentication Guide to ensure all requirements are met. To ensure that supported YubiKey devices are used, see the "YubiKey" section of the SecureAuth compatibility guide.
Thereafter, end users can use Login for Mac to log in when working online and offline.
Additionally, consider the following requirements for end users:
To use face recognition, available for iOS mobile phones only, end users must complete the following:
Enable their iOS mobile phone Face Recognition setting
Download and set up the SecureAuth Authenticate app
Sites upgrading from SecureAuth release 9.3 to the Identity Platform release 19.07: End users who already use the Authenticate app and want to add the ability to accept biometric push notifications to use face (iOS) or fingerprint recognition must first reconnect the account for their mobile device.
To use fingerprint recognition, end users must complete the following:
Enable the Fingerprint setting on their iOS or Android mobile phone
Download and set up the SecureAuth Authenticate app
End users who already use the Authenticate app and want to add the ability to accept biometric push notifications to use face (iOS) or fingerprint recognition must first reconnect the account for their mobile device.