Self-service password reset hotfix update
Hotfixes were released in SecureAuth Identity Platform releases 20.06 and 21.04 to improve the self-service password reset functionality. This applies to a specific use case outlined in this topic.
Applies to
Hotfix update applies to the following product releases:
Identity Platform release 20.06, up to Hotfix 10
Identity Platform release 21.04, up to Hotfix 4
LDAP data stores
Issue
There is a specific use case that bypasses the password minimum age rule set in the data store, and allows users to change their passwords many times in the same day.
This can cause a security issue with users cycling through their passwords and going back to reusing a password.
This use case is specific the following Password Reset configuration settings on the Post Authentication tab for LDAP data stores.
 |
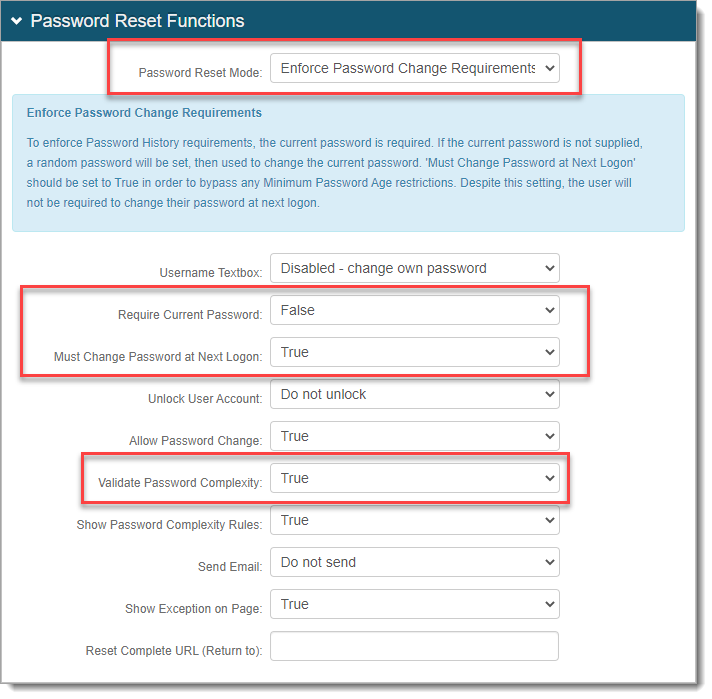
In the Password Reset Functions section, it has the following settings.
Password Reset Mode | Set to Enforce Password Change Requirements. To enforce password history rules, it must use the current password. If the current password is not given, a random password is set, then used to change the current password. |
Require Current Password | Set to False. With this setting, a random password is given during the password reset. |
Must Change Password at Next Logon | Set to True. With this setting, the user could log in several times a day using a different password and bypasses the minimum password age rule. |
Validate Password Complexity | Set to True. With this setting, the Identity Platform reads and validates the password complexity rules set in the data store. |
 |
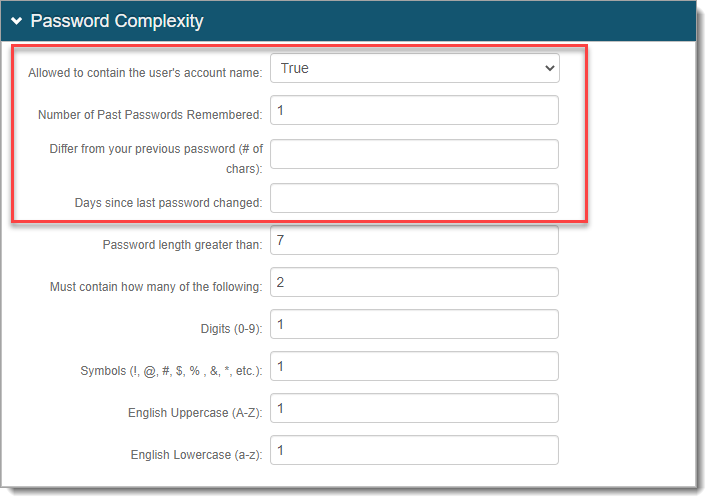
The Password Complexity section was designed to allow administrators to show the password rules to the end user. The rules set here should mirror what is set in the data store for display to the end user.
The Identity Platform does not validate the first four rules in the Password Complexity section; however it does read and validate the password from the data store, based on the data store settings.
 |
In the use case outlined above, since there is an administrative reset that takes place to obtain a known current password to use in enforce mode, the Identity Platform bypasses the minimum age for the second reset. Thus allowing for the password cycling.
Solution
With the hotfix update, Identity Platform now uses the Days since last password changed setting. It reads the pwdLastSet attribute from the user's profile and compares that against the setting for validation. If the condition is not met, then the administrative reset will not occur and prevents the user from changing their password a second time.
As a solution, use the following applicable for your product release:
For Identity Platform release 20.06, apply Hotfix 11 or later
For Identity Platform release 21.04, apply Hotfix 5 or later